Continuous Access Evaluation (CAE) for AzureAD is one of the latest functions and is available in public preview. With this new technique, it is possible to respond much faster in comparison with the default token refresh. In the old situation, a user accesses an online service like Exchange Online, Teams, or Office365. The requests are authorized via tokens issued by the AzureAD authentication provider. These are provided at the point a successful authentication takes place, with a default validity of one hour. For security response is an hour too long. In this blog the usage of Azure AD Continuous Access Evaluation (CAE) to speed up the process with Continuous Access.
Introduction Azure AD Continuous Access Evaluation
Continuous access evaluation is a feature in Previews as part of Azure Active Directory. The new function gives more control for the token lifetime and evaluates in real-time Conditional Access Policies and user Changes in comparison to the traditional lifetime of a token. Default 1 hour.
When a client application like Microsoft Teams connects to a service like Teams Online, the API requests are authorized using OAuth 2.0 access tokens. By default, those access tokens are valid for one hour. After the default timings the client is redirected back to AzureAD and requests a new token for the refresh/ extend. This token is the Access Token Lifetime property.
Now the following example; as IT admin you need to block a user directly from the AzureAD portal due to a huge data security breach. In this situation, each minute counts and the default token for 1 hour is too long. This is the part where Continuous access evaluation comes in. Let’s take a look. Editorial note; Of course you can use more Microsoft toolings like Information Protection or Data Loss prevention to solve this issue (:
Continuous Access Evaluation – The tech part
Currently, Continuous access Evaluation works for different types of scenarios. For now the following scenarios are supported:
- Elevated user risk detected by Azure AD Identity Protection
- User Account is deleted or disabled
- Password for a user is changed or reset
- Multi-factor authentication is enabled for the user
- Administrator explicitly revokes all refresh tokens for a user
Not all app and resource combinations are supported. In the table below are the specific combinations for the web-access and app access. For a good visual view on mobile devices; Source Microsoft
| Outlook Web | Outlook Win32 | Outlook iOS | Outlook Android | Outlook Mac | |
|---|---|---|---|---|---|
| SharePoint Online | Supported | Supported | Not Supported | Not Supported | Supported |
| Exchange Online | Supported | Supported | Supported | Supported | Supported |
| Office web apps | Office Win32 apps | Office for iOS | Office for Android | Office for Mac | |
|---|---|---|---|---|---|
| SharePoint Online | Not Supported | Supported | Supported | Supported | Supported |
| Exchange Online | Not Supported | Supported | Supported | Supported | Supported |
Client-side claim challenge
By default clients would always try to reply to the access token from its cache as long the token is not expired. With the CAE technique the resource provider can reject a token even when it is not expired. Claim challenge is the new mechanism to indicate the token reject. CAE requires a client update to understand the latest claim challenge available for the new function. Currently the following apps are supported with the latest version:
- Outlook Windows
- Outlook iOS
- Outlook Android
- Outlook Mac
- Outlook Web App
- Teams for Windows (Only for Teams resource)
- Teams iOS (Only for Teams resource)
- Teams Android (Only for Teams resource)
- Teams Mac (Only for Teams resource)
- Word/Excel/PowerPoint for Windows
- Word/Excel/PowerPoint for iOS
- Word/Excel/PowerPoint for Android
- Word/Excel/PowerPoint for Mac
Continuous Access Evaluation Protocol (CAEP)

Important note about the access token lifetimes: source: Microsoft docs)
Because risk and policy are evaluated in real time, clients that negotiate continuous access evaluation aware sessions will rely on CAE instead of existing static access token lifetime policies, which means that configurable token lifetime policy will not be honored anymore for CAE-capable clients that negotiate CAE-aware sessions. Token lifetime is increased to be long lived, up to 28 hours, in CAE sessions. Revocation is driven by critical events and policy evaluation, not just an arbitrary time period. This change increases the stability of applications without affecting security posture.
Activate the CAE preview
To activate the preview of CAE. Sign in to the Azure Portal with one of the following roles;
- Conditional Access Administrator
- Security Administrator
- Global Administrator
Now go to Azure Active Directory > Security (2) > Continuous access evaluation (3)
For the activation of CAE select the button; enable preview and select a group of users. The default is set to all users/groups.

Integration with Conditional Access
The CAE function works with Conditional Access. For a demo, we have a situation where the clients leave the company network and switch to a phone hotspot and use the already active Outlook web application (1-hour login token). All networks outside corporate are blocked.
Create CA:
User and groups: Select specific user or group
Cloud apps or actions: All cloud apps
Conditions: Select include any location, and exclude all trusted locations. The first screenshot shows the include any location action. The second screenshot shows the exclude for all trusted locations.

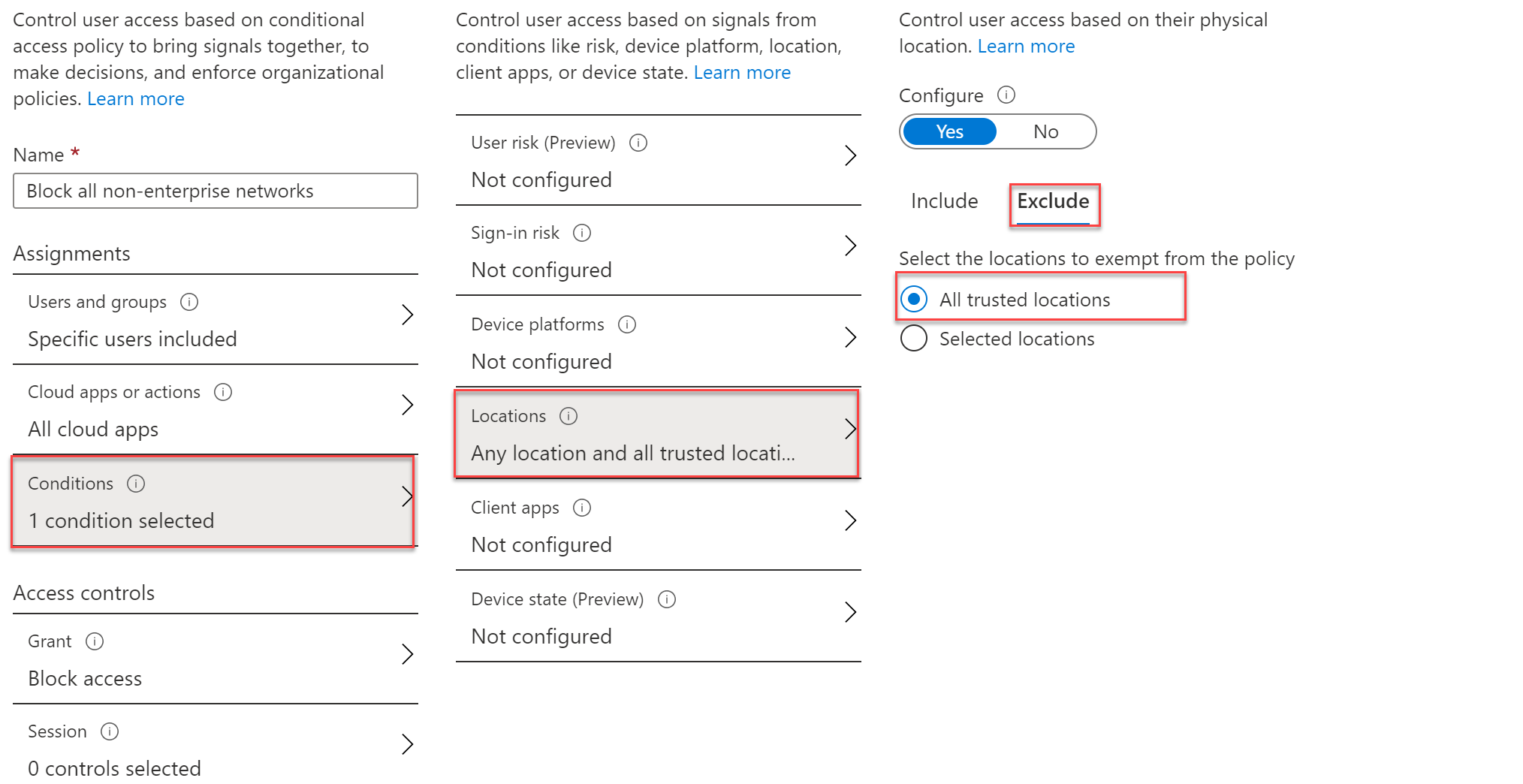
Now configure the access control on block access and enable the policy.

The result:

When switching to a mobile hotspot or another non-enterprise trusted network the only issue: if there is a session active the application is not closed directly based on the default token time. This is the part where Continuous access evaluation comes in.
Continuous Access Evaluation in action
For the best visibility, two short videos. The first without CAE, the latest video with CAE enabled: Both videos with realtime timings.
Note; the network adapter step is to switch the network from corporate to a mobile hotspot for a block action based on the CA rule created before.
CAE disabled:
CAE enabled:
The above situations are based on CAE + Conditional access location-based. Of course it is possible to create more combinations. More Microsoft services, such as Dynamics and Azure, will be enabled in the future.
Sources:
Announcement: Moving towards real time policy & security enforcement




