Credential dumping or password dump is a technique used by cybercriminals to gain access to a network. They will enter the workstation through phishing and controls through the typical way the admin uses and monitors the network to find more exposed credentials (Lateral movement). Credential dumping is the process of obtaining account login password information, normally in the form of a hash or a clear text password, from the operating system layer and software layer.
When attackers have established a foothold in a system, the main focus is to find high privileged credentials. Credentials are useful information, as they can give access to critical systems. Stealing user credentials is a key step for attackers to move laterally across victim networks. Important to protect and monitor any environment.
What is credential dumping?
Credential dumping (MITRE T1003) refers to obtaining login information from a system’s operating system and software. There are a variety of places within operating systems where credentials are stored for use in everyday operations.
The term credential dumping refers to any means of extracting or dumping user authentication credentials like usernames and passwords from a victim’s computer. This hacking technique is implemented after a computer has been breached by the attacker. Usernames and passwords are extremely valuable to cybercriminals and can be used to acquire sensitive information as well to gain more access to the complete network.
Critical parts for credential dumping are located at the memory cache or application cache. The most common tool used is Mimikatz. Mimikatz became one of the world’s most used hack tools.
Operation systems store passwords in memory, databases, or files to reduce the number of times a user is required to enter their password. Windows stores the password in the system memory/LSA Subsystems Service. Credential dumping is largely possible because operating systems stores the password in the memory to avoid the user from repeatedly entering their password.
Credential dumping can open the door to other credential-based attacks. (Pass the hash, Pass the Ticket (PTH), Kerberos Golden Ticket, Kerberos Silver Ticket).
Where to steal
There are a variety of places within operating systems where credentials are stored for use in everyday operations. With access to an endpoint the victim can look for credentials in the below locations.
- Kerberos
- Local Security Authority (LSA)
- LSA Subsystems Service (LSASS)
- Security Accounts Manager (SAM)
- WDigest (Legacy protocol)
- Registry SAM key
- ……
Toolings used
For example, the following tools can be used:
- Mimikatz
- Empire
- L0phtCrack
- gsecdump
- PWDumpX
- Creddump
- PowerSploit
- Procdump
- .Crackmapexec
- LSASSY
- ………
Common behaviors
The following behaviors are common during real-world attacks. Source: Redacanary.com
- PowerShell and other processes (e.g., Windows Task Manager and Sysinternals ProcDump) accessing and dumping memory from the Local Security Authority Subsystem Service (LSASS)
- Windows Registry Console Tool (reg.exe) exporting Windows Registry hives containing credentials
- NTDSUtil dumping NTDS.dit (Active Directory)
- Windows Credential Editor dumping NT Lan Manager (NTLM) hashes
How does a credential dump work?
Credential dumps are not difficult when there is no additional protection enabled. It all starts with access to one of the endpoints.
- A malicious actor finds a way into the device. This can be using a zero-day vulnerability, weak security/identity, legacy software, non-patched systems, or any other method.
- Now they have access and can start the credential search. During credential dump attacks, the first place the attackers will usually look is the device RAM, which stores without protection credentials in plain text. Attackers will try to attempt the Security Account Manager (SAM). SAM contains a full list of password hashes used to log into the device. (including mostly IT accounts or local admins).
- With those valid credentials (or hashes) in hand, the attackers can start lateral movement and gain more access to getting the golden key (administrator’s credentials).
Blog tip: Protecting against Lateral Movement with Defender for Identity and monitor with Azure Sentinel
Protect against credential dumping attacks
Device protection is critical to avoid credential dumping attacks. Based on default security and Defender techniques the attacks can be reduced/ blocked. Using an EDR with signature-based detections will mostly detect and block Mimikatz or credential dumping attacks.
There are a few things your organization can do to help prevent these attacks. Ideally, all end-of-life Windows operation systems should be decommissioned. Newer systems disables automatically WDigest by default for exporting plaintext passwords. For newer systems, it is still possible to dump the NTLM hashes. Another important defense is to restrict local administrative access as much as possible.
A couple of the protection capabilities which are possible;
General protection;
- Decommission all end-of live Windows Operating systems
- Restrict local administrative access
- Disable WDigest on all Windows Operating systems prior to Windows 8 and Windows Server 2012 R2
- Disable Lan Management (LM) hashes
- Limit domain and highly privileged accounts
Defender protection:
- Windows Defender Credential Guard
- Enable Defender Antivirus (AV)
- Onboard Defender for Endpoint (MDE)
- Onboard Defender for Identity (MDI) to detect possible attacks
- Enable Attack Surface Reduction Rule (ASR); Block credential stealing from the Windows local security authority subsystem
When Defender Credential Guard is correctly configured, there is no need to configure the Attack Surface Reduction rule. Credential Dumping is already blocked as part of the Credential Guard configuration.
Simulations
Before switching to some of the technical explanations, let’s start with some credential dumping attack examples. For simulations dumping credentials using Mimikatz or other hack tools use some searches to find other blogs.
Simulation #1 Dump credentials using Task Manager
If the victim has Remote Desktop Protocol (RDP) or other GUI access to the device, the Windows Task Manager can be used for creating a dump file of the LSASS memory.
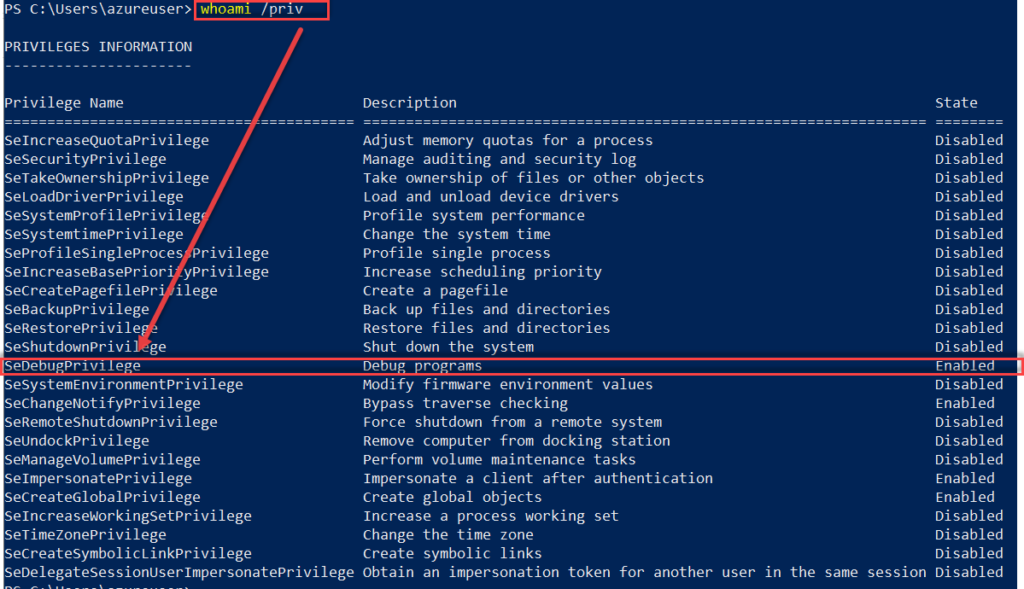
In order to dump LSASS as an attacker, it is necessary to have the SEDebugPrivilege. The default Windows setting is to grant this privilege to local administrators. The permissions can be easily checked by using the following command: whoami /priv
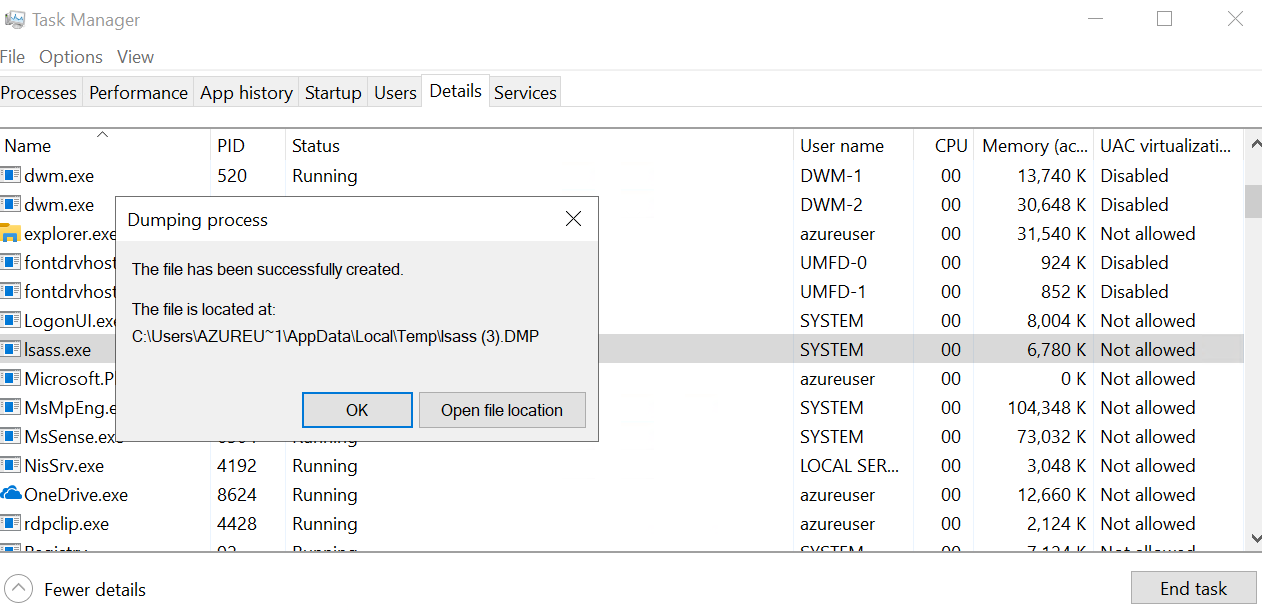
From the Task Manager, go to the Details tab, find lsass.exe, right-click, and select Create dump file:
This will create directly a dump file located in the AppData\Local\Temp directory of the user.
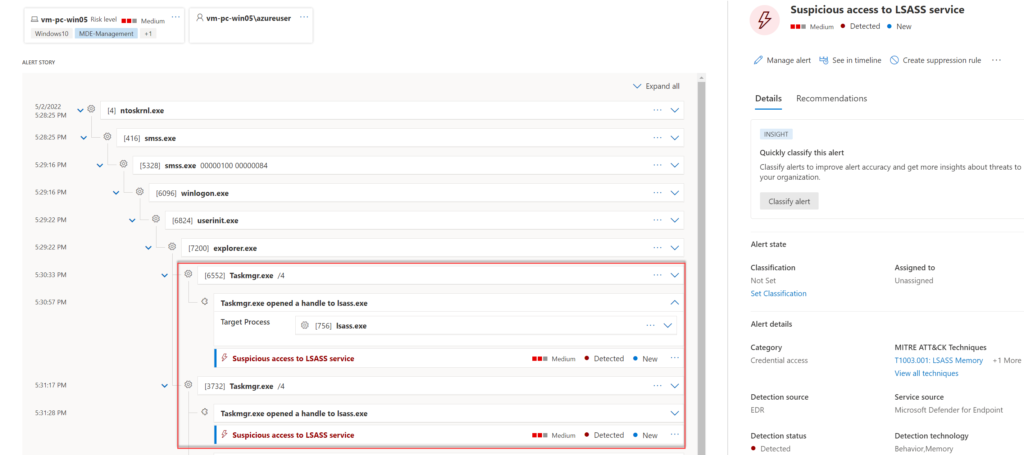
Without any additional protection, Defender for Endpoint is detecting suspicious access to the LSASS service.
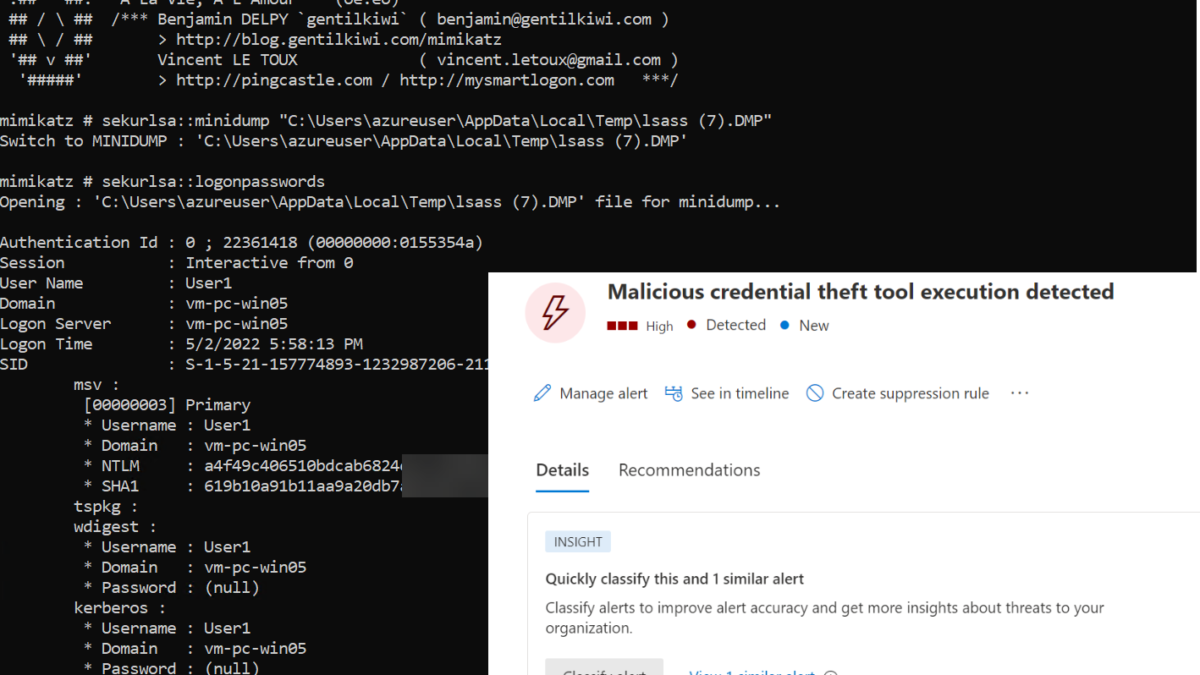
You can then use multiple tools ( Mimikatz/ pypykatz ) to extract any stored credentials and hashes from the dump file. For example switch to mimikatz context to read the minidump file.
sekurlsa::minidump C:\Users\ADMINI~1.OFF\AppData\Local\Temp\lsass.DMP
sekurlsa::logonpasswords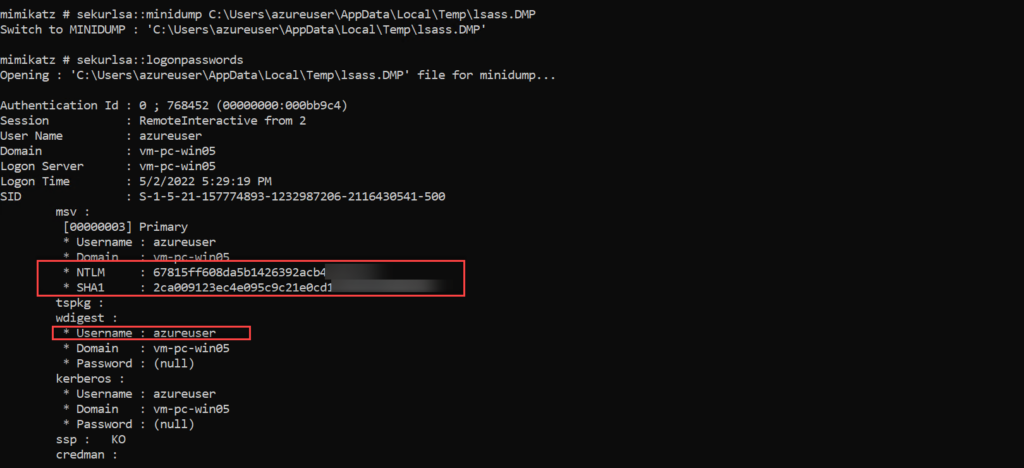
As you can see, we got NTLM hashes of all active users. The command was successful because the Debug Mode is enabled (Default Behaviour). In the SeDebugPrivilege mode programs can get low-level memory access.
Simulation #2 Dump credentials using Procdump
Procdump from Sysinternals can be used to create memory dumps of the LSASS process. Procdump is a Windows Sysinternals tool.
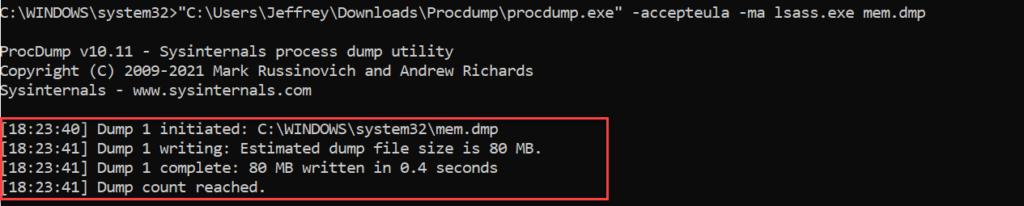
Use the below syntax for creating a memory dump of the LSASS using Procdump. Notice: This process will be blocked by Defender AV.
procdump.exe -accepteula -ma lsass.exe memresult.dmpWithout any additional protection, Defender for Endpoint is preventing the execution of DumpLsass part of the Procdump.
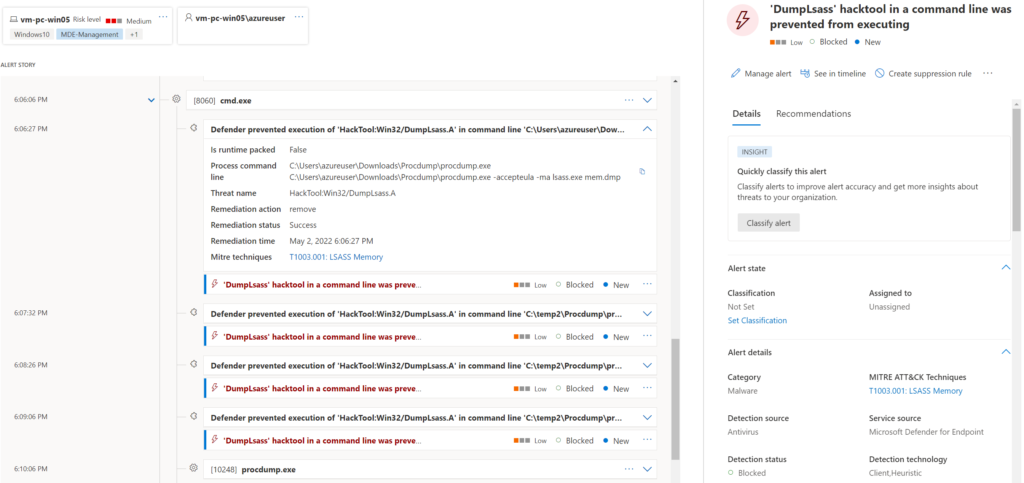
Without any protection the following is visible;
Simulation #3 Dumping LSA Secrets
LSA Secrets are stored in the following registry path;
HKEY_LOCAL_MACHINE\SECURITY\Policy\SecretsLSA secrets can be dumped directly from registry hives. Normal this behavior is already blocked by Defender for Endpoint.
reg save HKLM\SYSTEM system & reg save HKLM\security securityOf course, more ways are available for exporting credentials. Recommended read:
- ired.team: Credential Access & Dumping
- Whiteoaksecurity: Attacks & Defenses: Dumping LSASS With No Mimikatz
Prevention #1 Disabling WDigest
If you have any outdated Windows operating systems (prior to Windows 8 and Windows Server 2012 R2), WDigest is enabled by default and should be disabled directly via Group Policy. When it is enabled, Lsass.exe retains a copy of the user’s plaintext password in memory, where it can be at risk of theft.
For disabling WDigest install Windows patch KB2871997 and configured below registry key to the value 0.
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest\UseLogonCredentialPrevention #2 Enable ASR
Attack Surface Reduction is available for Windows 10 and higher, Server 2012R2, Server 2016, Server 2019, and higher. Block credential stealing from the Windows local security authority subsystem blocks untrusted processes from having direct access to LSASS memory (lsass.exe).
Important: The default state for the Attack Surface Reduction (ASR) rule “Block credential stealing from the Windows local security authority subsystem (lsass.exe)” will change from Not Configured to Configured and the default mode set to Block.
Microsoft Defender Credential Guard in Windows prevents attempts to extract credentials from LSASS. Credential Guard gives sometimes issues with hardware support. Enabling the specific Attack Surface Reduction rule can reduce the impact when hardware requirements are not passed.
Result when enabled
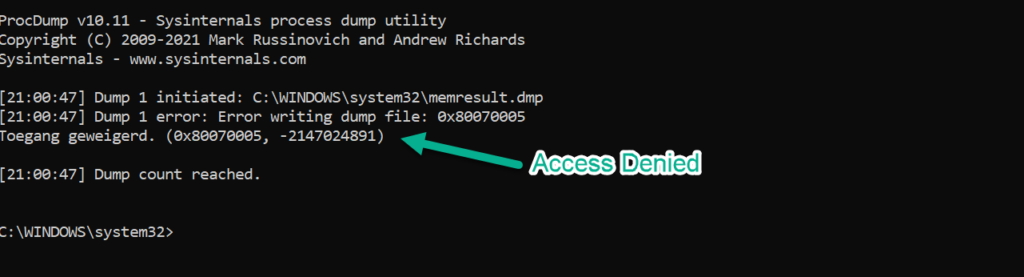
When enabled it is not possible to dump the credentials using tools or using the Task Manager.
Result using Sysinternals / Procdump. Toegang geweigerd=Access Denied
How to enable ASR?
Attack Surface Reduction can be enabled using GPO, PowerShell, MEM/Intune, or MECM. Always recommended to start for some days in audit mode before enabling the complete rule.
Information Microsoft for all ASR deployment options: Enable Attack Surface Reduction Rules
Intune
Attack Surface Reduction can be enabled using Intune. Multiple configuration methods for ASR are currently available using Intune:
- Endpoint Security – Attack Surface Reduction
- Endpoint Security – Security baselines/ Attack surface reduction rules
- Configuration profiles – Templates/ Endpoint Protection
- Configuration profiles – Settings catalog
Endpoint Security – Attack Surface Reduction policies are recommended.
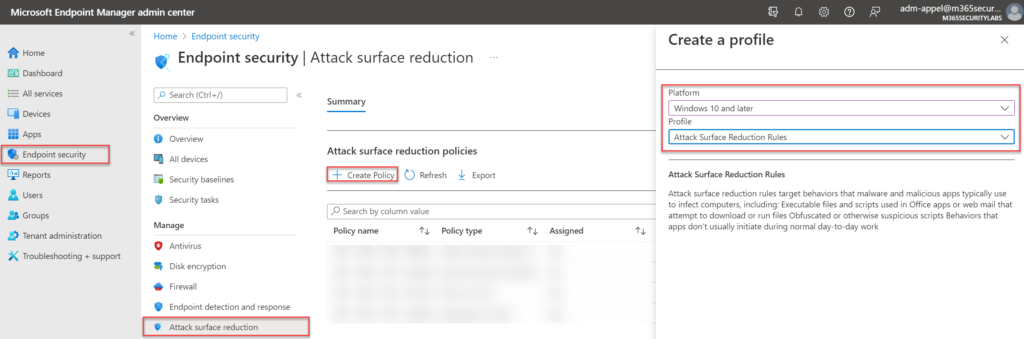
For configuring Attack Surface Reduction using the Endpoint Security profiles open the Endpoint Manager portal and navigate to Endpoint Security -> Attack surface reduction. Create a new Attack Surface Reduction Rules profile for the Windows 10 and later profile.
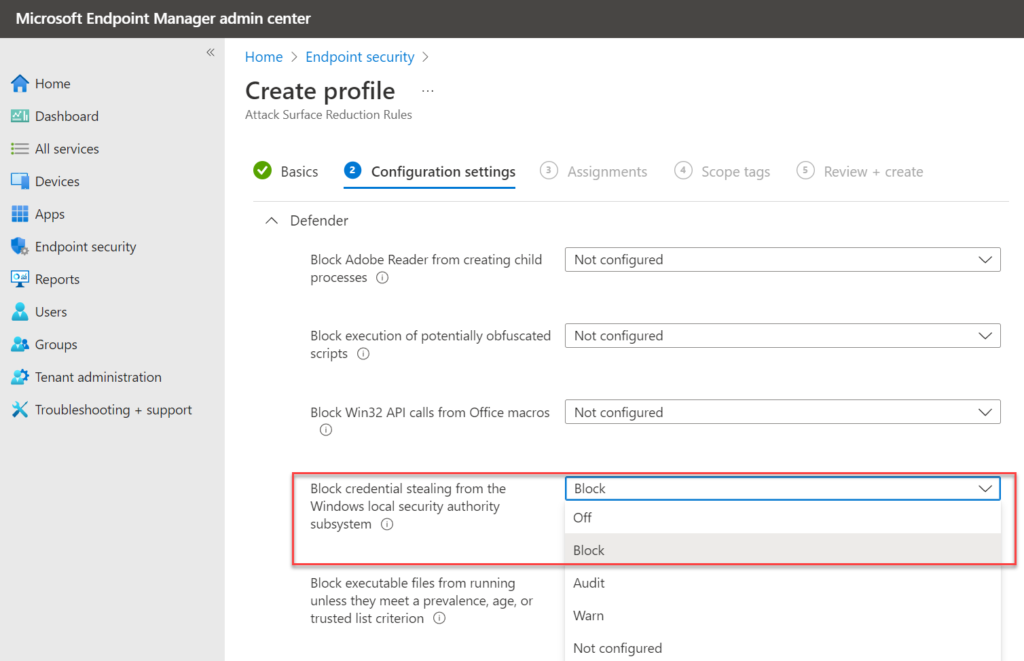
Enable the following rule: Block credential stealing from the Windows local security authority subsystem.
PowerShell
Enablement using PowerShell is possible with the Set-MpPreference module. 9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2 is the correct ID.
## block mode
Set-MpPreference -AttackSurfaceReductionRules_Ids 9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2 -AttackSurfaceReductionRules_Actions Enabled
## audit mode
Set-MpPreference -AttackSurfaceReductionRules_Ids 9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2 -AttackSurfaceReductionRules_Actions AuditMode
Review events
Defender for Endpoint Advanced Hunting can be used to view all events which are audited or blocked.
## audit events
DeviceEvents
| where ActionType == "AsrLsassCredentialTheftAudited" and Timestamp > ago(7d)
## block events
DeviceEvents
| where ActionType == "AsrLsassCredentialTheftAudited" and Timestamp > ago(7d)
## summarize by ParentProcess
DeviceEvents
| where ActionType == "AsrLsassCredentialTheftAudited" and Timestamp > ago(7d)
| project BlockedProcess=FileName, ParentProcess=InitiatingProcessFileName, DeviceName
| summarize MachineCount=dcount(DeviceName), RuleHits=count() by BlockedProcess, ParentProcess
| sort by MachineCount desc
Prevention #3 Defender Credential Guard
Microsoft Defender Credential Guard uses virtualization-based security to isolate and protect secrets (e.g., NTLM password hashes and Kerberos ticket-granting tickets) to block pass-the-hash or pass-the-ticket (PtH) attacks.
Credential Guard uses virtualization-based security to isolate secrets/ credentials. So that only privileged systems can access them.
Microsoft Defender Credential Guard uses virtualization-based security to isolate and protect secrets (e.g., NTLM password hashes and Kerberos ticket-granting tickets) to block pass-the-hash or pass-the-ticket (PtH) attacks.
Credential Guard can be enabled using Group Policy, Intune, and Registry. Credential Dumping is already blocked as part of the Credential Guard configuration.
Blog focussing on Credential Guard is coming to explain Credential Guard more in-depth.
Intune
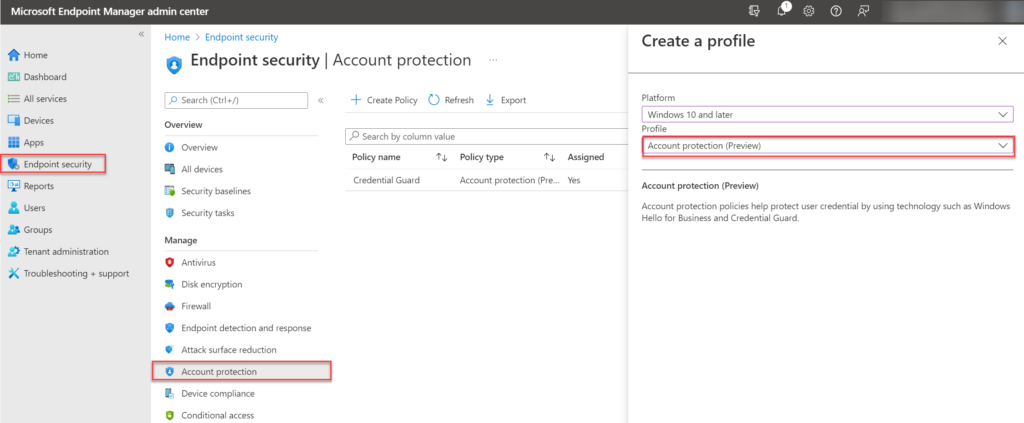
Attack Surface Reduction can be enabled using Intune. Many options are currently available for enabling Defender Credential Guard. For enabling using the new Account protection (preview) policy.
For configuring Credential Guard using the Endpoint Security profiles open the Endpoint Manager portal and navigate to Endpoint Security -> Account protection. Create a new Account protection profile.
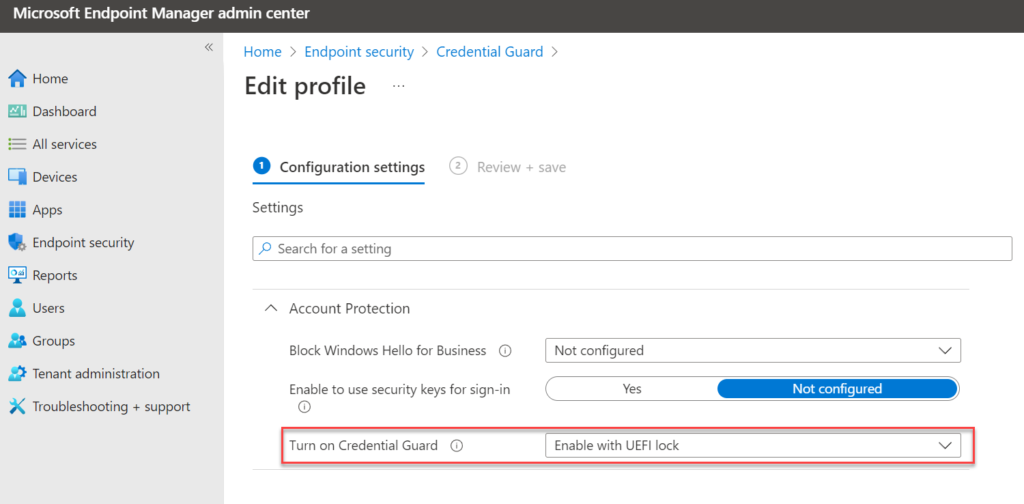
Enable the following setting Turn on Credential Guard and configure the value; Enable with UEFI lock. When configured UEFI lock the only method to disable Credential Guard is by setting this configuration to disabled and clearing the UEFI physically. Best practice in terms of security.
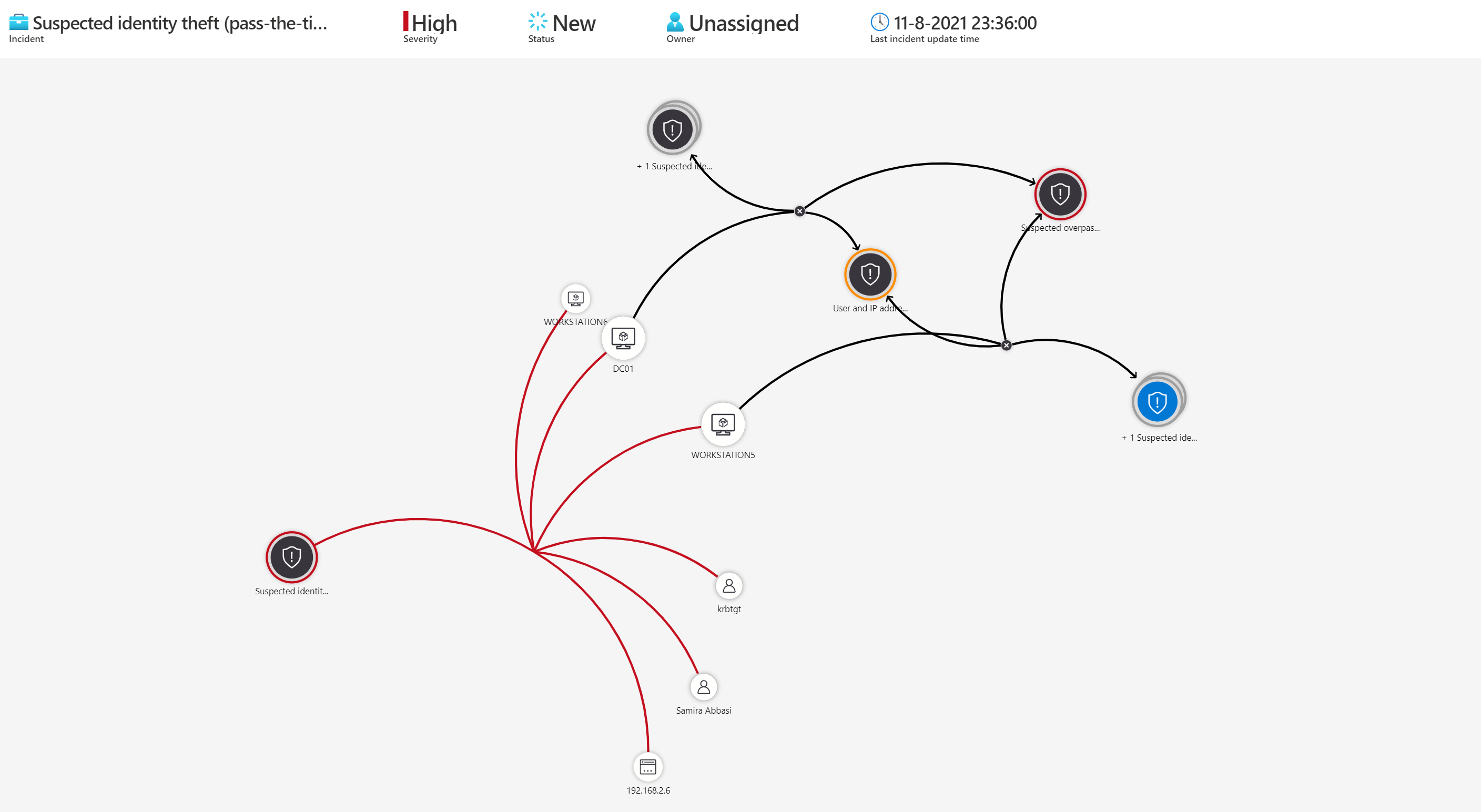
Prevention #4 Defender for Identity
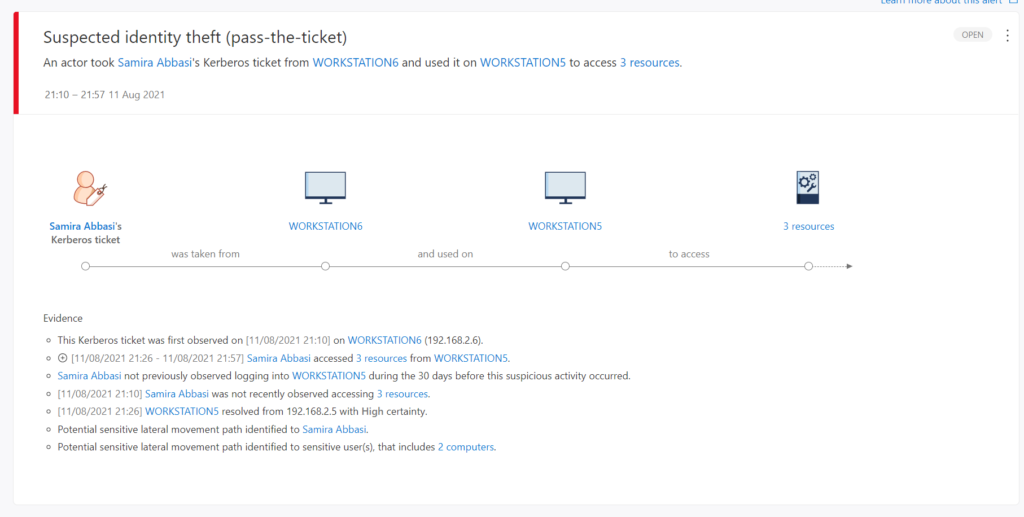
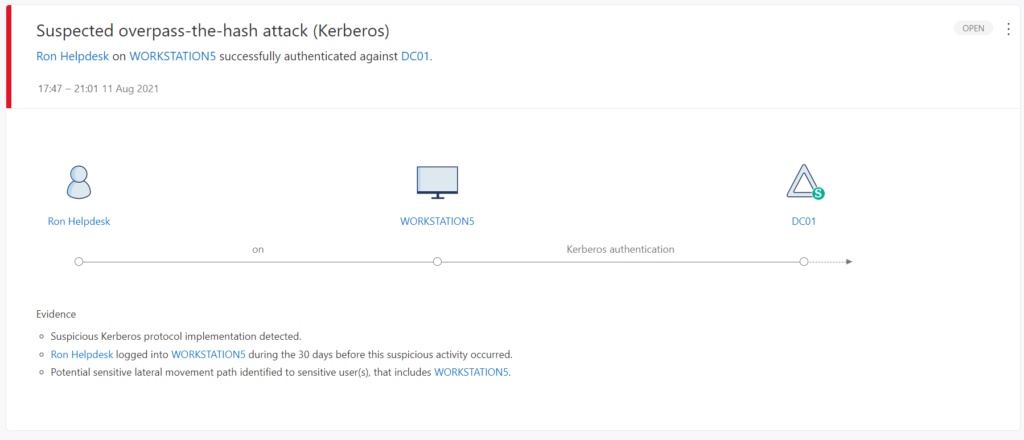
Multiple methods are available for monitoring credential dumping / Lateral Movement. In one of the previous blogs: Protecting against Lateral Movement with Defender for Identity and monitor with Azure Sentinel detection with Microsoft toolings ( Defender for Identity and Microsoft Sentinel) is explained.
Defender for Identity is highly recommended for detecting early stages of credential-based attacks. (Pass the hash, Pass the Ticket (PTH), Kerberos Golden Ticket, Kerberos Silver Ticket).
Sources
- Microsoft: Manage Windows Defender Credential Guard
- Microsoft: Attack surface reduction rules
- ired.team: Credential Access & Dumping
- Whiteoaksecurity: Attacks & Defenses: Dumping LSASS With No Mimikatz
- MITRE: OS Credential Dumping T1003
- Red Canary: MITRE ATT&CK® Technique T1003: Credential Dumping