Last year Microsoft announced a new feature called; Automatic attack disruption which uses correlated insights from the Microsoft 365 ecosystem and powerful AI models to stop sophisticated attack techniques while the attack is in progress. Automatic attack disruption supports the adversary-in-the-middle (AiTM) attacks.
Microsoft attack disruption is using the power of XDR (Microsoft 365 Defender) to correlate all signals from multiple products. When the attack is in progress Microsoft 365 Defender disrupts the attack by containing the assets that the attacker is using via the attack disruption capability. With this approach, Microsoft stops the attack early prevents further damage, and more importantly reduces the overall impact of the attack.
Microsoft releases attack disruption to answer to the ever-growing volume of advanced, rapid, large-scale cybersecurity attack challenges. With the use of attack disruption, it is possible to answer quicker and prevent high-fidelity alerts.
Good example of a complex multi-stage campaign; Detecting and mitigating a multi-stage AiTM phishing and BEC campaign
In simple words; what is attack disruption?
Attack disruption are automated response actions aimed to quickly and effectively contain an attack in progress and reduce the overall impact.
How works attack disruption?
Attack disruption is part of the Microsoft 365 Defender XDR ecosystem and correlates all signals from individual Defender/ Microsoft security products. Attack disruption is enabled by default when all prerequisites are correctly enabled and configured – the feature is built-in and is based on the collected insights/ security research and AI models to combine and correlate events to identify advanced attacks and perform automated actions (attack disruption).

When checking the complete flow Automatic attack disruption operates in three stages:
Stage 1: Correlates events from Microsoft 365 Defender XDR across all products and creates one single, high-confidence incident based on all collected data from endpoints, identities, email, and collaboration tools. Calculation is performed to calculate high-fidelity attacks to avoid false positives.
Stage 2: Identify affected assets controlled by the attacker that are used during the attack.
Stage 3: Take automated response actions to contain the attack and isolate affected machines.
Since automatic actions can lead to potential impact when the alert/ signal is classified as a false positive. Attack disruption is designed to rely on high-fidelity signals. Microsoft shares the following information:
In addition to XDR capabilities that correlate incidents with millions of Defender product signals across email, identity, applications, documents, devices, networks, and files. Insights from the continuous investigation of thousands of incidents by Microsoft’s security research team ensure that automatic attack disruption maintains a high signal-to-noise ratio (SNR).
Microsoft
Based on the incident Microsoft calculates the incident and knows the “impact”. When multiple products are correlating alerts Microsoft is able to validate the real attacks with confidence to avoid running automation as a false positive.
Simplified overview of the flow (not official Microsoft)

Available actions
Microsoft is leveraging the Microsoft XDR response actions which are part of the product. Example of available actions:
Endpoint (Microsoft Defender for Endpoint)
- Contain device
- Contain unmanaged devices
- Contain user
With the leverage of Defender for Endpoint device discovery and containment, it is possible to detect unmanaged devices and block incoming/outgoing communication with the suspected device. With this approach the contain action is way more powerful, since attackers can use unmanaged devices as part of the network.
Attackers leverage mostly unmanaged devices for performing advanced attacks. With the use of contain it is possible to contain the unmanaged devices, even when the machine is not onboarded to Defender.
Identity (Microsoft Defender for Identity)
- Disable user
With the leverage of Defender for Identity is it possible to block users in AD/ AzureAD. The actions will be performed via Defender for Identity.
Supported attacks
Currently, Microsoft supports a couple of attacks where attack disruption will take place. The following attacks are currently supported by attack disruption:
- Human Operator Ransomware (HumOR)
- Business email compromise (BEC)
- Adversary in the middle (AiTM)
Most of the attacks are well known – let me explain the attacks quickly:
Human Operator Ransomware (HumOR)
In cases on Human human-operated ransomware, the attack will block access to critical data, network, or physical infrastructure. Human-operated ransomware can have a major impact since the deployment is rapid to increase the full damage. During attack disruption, it is important to reduce the risk from the earlier states.
Business email compromise (BEC)
A BEC attack relies upon the ability to look like someone with power within a company or a trusted external partner. Typical types of BEC attacks; (False invoice scam, CEO fraud, Account compromise, Attorney Impersonation, Data Theft).
BEC attacks are typically focused on financial gain, where the attacker tries to convince the victim to transfer funds to fraudulent accounts or pay fake invoices.
More information: What is business email compromise
Adversary in the middle (AiTM)
During AiTM attacks, a phished user interacts with an impersonated site created by the attacker. This allows the attacker to intercept credentials and session cookies – cookies include the MFA token, which makes this attack able to bypass multifactor authentication.
More information: Detecting and mitigating a multi-stage AiTM phishing and BEC campaign | Microsoft Security Blog & Automatically disrupt adversary-in-the-middle attacks with XDR (microsoft.com)
How to enable automatic attack disruption?
Automatic attack disruption is automatically enabled when using Microsoft 365 Defender. When using all Defender products it will increase the protection coverage. For automatically containing devices it is required to deploy Defender for Endpoint, blocking of user accounts requires Defender for Identity.
When checking the complete XDR view of Defender products – the following configuration is important. The reason is that attack disruption is XDR capability – it requires multiple signals from multiple sources to gain confidence in the compromised assets.
- Defender for Office
- Defender for Endpoint
- Defender for Identity
- Defender for Cloud Apps
- Azure AD Identity Protection (Correlated with Microsoft 365 Defender)
Prerequisites
- Defender products configured (to get full visibility)
- Correct license/ subscription available
- Defender for Endpoint device discovery set to standard discovery
- Defender for Endpoint configured with automation level
The following prerequisites are needed. More information: Prerequisites for automatic attack disruption in Microsoft 365 Defender
Attack disruption works at its best when all products are deployed and configured. Each attack (AiTM/ BEC/ Operated ransomware) works on multiple signals across the Defender 365 product suite. In the situation of a BEC attack, it is mostly using the following products during the full attack stage:
Common BEC attack flow
Initial access
During the initial access, the attacker obtains user credentials/ possibly purchased by the dark web/ collected data, or via targeted phishing. Attackers target mostly high-level individuals, discovered via Linkedin, Facebook/ Instagram, or other OSINT data sources.
Products involved: AAD/ M365D & MDA.
Account compromise
During the compromise phase, the user authorized sign-in due to MFA fatigue/ reverse proxy or other methods of MFA stealing/ cookie stealing. During the account compromise phase, the attacker logs into the account from the high-level individuals.
Products involved: AAD
Collecting/ Phishing
During the collection/ phishing/ evasion phase the inbox rules will be created and the attacker will observe recent communications/ send invoices to partner organizations with a changed bank number and update inbox rules with new addresses.
This flow will be repeated to affect many organizations (supply chain attack)
Products involved: M365D/ MDO/ MDA
As you can see multiple products are involved for each single stage during a BEC attack. Since AAD/ M365D/ MDO/ MDA are involved it is important to detect multiple events and it is needed to correlate events to see it from the identity/ app/ endpoint perspective. The combination of alerts/ signals makes it important. When only AADIP is alerting it is missing the part which can lead/ identify a full BEC attack in the environment. With this XDR approach/ the attack disruption flow works best when all supported products are configured to collect and generate alerts within Microsoft 365 Defender.
When BEC is in place a potential response action is the token revoke or password change for the compromised account.
More information: Automatic disruption of Ransomware and BEC attacks with Microsoft 365 Defender & XDR attack disruption in action – Defending against a recent BEC attack
Ransomware (Human-Operated Ransomware) flow
Ransomware is complex and relies on multiple products and signals. The first phase of ransomware is based on initial access, reconnaissance, credential theft, lateral movement, persistence, reconnaissance, and defense evasion.
Ransomware is not only focused on devices; since email for the initial access and reconnaissance is an important step during a real attack.
When attacks are complex; Microsoft relies on the following products to share and correlate events:
- Defender for Identity
- Defender for Office
- Defender for Endpoint
- Azure AD Identity Production
The typical action during Human-operated ransomware is the contain the device used for the ransomware deployment and block/contain the affected user.
More information: Automatic disruption of Ransomware and BEC attacks with Microsoft 365 Defender
Configure features in the products
When having the products – make sure they are correctly configured. It is always recommended to follow the best practices for all individual products and make sure the products are configured with the best protection and event collection. For attack disruption, the following is important for each single product:
Defender for Endpoint
Since attack disruption relies heavily on the discovery and contain feature it is important to configure Defender for Endpoint to discover unmanaged devices in the network and the automatically responses actions.
Device discovery
First, we need to configure the device discovery to standard discovery. With the use of device discovery Defender for Endpoint is able to discover unmanaged devices connected to the corporate network.
In general, there are two ways of discovery
- Basic discovery
- Standard discovery
For the contain and attack disruption functionality it is needed to configure the standard discovery mode. This discovery is active and based on common discovery protocols/ multicast with smart active probing.
Configuration is possible via Microsoft 365 Defender. Navigate to Settings -> Device Discovery.
The discovery mode must be “standard discovery”. It is recommended to discover via all devices; when needed it is possible to select device groups to discover by tag. Unwanted networks can be excluded via the monitored network configuration.

Run the following query to check if machines are discovered in the environment.
DeviceInfo
| summarize arg_max(Timestamp, *) by DeviceId // Get latest known good per device Id
| where isempty(MergedToDeviceId) // Remove invalidated/merged devices
| where OnboardingStatus != "Onboarded"Automation levels
The automated action in Defender for Endpoint is based on the automation level for device groups. Ideally, actions will be performed automatically. With the levels of automation, it is possible to define the level and exclude devices from automated response actions.
I recommend using the Full – remediate threats automatically level – since this remediates threats automatically and will perform automatic actions ( file collections/quarantine/ submissions). When needed configures exclusions for specific machines.

Defender for Identity
The disabled user activity is based on the Microsoft Defender Identity capability. As part of the integration, the attack disruption flow will automatically block the compromised account to prevent additional damage.
Manage action accounts
To get this feature up and running it is needed to configure the action account in Defender for Identity. Currently, there are two options for configuring the action account:
- Automatically use the sensor’s local system account
- Manually configure your management accounts
When selecting manual it is possible to configure a gMSA account. When using the automatic option the local system account of the sensor is used.

More information: Microsoft Defender for Identity action accounts
The disable user action relies on the on-premises Active Directory. When the account is not found/ or detected the following error is visible in M365D Action Center:

Attack disruption in action
Let’s simulate the attack disruption flow to see how M365D collects all data and correlated events. Since the events are high fidelity it is not easy to generate test alerts with the use of test domains. In my situation, I was able to generate the attack disruption response during the AiTM attack.
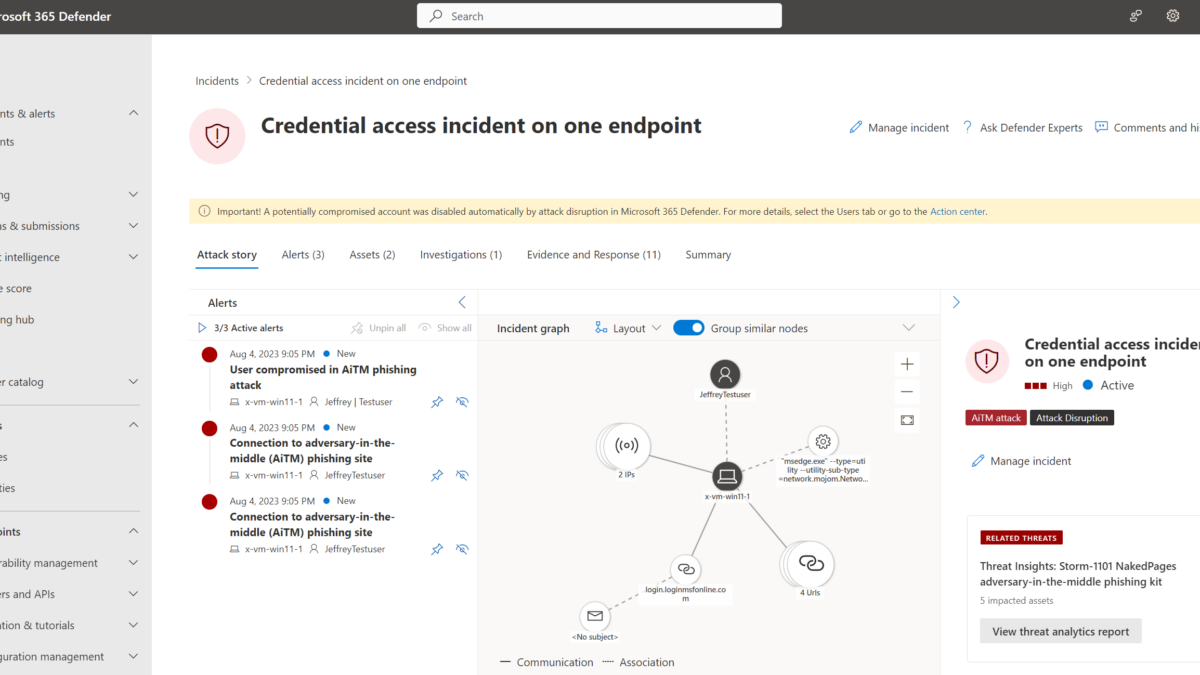
Alerts
The following alerts were visible in M365D:
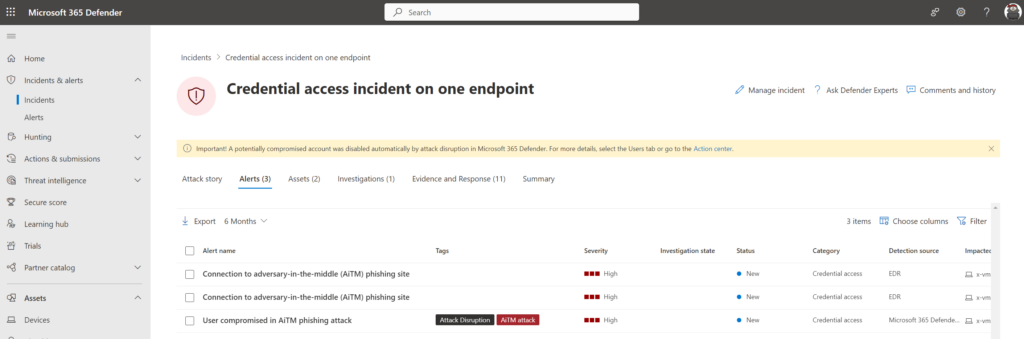
- User compromised in AiTM phishing attack
- Connection to adversary-in-the-middle (AiTM) phishing site
As you can see the User compromised in AiTM phishing attack alert is flagged with the tags Attack Disruption/ AiTM attack.
Incident
All alerts were mapped in one single incident; the incident is performed via the flow:
- Send an e-mail to test user with the AiTM phishing link
- The user clicks on the link and sign-in via AiTM link
- Attackers receive the tokens and used the token to get access

The incident is classified as high with the following tags:
AiTM attack: This tag identifies the incident detected as AiTM attack
Attack Disruption: This tag identified the incident as part of the attack disruption flow

At the top there is the following information visible:
“Important! A potentially compromised account was disabled automatically by attack disruption in Microsoft 365 Defender. For more details, select the Users tab or go to the Action Center.”
This notification notifies the compromised account was disabled automatically by attack disruption in Microsoft 365 Defender. When searching for the ActionType: Disable user we can see the action is performed automatically by MDI.

Part of the incident is the threat analytics detection – during the performed simulation the alert is flagged with the threat insights Storm-1101.
Option to exclude assets?
It is possible to exclude assets from the Attack Disruption flow. With the exclusions, it is possible to exclude identities and assets. All be a bit careful with exclusions. Most organizations will exclude the most valuable assets (Domain controller/ CEO/ CTO accounts/ Critical Service accounts) – Of course, the most valuable assets are those that are mostly the target of attackers.
Excluding user accounts is not recommended, since accounts added to the exclusions list won’t be suspended in all supported attack types.
When exclusions are needed the users can be exclusions via Microsoft 365 Defender portal -> Settings -> Identities -> Automated response exclusions

IMPORTANT – Attack disruption requires always investigation
Attack disruption is no ultimate protection (detect and forget) – it is critically important to make sure the analyst is investigating the full attack. When the assets are contained/ blocked – the attacker will always try to bypass and find more ways to launch the attack again.
When the attack is ‘stopped’ by attack disruption it is important to review the alerts/ incidents. Attack disruption will not resolve the full attack; it will give additional time for the SOC team and stop the growing count of infected assets. Since the attack is under control the SOC team can focus fully on the investigation and further remediation of the attack.
View Attack disruption events
Each alert/ incident part of Attack disruption is tagged with the tag Attack disruption. Via the alerts/ incident view, it is possible to filter by the tag “AiTM attack”

Performed automated response actions can be reviewed via Action Center. In Action Center click on history and filter for a specific action type. All Attack disruption actions can be viewed when using the decided by “Attack disruption” filter.

Sources
Microsoft: Automatic attack disruption in Microsoft 365 Defender
Microsoft: Configure automatic attack disruption capabilities in Microsoft 365 Defender
Microsoft NinjaShow: Attack Disruption | Virtual Ninja Training with Heike Ritter
Microsoft Ignite: Microsoft 365 Defender: Stop attacks with automated cross-domain (XDR) security | LRN201
Microsoft: Automatic disruption of Ransomware and BEC attacks with Microsoft 365 Defender




I configured but i want too test if it is working. Is there any way to simulate the test?
Great article.
Is there a QR code phising campaign within the Defender 365 portal like there is with Defender for O365?