Defender for Endpoint is available for multiple platforms. For mobile platforms Defender for Endpoint is supported for iOS en Android. In this blog, I will explain the zero-touch onboarding of Defender for Endpoint for iOS.
View the updated post: Deploy Microsoft Defender for Endpoint on iOS using Intune/MEM
With zero-touch admins can configure Microsoft Defender for Endpoint to deploy and activate Defender for Endpoint silently, without any interaction from the user. The user is simply notified and all the configuration will be done automatically without any action in the permission or requirements required by the end-user.
Article updated 4 January 2022
Prerequisites
- Defender for Endpoint license assigned to the end-user. See Microsoft Defender for Endpoint licensing requirements.
- iOS device enrolled via the Intune Company Portal app
- Device registered with Azure Active Directory
- iOS 12 and above required
- MEM Requirements for IOS onboarding (MDM push certificate)
Integration with Microsoft Endpoint Manager
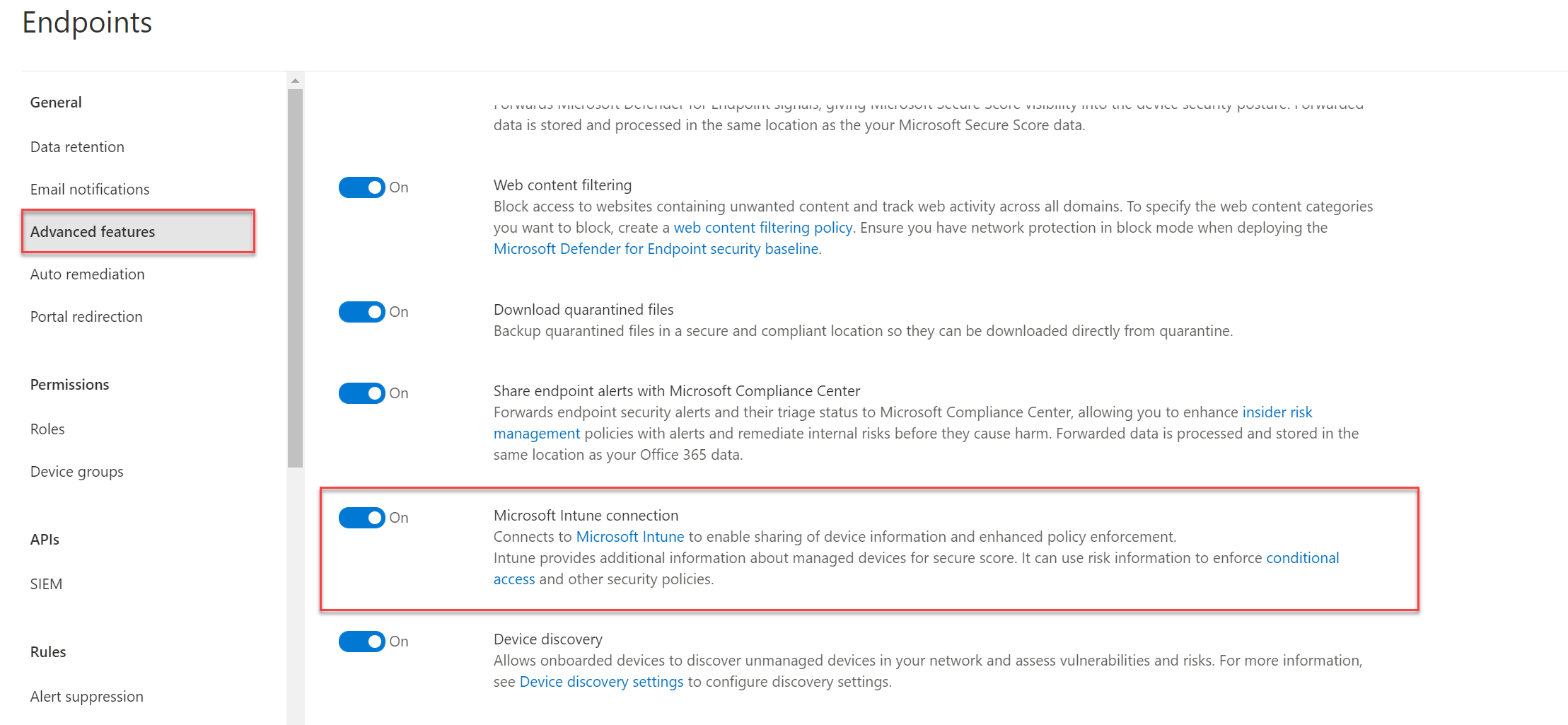
Defender for Endpoint makes it possible to integrate with Microsoft Endpoint Manager. With the integration, it is possible to share risk-level information and use it with compliance policies. The connection with Microsoft Endpoint Manager can be enabled in the Microsoft Defender Security Center portal.
- Open Microsoft Defender Security Center
- Navigate to Settings -> Advanced features
- Configure Microsoft Intune Connection.
Now we need to allow iOS devices in the Microsoft Endpoint Manager admin center. To enable the feature for IOS, follow the following steps:
- Open Endpoint Manager admin center
- Navigate to Endpoint Security -> Microsoft Defender for Endpoint
- Now configure the: Connect iOS devices to Microsoft Defender for Endpoint to On
With this feature, the compliance policy integrates with Microsoft Defender for Endpoint and can be used for blocking access to corporate data in case of threats/ risk levels.

Deployment of the Microsoft Defender for Endpoint iOS app
The Defender for Endpoint app can be deployed by using Microsoft Intune. For using zero-touch deployments it is recommended to use and integrate the deployment with MEM to silently onboard and configure the app.
- Open Endpoint Manager admin center and navigate to the apps panel.
- Now click on iOS/iPadOS
- Click Add and select the iOS Store app as App type

- Search for the app Microsoft Defender for Endpoint, select the app and click next

- Fill in the additional information if needed for the deployment profile.
- In the Assignments section, go to the Required section and select Add group. Important: The user group must be based on users and not devices.
Configuring zero-touch onboarding
The next step is configuring the iOS configuration profile for the zero-touch onboarding. With zero-touch onboarding, admins can configure the onboarding and configuration completely silent without any user interaction.
For creating the configuration profile:
- Open Endpoint Manager admin center
- Navigate to Devices -> Configuration Profiles -> Create profile
- Select the platform iOS/ iPadOS and the profile type VPN

- Fill in the custom configuration profile name
- In the configuration settings panel, it is required to configure the connection type. For Defender for Endpoint we will configure the Custom VPN connection type.

- Now it is time to configure the Base VPN and Automatic VPN configuration. For configuring the correct profile use the below settings:
Base VPN settings:
-
-
- Connection Name = Microsoft Defender for Endpoint
- VPN server address = 127.0.0.1
- Auth method = “Username and password”
- Split Tunneling = Disable
- VPN identifier = com.microsoft.scmx
- Key-Value: SilentOnboard with value to True
-
With the result:

Automatic VPN settings:
-
-
- Type of Automatic VPN = On-demand VPN
- On-demand rules: I want to restrict to Establish VPN for all domains
-
With the result:

The configuration profile can be deployed to one of the available user groups. Important to scope the profile directly to the user group and not device-based.
Result onboarding
Once the app and the configuration item are deployed the following actions will take place on the iOS devices after a successful MEM enrollment. Note: MEM onboarding is not part of this blog.
- User registered devices and installs company portal
- Devices sync apps and configurations
- Microsoft Defender for Endpoint will be silently installed and configured
- Web protection and other features will be silently configured for Defender for Endpoint
- Device onboarded into Defender for Endpoint portal
With the configuration profile and app deployed there is no need for the user to open directly the app for completing the onboarding. After some time the device is visible in the Defender for Endpoint console.
The experience is without any manual action. Directly after installing the following screen is visible in Defender for Endpoint. VPN profile is configured automatically – no user interaction is needed for completing the configuration.

Portal:
iOS device visible in Defender for Endpoint portal:

Testing web protection
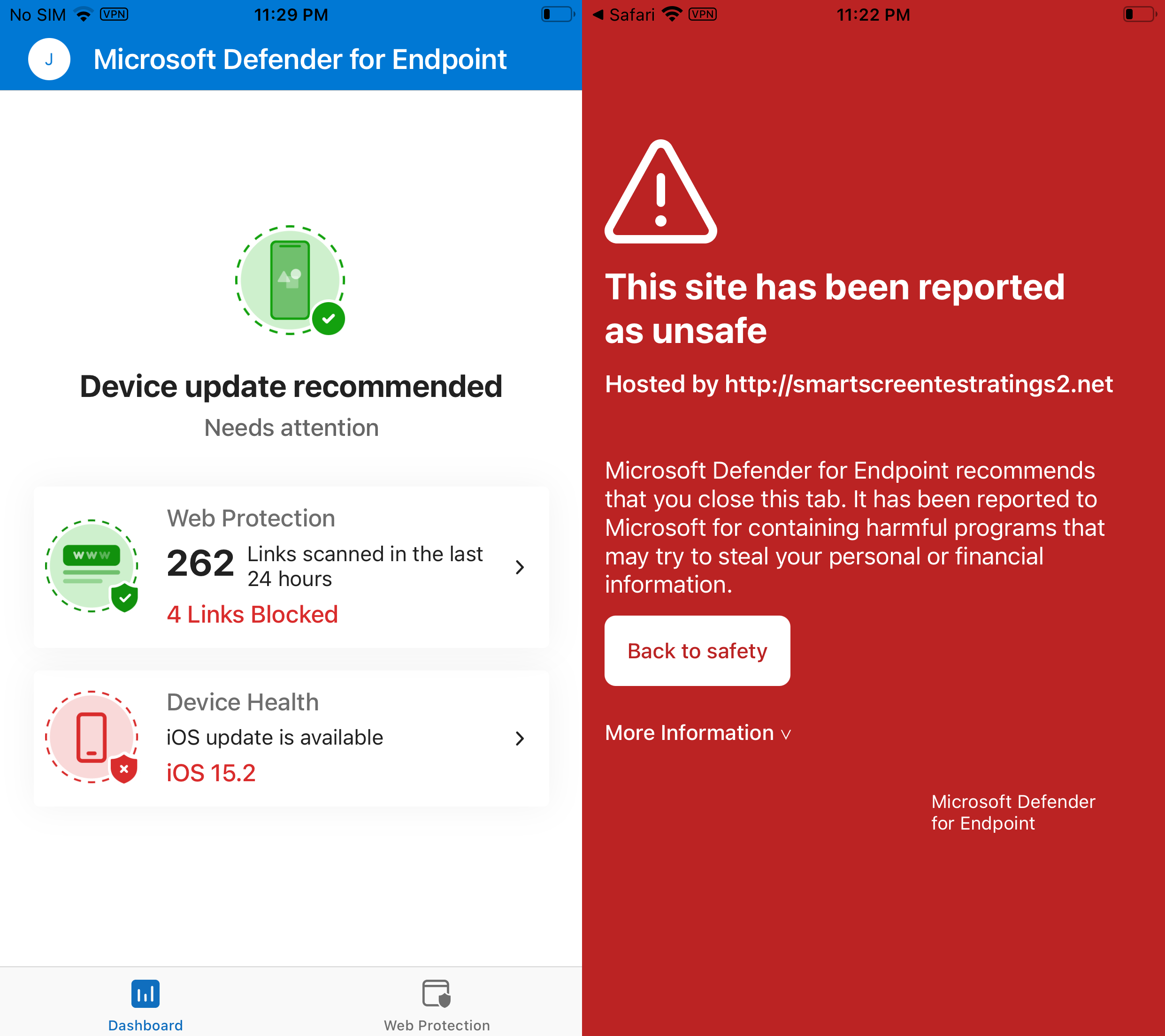
For testing Defender for Endpoint use the SmartScreen testing website. When navigating to smartscreentestratings2.net the user will receive a block message. The alert will be logged in the Microsoft Security portal.
iOS device: Testing URL: smartscreentestratings2.net Websites blocked as unsafe, MDE app shows 4 links are blocked and the total count of scanned links with web protection.
Defender portal
Alert with the name: Device tried to access a phishing site is severity informational. When the user cancels the warning – the alert severity is low with the alert title: Device connected to a phishing site after user disregarded the warning.

Alert pages show detailed information related to the outbound connection and additional network information.

Sources
For more information about MDE for iOS – below are some of the sources available:
Microsoft: Enroll iOS/iPadOS devices in Intune/MEM
Microsoft: Microsoft Defender for Endpoint for iOS




Excellent article, Thanks.
is it the same for android ??
Fantastic – thanks. Per Henrik’s comment, it’d be great if you could show us how to do this on Android.
Thanks, Android is different, blog is on the schedule for Android based MDE deployments.
The display name is not the same as the intune device name – how to correct this? it would be hard to manage/find user’s devices this way
This doesn’t seem to be working for me. I have the profile in as detailed above. There are only 12 devices to the 1300+ devices the policy is assigned to.