The Flubot-malware is currently active in the news. The malware with the name FluBot will be sent to mobile endpoints with a text message or WhatsApp message. When opening the link and installing the app the FluBot malware will be activated. With the onboarding to Defender for Endpoint the FluBot can be prevented.
Android devices are being affected by a malicious piece of spyware, known as FluBot. In this post I want to start with a short introduction about FluBot, followed by the configurations for Defender for Endpoint for Android.
How the Flubot Phishing Scam works
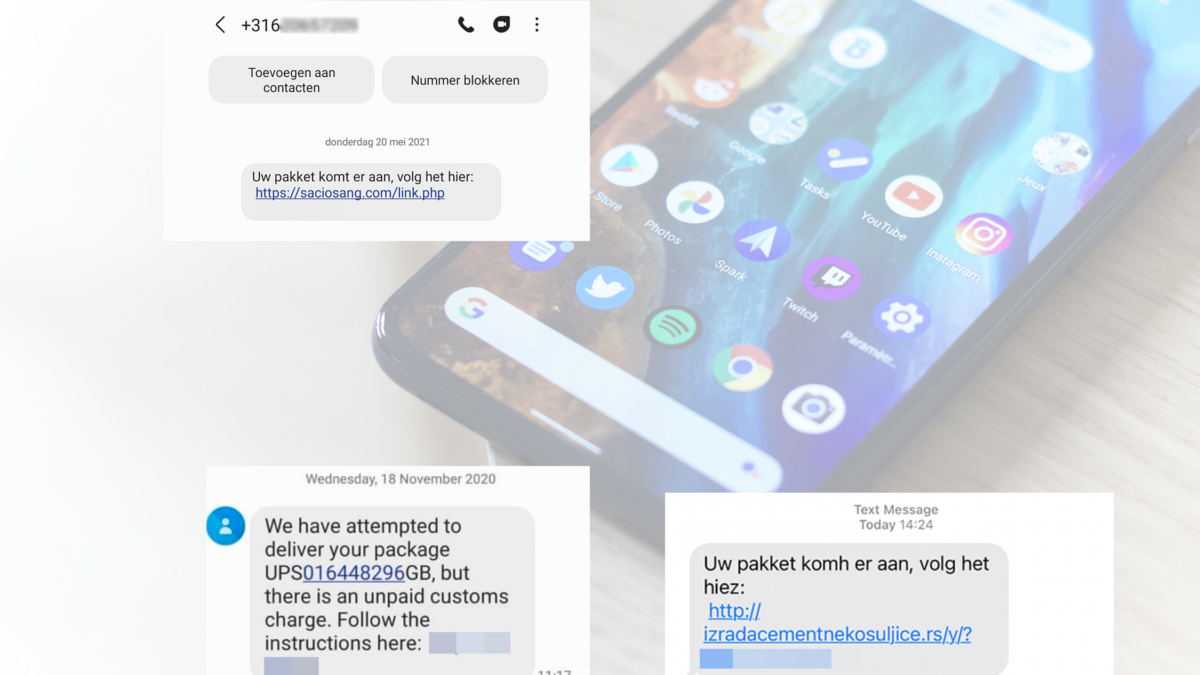
This attack begins with the victim receiving a text message. The message tells them to install a tracking app or a direct link to follow the package from the website. The message plays on the high number of parcels being delivered during the COVID-19.
The FluBot phishing scam is the spyware that steals passwords and other sensitive data from the user’s device. Contact details are accessed and used for sending out additional text messages to spread the attack. This continues the spread of the phishing scam.
Once installed, FluBot obtains the necessary permissions to access and steal any sensitive information you might have on your phone. When a person clicks on the link, it redirects them to a third-party site containing a link to a malicious APK.
Example of the message:
For the English readers( ENG): Your package is coming, follow it here
![]()
Example of the message (English)
![]()
Microsoft Defender for Endpoint for Android
Microsoft announced last year the Defender for Endpoint support for the Android platform. With the use of mobile endpoint protection it is possible to protect the Android OS systems. For the mobile platforms Android and iOS are supported.
MDE for Android provides protection against phishing, unsafe network connections, and malicious apps. All events and alerts around those events will be available in the Defender security center portal.
Prerequisites:
- Defender for Endpoint license assigned to the end-user(s)
- Active network connection from device
- Android 6.0 and above
- Intune Company Portal app available
- Device enrollment inside corporate Intune environment. Device enrollment is required for Intune device compliance policies to be enforced
Integrate Defender for Endpoint with Microsoft Intune
The first step is to integrate Defender for Endpoint with Microsoft Intune. The connectivity integration is supported for all supported platforms. To enable the Microsoft Intune connection, the following steps are required.
- Open security.microsoft.com portal
- Go to Settings -> Endpoints -> Advanced features
- Enable the Microsoft Intune connection

Now it is required to select the Android devices for getting the MDM compliance Policy Settings directly to Defender for Endpoint. For getting the MDM compliance Policy configuration.
- Open the Endpoint Manager Admin center portal
- Go to Endpoint security -> Microsoft Defender for Endpoint
- Under MDM compliance policy settings; enable the value Connect Android devices of version 6.0.0 and above to Microsoft Defender for Endpoint

Deploy the Android application
Now it is required to deploy the corporate app with the use of Microsoft Intune. For deploying the application from Microsoft Intune multiple methods are available. For the Android Enterprise devices use the Managed Google Play app functionality. For the device administrator enrolled device uses the Android store app functionality.
In Microsoft Endpoint Manager admin center , go to Apps > Android Apps > Add > Android store app/ Managed Google Play app.
More detailed steps for deploying the app. Source Microsoft
App configuration policy
Defender for Endpoint supports App configuration policies for managed devices via Intune. This capability can be leveraged to auto grant applicable Android permission(s), so the end-user does not need to accept these permission(s). With this feature, it is possible to assign always the permissions for all the features.
For creating the configuration policies:
- Go to Apps – App Configuration policies -> Add -> Managed devices.
- Choose Android Enterprise as platform
- Choose All profiles or Fully Managed as Profile Type
- Select the Microsoft Defender for Endpoint app (approved during the Google Play Store Enterprise connection)

Now configure the configurations for the External storage read and External storage write permissions.

Configure both values with the Auto Grant permission state. With the Auto Grant setting the permission state will be automatically set from the Endpoint Manager configuration.

By default, Microsoft Defender for Endpoint for Android includes and enables the web protection feature. The configuration key Web protection is not needed, or you need to disable the feature completely.
On the Assignments page, select the user group to which this app config policy would be assigned. Include the applicable group.
After deploying the configuration and Defender for Endpoint app the device is managed and visible in the Defender for Endpoint portal. If we go to the Defender for Endpoint app. All services running fine.

Testing the FluBot
Now the device is protected with the Defender for Endpoint capabilities. Let’s try to start the FluBot attack.
Result without Defender for Endpoint
When opening the SMS fraud/ WhatsApp message or any other messaging app and opening the URL. The website shows most of the time notification prompts or app download button. When allowing notifications; a request is visible to install a malicious app.

Or another example; with the button: Download app (malicious)

Result with Defender for Endpoint
Now Defender for Endpoint and the web protection functionality is available. When opening the URL: The following message will be prompted to secure the end-users from opening and installing the malicious app.

Defender for Endpoint portal – incident response
After detecting with the Defender for Endpoint agent installed. The following rules are visible from Defender for Endpoint.
- Green: Alert – User connect to phishing after user disregarded the warning
- Red: device tried to access a phishing site

Incident story
Device tried to access a phishing site

Device connected to a phishing site after user disregarded the warning
Sources
Microsoft: Defender for Endpoint on Android
Microsoft: Configuration Defender for Endpoint