File Integrity Monitoring (FIM) is a technology that monitors and detects file changes that could be indicative of a cyberattack. File Integrity Monitoring is part of Defender for Servers P2 and enables monitoring of operating system files, Windows Registry, Application Software files, and Linux system files for changes that might indicate an attack or configuration change. FIM is a core requirement in many compliance standards like PCI-DSS, NERC CIP, FISMA, SOX, NIST, and HIPAA.
| Blog information: Blog published: September 20, 2022 Blog latest updated: September 20, 2022 |
Introduction File Integrity Monitoring
As already explained shortly in the introduction above. File Integrity Monitoring (FIM) is a security process that monitors and analyzes the integrity of critical assets and locations. Changes in critical structures can indicate signs of tampering or corruption, which can be used as an indication of a cyberattack.
FIM monitors all file modifications that are located on databases, servers, applications, network devices, directory servers, and cloud environments. And delivers information about how, why, when, and more detailed information.
FIM is not only useful during cyberattacks. Some changes made by administrators or employees can enable risk to the organizations. With the use of FIM it is possible to identify vulnerabilities and fix them before they can be exploited.
File Integrity Monitoring (FIM) helps you to monitor the Windows registry and files of operating systems such as Windows and Linux application software and all the changes that might indicate a cyberattack/ misconfiguration.
Start with the inventory
The first step in securing the systems and enabling File Integrity Monitoring is the inventory of available assets and sensitive locations of servers/ custom applications and other important corporate locations (databases/ custom applications/ log files/ configuration files). Avoid a complex starting point with a complex large rule set.
Create a baseline with the files/ locations that will fall under the created FIM policy. A documented policy overview provides information for IT/ Security professionals of the file is legitimate.
File Integrity Monitoring in Defender for Cloud
Microsoft Defender for Servers is one of the plans provided by Microsoft Defender for Cloud and provides FIM.
Defender for Servers provides two plans:
- Defender for Servers Plan 1
- Defender for Servers Plan 2
Plan 1 supports integration with Defender for Endpoint Plan 2, Threat Vulnerability management with MDE, and enables automatic onboarding. For the additional enhanced security features, Plan 2 is needed.
| Feature/Capability | Defender for Servers Plan 1 ($ 5) | Defender for Servers Plan 2 ($ 15) |
|---|---|---|
| Microsoft Defender for Endpoint P2 | ✅ | ✅ |
| Microsoft threat and vulnerability management | ✅ | ✅ |
| Automatic agent onboarding, alert, and data integration | ✅ | ✅ |
| Just-in-time VM access for management ports | ❌ | ✅ |
| Network layer threat detection | ❌ | ✅ |
| Adaptive application controls | ❌ | ✅ |
| File Integrity monitoring | ❌ | ✅ |
| Adaptive network hardening | ❌ | ✅ |
| Integrated vulnerability assessment ( Qualys) | ❌ | ✅ |
| Free 500MB Log Analytics data ingestion | ❌ | ✅ |
Defender for Cloud and Defender for Endpoint is explained here more in-depth. Microsoft Defender for Endpoint series – Onboard using Defender for Cloud – Part3B
Enable Defender for Servers Plan 2
File Integrity Monitoring (FIM) is part of Defender for Servers Plan 2. Enablement of Defender for Servers is possible directly in Defender for Cloud.
- Sign in to the Azure portal
- Search for Microsoft Defender for Cloud
- In Defender for Cloud, select Environment settings

- Open the subscription
- Enable Defender for Servers in the Defender plans setting view

When enabling Defender for Servers make sure Plan 2 is enabled. When Plan 2 is not visible in the pricing select Change plan and select Defender for Servers Plan 2. Defender for Servers will be activated for all supported resources in the subscription.
Deploy Azure Monitor Agent (AMA)
Since September 2022 it is finally possible to use the new Azure Monitor Agent for File Integrity Monitoring. Which removes the previous complexity with the Microsoft Monitoring Agent (MMA). When possible start the migration from MMA to AMA where the latest version of AMA enables way more features and improvements. For using File Integrity Monitoring it is needed to deploy the Azure Monitor Agent (AMA).
NOTE: Auto provision of the Azure Monitoring Agent is currently in public preview. When needed Microsoft Monitoring Agent can be used (previous solution).
Prerequisites
For configuring auto provisioning via Defender for Cloud the following prerequisites are important:
- For multi-cloud and on-premises machines configure Azure Arc
- Enable Defender for Servers Plan 2
Deploy Azure Monitor Agent using auto provisioning wizard
Deployment of the Azure Monitor Agent is possible with the use of auto-provisioning. Auto-provisioning can be enabled directly in Defender for Cloud. Auto provisioning reduces the overhead by installing required agents and extensions.
- Go to Defender for Cloud and open Environment settings
- Select the relevant subscription
- Open the Auto provisioning page

Configure the extension: Log Analytics agent/ Azure Monitor Agent. When you enable auto-provisioning, Defender for Cloud decides which agent to provision based on the configuration in the environment. The configuration can be changed where the AMA agent (preview) can be configured as default agent type. For changing the configuration select Edit configuration and select Azure Monitor Agent (preview).

Workspace configuration
When installing the Azure Monitor Agent with auto provisioning, you can define the default destination workplace of the installed extension. By default; Microsoft creates a default workspace that will be enabled for each region in the subscription. Default workspaces are configured in the following name convention: defaultWorkspace-<subscriptionId>-<regionShortName>
For configuring custom workspace; select Custom workspace and select the created Log Analytics workspace.

Important
When using custom Log Analytics Workspaces in combination with Defender for Cloud it is required to enable the additional workspace solutions. Microsoft installs the additional workspace solutions only for the default workspaces created by Defender for Cloud.
The required workspace solutions are needed for the following products:
- Security posture management (CSPM) – SecurityCenterFree solution
- Defender for Servers Plan 2 – Security solution
More information: Configure custom destination Log Analytics workspace
Enable File Integrity Monitoring with AMA
File Integrity Monitoring uses the Azure Change Tracking solution to track and identify changes. With the use of the Defender for Cloud recommendations, FIM can be enabled.
- Go to Defender for Cloud
- Open Recommendations
- Search for Enable File Integrity Monitoring with AMA
Prerequisites
- ChangeTracking-Windows or ChangeTracking-Linux extension
- Azure Monitor agent installed
Enabling using recommendations
Part of Defender for Cloud is the recommendation: File integrity monitoring should be enabled on machines

For validating of the Azure Monitor agent is correctly installed – view the recommendation and click on Not applicable resources. Reasons explain why the resource is not applicable. Azure Monitor agent, a prerequisite for this feature, is missing.

Under unhealthy resources, all affected resources can be selected for enabling File Integrity Monitoring. Select fix and confirm the fix for enabling FIM using the built-in remediation.

The recommendation fix applies the following items automatically:
- Installs ChangeTracking-Windows/ ChangeTracking-Linux extension
- Creates data collection rule for the subscription with the name Microsoft-ChangeTracking-[subscriptionId]-default-dcr
- Creates Log Analytics workspace with the following name convention defaultWorkspace-[subscriptionId]-fim in the resource group Fim-DataCollectionRules
Log Analytics workspace can be viewed in the Log Analytics Workspaces overview.

ChangeTracking-Windows extension can be validated using the Extensions + Application screen of the VM in Azure.

Change Data Collection Rules (DCR)
FIM uses Data Collection Rules for defining the list of files and registry keys to track. Each subscription has a DCR for the configured machines in the subscriptions. When enabling FIM there is a default configuration enabled.
An overview of the available DCR rules is visible in the DCR view.
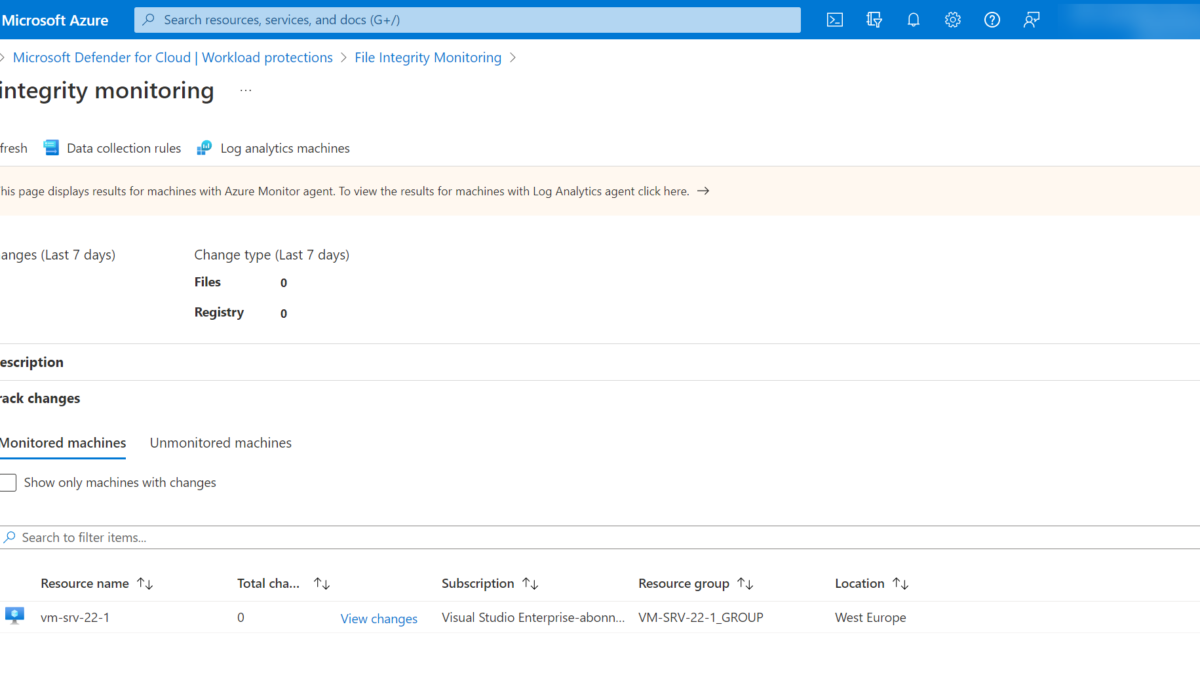
File Integrity Monitoring is visible via the following path; Defender for Cloud -> Workload protections and open File Integrity Monitoring.

The default page shows the Log Analytics Agent version. Open the link in the informational wizard for the specific Azure Monitoring Agent view or use the direct link; File integrity monitoring – Microsoft Azure

The File Integrity Monitoring main page for Azure Monitor agent results shows the total changes in the last 7 days and change types. All connected machines are visible under the Monitored machines tab.

Open Data collection rules for viewing the configured Data collection rules.

The FIM data collection rules page contains all configured data collection rules as part of the FIM enablement.

When opening the DCR rules all pre-configured rules are visible for the Windows registry/ Windows files and Linux files.

Add new rules
New rules can be added using the Add Windows registry/ Add Windows files/ Add Linux files button.

The following properties are available for adding new DCR rules for Windows files and registry. Please note that if recursion is enabled for Windows Files, then the path must contain a wildcard at the end of the configured path(*).
File – Windows
| Property | Description |
|---|---|
| Enabled | True if the setting is applied, and False otherwise. |
| Item Name | Friendly name of the file to be tracked. |
| Group | A group name for logically grouping files. |
| Enter Path | The path to check for the file, for example, c:\temp\*.txt. You can also use environment variables, such as %winDir%\System32\\\*.*. |
| Path Type | The type of path. Possible values are File and Folder. |
| Recursion | True if recursion is used when looking for the item to be tracked, and False otherwise. |
| Upload file content | True to upload file content on tracked changes, and False otherwise. |
Registry – Windows
| Property | Description |
|---|---|
| Enabled | True if a setting is applied, and False otherwise. |
| Item Name | Friendly name of the registry key to track. |
| Group | Group name for logically grouping registry keys. |
| Windows Registry Key | Key name with path, for example, |
More information: Manage Change Tracking and Inventory in Azure Automation | Microsoft Learn
Notifications and change events
FIM informs in the following cases:
- File and registry key creation or removal
- File modification (changes in file size, access control lists, hash of the content)
- Registry modifications (changes in size, access control lists, type, content)
Changes can be validated using the File Integrity Monitoring page via File integrity monitoring – Microsoft Azure for the Azure Monitor agent or directly via KQL on top of the Log Analytics workspace.

Hunt for changes
KQL can be used for hunting configuration changes in the pre-created FIM Log Analytics workspace. Example KQL query for Files and registry changes:
ConfigurationChange
| where Computer == "<hostname>"
| where ConfigChangeType in("Files", "Registry")
| order by TimeGenerated
Conclusion
Microsoft migrates more features from the previous Microsoft Monitoring Agent (MMA). With the support for AMA and DCR rules – the roll-out for DCR rules will be more simplified.
File Integrity Monitoring, is about keeping track of change from an established baseline and alerting you to any unexpected change that may result in a security risk or a compromise in compliance.
Some usecases for FIM;
- Detecting early stage of a complex cyberattack (changing important files)
- Identifying weaknesses in IT infrastructure ( Changes by IT/ Admin) which result in exploits
- Compliance reasons (HIPAA, GDPR, ISO 17799 and PCI DSS, and many more)
Sources
Microsoft: Enable File Integrity Monitoring (Azure Monitor Agent) | Microsoft Learn
Microsoft: Manage Azure Automation inventory collection from VMs | Microsoft Learn
Microsoft: Track changes to system files and registry keys | Microsoft Learn