Microsoft Defender Threat Intelligence (MDTI), previously known as RiskIQ brings threat Intelligence data together from multiple sources.
With Microsoft Defender Threat Intelligence (MDTI), customers will have direct access to real-time data and signals to hunt for threats across their environments. It is built with AI and machine learning capabilities. Defender TI is available in a free community version and paid version.
| Blog information: Blog published: Augustus 17, 2022 Blog has been completely rewritten/updated: August 25, 2023 |

What is Microsoft Defender Threat Intelligence?
Microsoft Defender Threat Intelligence can be used for multiple solutions. It can act as a standalone product and allows the option for ingesting TI data into Microsoft Sentinel or Microsoft 365 Defender. Microsoft Defender Threat Intelligence is a threat intelligence (TI) solution, that helps with additional insights, context, and additional strategies about threat actors and adversary threat infrastructure. Data is based on open-source intelligence (OSINT) combined with threat research articles, threat indicators, and vulnerability intelligence found in the wild.
Microsoft Defender Threat Intelligence collects intelligence/ IOC data from various sources. Input is based on:
- RiskIQ
- Microsoft Threat Intelligence Center (MSTIC)
- Microsoft 365 Defender Security Research
- Other sources
Defender Threat Intelligence is built from the RiskIQ technique. Microsoft integrated RiskIQ technologies in Defender based on two new solutions:
- Microsoft Defender Threat Intelligence
- Microsoft Defender External Attack Surface Management
Microsoft Defender Threat Intelligence collects data from the internet every day and provides security teams with information to understand adversaries and used attack techniques. Customers can access a library of threat intelligence data.
Currently, Microsoft Defender Threat Intelligence is available in two different plans (end-user plans):
- Defender TI Premium
- Defender TI Free community offering (limited)
Without any Defender TI Premium license, it is possible to use the Defender Threat Intelligence Portal and access the context part of the free offering with limited data.
Price and trial
For the Defender TI Premium solution, the license is currently available for €3900 license/month or €45,803 license/year. The trial can be activated via admin.microsoft.com. The license is user/assigned. The trial enables 5 licenses.

Assign the available Defender Threat Intelligence license to the user. Important: Defender Threat intelligence UI is licensed per user. So make sure the users are assigned a license for using the premium functionalities and full dataset with all historic data or use the free community edition without any assignment.

Defender TI Portal
The portal is available via: ti.defender.microsoft.com. The free limited/ community version can be used without any additional pricing or trial activation.
Interoperability with Microsoft 365 Defender
Defender TI is integrated with the Microsoft 365 Defender portal. Defender TI is available via Microsoft 365 Defender with a couple of new tabs.
NOTE: The futures are only available when the user is licensed for Defender TI, without a license the Defender TI view is not visible in Microsoft 365 Defender.
Threat analytics part of Microsoft 365 Defender is available when using Defender. The pages “Intel profiles” and “Intel explorer” require a license to Defender TI.
Visible without license

Require MDTI license:


See: What’s New: MDTI Interoperability with Microsoft 365 Defender
Data sets
Microsoft centralized a couple of different data sets into the Defender TI platform. Microsoft provides as much data as possible which gives useful insights from analysts/security points of view. Microsoft collects internet data via its’ PDNS sensor network, global proxy network of virtual users, port scans, and leverages third-party sources for malware and added Domain Name System (DNS) data.

The following data sets are available:
- Resolutions
- Whois
- Certificates
- Subdomains
- Trackers
- Components
- Host pairs
- Hashes
- Cookies
- DNS
- Reverse DNS
Microsoft explains all the futures more in-depth for each data set. Defender TI Data sets | Microsoft Docs
Defender TI Premium vs. Defender TI Free
Defender TI Premium contains more features in comparison with the Defender TI Free solution. Without any premium license, only free content is available. Of course; there is a difference between the two offerings.
Note: Currently there is no official comparison available. Let’s compare the portals (free vs. paid).
Free version: Shows 2053 articles

Paid version: Shows 2362 articles
As you can see in the image there are more recent threat articles available in the premium version. In the premium version, Microsoft shares more often new articles.

Compare indicator
Logincyberdemo(.)com is used as a test site for the Evilginx/ AiTM blog post. Interesting is the difference between the free and premium plans for the newly discovered domain name.
- Light theme = free
- Dark theme = premium


In Defender TI Premium there is more data based on reputation and insights. Defender TI Premium shows Reputation-based score and analytics insights. The domain is newly registered and shows the label; New subdomain 6 days ago. Microsoft gives the domain a reputation score of 65; calculated based on Registar/ Resolving IP Address rule. ( 0-100 higher more suspicious)
Interesting is the data section. Part of the data is additional RAW data which is discovered based on the domain. Here is a difference; where the free version shows loading errors for Whois, Host Pairs, and Cookies, (not loading when copying the same URL).


For Defender TI Premium it is interesting to see the additional Cookies information. When used for AiTM phishing Defender TI detects the used cookies and shows, for example, the used Microsoft cookies; MicrosoftApplications and other Microsoft cookies

When clicking on the cookie it is possible to see the additional relations and view other detected websites where the cookie is used.
Defender TI Premium shows more historic data. The free version is showing 14 days of historic data.

Compare articles
Defender TI Premium shows more articles. Newer articles are only available in the premium plan and released after some weeks in the free plan. Based on the available indicators (Public indicators / Defender TI indicators) only the premium plans shows the Defender TI Indicators. Article descriptions contain more information about the attack or attacker profile. Longer descriptions may contain images, links, and preventions.

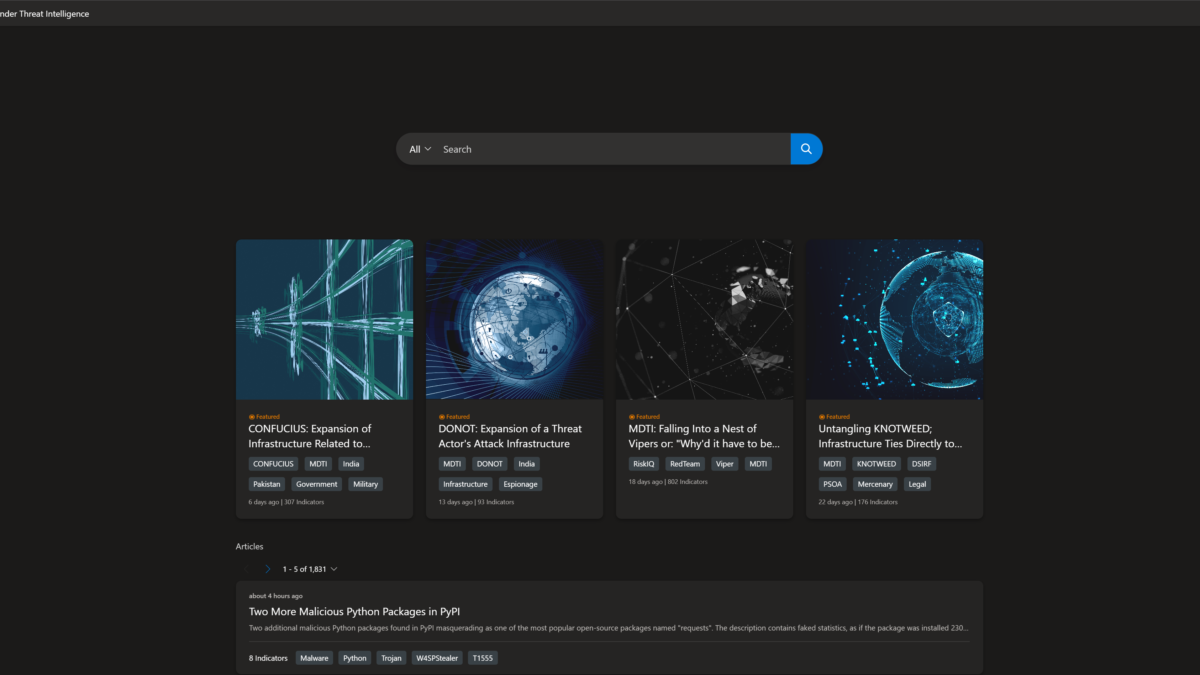
The Defender TI indicators section covers the indicators that Defender TI’s research team has found and added to the articles.
All articles are listed under the Microsoft Defender TI Threat Intelligence Home Page articles section, ordered by creation date (descending). The featured article section of the Defender TI Home Page shows the featured Microsoft content.

Differences Free vs Paid

Compare Malicious domains
Based on DEV-0196 there are some interesting differences. In free and premium the description of the article is the same and contains intelligence brief information/ references. The same for the public indicators. Interesting is when opening one of the indicators. Based on the premium there is some nice addition based on the reputation calculation and analytics insights which make the investigation easier with the malicious/reputation score and analyst insights.
Free version: Shows only basic information and attached articles

Paid version: Shows additional reputation and analytics insights.

Based on the reputation score there is directly more visibility – where you can see the indicator is part of the RiskIQ Intel article and more information.
Compare WHOIS data
Historic WHOIS information is only available in Defender TI Premium. In Defender TI Free there is only the latest record available in the WHOIS lookup.
Defender TI shows the current Whois lookup and historical Whois lookups. Defender TI’s Whois History repository provides all known historical domain associations to Whois attributes based on the system’s observations.

More dataset information: Microsoft Defender Threat Intelligence (Defender TI) Data Sets | Microsoft Learn
Reputation scoring

Part of Defender TI Premium is the reputation scoring model. Reputation Scores are determined by a series of factors. Microsoft explains the scoring based on the following order:
Reputation Scores are displayed as numerical scores with a range from 0 to 100. An entity with a score of “0” has no known associations to suspicious activity or known indicators of compromise; a score of “100” indicates that the entity is malicious.
| Score | Category | Description |
|---|---|---|
| 75+ | Malicious | The entity has confirmed associations to known malicious infrastructure that appears on our blocklist and matches machine-learning rules that detect suspicious activity. |
| 50 – 74 | Suspicious | The entity is likely associated to suspicious infrastructure based on matches to three or more machine learning rules. |
| 25 – 49 | Neutral | The entity matches at least two machine learning rules. |
| 0 – 24 | Unknown (Green) | If the score is “Unknown” and green, the entity has returned at least one matched rule. |
| 0 – 24 | Unknown (Grey) | If the score is “Unknown” and grey, the entity has not returned any rule matches. |
More information can be found here: Defender TI Reputation scoring | Microsoft Docs
Analyst insights

Analyst Insights gives quick insights about the artifacts to help during the investigation. Currently, the following Analyst insight types are available in Defender TI;
| Analyst insight types | Questions they can address |
|---|---|
| Blocklisted | Is/when was the domain, host, or IP address blocklisted? |
| How many times has Defender TI blocklisted the domain, host, or IP? | |
| Registered & Updated | How many days, months, years ago was the domain registered? |
| When was the domain WHOIS Record updated? | |
| Subdomain IP count | How many different IPs are associated with the subdomains of the domain? |
| New subdomain observations | When was the last time Microsoft observed a new subdomain for the domain in question? |
| Registered & Resolving | Does the domain queried exist? |
| Does the domain resolve to an IP address? | |
| Number of Domains sharing the WHOIS record | What other domains share the same WHOIS record? |
| Number of domains sharing the Name Server | What other domains share the same name server record? |
| Crawled by RiskIQ | When was this host or domain last crawled by Microsoft? |
| International Domain | Is the domain queried for an international domain name (IDN)? |
| Blocklisted by Third Party | Is this indicator blocklisted by a third party? |
| Tor Exit Node Status | Is the IP address in questions associated with The Onion Router Network (Tor)? |
| Open Ports Detected | When did Microsoft last port scan this IP address? |
| Proxy Status | What is the proxy status of this indicator? |
| Host Last Observed | Is the IP address in question internet accessible? |
| Hosts a Web Server | Does the IP address have a DNS server that uses its resources to resolve the name into it for the appropriate web server? |
Example: Domain logincyberdemo.com with the malicious score of 100 and detected by the rule: Microsoft Blocklist(watchlist) and description: This indicator relates to an emerging threat actor DEV-0563

More information can be found here: Defender TI Analyst Insights | Microsoft Docs
Comparison table ( Free vs Paid)
Notice: There is currently no official comparison table between the free and paid services. Based on a comparison between Free and Premium it seems the following is the difference:
| Feature | Defender TI Free | Defender TI Premium |
|---|---|---|
| Articles | ✅ New articles first in Premium | ✅Directly available |
| Intel profiles | ❌ | ✅ |
| Articles description | ✅ | ✅ |
| Articles Public Indicators (OSINT) | ✅ | ✅ |
| Articles Defender TI indicators (MDTI) | ❌ | ✅ |
| OSINT IOCs | ✅ | ✅ |
| MDTI IOCs | ❌ | ✅ |
| Reputation | ❌ | ✅ |
| Analytics insights | ❌ | ✅ |
| Data: Historic data | ❌ 14 days only | ✅ |
| Data: Whois information | ✅ no history | ✅ |
| Data: Whois historic information | ❌ | ✅ |
| Data: Resolutions | ✅ 14 days only | ✅ |
| Data: Certificates | ✅14 days only | ✅ |
| Data: Subdomains | ❌ | ✅ |
| Data: Trackers | ✅14 days only | ✅ |
| Data: Components | ✅14 days only | ✅ |
| Data: Host pairs | ❌ | ✅ |
| Data: Hashes | ✅14 days only | ✅ |
| Data: Cookies | ❌ | ✅ |
| Data: DNS | ✅ 14 days only | ✅ |
| Data: Reverse DNS | ✅ 14 days only | ✅ |
The following message is visible when the dataset is only available to accounts assigned with a premium MDTI license:

Indicators
Defender Threat Intelligence shows multiple indicators. There are two types of indicators (Public Indicators/ Defender TI indicators).
Defender TI are the indicators that the Defender TI research team has found and added to the articles. The public indicators section is related to all underlying Defender TI data or external data sources.

Intel profiles
Intel profiles were recently announced and are part of Defender TI. With the use of the new Intel profiles, there is an insight into the threat ecosystem including threat actors/ vulnerabilities and the used infrastructure.
Intel Profiles are visible directly in the Defender TI portal or the Microsoft 365 Defender Portal. When there is a license active the Defender TI data is directly visible in the Microsoft 365 portal.

Intel Profiles are segmented into two specialties: Threat actors and Tools. Microsoft used automated discovery for checking across the worldwide infrastructure and mapped it all together.
- Threat actors: For example Aqua Blizzard/ Brass Typhoon/ Cadet Blizzard.
- Threat tools: For example AppleJeus/ AsyncRat/ BazaLoader, Cobalt Strike
Intel Profiles – Cobalt Strike tool; directly from the page all detected indicators are visible.

Threat actors – Mango Sandstorm aka Mercury, MuddyWater, SeedWorm. The threat actors profile contains the available information like country/region of origin and known targets/ defender TI indicators.

The detailed page contains the threat actor description/ available TTPs and available indicators.

Detonation analysis
Detonation analysis is part of Defender TI and provides additional insights about the file hash or URL and associated links to the articles. Detonation intelligence is available for the following types:
- File Hash
- URL
Defender TI leverages Microsoft’s threat intelligence through static and dynamic analysis for analysis of the files with more in-depth detonation. Microsoft uses dynamic analysis in a controlled environment to detect and check the behavior of the file/ URL.
When detonation is available the result is directly visible in the portal:
Detonation for file hash:


Detonation for URL:
When searching URLs with HTTP:// or HTTPS:// the detonation view is visible. When the detonation analysis is visible the analysis shows the HTTP response code/ final URL and resolved IP address and includes a screenshot.

Domain redirects to Microsoft sign-in page/ common credential-stealing attack:

Microsoft Sentinel integration with Defender TI/ MDTI
When using the Microsoft Sentinel MDTI connection it is possible to use the connection without a premium license. All IOCs will be sent to the TI blade and the Threat intelligence indicator table in Sentinel. Currently, MDTI collects the following TI feeds as part of the connector:
- MDTI OSINT/ available free IOCs
- SONAR IOCs
- MSTIC Nation State IOCs
- Other IOCs (not defined exactly)
The Threat Intelligence data connector is an add-on data connector and provides a full feed of IOCs to be used to match with the event data. There will be a cost for the ingested IOCs.

All Defender TI indicators will be stored in the Threat Intelligence view and ThreatIntelligenceIndicator Log Analytics table.


Use the following query to summarize the indicators by threat type (C2/ Botnet/ Watchlist/ MaliciousUrl) and see the count of ingested indicators.
ThreatIntelligenceIndicator
| summarize count() by ThreatType
Threat Intelligence Analytics rule
The Threat Intelligence Analytics rule only matches when the IOC is matched based on the collected logs and creates an alert/incident when the match is identified.
The “(Preview) Microsoft Defender Threat Intelligence Analytics” Analytics rule runs every hour and correlates indicators against the ingested logs ingested in the Sentinel/ Log Analytics workspace.

More in-depth information focussed on available integrations/ automation and Logic Apps is explained in the following blog: Microsoft Defender Threat Intelligence (Defender TI) integrations with Microsoft Sentinel
Conclusion
Defender Threat Intelligence combines multiple sources in one platform and correlates data in articles and additional sources. Microsoft Defender Threat Intelligence (Defender TI/ MDTI) makes the platform interactive and combines multiple sources in one single view which saves time and security resources.
Hopefully, more features are coming for more in-depth integration with other products in the future. Next blog; more information scoped on Microsoft Sentinel, Microsoft 365 Defender, and Defender for Cloud integrations based on Microsoft Defender Threat Intelligence.
Sources
Microsoft: What is Defender Threat Intelligence (Defender TI)
Microsoft Sentinel: New Threat Intelligence features in Microsoft Sentinel
Microsoft: What’s New: Intel Profiles Deliver Crucial Information, Context About Threats




What are the advantages for customers in terms of accessing real-time data and signals to proactively detect and respond to threats in their environments?
The pricing scheme looks strange to me on the Microsoft portal. Do I understand it correct it is per-user-per-year? So every cybersecurity analyst needs a license? Or is it assumed there’s one (API) user that pulls the data. With 25+ analysts this is becoming expensive quickly I would say.