Legacy authentication is the most compromising sign-in. Microsoft is going to disable basic/ legacy authentication. It is recommended to implement Legacy Authentication as soon as possible and switch users to the latest modern authentication protocol. In this blog post, we take a look at legacy authentication and how to block it on your tenant.
Since 2019 Microsoft announced that Microsoft will be turning off legacy authentication. Microsoft announced the following information during the current pandemic:
We previously announced we would begin to disable Basic Auth for five Exchange Online protocols in the second half of 2021. Due to the pandemic and the effect it has on priorities and work patterns, we are announcing some important changes to our plan to disable Basic Auth in Exchange Online.
It is a good point to disable legacy authentication and track the usage and don’t wait for Microsoft. Single-factor authentication is not enough these days to remain secure. One of the easiest things that can be done to protect against password threats is implementing multi-factor authentication (MFA).
What is legacy auth?
The usual meaning for legacy auth in the context of Microsoft cloud services includes all those older protocols one could use to access email and other services.
Currently, the older protocols have been replaced with modern authentication services. More importantly, modern authentication supports multi-factor authentication and modern authentication methods. For security reasons disabling the legacy authentication is highly recommended to improve the security environment.
Modern Authentication is based on OAuth 2.0.
The following options are considered legacy authentication protocols. legacy authentication refers to all protocols that use Basic Authentication. Basic Authentication only requires one method of authentication. Enabling multi-factor isn’t effective if legacy protocols are not blocked.
- Authenticated SMTP – Used by POP and IMAP clients to send email messages.
- Autodiscover – Used by Outlook and EAS clients to find and connect to mailboxes in Exchange Online.
- Exchange ActiveSync (EAS) – Used to connect to mailboxes in Exchange Online.
- Exchange Online PowerShell – Used to connect to Exchange Online with remote PowerShell. If you block Basic authentication for Exchange Online PowerShell, you need to use the Exchange Online PowerShell Module to connect. For instructions, see Connect to Exchange Online PowerShell using multi-factor authentication.
- Exchange Web Services (EWS) – A programming interface that’s used by Outlook, Outlook for Mac, and third-party apps.
- IMAP4 – Used by IMAP email clients.
- MAPI over HTTP (MAPI/HTTP) – Used by Outlook 2010 and later.
- Offline Address Book (OAB) – A copy of address list collections that are downloaded and used by Outlook.
- Outlook Anywhere (RPC over HTTP) – Used by Outlook 2016 and earlier.
- Outlook Service – Used by the Mail and Calendar app for Windows 10.
- POP3 – Used by POP email clients.
- Reporting Web Services – Used to retrieve report data in Exchange Online.
- Other clients – Other protocols identified as utilizing legacy authentication
What is the security risk?
Legacy authentication is a security risk for multiple reasons. In the current digital workplaces, you need to make sure multi-factor authentication is enabled for all the users. The largest security risk is that legacy authentication cannot enforce MFA, this makes it hard for an organization to force the MFA.
Monitor Legacy Authentication Usage
Microsoft made it easy to check if your organization is using currently using legacy authentication protocols. There are multiple options. The first one is using the build-in Azure Active Directory sign-ins screen. 
- Navigate to https://portal.azure.com and log on with a user
- User must have one of the following rights: Global Administrator, Security Administrator, Security Reader, Global Reader and Report Reader
- Open the Azure Active Directory and click Sign-ins. Here you find the Monitor section
- Add a new filter by clicking Add Filters and choose Client app.
- Select all protocols under Legacy Autgentications Clients
- With this view information for 7 days is visible with the option to export to JSON/CSV
Azure Log Analytics Workspace
A Better way to monitor is using the Log Analytics Workspace. With the LA Workspace, you get more detailed information and history with the built-in workbooks.
Log Analytics will be free for Azure AD. Note: an Azure Subscription is required to set this up. Azure AD P1 is required to export your sign-in logs to the LA workspace.
For the creation of the Log Analytics workplace:
- Go to Azure AD – Diagnostic Settings
- Click Add diagnostic Settings
- Select the logs Signinlogs/Auditlogs
- Select the created subscription
- Select the Log Analytics Workplace
Now the connection is created from AzureAD with Log Analytics. For opening the workbooks go to Azure Active Directory -> workbooks.
Subsequently, a number of workbooks are available; in this case it concerns the Usage workbooks (sign-ins and sign-ins using legacy authentication).

Enable Modern Authentication
Before blocking all the legacy authentications inside the AzureAD tenant make sure that your users can use the new modern authentication method. For tenants created after 1 august 2017 modern authentication is enabled by default. Always good to check if Modern Authentication is enabled.
You enable modern authentication in the Microsoft 365 Admin Center or with PowerShell.
- Navigate to the Microsoft 365 Admin Center and log on with a global administrator.
- Click Settings.
- Under the service tab open the Modern authentication part
- Check Enable Modern Authentication for enabling modern authentication.
Report/ Block Conditional Access
The best way to block and report legacy authentication for the user is with conditional access. For Conditional Access make sure an Azure AD P1 license is added for every user to be compliant.
Conditional Access configuration:
-
- User and groups: All users or a selected group
- Cloud apps or actions: All
- Conditions Clients apps: Exchange ActiveSync clients, Other clients
- Navigate the https://portal.azure.com
- Open the Azure AD Conditional Access screen
- Click on + New Policy
- Enter a name EXAMPLE; BLOCK – Legacy auth
- Click User and Groups and select All Users. Except for the break-glass account. If you have no break-glass account. Create an emergency access account with additional exclusions.

- Click Cloud Apps or actions and select All Cloud Apps
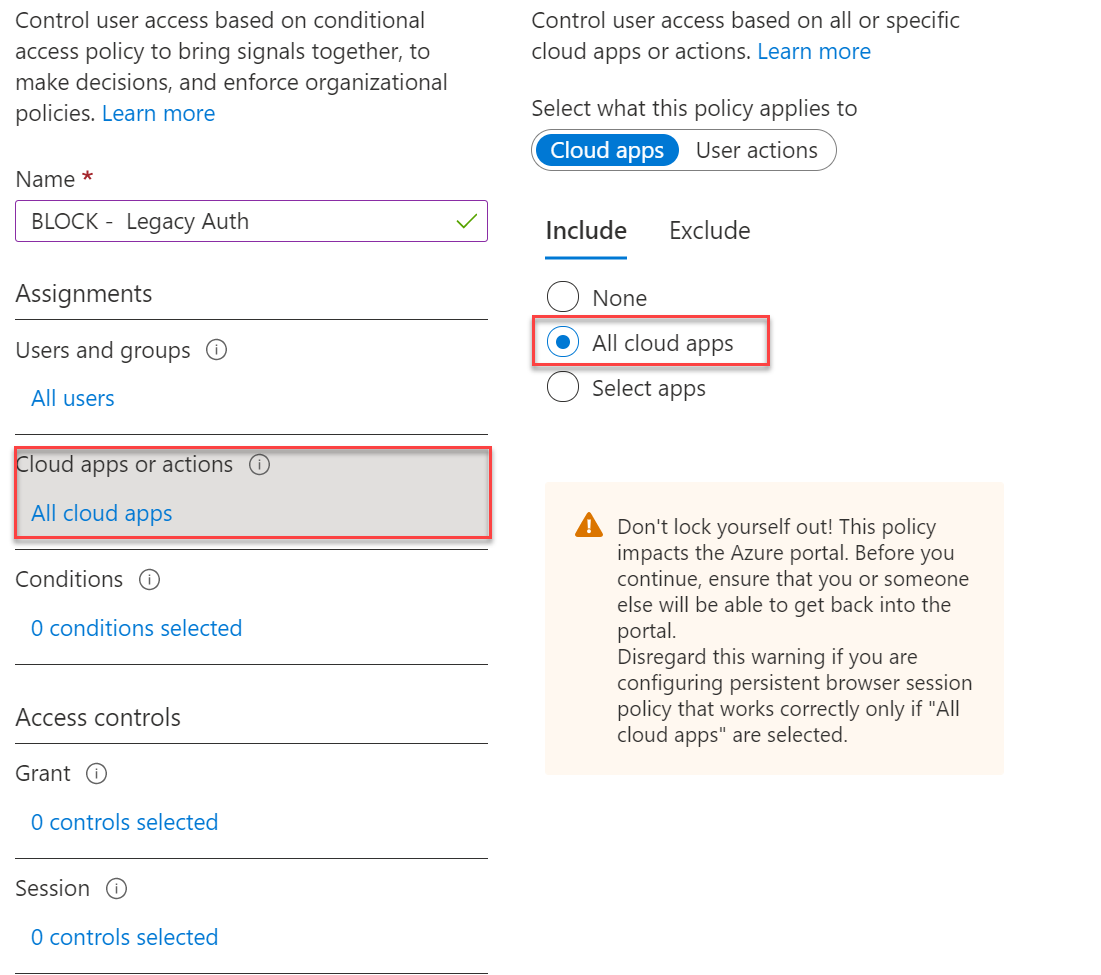
- Click on Conditions -> Clients Apps and select the value Yes and only both Legacy Clients.

Now you’re ready to configure the policy. The advice is to start with the report-only mode and check first the blocked sign-ins.
Security Defaults
For smaller organizations, the option is using Security Defaults. This gives your users basic protections with Multi-factor authentication and some basics like disabling legacy authentication.

Wrap things up
The general tenant block for legacy authentication is postponed multiple times due to the current COVID-19 crisis. The vision from Microsoft is clear, legacy authentication is going to be disabled on all tenants. Now with all the information it is a good idea to start the reporting and blocking actions.
Start small and analyze all the reports. With the report-only mode there is no impact for the users and you have the option to see the impact with the workbooks feature. Of course you can always start with a small pilot group for disabling legacy authentication.
From a security vision, legacy authentication is still the most compromising sign-in. And the biggest risk, modern authentication can not be used for legacy protocols. Legacy authentication does not support multi-factor authentication (MFA).
Now the most common question; Q: He security admin: I have enabled MFA for all users. A: Nice Job. Now the real answer; Hackers can still brute force passwords using older protocols without any modern authentication. 😉
Sources
Microsoft: Basic Authentication and Exchange Online – February 2021 Update
Microsoft: Legacy authentication protocols




