Human-operated ransomware (HumOR) is growing and needs different layers of protection. Microsoft released some new features to protect against C2 communication.
Attackers rely heavily on C2 communications for multiple stages, and blocking these direct connections can disrupt or mitigate attacks in the earlier state.
| Blog information: Blog published: May 1, 2023 Blog updated: May 2, 2023 |
What is C2 communication /Command and Control?
A command-and-control C&C server is a computer-controlled by an attacker that sends commands to systems compromised by malware and receives data from the network.
Command and Control (C2) servers often take advantage of rarely monitored traffic and send commands back to the infected host. C2 servers are essential to ransomware, commodity, and nation-state attacks. They control infected devices and perform malicious activities (downloading; launching payloads, commanding post-exploitation).
Command and Control (C2) servers take advantage of trusted and rarely monitored traffic for sending commands back to the infected host.
How works Command and Control (C2) servers:
Step 1: The attacker infects an endpoint within an organization with malware. This can be done using phishing, malvertising, vulnerable software, malicious software, or many more attacks
Step 2: When the host is infected; the C2 connection/ channel is created and sends an acknowledgment back to the C2 server; which indicates that the endpoint is ready to receive commands.
Step 3: When the malware is undetected and the C2 channel is established, the infected system can now receive more commands from the C2 server. The C2 server can be used for malicious software installation, encryption, and further deployment of malicious items.

Image source: Microsoft
Options for detecting C2 channels
There are currently many ways of detecting C2 channels based on indicators/ URL data. When using Defender for Endpoint it is possible to use Advanced Hunting and hunt against the public data via CSV/ JSON feeds and Advanced Hunting. When adding indicators it is possible to block known hashes/ IPs and indicators. More important during C2 channels is the automatic blocking process during the initial connection and closure of the process.
Common options to block/ detect C2 channels:
- Indicators (based on manual hunting/ TI collection)
- Advanced Hunting based on CSV/ JSON feeds
- Threat feeds in other toolings Sentinel/ Siem.
C2 protection in Defender for Endpoint
Microsoft Defender for Endpoint supports different commands against C2 attacks. Defender for Endpoint helps in the detection of C2 attacks earlier in the complete attack chain. Microsoft released detection and remediation for Defender AV/ Defender for Endpoint some months ago.
Network protection command and control detection in Defender for Endpoint is focused on the detection and remediation process.
During C2 channels it is important to detect the early stage of the attack chain and minimize the spread by blocking further attack propagation. In this protection area, the C2 data is combined with the Defender AV engine to block the process which makes the C2 channel using remediation. More information later in this blog with some simulations.
Prerequisites Network Protection
- Windows 10/11 ( Windows 10 version 1709 or later)
- Windows Server 1803, Windows Server 2019, or later
- Windows Server 2012R2/ 2016 installed with unified agent
- Defender Antivirus with real-time protection and cloud-delivered protection enabled
- Defender Antivirus must be in active mode
- Network protection enabled in block mode
- Engine version 1.1.17300.4 or later
For Network Protection make sure the additional configurations are configured for servers. Without the additional configuration, the network protection feature is not enabled.
How works C2 detection and remediation in MDE?
Microsoft Defender for Endpoint uses inspection of network packets and detects the C2 network patterns (known IP/ detected IP/behavior) Of course; when there is a brand new IP used it is not already detected as a “known C2” IP, in this place the behavior helps and tries to detect the C2 activity.
Since 11/10/2022 Network protection command and control detection and remediation capabilities are generally available in MDE. This new future inspects network packets and checks for any types of C2 malware configuration patterns. Microsoft maps outbound connections with threat intelligence and checks for malicious connections./behaviors.
When the connection is evaluated as malicious MDE will automatically block the connection and roll back the binaries to a clean state.
Network protection uses a dynamic reputation database that stores additional information on IPs, domains, and URLs gathered from multiple online sources including research/ adversary tracking/ memory scanning and web scanning for known C2 IPs + machine learning.
The image below it shows the logic. Network protection (NisSr.exe) checks the reputation data with the cloud data and checks the connection data with the Defender Antivirus intelligence (MsMpEng.exe). All data is ended via Sense to the Microsoft Defender for Endpoint service for alerting and visibility. MsMpEng.exe/ Defender AV remediates the process.

Zeek
Microsoft used Zeek for deep packet inspection. Zeek is integrated into the Defender for Endpoint/ MDE agent/ sensor and runs without any additional configuration/ installation. Ensure the OS version is updated with the latest available monthly OS updates later than November 2022 to get the necessary components to enable Zeek.
Zeek maps with the action type ConnectionInspected in the ActionType field of the DeviceNetworkEvents. The following action types/ events are available related to Zeek:
- IcmpConnectionInspected
- HttpConnectionInspected
- SshConnectionInspected
- SmtpConnectionInspected
- FtpConnectionInspected
DeviceNetworkEvents
| where ActionType contains 'ConnectionInspected'
| limit 100
More information: enrich your advanced hunting experience using network layer signals from Zeek
Attack path
A good example is the Rasberry Robin malware attack path. More information: Stopping C2 communications in human-operated ransomware through network protection – Microsoft Security Blog
With the use of Network Protection and C2 detection, the outbound connection is blocked directly from the msiexec.exe process to the C2 domain connection, which prevents automatically the download and launch of TrueBot and Cobalt Strike beacons/ C2 connections.

Image source: Microsoft
Simulate C2 flow
Testing C2 detection and direct remediation is possible with the use of one of the SmartScreen demo sites.
Open PowerShell and run the following command:
Invoke-WebRequest -URI https://commandcontrol.smartscreentestratings.comWhen correct the following message is visible: The request was aborted: Could not create SSL/TLS secure channel. Directly after the message; the process PowerShell is directly closed.

Video: PowerShell initiates connections with C2-channel. MDE/MDAV directly closed the connection and remediates the complete PowerShell process.
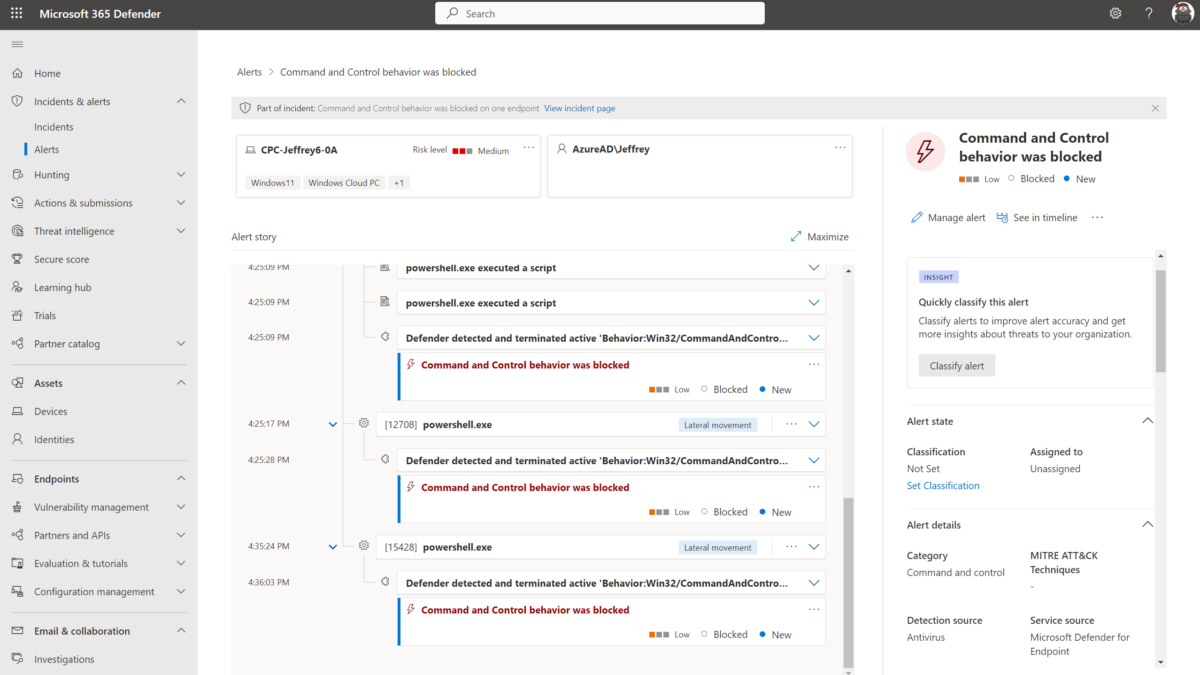
Alert in MDE:
In Defender for Endpoint, the following alert will be visible; “Command and Control behavior was blocked”.

Other methods
There are more ways of detecting C2 activity. With the use of Advanced Hunting it is possible to actively hunt using KQL against known indicators and force automated actions (Restrict app execution, isolate..)
For example, there is the Feoda Tracker. Feodo Tracker is a project of abuse.ch to share botnet C&C servers associated with Dridex, Emotet (aka Heodo), TrickBot, QakBot (aka QuakBot / Qbot), and BazarLoader (aka BazarBackdoor). Of course; Microsoft is already adding “known” indicators as part of the C2 detection/logic.
- https://feodotracker.abuse.ch/
- https://threatview.io/
- https://feodotracker.abuse.ch/downloads/ipblocklist.json
With the use of the externaldata operator it is easily possible to include external data in your queries and match it against the DeviceNetworkEvents table.
See the blog from Fabian Bader for more information. Automated response to C2 traffic on your devices
Sources
Microsoft: Detecting and remediating command and control attacks at the network layer




How can these features help disrupt or mitigate attacks in their early stages by targeting the reliance of attackers on direct C2 connections?