Content updated: 29 March 2021. Changes or newer versions can be released by Microsoft.
Microsoft Defender for Endpoint supports more platforms. Since 2020 Defender for Endpoint is available for Linux systems. Recently Microsoft announced the behavior monitoring preview feature for Linux. This blog is about all the parts of Defender for Endpoint on Linux systems, focussed on the new behavior monitoring and detection part.
Defender for Endpoint on Linux
Microsoft extends the endpoint security capabilities from only Windows to macOS, Linux, Android, and iOS. With the Defender for Endpoint solution, it is possible to protect all the different platforms.
With Microsoft Defender for Endpoint, customers benefit from a unified view of all threats and alerts across Windows and non-Windows platforms.
First of all the requirements for the Linux onboarding part.
Requirements
Supported Linux server distributions and versions:
- Red Hat Enterprise Linux 7.2 or higher
- CentOS 7.2 or higher
- Ubuntu 16.04 LTS or higher LTS
- Debian 9 or higher
- SUSE Linux Enterprise Server 12 or higher
- Oracle Linux 7.2 or higher
Kernel and audit
- Minimum kernel version 3.10.0-327
- Fanotify kernel option must be enabled
- Auditd must be enabled
Disk space:
- 1GB minimum disk space
Network
- Network connector to separate URLs
What is EDR / Behavior monitoring?
The protection for Linux is based on EDR detections. Most AV solutions will just look at known hashes for files and processes. EDR is more advanced and looks at memory, processes, network traffic and more advanced detections.
Since last week the Linux antivirus platform is supporting behavior monitoring capabilities. At the moment behavior monitoring and blocking are available as public preview for the supported Linux.
Microsoft announced EDR for Linux as:
The new preventive antivirus functionality complements our existing strong content-based capabilities with behavior monitoring and deep memory scanning. These enhancements bring immediate ability to closely monitor processes, file system activities, and process interactions within the system. The enhanced ability to correlate events and behaviors across multiple processes allows us to more generically detect and block malware based on their behavioral classification. These behavior-based signals will act as additional runtime signals for behavioral cloud-powered machine learning models and for effective runtime protection.
The preview is at the moment supported by the following Linux distributions: Note; all supported Linux platforms for MDFE
- RHEL 7.2+,
- CentOS Linux 7.2+
- Ubuntu 16 LTS, or higher LTS
- SLES 12+
- Debian 9+
- Oracle Linux 7.2+
For the behavior part, make sure the device contains the following prerequisites;
- InsiderFast channel
- Defender for Endpoint version 102.25.42 or higher
- Manual enrollment in the preview future.
- More later in the blog
First onboard Linux
For onboarding Linux multiple options are available. For this blog we using a CentOS machine. Follow the steps below for the CentOS part.
Install yum-utils
if it isn’t installed yet on the device install yum-utils.
sudo yum install yum-utils
sudo yum-config-manager --add-repo=https://packages.microsoft.com/config/[distro]/[version]/[channel].repo
Replace the distro and version with the VM information. For example, if using CENTOS 7. Use the following code: In this demo example distro is replaced with centos and version with the used Linux distro version. Channel is the part where you can select the update ring. The choice of channel determines the frequency of updates. Insider-fast is the first order, followed by insider-slow and the most stable; prod.
The following channels are available:
- Insiders-fast
- Insiders-slow
- Prod
Note: Browse https://packages.microsoft.com/config/ for the explorer and data structure. Microsoft has published the MDATP Linux agents in their https://packages.microsoft.com repository.
In the case of this blog post and the usage of the behavior part, we will use the insider-fast ring. The command for CentOS 7 with the insiders-slow ring is:
sudo yum-config-manager --add-repo=https://packages.microsoft.com/config/centos/7/insiders-slow.repo

sudo rpm --import http://packages.microsoft.com/keys/microsoft.asc
yum makecache
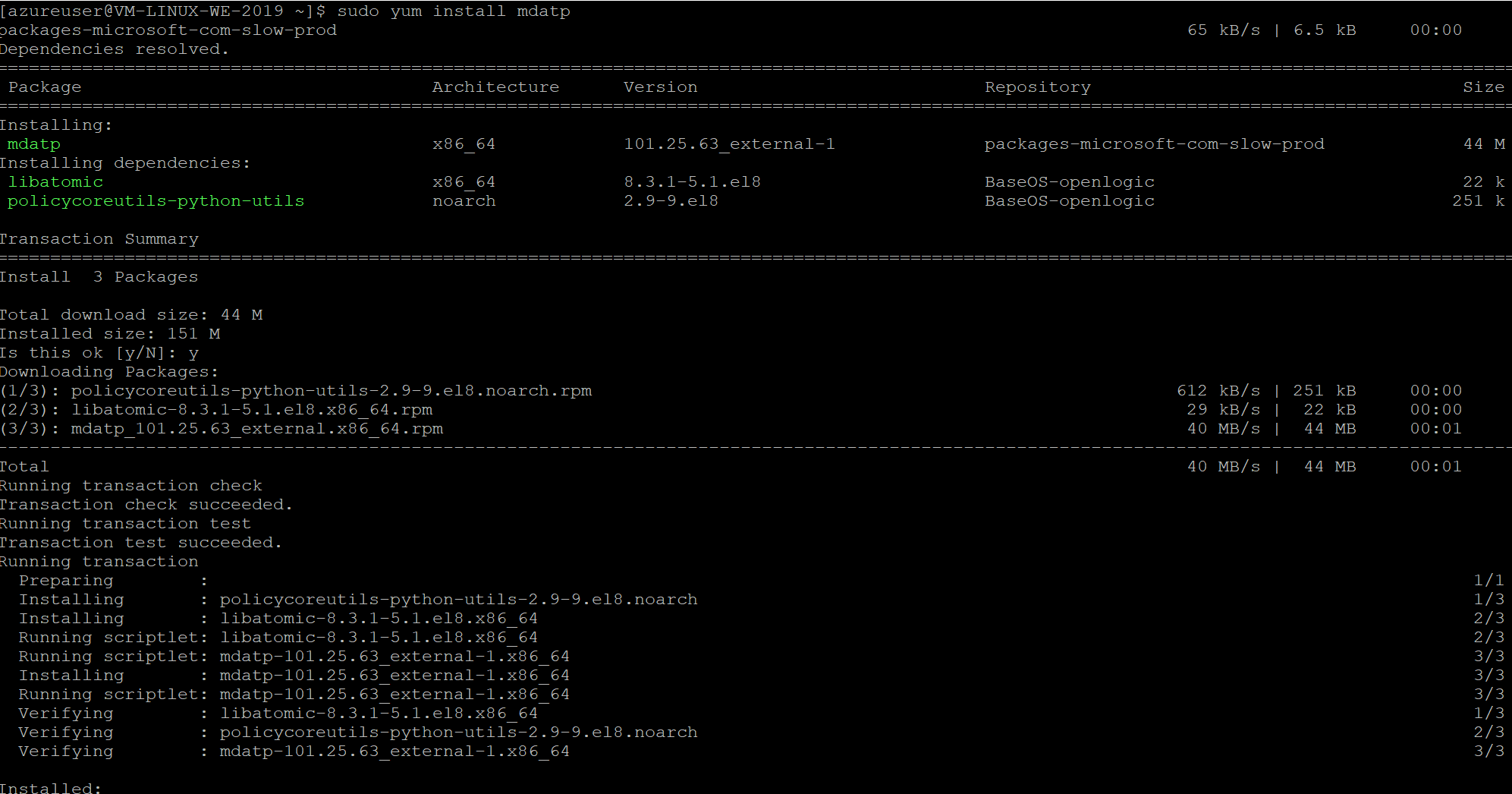
Install MDATP:
See https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/linux-install-manually for detailed instruction for distributions like SLED, Redhat etc. For CentOS use the following command to install Defender for Endpoint for Linux:
sudo yum install mdatp
Onboarding Defender for Endpoint package
Now onboarding Defender for Endpoint with the Python script. First, download the onboarding package from Microsoft Defender for Endpoint portal. For downloading the onboarding package:
- Go to: Settings > Device Management > Onboarding
- Download the Linux Server onboarding file
- Save the file and copy it to the machine
- Run the python script from the server

Checking health & onboarding
mdatp health
mdatp health --field real_time_protection_enabled
mdatp health --field org_id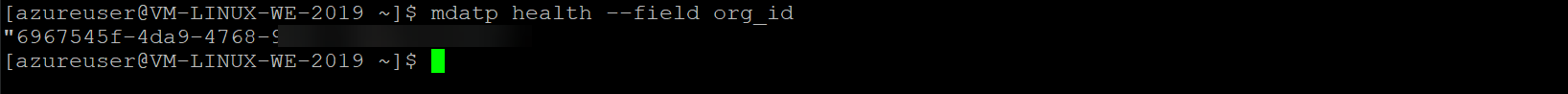
mdatp health --field definitions_status
You can use an automated bash script. View the GitHub repository for the install scripts. Of course, you can use the Puppet or Ansible deployment toolings for Linux.
The Linux machine is now onboarded to the Defender for Endpoint instance:

Test & detection
Test eicar.com test file:
curl -o ~/eicar.com.txt https://www.eicar.org/download/eicar.com.txt
In this scenario the real-time protection kicks in, and flag the download as malicious.

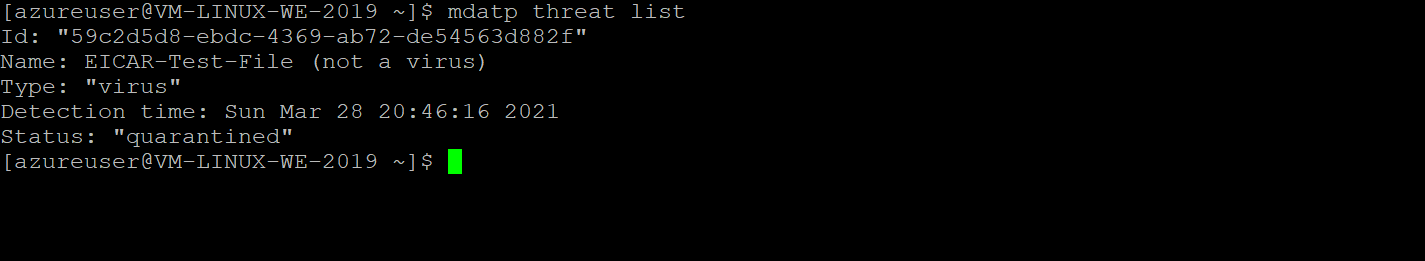
Check Quarantined actions
mdatp threat list
All the incidents are reported to the Defender Security Center portal:

And the detailed page for the eicar-test-file:
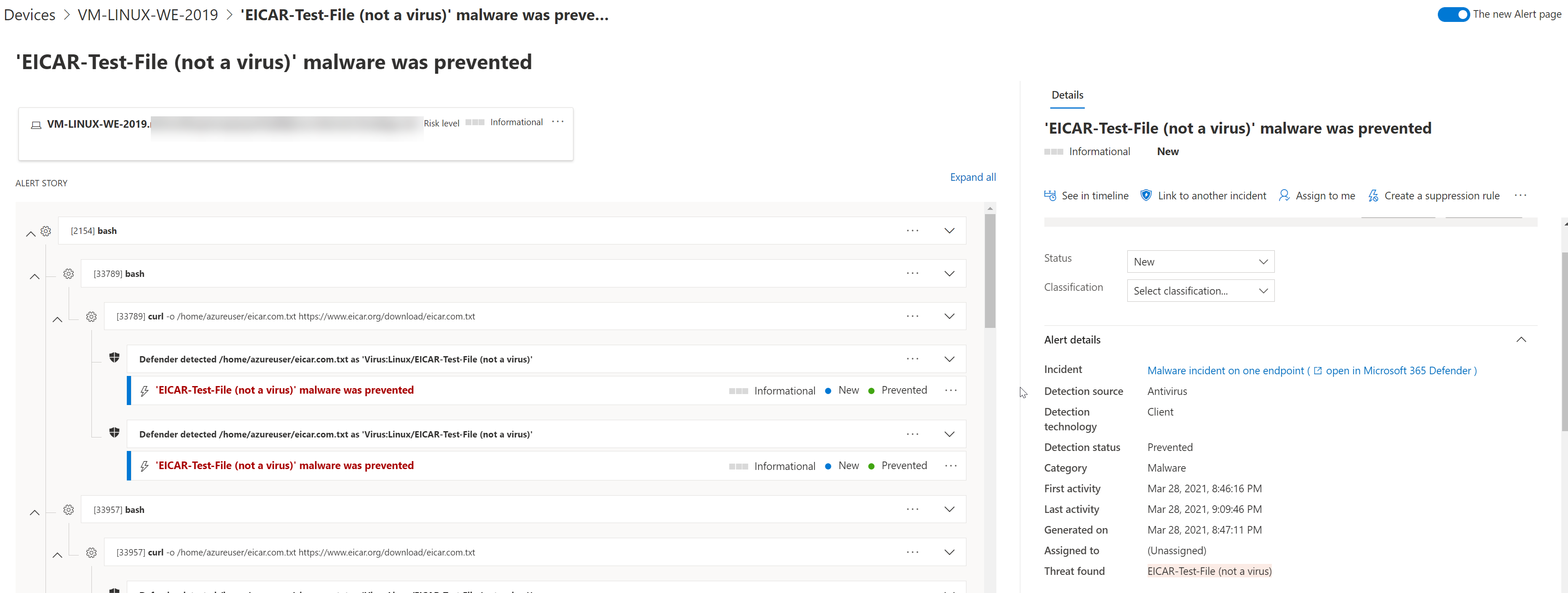
Behavior monitoring
For the behavior monitoring public preview part the following requirements are needed:
- InsiderFast channel
- Defender for Endpoint version 102.25.42 or higher
- Manual enrollment in the preview future.
Manual enrollment command
mdatp config behavior-monitoring --value enabled
Disable command
mdatp config behavior-monitoring --value disabled

For enabling the behavior monitoring part; Defender for Endpoint must be restarted.
Now make sure the cloud-delivered protection part is enabled.
mdatp health --field cloud_enabled

Behavior monitoring demo
Now the demo part for behavior monitoring. With the Do it ourself scenarios it is possible to use multiple scenarios to test the new feature. View the Microsoft source for all scenarios.
Metasploit
Note: all in this part is only for testing the behavior part. Not recommended for production systems.
Metasploit is a popular exploitation framework used by attackers. Metasploit allows attackers to generate reverse shell payloads that an attacker can execute on a remote machine to gain access to a victim machine.
First, install and configure Metasploit for the test behavior monitoring block actions.

Run the MSFVenon command:
msfvenom -p cmd/unix/reverse_python LHOST=127.0.0.1 LPORT=4444 -f raw
As you can see the Python reverse shell command is immediately killed before the attack could cause any harm to the system.
For the action checkup; use the command:
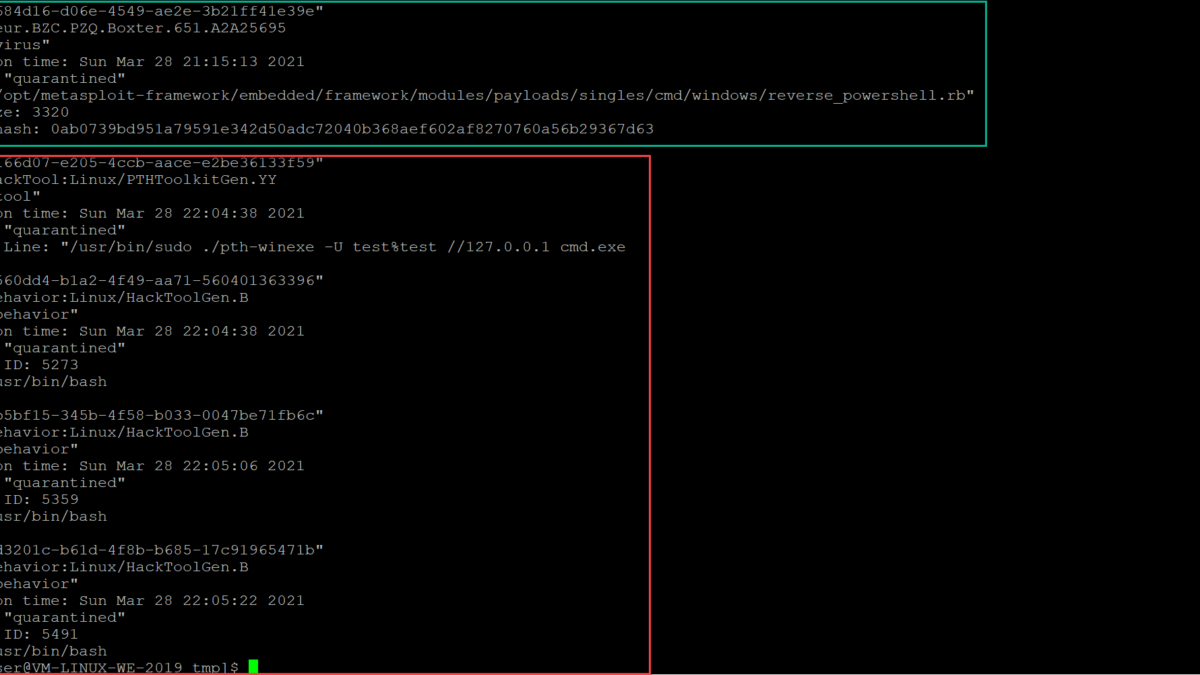
mdatp threat list
In the green the virus detection part. In red the new behavior actions.
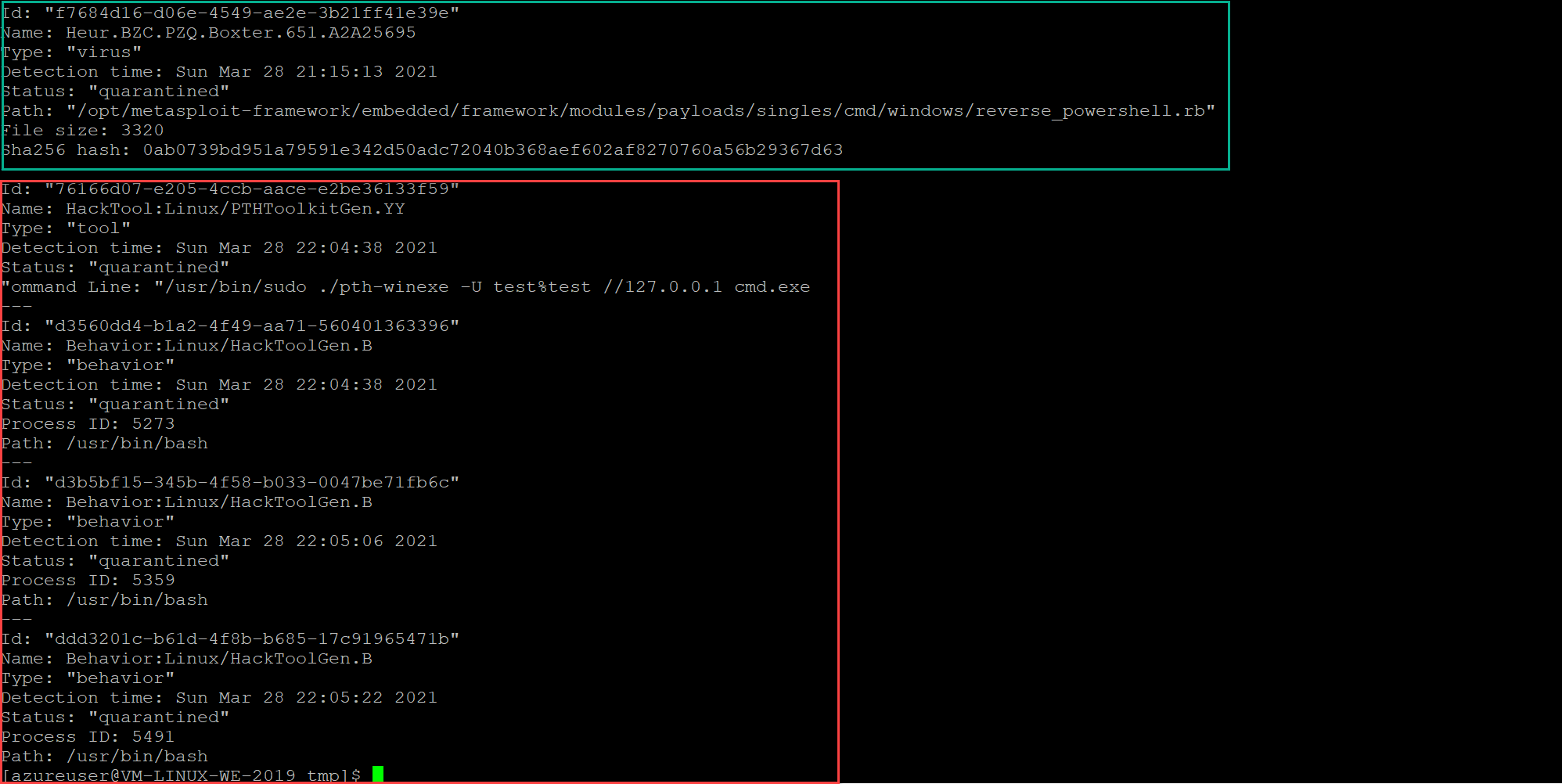
If we take a look inside the Defender for Endpoint portal. You can find detection related to the behavior.

PTHToolkitgen:
Pth-toolkit is another very popular post-compromise framework. Defender for Endpoint detects and prevent the PTHToolkitGen.


Conclusion
Microsoft Defender ATP for Linux is available in Defender for Endpoint. Microsoft releases and improves the Linux part a lot in the last months. With EDR and Behavior monitoring more enterprise protection layers can be added for protection Linux systems.
For the Linux part, more interesting blog posts in the next months. Happy hunting
Sources
Microsoft: Enhancing Linux antivirus with behavior monitoring capabilities!
Microsoft: Microsoft Defender for Endpoint for Linux