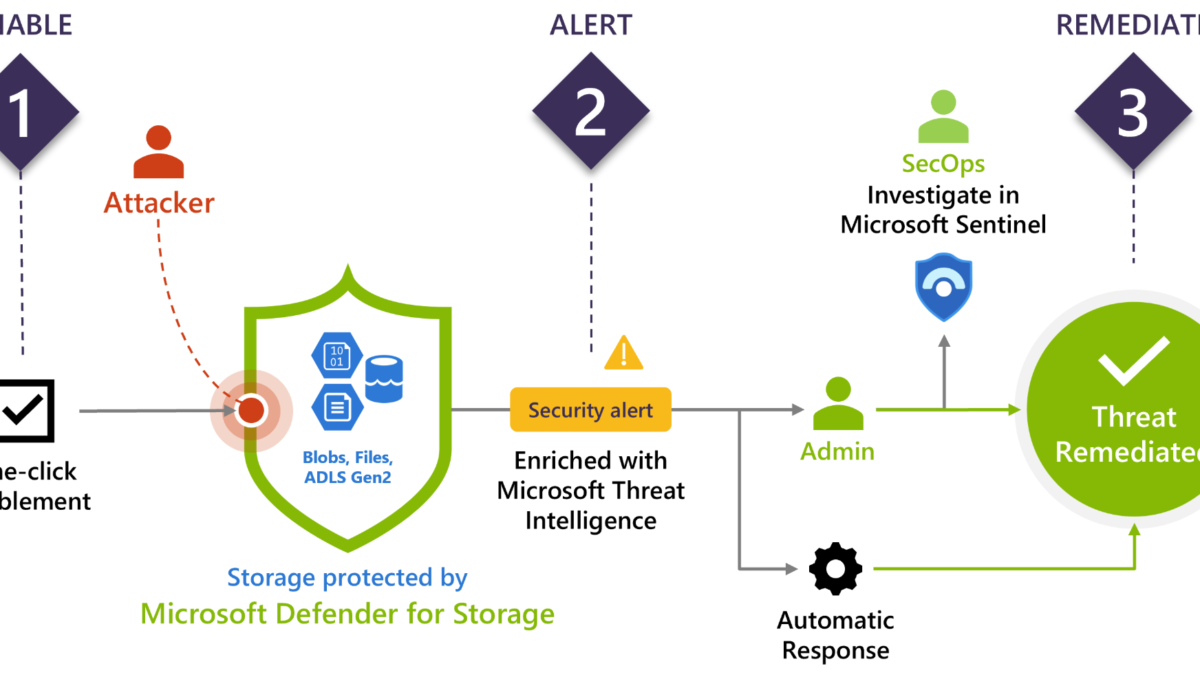
Defender for Storage is the Azure-native layer of security intelligence that detects potentially harmful attempts to access or malicious activity. With the use of Microsoft Threat Intelligence and security AI, contextual security alerts and recommendations are available. Defender for Storage is part of the Defender for Cloud stack. Cloud storage is a common target for attackers focussed on sensitive information for further exfiltration.
| Blog information: Blog published: January 31, 2023 Blog latest updated: 5 September, 2023 (update for GA release) |
What is Defender for Storage?
Defender for Storage is the Azure-native layer for protecting storage accounts and is part of Defender for Cloud. Currently, the following cloud storage types are supported:
- Blob Storage
- Azure Files
- Azure Data Lake Storage Gen 2
Defender for Storage is important for detecting/identifying attempts to exploit storage accounts.

Image source: Microsoft
When the Defender for Storage plan is enabled all detection logic is automated and part of the plan itself. Common question; Do we need additional log configuration? The answer is no, there is no requirement for collecting more events for the core protection futures part of Defender for Storage. It is recommended to enable more in-depth diagnostic auditing and hunt for more use cases based on all ingested logs. (more details later in this blog)
Recently the following features were announced and included in the Defender for Storage add-on as additional components for additional cost.
– Malware Scanning – GA since 1 September 2023
– Sensitive data threat detection (Sensitive Data Discovery) – Preview and free
Since 1 September Malware scanning in Defender for Storage is generally available (GA) for Azure Blob Storage. The cost of the additional add-on is $0.15 for each scanned data.
Announcement blog: Malware Scanning for cloud storage GA pre-announcement | prevent malicious content distribution
What are known cloud storage threats?
Currently, there are a couple of known cloud storage threats. The most common data breaches are based on anonymous access to misconfigured resources/ compromised credentials or breaches involved using social engineering.
Common attacks
- Malware upload: Upload malware to a storage account and use it as an organization’s entry point and distribution point.
- Data Exfiltration: Data Exfiltration of sensitive files outside the cloud storage accounts
- Cloud ransomware: Encrypt and delete data part of the storage account
Cloud storage accounts are used quite often and can be used for any type of data. In some cases, authentication data (keys, tokens, credentials) or other sensitive information is part of the public cloud storage account, which can be abused for other attacks/ lateral movement inside the organization. Common example; PowerShell script with managed identities shared on public blob stores.
When malware/ phishing content is available on machines the Defender for Endpoint product detects malicious files. Within cloud storage accounts it is different with more impact: For example;
Replacing file: The attacker discovers a cloud storage account that is used for deploying scripts which is part of the deployment mechanism (GPO or other tools). When there is malicious access to a cloud storage account; it is easy to replace files with malicious files.
Common threats
- Reconnaissance: Scanning accounts/containers/ blobs for publicly available data and possible secrets for the movement against more cloud storage accounts
- Using search engines: With the use of search engines (Google Dorking/Shodan/ Public information) public blob URLs/ containers can be found.
- Credential/ Access token theft: Phishing, Credential Theft, HTTP Man in The Middle
- Lateral movement from cloud storage assets
Recommended is to view the MITRE threat mapping for the full attack mapping. (source Microsoft)

More information: Threat matrix for storage services | Microsoft.com
Detections in Defender for Storage
Defender for Storage contains a couple of detections based on storage telemetry logs. All detections are improved with behavioral models and Microsoft Threat Intelligence. Defender for Storage maps detections based on MITRE ATT&CK.
Important to know: Defender for Storage in general (without the add-on) doesn’t access the Storage account data and has no impact on its performance. It is all based on collected telemetry/ operation types.
The following alerts are available in GA
More information: Reference list of alerts | Microsoft Learn
| Alert type | MITRE tactics | Severity |
| Access from a suspicious application | Initial Access | High/Medium |
| Access from a suspicious IP address | Pre Attack | High/Medium/Low |
| Phishing content hosted on a storage account | Collection | High |
| Storage account identified as source for the distribution of malware | Execution | Medium |
| The access level of a potentially sensitive storage blob container was changed to allow unauthenticated public access | Collection | Medium |
| Authenticated access from a Tor exit node | Initial Access / Pre Attack | High/Medium |
| Access from an unusual location to a storage account | Initial Access | High/Medium/Low |
| Unusual unauthenticated access to a storage container | Initial Access | High/Low |
| Potential malware uploaded to a storage account | Lateral Movement | High |
| Publicly accessible storage containers successfully discovered | Collection | High/Medium |
| Publicly accessible storage containers unsuccessfully scanned | Collection | High/Low |
| Unusual access inspection in a storage account | Discovery | High/Medium |
| Unusual amount of data extracted from a storage account | Exfiltration | High/Low |
| Unusual application accessed a storage account | Execution | High/Medium |
| Unusual data exploration in a storage account | Execution | High/Medium |
| Unusual deletion in a storage account | Exfiltration | High/Medium |
There are a couple of new alerts currently in preview. With the new alerts Microsoft alerts when a malicious blob is uploaded to a storage account. View the full alert list here including the new preview alerts.
Important: Defender for Storage uses the hash reputation method supported by Microsoft TI to determine the status. With the new storage account plan it is possible to enable the Malware Scanning feature – this method scans uploaded files for malware.
Some of the alerts require the enablement of data sensitivity threat detection enabled. This add-on will be explained in a separate blog.
How to enable Defender for Storage?
Enablement is possible with the use of Defender for Cloud. In Defender for Cloud, it is required to enable the plan Defender for Storage. On the subscription level itself, it is possible to enable only the per-storage account pricing.
There are currently two pricing models:
- Per-storage account pricing (Subscription level)
- Per-transaction pricing (legacy plan)
The per-transaction pricing is the legacy plan and does not support the new capabilities. It is possible to override Defender for Storage subscription-level settings and disable Defender for Storage or a specific feature for a set of storage accounts. It is recommended to enable Defender for Storage on the entire subscription to protect all of the existing and new storage accounts. With the flexibility of the design, it is possible to exclude specific storage accounts from the Defender for Storage plan with the override as part of the storage account settings.

See: Override Defender for Storage subscription-level settings
Pricing
Important is the monitoring of cost. Transactions can increase the cost. By default, the start price is $10 for each storage account/month. Storage accounts that exceed 73 million monthly transactions will be charged $0.1492 for every 1 million transactions that exceed the threshold.
Use the Microsoft Defender for Storage Price Estimation workbook for more price calculations.
Enable using Defender for Cloud
Enablement is with the use of Defender for Cloud easy for the complete subscription.
- Sign in to the Azure portal and navigate to Microsoft Defender for Cloud and open the Environment settings. Open one of the available subscriptions:

- Enable Defender for Storage with the per-storage account pricing for the subscription level

When the plan is enabled for the complete subscription; it will protect all available storage accounts by default.
View estimated transactions
When the plan is enabled Defender for Storage gives the estimated analyzed transactions/day for the last two weeks of usage. Open the storage account in Azure and open the details in the Defender for Storage section for the transaction statistics.

Malware Scanning in Defender for Storage
Malware Scanning in Defender for Storage is available when the new Defender for Storage plan is enabled. Malware Scanning supports a full malware scan during the upload of content in near real-time using the capabilities of Defender Antivirus/ Defender for Endpoint. It is using the engine of Defender Antivirus for threat detection.
As soon as a file is uploaded to a storage account, Malware Scanning will immediately read the uploaded content

Source: Microsoft
The Malware Scanning capability is completely agentless and based on the technology of Defender Antivirus; with this, there is no additional agent installation required or depending on locally installed Defender components. It is supported for a standard general-purpose v2 storage account, Azure Data Lake Storage Gen2, or premium block blobs storage account.
Since storage accounts can be an initial starting point for malware it is important to scan malware before the file/ blob is uploaded. Each file is scanned with a max of 2GB for each file, this includes zipped/ files. When the malware scan identifies a malicious file, detailed Microsoft Defender for Cloud security alerts are generated.
Malware Scanning can be enabled at scale via Azure portal, Azure policy, ARM, API, or Bicep templates. Read the Microsoft documentation for the automated options. For now, we will focus on manual onboarding via the Azure portal.
How to enable manual via Azure Portal for subscription
In Defender for Cloud it is possible to enable Defender for Cloud via the environment settings. Go to the subscription and enable the plan Defender for Storage.
NOTE: This will enable malware scanning for all storage accounts in the subscription. It is possible to enable Defender for Storage for each storage account separately via the storage account settings view in Azure. See image.

For malware scanning you need to update to the new Storage Account plan ($10/Instance/Month + additional transaction cost). Malware scanning is only available in the new storage plan.
In the Defender for Storage plan, there is a new configuration capability for on-upload malware scanning. When enabled the on-upload malware scanning is enabled.
The cost is $0.15/GB scanned. When needed it is possible to limit the GB scanned per month. When the limit is reached, no additional files will be scanned as part of the feature.

Via settings, it is possible to check if the feature is enabled and change the limit/ feature when needed.

After the configuration/ enablement in Defender for Storage there are a couple of automated actions as part of the enablement:
- Event Grid System Topic resource is created in the resource group of the storage account
- Data scanner resource with the name StorageDataScanner is created in the Azure subscription and assigned with a system-assigned managed identity. This resource is part of the Storage Blob Data owner role assignment.
In case Malware Scanning is enablement on the subscription level, a new Security Operator resource called StorageAccounts/securityOperators/DefenderForStorageSecurityOperator is created with a system-managed identity. This resource enables and repairs the configuration on existing storage accounts and checks for new storage accounts to be enabled.
Event Grid Resource
For use of the new threat protection features it is needed to enable the Event Grid resource provider. During the enablement, the provider will be registered automatically when the correct permissions are in place. Always good to confirm that the Event Grid resource is enabled in the resource provider settings for the subscriptions.

For more information and requirements see: Malware scanning | Microsoft
Privacy
Good to know the scanning approach is completely private. The regional malware scanning engine never retains the content of the files, and the data is never centralized. All files are scanned in memory and not stored in the malware-scanning engine.
Each malware-scanning instance is available in the same region of the storage account. When more data is required – the engine is able to share metadata (sha-265 hash) with other regions This is based on the same approach in comparison with Cloud Protection in Defender AV/ Defender for Endpoint.
Cost control
The enablement of Malware scanning capability can be enabled at the subscription level or at the resource level. It is always possible to exclude individual storage accounts from the protection – with this approach, it is possible to tweak the usage and enablement across the environment.
Structure in storage blobs
There is a known structure in the blob service concept. Each storage blob contains the following components/ structure.
- Account
- Container
- Blob
It starts all with a storage account. For example, the storage account contains the name: maliciousblobstore. The account name is always unique.
A container provides a grouping of a set of blobs. All blobs must be in a container. See this as a folder; for example files/ Movies/ Pictures.
A blob is a file of any type and size. For example Eicarr.zip / Image1.png / movie.mp4
http://<storage account>.blob.core.windows.net/<container>/<blob>
https://maliciousblobstore.blob.core.windows.net/files/eicar_com.zipPublic storage accounts can be easily discovered using different OSINT tools or using Google and other tools. All storage accounts are created with the default URL structure; the ending is always blob.core.windows.net.
Permissions
Storage accounts contain a different set of permissions. Every container is associated with a public access level. The permissions can be configured based on the container:

- No public read access (private)
- Public read access for blobs only (available via complete full URL)
- Public read access for containers and blobs
No public read access is the default for each container and can be accessed only with an authorized request.
Blobs within the container can be read by anonymous request, but container data is not available anonymously. There is no enumeration possible with the blobs inside the container.
Container and blob data can be read by anonymous request in the container. and enumerate inside the container.
When public; the file is directly available via the URL structure:


Files can be “protected” with the use of a Shared Access Signature (SAS token) that allows access to the objects. The URIs are quite commonly visible on the public web. Within seconds public SAS tokens are visible on GitHub. Microsoft explained the SAS structure. More information: SAS parameters | Microsoft Learn
Example of SP:
https://maliciousblobstore.blob.core.windows.net/files/eicar_com.zip?sp=r&st=2023-01-30T20:22:08Z&se=2023-01-31T04:22:08Z&spr=https&sv=2021-06-08&sr=b&sig=cfZkxWdsTLN8uJsJk%2Fl4e2uNfrZw%2BFbvpTOR0FNiofQ%3DWith the use of the account/container information, it is possible to view all related content.
https://maliciousblobstore.blob.core.windows.net/files?resttype=container&comp=list
Collect additional events
For active hunting, it is recommended to add additional logging for each diagnostic account. Defender for Storage is by default protecting with a set of default activities, more hunting is possible when diagnostic settings are enabled. Diagnostic settings are disabled by default.
Diagnostic settings can be easily applied in the Azure Portal for each storage account. When configuring it is possible to streal all events directly to Log Analytics, event hubs, or other solutions.
Make sure to include the StorageRead/ StorageWrite/ StorageDelete and Transaction metrics for all available services.

Enable logging for all of the services:

And configure the destination source: (Send to Log Analytics when using Sentinel)

Simulation of malicious attempts
Discovery/ reconnaissance of the Azure Blobs is the first step. With the name convention, it is easy to search for public storage accounts. Example; *.blob.core.windows.net. With the use of Google, there are +- 2.980.000 results.
site:*.blob.core.windows.netMore properties are allowed, including an intext search for CONFIDENTIAL
site:"blob.core.windows.net" and intext:"CONFIDENTIAL"
It is quite easy to check against public storage accounts. There are quite some tools available (AZ-Blob-Attacker/Microburst/Basic Blob Finder/ GrayHat Warfare and many more)
GrayhatWarfare is a simple website/ searchable database for searching against public accounts. The result shows more details (Account, Files, Container).

When clicking on the count all files are directly visible including limited metadata:

Let’s assume you have a leaked account name and key. With the use of PowerShell, it is easy to connect without any authentication from the user/admin itself. Only the account key/account name is needed.
az storage container list --account-key lYhFwFIio7FZi9KQec4C7a9L2JfleHSVTPEzQyxlyKEXEFn2BN9KMhk94oC3Ipb39KQ== --account-name maliciousblobstore
By running the command via PowerShell the container name is visible:

Now it is possible to list the blob names with the use of the known account name, key, and container:
az storage blob list --account-key lYhFwFIio7FZi9KQec4C7a9L2JfleHSVTP406gO5IEzQyxlyKEXEFn2BN9KMhk94oC3Idb6J23T2+AStpb39KQ== --account-name maliciousblobstore -c files
When the account key/account name is available with the correct permissions. It is possible to upload/ delete/ download files.
Tor node
Access from a Tor node is one of the available alerts in Defender for Storage. Use the SAS URL and access the SAS URL directly from the browser. Within a couple of hours, the following security alert is visible in the Defender for Cloud portal: “Access from a Tor exit node to a storage blob container”

Potential malware uploaded
When uploading malicious files – Defender for Storage checks the hash against available/ TI data. Defender for Storage uses the hash reputation method supported by Microsoft TI to determine the status. Hash reputation checking is enabled for all plans and there is no requirement with the add-on for malware scanning.

Recently Microsoft announced the new direct scanning feature in the new Defender for Storage plan.
Malware Scanning in Defender for Storage:
For threat protection and malware scanning it is needed to enable the additional malware scanning add-on, as already explained in this blog. When uploading malicious files directly to the storage account it will perform a scan based on the Microsoft Defender Antimalware technology.
The malware scanning scan results are available via a couple of methods:
- Blob index tags for uploaded and scanned files in the storage account
- Microsoft Defender for Cloud security alerts
- Event Grid event (Custom)
- Log Analytics (Custom)
When uploading mimikatz-master.exe the file is flagged as malicious. Part of the file is the blob index tags, including the malware scanning scan result “Malicious”

When malicious files are detected as part of the scan there is a new detection triggered in Defender for Cloud with the title: Malicious file uploaded to storage account. Based on the alert insights it is possible to take action and remove the file – this can be automated via Logic Apps (Upcoming blog)

Connect Defender for Storage alerts with Microsoft Sentinel
For sending alerts (SecurityAlert) to Microsoft Sentinel, use the Defender for Cloud connector in Sentinel for all available subscriptions.
Alert synchronization
When connecting Defender for Cloud to Microsoft Sentinel there is the option for enabling alert synchronization. When an alert is closed in Defender for Cloud; the alert will be closed in Microsoft Sentinel as well. Important: The incident status will not be changed in Sentinel; only that of the alert itself.
Bi-directional alert synchronization can be used to automatically sync the status bi-directional. When the incident is closed in Microsoft Sentinel; the alert will be closed in Microsoft Defender for Cloud.
How to connect
Open the Defender for Cloud connector page in Sentinel and enable the toggle for each subscription. Important: Be careful with the button; Enable Microsoft defender for all subscriptions and Enable All
Enable the Status to Connected and configure Bi-directional sync for automatically sync alerts. Don’t forget to enable the incident analytics rule “Create incidents based on Microsoft Defender for Cloud” in Microsoft Sentinel.

Conclusion
Defender for Storage gives some more extra insights. Important; Defender for Storage is not applying any baseline/ protection to the Defender for Storage accounts, make sure the Storage Account is protected and limited. It is recommended to turn on soft delete for blobs/ containers to recover a container it has been deleted, HTTPS traffic, and some more basics. There are more protections available. Read all available security recommendations for Blob storage
Stay tuned for the next blog with a strong focus on the new data sensitivity threat detection add-on part of the Defender for Storage plan for more alert generation.
Sources
Microsoft: Malware Scanning for cloud storage GA pre-announcement | prevent malicious content distribution
Must read from inversecos.com: How to Detect and Compromise Azure Blobs and Storage Accounts
Interesting research from Cyberark: Hunting Azure Blobs Exposes Millions of Sensitive Files
Microsoft Threat Matrix for Storage service: Threat matrix
Microsoft: Security recommendations for Blob storage
Microsoft: Security baseline