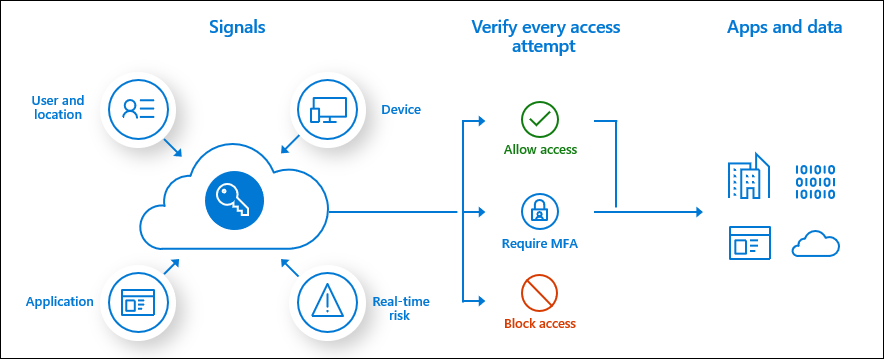
Conditional Access is one of the available tools used by Azure Active Directory to bring different signals together. Based on different signals it is possible to create decisions like; block access, remediate risk, allow full access, and many more situation.
In multiple situations it is useful to require actions like multi-factor authentication before a user can access a resource. For example: A payroll manager wants to access the payroll application and is required to perform multi-factor authentication to access it.
By using Conditional Access policies, you can apply the right access controls when needed to keep your organization secure and stay out of your user’s way when not needed.
Requirements
Using the Conditional Access feature required an Azure AD Premium P1 license. For the sign-in risk signal access to Identity Protection is required.
In this blog a short overview of the option to export Conditional Access configurations based on the Microsoft Graph API and export all the Conditional Access Policies.
API
For the API to retrieve a list of conditionalAccessPolicy objects the following permissions are required:
| Permission type | Permissions (from least to most privileged) |
|---|---|
| Delegated (work or school account) | Policy.Read.All |
| Delegated (personal Microsoft account) | Not supported. |
| Application | Policy.Read.All |
HTTP request
GET /identity/conditionalAccess/policies
More information and request details: Source Microsoft
Query
Now go to: Developer.microsoft.com and sign-in with user credentials. After the sign-in it is important to consent to the permissions. For the consent action; click on modify permissions and click on consent:
The result
The Microsoft Graph Explorer is a good tool for analyzing and testing API requests.
Next steps
The API makes it possible to use the Graph for different situations. Microsoft showed some samples of what you can do with API and scripts related to Conditional Access: Examples are; Deploy from a standard set, monitor policy changes, backup CA rules, and import. More information on techcommunity and GitHub