With the use of Defender for Cloud Apps in combination with Defender for Endpoint it is possible to block unsanctioned apps, the block of apps is possible based on discovered applications.
| Blog information: Blog published: July 26, 2023 Blog latest updated: July 26, 2023 |
One of the core features in Defender for Cloud Apps is the ability to use the Cloud Discovery feature. In the past years, I blogged multiple times about the integration capabilities between Defender for Cloud Apps and Defender for Endpoint. With the recently merged portals; where Defender for Cloud Apps is now part of Microsoft 365 Defender it is time for a new deep-dived blog focussing on the blocking capabilities of apps from Defender for Cloud apps in combination with Defender for Endpoint.
How can we block apps automatically?
With the recent announcement and improvements in both products, there are a couple of ways of blocking apps in Microsoft 365 Defender
- Defender for Endpoint Vulnerability management add-on
- Block apps in Defender for Cloud Apps and sync indicators to Defender
- Block apps via indicators in Defender for Endpoint
- Use corporate firewall
With the vulnerability management add-on feature, it is possible to block all vulnerable versions. This feature is more in-depth explained in the following blog: Block “vulnerable/unwanted” applications with Defender for Endpoint and Vulnerability Management
When using corporate firewalls it will not prevent the user/devices from accessing the URL/ App when they are not working behind the corporate feature. With a more working-from-home structure, it is important to block the app directly on the endpoint to avoid workarounds via multiple networks.
In this blog, I will deep-dive more into the capabilities of blocking apps automatically in Defender for Cloud Apps and sync indicators to Defender for Endpoint.
Govern discovered apps
When onboarding machines to Defender for Endpoint there is the option to sync data with Defender for Cloud Apps. This feature is called Cloud Discovery.
There are several ways to connect the cloud discovery feature in Defender for Cloud Apps. The most simplified way is possible with continuous reports and enabling the Defender for Endpoint integration. Defender for Cloud Apps integrates with Defender for Endpoint natively via the sensor for collecting data.
The traffic information collected by Defender for Endpoint will be used. There are no additional requirements for the deployment and the integration can be enabled in Defender for Endpoint and Microsoft 365 Defender.
Prerequisites
Before starting with the cloud discovery feature make sure the following requirements are available:
- License to Defender for Cloud Apps
- License to Defender for Endpoint P2
For the client there are no specific prerequisites, make sure to use the latest support versions of Windows 10/ Windows 11 for collecting data via the sensor. For older versions, there are a couple of specific requirements.
The blocking part works together with the indicators in Defender for Endpoint. Important to validate the following Defender AV components:
- Real-time protection must be enabled
- Cloud-delivered protection must be enabled
- Network protection enabled and configured in block mode
Important: When using Network protection in audit mode there is visibility in the discovered apps; there is no option to block the apps on the endpoints themselves.
Defender for Cloud Apps Cloud Discovery
Cloud Discovery is one of the main Microsoft Defender for Cloud Apps features; it helps to get more information on the traffic around apps and detected “unwanted/ unmanaged” apps in the organization. In a nutshell; it detects user activities, traffic volume, usage and gives a clear overview of the “shadowed” traffic part of the organization.
The main question for organizations is; do you have right now visibility when data leaks out from the organization to unmanaged cloud applications? For example; the organization is using OneDrive – when other cloud apps are not restricted or the data itself is not protected – there is a good chance data is transferred to unmanaged applications. With the use of Defender for Cloud apps it is possible to control the data flow and prevent unmanaged app usage.
As already explained – when using Defender for Endpoint on endpoints it is possible to send the network-related data from Defender for Endpoint to Defender for Cloud Apps via the enabled integration between both products.
Defender for Cloud apps contains thousands of cloud applications that are pre-added with available indicators. The complete cloud app catalog can be found here.
Important: The discovery integration with Defender for Endpoint works only for Windows 10 and higher machines. For servers, it is needed to configure the data integrations from firewalls & proxies. Of course; when blocking apps from Defender for Cloud apps it will target all devices in Defender for Endpoint when no scoping profile is selected, with this approach it is possible to block apps via the same method for iOS, macOS, and other platforms.
Enable integration in Microsoft Defender for Endpoint
First, we need to enable the integration in Microsoft Defender for Endpoint. Go to Microsoft 365 Defender (security.microsoft.com) and click Settings -> Endpoints -> Advanced Features.
Enable the integration: Microsoft Defender for Cloud Apps

Now the integration between Defender for Endpoint and Defender for Cloud Apps is enabled. We need one more integration to make sure the indicators will be added to the indicator list.
| IMPORTANT: Once the integration is done in both products, each app marked as unsanctioned will be added to the MDE custom indicators list. With the network protection feature on block – each URL indicator will be blocked on the device. Always verify the current block list of apps before enabling both integrations. |
Enable integration in Defender for Cloud Apps
For enabling the indicator integration go to Microsoft 365 Defender (security.microsoft.com) and click Settings -> Cloud Apps -> Microsoft Defender for Endpoint
Under Defender for Endpoint enable the configuration Enforce app access. When enabled all apps marked as unsanctioned will be added in the indicator list with the value block.

By default, alerts will be created with the severity Informational. When needed the severity can be changed for the blocked apps. My recommendation is to keep the severity configured with informational – this results in more priority and focuses on the real malicious indicators.
Now we are ready to go to block the first apps in Defender for Cloud Apps.
Block apps in Defender for Cloud Apps
With the integrations enabled it is possible to block the apps. First some basic explanation of the Defender for Cloud Apps views in Microsoft 365 Defender. Recently, Microsoft finalized the integration between Microsoft 365 Defender and Defender for Cloud Apps.
Defender for Cloud Apps is available via Microsoft 365 Defender (security.microsoft.com)
Cloud App Catalog
The cloud app catalog is the database from Microsoft with all discovered apps. At the moment July 2023, 31.173 apps are part of the catalog.

Cloud discovery
In Cloud Discovery there is a tab with the name; Discovered apps. This view shows the traffic and usage for all apps detected by the Defender for Endpoint integration. Here you can see the traffic/ upload size/ transactions/ last seen timestamp and many more for apps discovered in the organization via the Defender for Endpoint integration.

Sanctioned and unsanctioned
Now the most common question is – what is the difference between sanctioned and unsanctioned? In Defender for Endpoint, there are several actions available for each app.

Action explanation:
| Action | App available for end-user? | Explanation |
| Sanctioned | ✅ | App is generally allowed and accessible from the endpoints |
| Unsanctioned | ❌ | App is generally not allowed and might be not accessible. Indicators are synced to Defender for Endpoint in the block state. |
| Monitored | ❗️ | App is monitored, and the user receives a notification that the app is monitored |
App risks score
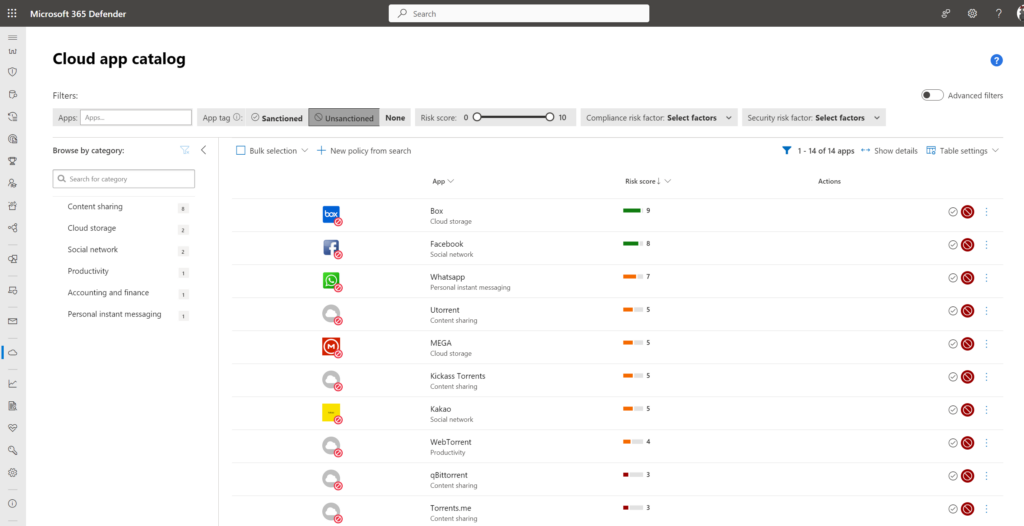
Each app is rated by Microsoft and provided by Microsoft for the apps in the catalog. The score from 0 (worst) up to 10 (best) can be used to identify unwanted/ unwanted applications in the organization.
Apps with risk score 10

App with risk score 2

Block the app itself
When using the action Unsanctioned it is possible to block the app. Use the block icon or click on the three dots for the unsanctioned action.

When blocking the specific application (tag as unsanctioned) there is a prompt visible. Enable the checkbox for configuring specific groups (limiting the scope). Without selecting the checkbox the indicator will be deployed against all devices.

When the checkbox is selected it is possible to configure the block actions against a specific group of machines.

App tags can be configured via the Defender for Cloud Apps settings. Go to Microsoft 365 Defender (security.microsoft.com) and click Settings -> Cloud Apps -> App tags.
Open the item Scoped profiles and create a new profile:

Fill in the profile name and description. It is possible to include or exclude specific device groups configured in Defender for Endpoint. With the scoped entities include; only the selected groups will be part of the profile. When using exclude device groups that are excluded will not be impacted by these tags

After some time the indicator is added in Defender for Endpoint as URLs/Domains indicator. Each indicator part of the integration is visible with the following information:
- Created by: Microsoft Defender for Cloud Apps
- Title when blocked: Unsanctioned cloud app access was blocked
- Title when using monitored: Connection to a risky cloud application was detected

Monitor the app itself
With the option monitored it is possible to warn the app and notify the users with a warning for compliance awareness. When using monitored the indicator will be added in Defender for Endpoint with the type warn.

In the above block screen, there are some differences in comparison with the block tag. First, the Allow button is visible. With Allow you can open always the site. If you click on the: visit the support page button you will redirect direct to the support page set in the Defender for Cloud Apps portal.
If the user clicks on Allow. Microsoft Cloud App Security will register the bypass in the Defender for Cloud Apps detail page of the app. (Cloud Discovery)

Result
When the app is configured in the state monitor or block the experience is different based on the used browser.

Note: It can take up to 3 hours before the Cloud App / URL is blocked on endpoints. The apps will be synced every hour; it can take up to 2 hours before the endpoints have received the policy.
Block app
Website blocked with Microsoft Edge: When using Microsoft Edge the website is blocked using the SmartScreen component. SmartScreen must be configured for Microsoft Edge, without SmartScreen enabled the website is not blocked.

Website blocked with Chrome or other browsers: When using Chrome or other non-Microsoft browsers the website is blocked using the Network Protection component.

Monitor app
Website monitored with Microsoft Edge: When using Microsoft Edge it is possible to Allow the website to bypass the block. This is only working when using websites; when using the native Dropbox app the indicator is blocked since there is no input/ screen.

Website monitored with Chrome or other browsers: When using Chrome or other non-Microsoft browsers the warn/ monitor state is not working, the result is the block message.

Test always the app
One tip – test always the app and the blocking state for both the web version and the native client. In general Defender for Cloud Apps works well for websites en cloud applications. There can be some challenges in the detection of native apps which use different indicators.
Defender for Cloud Apps is mainly designed for browser-based apps; in comparison with a couple of years ago, native apps are better supported. For native apps always test and validate if the app is completely blocked, and when needed configure additional indicators.
Check indicators in Defender for Cloud Apps
For each app, Microsoft listed the detected URLs part of the application. When blocking Facebook Microsoft listed the following URLs:
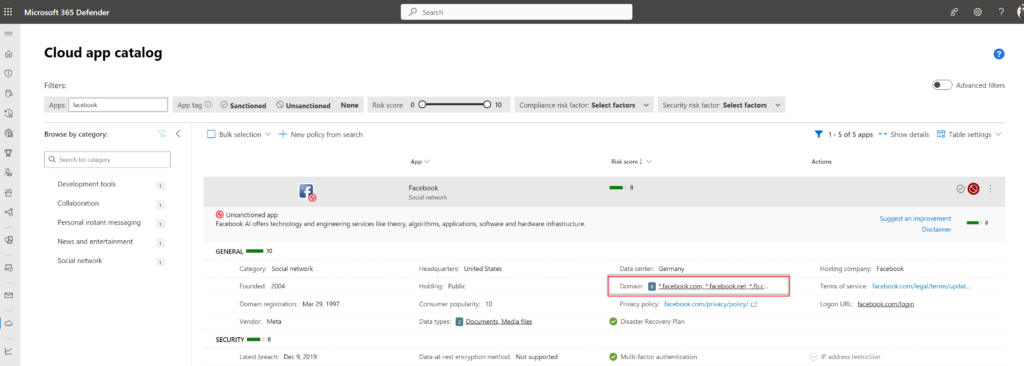
- *.facebook.com
- *.facebook.net
- *.fb.com
- *.fbcdn.net
- *.fbcdn-profile-a.akamaihd.net
- *.fbexternal-a.akamaihd.net
- *.fb.me
- *.fbsbx.com

Conclusion
Managing the discovered ‘Shadow IT’ applications can be a complex task. With the use of Defender for Cloud Apps and Defender for Endpoint it is possible to block apps; it is no ultimate protection – and needs validation for different URLs and native apps.
In one of the upcoming blogs, I will explore the capabilities of blocking apps automatically based on policies and trends in the organizations for newly detected apps.
Stay tuned for more!
Sources
Microsoft: Govern discovered apps
Microsoft: Govern discovered apps using Microsoft Defender for Endpoint
Microsoft: Enable Network Protection




With regard to this integration, something I’ve struggled with is “How do I just let DCA and MDE block the app without hassling me with an alert all the time?”
I ask because a) you can’t edit the DCA linked MDE indicators to just block and not alert, and b) “tuning” the alerts (formerly alert suppression) doesn’t seem to work or requires you to set new suppressions every time an IP Address changes.
Is there a use for macOS here at this time or in the near future? Thanks!
Currently macOS is not supported via Defender for Endpoint sensor, maybe it will be releases in the near future for macOS and other platforms.
Pardon me for asking this seemingly simple thing here, but for the life of me I can’t seem to locate a guide or the location for the “If you click on the: visit the support page button you will redirect direct to the support page set in the Defender for Cloud Apps portal.” in the cloud apps portal. Where exactly can I define the support page link?