During Ignite ’21 Microsoft announced multiple new functionalities, renames, and new products. In the upcoming weeks, more blogs are coming with new features which are in preview or GA. This blog is all about the new Identity Protection Risk Analysis workbook. Useful for more in-depth insights based on Azure AD Identity Protection data.
Identity Protection
Risk data is part of Azure AD Identity protection. Azure AD Identity Protection is all about risk, detection, and remediation based on the identity user level. Microsoft uses threat intelligence for specifying the risk levels.
Two main risk detection components are part of the Azure AD Identity Protection solution:
- Sign-in risk
- User-risk
Azure AD stores reports and security signals for a defined period. Below is the table with the max retention period for AzureAD free, AADP1, and AADP2 for each of the signals. With AADP2 the max retention period is 30 days for the audit logs, sign-ins, risky sign-ins, and AzureAD MFA usage.
| Report / Signal | Azure AD Free | Azure AD Premium P1 | Azure AD Premium P2 |
|---|---|---|---|
| Audit logs | 7 days | 30 days | 30 days |
| Sign-ins | 7 days | 30 days | 30 days |
| Risky users | No limit | No limit | No limit |
| Risky sign-ins | 7 days | 30 days | 90 days |
More Azure AD Identity Protection information is available in one of the previous blogs.
AAD Diagnostic settings
Before we can use the new preview workbook, it is required to enable the Risk log events in the diagnostic settings and share the data directly into a Log Analytics workspace or Microsoft Sentinel.
From the Diagnostic settings panel, it is possible to stream risk events from Azure AD Identity Protection into Microsoft Sentinel/ Log Analytics based on two new tables. After the enablement the following tables will be created:
- AADUserRiskEvents
- AADRiskyUsers
Both new events tables are needed for the new Identity Protection Risk Analysis workbook.
For sending the RiskyUser and UserRiskEvents data to a Log Analytics workspace, storage account or Event hub go to the Azure Active Directory diagnostic setting:
Azure portal > Azure Active Directory, Diagnostic settings
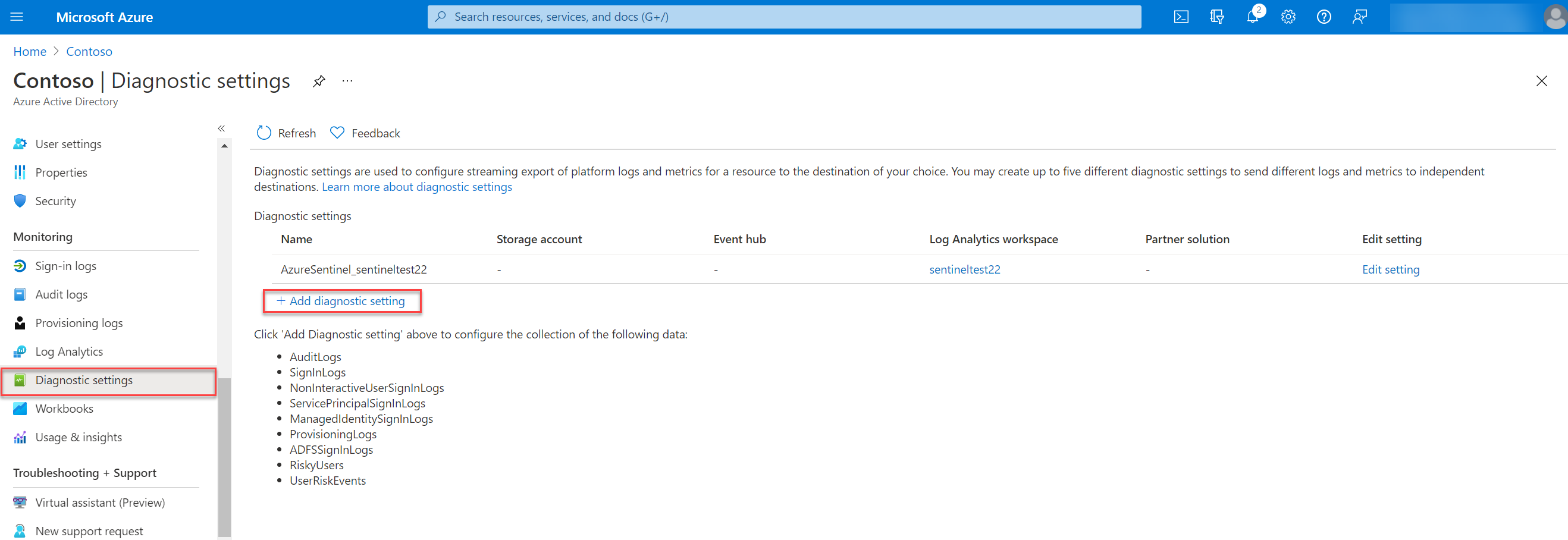
The next step is to fill in the diagnostic settings name and select the category details and destination details. First the category details:
Log category details
For configuring the specific log event collector, select RiskyUsers and UserRiskEvents or more if needed for further investigation.
Destination details
For exporting events into Log Analytics/ Microsoft Sentinel use the option; Send to Log Analytics workspace. For sending events into the Azure Sentinel workspace – select the subscription and workspace.
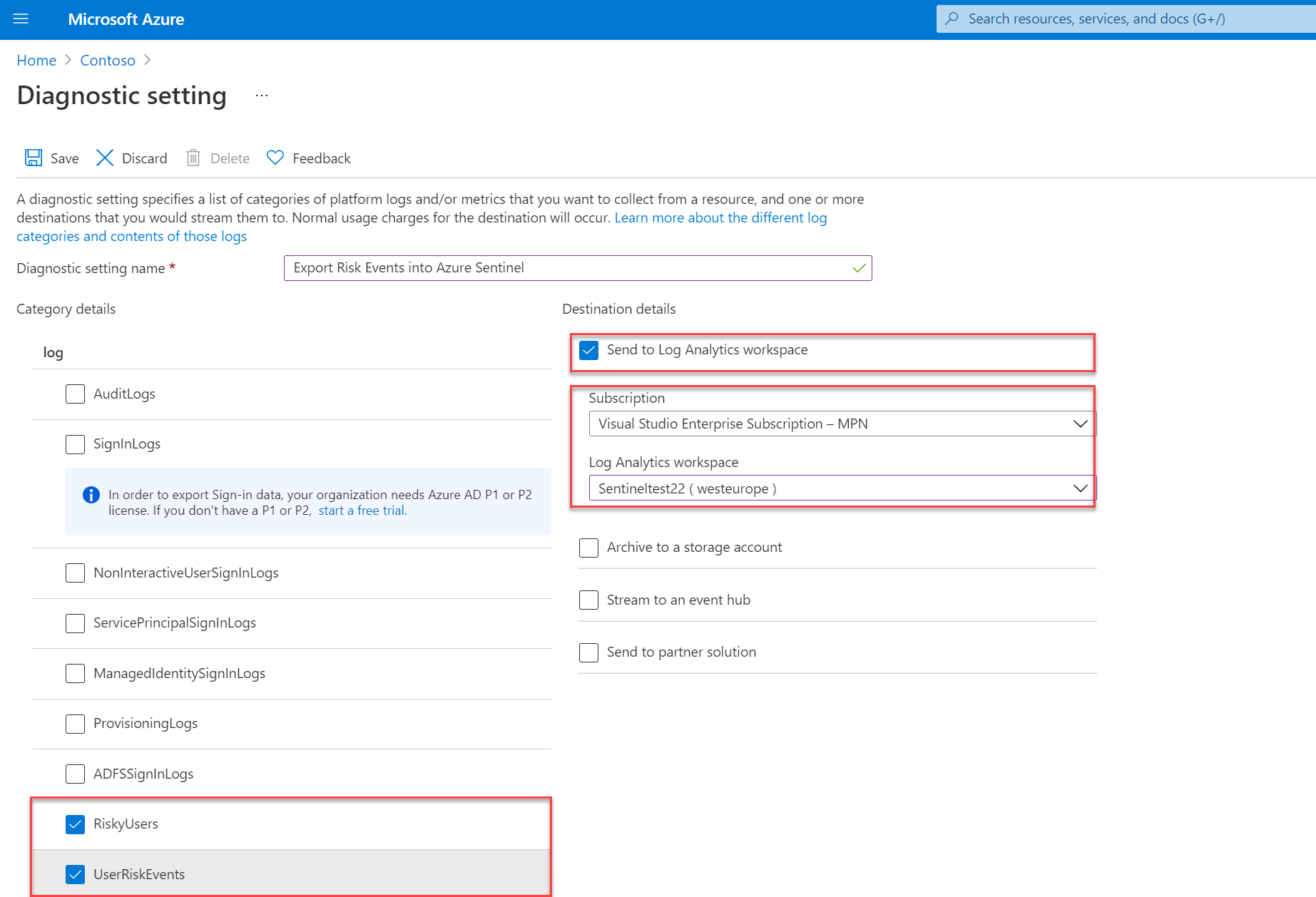
Once enabled two new data tables are available in the Log Analytics workspace. Based on the RiskyUsers and UserRiskEvents log the following tables are available:
- AADRiskyUsers – Provides data like the Risky users report in Identity Protection
- AADUserRiskEvents – Provides data like the Risk detections report in Identity Protection
For integration with Microsoft Sentinel and data hunting check this blog with multiple examples and advanced hunting views.
Identity Protection Risk Analysis workbook
The Identity Protection Risk Analysis workbook is available in the Azure AD Portal. For using the portal use the following link: portal.azure.com
For opening the new workbook:
- Open portal.azure.com
- Go to Azure Active Directory
- Open Workbooks
- Now open the Identity Protection Risk Analysis workbook

Report data/ visuals included
The new workbooks contain multiple useful views for the average detections or investigation view. The following data is available in the new Risk Analysis workbook:
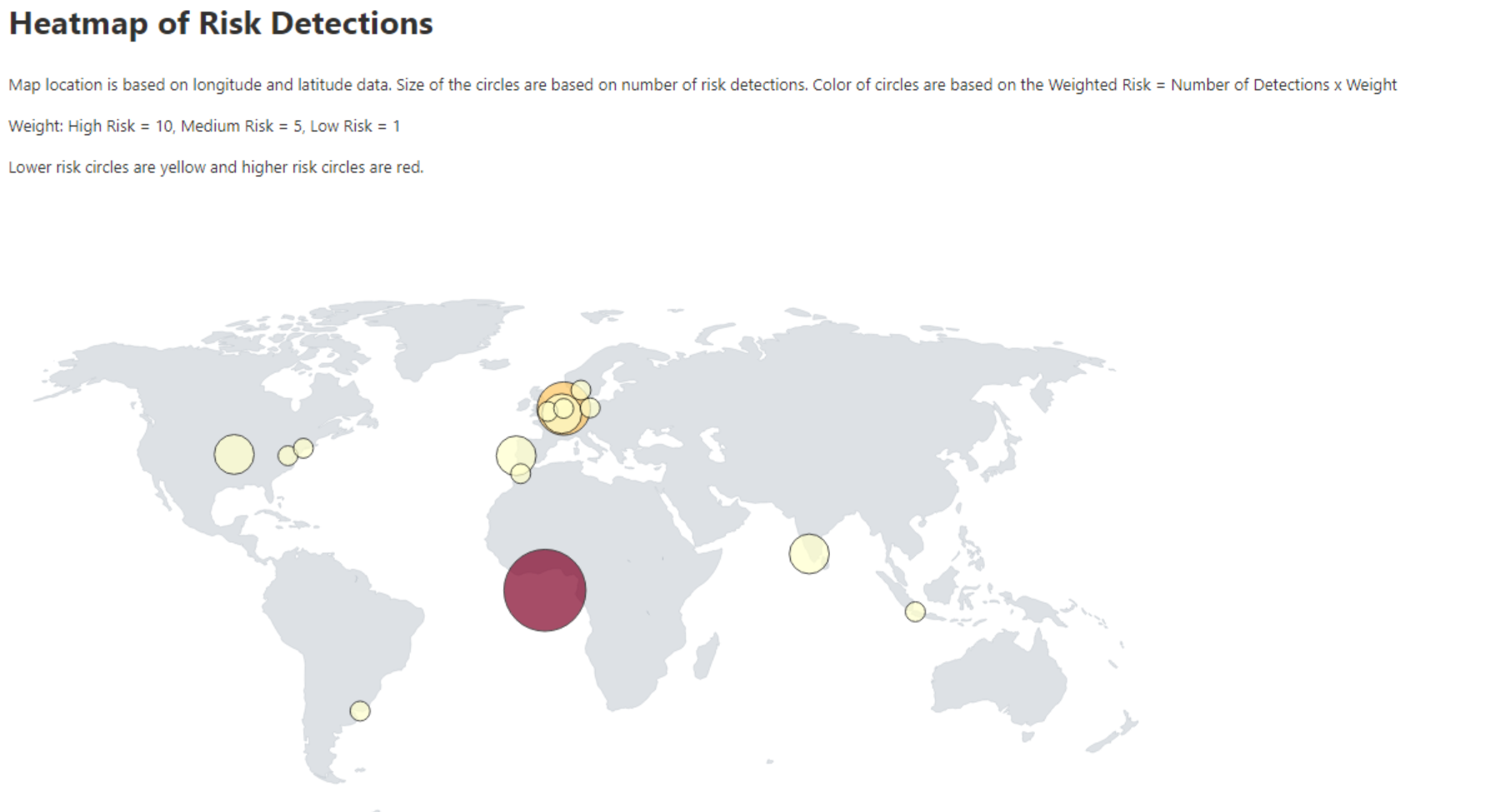
Map Location
Map location contains the location of the sign-in based on longitude and latitude data. The size of the circles is based on the number of risk detections. The color gives the weighted risk calculation: Weighted Risk = Number of Detections x Weight.
Offline vs Real-Time Risk Detections
Azure AD Identity Protection contains multiple detection/calculations: Real-Time and Offline. Two examples for explaining more the difference between Offline – Real-time Risk Detections.
Real-time Risk Detections:
- Anonymous IP address
- Unfamiliar sign-in properties
Offline Detection:
- Password spray
- Atypical travel
Notice: Real-time detections may not show up in reporting for five to 10 minutes. Offline detections may not show up in reporting for 48 hours.
The graph shows the Hourly Risk Detection and the Total count of detections. Visible for offline vs Real-Time Detections.

Risk Detection Trends
Following trends in the organization is important. For AAD Identity Protection trend visibility is possible with the Risk Analysis workbook. Multiple blocks are available for detection of the trend for different types, detections, and levels.
The following data is available:
- Hourly Risk Detections by Level
- Total Count by Risk Level

- Hourly Risk Detections Event Type
- Total Count by Risk Event Type

- Count of Risk Detections by User
- Risk Detections by IP Address

Risky Users
With the User Risk status, the identity is probability compromised. Microsoft calculated the risk based on internal and external threat intelligence sources and different detections for calculating the Risky User status.
From the user-level interesting information is available:
- Daily Count of Users by Risk Level
- Total Count of Users by Risk Level

- Users with changes in Risk Level
- Action taken on Risky Users
- High-Risk Users by Time Generated
- Medium Risk Users by Time Generated
With the data inside the workbook, you can easily track the daily count of users by each level and the total count of users, and the difference/actions are taken on Risky Users.
Summary
The summary gives the summary of risk detection by Risk Level and the summary of Risky Users by Risk Level
Conclusion
Protecting the Azure AD Identity is important. Azure AD Identity Protection enables protection for AzureAD-accounts. With the new Identity Protection Risk Analysis workbook more details and history graphs are visible based on the security identity risk events.
More Azure AD Identity Protection information is available in one of the previous blogs.




