Since April 11th, 2022, the new unified Microsoft Defender for Endpoint solution is generally available for Server 2016 and Server 2016. The unified Microsoft Defender for Endpoint solution enables more features that were previously only available on Windows Server 2019 and later. The new modernized solution stack enables more security features for Server 2012R2 and Server 2016.
August 18, 2022; Blog completely rewritten based on latest announcement and improvements; included MECM/ Defender for Cloud and updated information since GA release.
Previous method
Previously there was a large gap between the latest Server 2019 build and the down-level OS systems. In comparison with Server 2019, the onboarding process was quite complex with the Microsoft Monitoring Agent. The MMA agent was required as the EDR sensor wasn’t built-in, for Server 2016 en Server 2012R2.
Server 2016 is by default installed with Microsoft Defender Antivirus. For Server 2012R2 there was no installed AV by default, and you had to install System Centre Endpoint Protection (SCEP).
With the Microsoft Monitoring Agent and Defender AV/SCEP, there were still some missing protection features – like Attack Surface Reduction, Automated Investigation, Network Protection, and many more protection features.
Now the good news. Currently in general availability is the new unified solution for Server 2012R2 and Server 2016. The new unified solution reduces complexity by removing dependencies and installation steps – and more important no more SCEP, MMA, and all the latest security features available.
The new unified package brings the following major improvements directly to the new Defender for Endpoint solution:
- Attack Surface Reduction rules
- Network protection
- Controlled Folder Access
- Potentially Unwanted Application blocking
- Improved detection capabilities
- Response capacibiliteits
- EDR in block mode
- Automated Investigation and Response (AIR)
- Tamper Protection
- Live Response
New Defender for Endpoint agent
The new unified solution is available in one single package for all the down-level systems. Summary for Windows Server systems:
Built-in Defender AV and EDR sensor. Only onboarding package needed for onboard
- Windows Server 1803
- Windows Server 2019
- Windows Server 2022
New unified MDE installation package and onboarding package are needed for onboard
- Windows Server 2012R2
- Windows Server 2016
Windows Server 2008R2 is currently only supported for onboarding using the legacy MMA-agent and SCEP. Advised is to migrate Server 2008R2, which makes it possible to manage all systems with a single solution and the same configuration. SCEP is legacy and missed critical protection capabilities provided by Microsoft.
Microsoft announced in the last couple of months multiple improvements which make the installation of the new unified agent way more easier from products like; Microsoft Defender for Cloud and Microsoft Endpoint Configuration Manager. Currently it is possible to migrate all existing MMA-based Defender for Endpoint solutions to the new unified agent.
Download new Defender for Endpoint agent
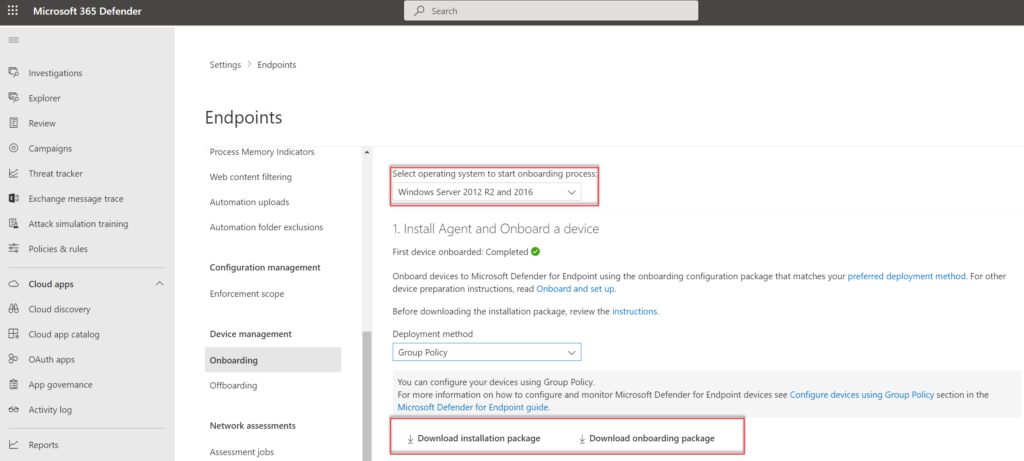
The new Defender for Endpoint installation and onboarding packages can be downloaded directly from the security.microsoft.com portal.
- Go to Security.Microsoft.com
- Open Settings -> Endpoints -> Onboarding
- Select Windows Server 2012R2 and Server 2016
- Select Deployment method; Group Policy or one of the other deployment methods
Download the installation package (md4ws.msi) and onboarding package (WindowsDefenderATPOnboardingScript.cmd).
NOTE: The package is updated monthly with new improvements. Make sure to download always the latest package before usage. The package contains the Defender product version and additional improvements.
Prerequisites for Windows Server 2012R2 and Windows Server 2016
For the new unified solution, fewer requirements are needed in comparison with the legacy method. The following requirements are needed before installing the new Defender solution.
Network
Ensure connectivity requirements are configured. Network requirements are the same as Windows Server 2019. Important: There is no OMS Gateway support for the new agent. Follow the instructions for configuring the network connectivity. Download here the spreadsheet including all URLs (WW + Defender Geography)
Server 2012R2 requirements
When the latest monthly rollup is installed – no additional prerequisites are needed for Server 2012R2. During the installer the package checks for the following updates:
- Update for customer experience and diagnostic telemetry / KB3080149
- Update for Universal C Runtime in Windows / KB2999226
Make sure both updates are correctly installed. Important; when already using SCEP it is needed to remove the SCEP agent first. Recommended is to use the installer script which automatically removes SCEP and installs additional prerequisites. (more information later in this blog)
Server 2016 requirements
For Server 2016 the build-in Defender server must be enabled. For correctly installing the new agent make sure the following prerequisites are in place.
- The Servicing Stack Update (SSU) from September 14, 2021 or later must be installed. (latest version recommended)
- The Latest Cumulative Update (LCU) from September 20, 2018 or later must be installed. (latest version recommended)
- Enable build-in Defender Antivirus
- Update the latest Defender Antivirus platform version (download package from Microsoft Update Catalog or MMPC)
Manual installation
Installation of the new Defender for Endpoint agent is simple when the prerequisites are correctly in place. md4ws.msi supports additional parameters:
Silent installation:
Msiexec /i md4ws.msi /quietSilent installation + configuration in passive mode:
Msiexec /i md4ws.msi /quiet FORCEPASSIVEMODE=1Passive mode
If there is a default non-Microsoft antivirus/antimalware solution available it is directly possible to enable the passive mode for the Microsoft Defender Antivirus components. using FORCEPASSIVEMODE=1
For making sure Defender for Endpoint is correctly configured in passive mode after the initial onboarding the “ForceDefenderPassiveMode” need to be added.
- Path:
HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection - Name:
ForceDefenderPassiveMode - Type:
REG_DWORD - Value:
1
During the installation the following error can be visible; Please update Windows Defender. When the error is showing make sure the latest Defender platform update is installed for Server 2016.
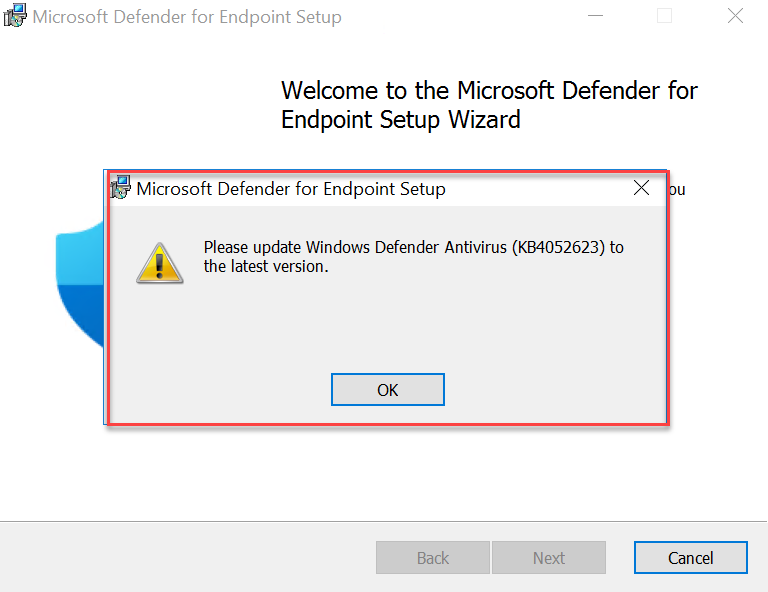
For checking the current platform version. Use the PowerShell command: Get-MpComputerStatus and check the value: AMProductVersion

Scripted installation
Microsoft published a GitHub installation script that automated most of the migration/ installation steps. The script can help with automating the following steps:
- Remove the OMS workspace for Microsoft Defender for Endpoint
- Remove System Center Endpoint Protection (SCEP) client if installed on Server 2012R2
- Download and install (Windows Server 2012 R2) prerequisites if required.
- Trying to active Defender on Windows Server 2016
- If Defender is installed and running but outdated, it updates to the latest platform version on Windows Server 2016 when the state is upgradeable (see prerequisites)
- Install Microsoft Defender for Endpoint
- Onboard Defender for Endpoint
More information and download: upgrade script | Github
Install and remove the MMA agent (replace <WORKSPACE_ID> with the actual MMA agent ID)
.\Install.ps1 -RemoveMMA <WORKSPACE_ID> -OnboardingScript ".\WindowsDefenderATPOnboardingScript.cmd"Install and configure passive mode
.\Install.ps1 -OnboardingScript ".\WindowsDefenderATPOnboardingScript.cmd" -Passive-Passive
The parameter -Passive enabled Defender Antivirus in passive mode. Make sure to set the “ForceDefenderPassiveMode” registry key on all servers for getting the passive mode enabled after the Defender for Endpoint onboarding.
Path: HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection
Name: ForceDefenderPassiveMode
Type: REG_DWORD
Value: 1
Passive mode can be disabled when changing the value from 1 to 0. Passive mode can be used when migrating from non-Microsoft antivirus solutions.
The result after installing and onboarding with the installer script:

For Server 2012R2 and Server 2016 the Sense service is enabled after completing the MDE onboarding script.

Install/Migrate in Defender for Cloud
When using Defender for Cloud for Server 2012R2 and Server 2016 onboarding the new Defender for Servers Plan 1/2 integration can be used for automatically installing or migrating from the MMA-based Defender solution.
MDE integration with Defender for Servers P2 is by default the new solution for new Defender for Cloud activations or new subscriptions. When Defender for Servers P2 was enabled before June 20th, 2022, or MDE integration was enabled before June 20th, 2022, the new Enable Unified Solution button is visible.
The following options are available:
- Migrate all machines in subscriptions using Enable Unified Solution button
- Testing particular machines using REST API without enabling the complete subscription
- Deploying using Azure Policy
One of the following situations is mostly available in environments;
- Defender for Servers is already enabled and Microsoft Defender for Endpoint was deployed (MMA solution)
- Defender for Servers integration was never enabled
To enable the MDE unified solution in existing subscriptions you can easily opt-in to the unified solution on the subscription environment settings/integrations page. For opening the settings:
- Go to Defender for Cloud
- Go to Environment settings and select the subscription
- Go to Integrations
The button Enable unified solution is visible when the MDE integration was enabled before June 20th, 2022.
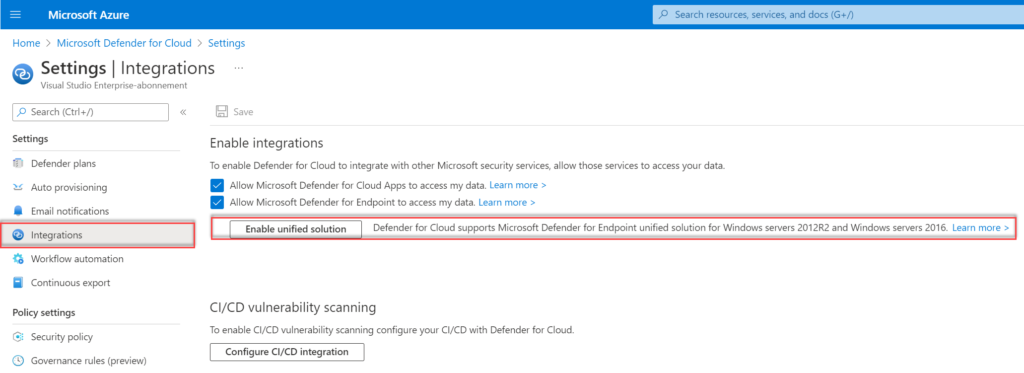
After enablement, it can take up to 12 hours before the extension is installed and MMA is replaced with the new Defender solution. Microsoft uses a version of the Defender script for uninstalling SCEP and installing the new solution. View the following blog for more information; How to upgrade from MMA-based Defender for Endpoint to MDE unified solution in Defender for Cloud?
Install using Microsoft Endpoint Configuration Manager
Since update 2207 for Microsoft Endpoint Configuration Manager current branch the improved Defender for Endpoint onboarding for Windows Server 2012R2 and Windows Server 2016 is finally available.
Since version 2207 Configuration Manager version 2207 supports the automatic installation of the new unified Microsoft Defender for Endpoint agent.
Migration is possible using the Client Settings which are used previously for MMA/ SCEP.
Migrating from SCEP
- Change the Client settings used for Endpoint Protection and change from Microsoft Monitoring Agent MMA (legacy) to MDE client (recommended).
- Configure the Defender for Endpoint onboarding file downloaded from security.microsoft.com
- Upload the .onboarding file and configure file sample collection
Client settings can be founded under Endpoint Protection
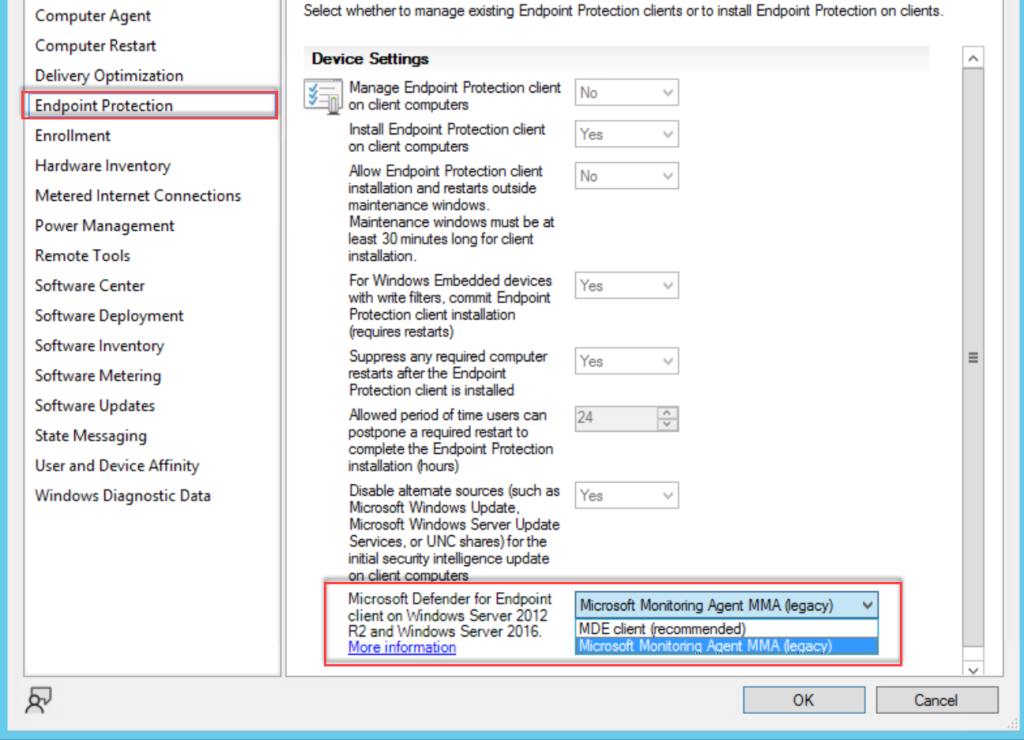
Go to Assets and Compliance > Endpoint Protection > Microsoft Defender ATP Policies and select Create Microsoft Defender ATP Policy and upload the downloaded onboarding file from security.microsoft.com. (use the Deployment method; Microsoft Endpoint Configuration Manager current branch and later)
Note: For Server 2008R2 and older MDE-supported down-level systems it is still needed to use Microsoft Monitoring Agent (MMA) (legacy) in the Client Settings and use the workspace key + workspace ID. Server 2012R2/ Server 2016 works via the .onboardingfile and the new MDE client setting; where Server 2008R2 works only with the MMA configuration.
Differences in portal
After onboarding, the new features are visible on the device page. The following actions are now available in comparison with the legacy MMA situation:
- Isolate devices
- Run Antivirus Scan
- Collect Investigation Package
- Initiate Live Response Session (now supported)
- Initiate Automated Investigation (now supported)
Server 2016 ( legacy MMA)

Server 2016 (new MDE unified solution agent)

Configuration
With the new Unified Solutions all the Group Policy, PowerShell commands, and other management options similar to Server 2019 are available for Server 2012R2 and Server 2016. You can use the Group Policy templates for Server 2019 to manage Defender on Windows Server 2012R2 and 2016. The following methods are available:
- Microsoft Endpoint Configuration Manager
- GPO
- PowerShell
- Security Management feature in MEM (advised and supported for the new agent)
View the following blog for more in-depth MEM for MDE management details; Managing Microsoft Defender for Endpoint with the new Security Management feature in MEM
Configuration – Attack Surface Reduction
Attack Surface Reduction is with the new unified solution available. Based on the Server OS there are some differences in the ASR support.
| ASR Rule | ID | Server 2016 | Server 2012R2 |
| Block abuse of exploited vulnerable signed drivers | 56a863a9-875e-4185-98a7-b882c64b5ce5 | Yes | Yes |
| Block Adobe Reader from creating child processes | 7674ba52-37eb-4a4f-a9a1-f0f9a1619a2c | Yes | Yes |
| Block all Office applications from creating child processes | d4f940ab-401b-4efc-aadc-ad5f3c50688a | Yes | Yes |
| Block credential stealing from the Windows local security authority subsystem (lsass.exe) | 9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2 | Yes | Yes |
| Block executable content from email client and webmail | be9ba2d9-53ea-4cdc-84e5-9b1eeee46550 | Yes | Yes |
| Block executable files from running unless they meet a prevalence, age, or trusted list criterion | 01443614-cd74-433a-b99e-2ecdc07bfc25 | Yes | Yes |
| Block execution of potentially obfuscated scripts | 5beb7efe-fd9a-4556-801d-275e5ffc04cc | Yes | Yes |
| Block JavaScript or VBScript from launching downloaded executable content | d3e037e1-3eb8-44c8-a917-57927947596d | Yes | No |
| Block Office applications from creating executable content | 3b576869-a4ec-4529-8536-b80a7769e899 | Yes | Yes |
| Block Office applications from injecting code into other processes | 75668c1f-73b5-4cf0-bb93-3ecf5cb7cc84 | Yes | Yes |
| Block Office communication application from creating child processes | 26190899-1602-49e8-8b27-eb1d0a1ce869 | Yes | Yes |
| Block process creations originating from PSExec and WMI commands | d1e49aac-8f56-4280-b9ba-993a6d77406c | Yes | Yes |
| Block untrusted and unsigned processes that run from USB | b2b3f03d-6a65-4f7b-a9c7-1c7ef74a9ba4 | Yes | Yes |
| Use advanced protection against ransomware | c1db55ab-c21a-4637-bb3f-a12568109d35 | Yes | Yes |
| Block Win32 API calls from Office macros | 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b | No | No |
| Block persistence through WMI event subscription | e6db77e5-3df2-4cf1-b95a-636979351e5b | No | No |
Configuration – Network Protection
For enabling Network Protection, additional configuration is required. For Server 2012R2 and Server 2016 additional configuration is needed for Network protection. Use the below PowerShell commands for enabling the NetworkProtection feature.
Set-MpPreference -EnableNetworkProtection Enabled
Set-MpPreference -AllowNetworkProtectionOnWinServer 1
Set-MpPreference -AllowNetworkProtectionDownLevel 1
Set-MpPreference -AllowDatagramProcessingOnWinServer 1
Set-MpPreference -AllowSwitchToAsyncInspection $True
Update maintenance
Important is to apply the latest updates which are supported for Server 2012R2 and Server 2016. KB5005292 is released for updating Microsoft Defender for Endpoint. This update services the EDR sensor included in the new Microsoft Defender for Endpoint unified solution and is needed for Server 2016 / 2012R2 based on the EDR sensor component. Important: Make sure the new update is deployed to receive features and fixes.
Result: Automated Investigation & Response AIR
Automated Investigation and response (AIR) is working and exactly the same in comparison with Windows 10+/ Server 2019+
Server 2016:

Server 2012R2:
Result: Live Response
Live response is supported and working exactly the same in comparison with Windows 10/ Server 2019.
Server 2016:
Server 2012R2:
Good to know
- Operating system upgrades aren’t supported. Offboard then uninstall before upgrading
- Automatic exclusions for server roles aren’t supported on Windows Server 2012 R2
- No UI is available on Windows Server 2012R2 (use PowerShell cmdlets)
More limitations can be founded here
Conclusion
The new Defender for Endpoint unified solution for Server 2012R2 and 2016 works way easier in comparison with the legacy MMA onboarding method. The new unified solution package reduces complexity by removing dependencies and installation steps. It also standardizes capabilities and functionality for the complete Defender for Endpoint stack.
Oh.. and it is always a good idea to upgrade Server 2012R2 and 2016 to one of the latest Server versions. Don’t stay behind if you can upgrade easily to Server 2019 or higher.
Sources
- Microsoft: Defending Windows Server 2012 R2 and 2016
- Jeffreyappel.nl: How to upgrade from MMA-based Defender for Endpoint to MDE unified solution in Defender for Cloud
- GitHub: MDE installer script
- Microsoft: Onboard Windows servers to the Microsoft Defender for Endpoint service
- Microsoft: Attack Surface Reduction (ASR) rules




Can you run both the legacy MMA agent and the new Microsoft Defender for Endpoint Agent at the same time?
MMA is used for Sentinel and the new MDE Unified Agent will be used to close the capability gap between my down-level servers and Up-level servers.
Yes – MMA is possible when using Sentinel. The new Defender for Endpoint unified agent is not using MMA or AMA.
For getting events – can be interesting for checking the AMA agent for collecting logs via DCR-rules.
Hi Jeffrey, thanks for the advice. One more question for you if you don’t mind. I’m struggling to apply the ASR rules to any server via the standard SCCM Exploit Guard section. Is there anything fancy you have to do to allow the ASR rules to stick to a collection? My antivirus policies are applying fine, just the ASR ones aren’t working.
If I apply the ASR rules via domain GPO they will stick to the devices with no problem.
Thoughts?
Yes – the answer is simple; the SCCM Exploit Guard section is not working for servers; only workstations can be applied.
Founded no fix for getting the features enabled on servers.
Hopefully, MS improves this part of the configuration.
Hi Jeffrey, I think that blog article is one of the most insightful regarding the installation of MDE on Windows Servers. Thanks for that!
I will try to ask you my question, knowing that I could not find the answer anywhere. Here is the situation:
When you have hundreds of Azure VM servers (Win 2012 R2, Win 2016, Win 2019) with an third-party EDR in place that you want to migrate to MDE, the process is to first install/onboard MDE in passive mode, with both EDR mutually excluding each other (to avoid server crash and unnecessary fight from both AVs).
I plan to do all the process as you described and as Microsoft used to recommend (prepare – setup – onboard) but now I see this tempting option where I can just press a button in MDC Server P1 (Microsoft Defender for Cloud Server) which include MDE and automatically use a version of the Microsoft’s script in the GitHub you shared.
The question, does this script from the MDC button is intelligent enough to detect the third-party solution in place to automatically install MDE in passive mode?
Hope I explain the situation well 🙂
Hi Jeffrey, something else, on your article you’ve written the following:
“-Passive creates the following registry key:
Path: HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection
Name: ForceDefenderPassiveMode
Type: REG_DWORD
Value: 1
Passive mode can be disabled when changing the value from 0 to 1. Passive mode can be used when migrating from non-Microsoft antivirus solutions.”
The script do not create any registry key, as this has to be done manually or in a different script.
Furthermore, to deactivate passive mode, you must change the value from 1 to 0, but that I think was just a typo.
Cheers
Hi Cyrus, correct – the registry key need to be added after the initial installation. The -Passive key configured Defender AV in passive mode; when running the onboarding script the registry key need to be configured on the devices. Article is changed; 1 – 0 is indeed a typo. Thanks for the feedback.
Hi Cyrus, thanks for the compliment. Trying to do my best and publish the best content.
Defender for Cloud enables Defender for Endpoint in active mode. Currently, there is no option for automatically installing Defender in passive mode from Defender for Cloud.
The script is currently not automatically enabling MDE in passive mode.
Explained some months ago the Defender for Cloud more in-depth. https://jeffreyappel.nl/microsoft-defender-for-endpoint-series-onboard-using-defender-for-cloud-part3b/
Let me know when more assistance is required.
In-place upgrades really not supported on 2016?
I just ran a test in-place upgrade from 2016 Version 1607 (Build 1493.5786) to 2019, having previously installed and onboarded using the latest (March 2023) github install.ps1, md4ws.msi, UpdatePlatform.exe and onboarding script. The point was to document how it would fail, for those colleagues who might forget to uninstall/offboard when required. To my surprise, it didn’t fail at all – the OS update proceeded exactly as usual…
The pre-update Device is present in the portal, with the Timeline full of events like FileDelete for setup.exe > SetupPrep.exe > SetupHost.exe > services.exe …which I assume is the OS files being updated.
There’s a second, post-update Device with a new DeviceID and an empty Timeline/Inventory (expected, the update was only a couple of hours ago), but I expect this to fill up by tomorrow.
HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection\ /v ForceDefenderPassiveMode is present (now) and set to 0 as expected. So it looks like Defender was fully up and running during the OS upgrade (I don’t recall what that key/value was on 2016, prior to update, but could check my snapshot).
Has there been any improvement/change to something, which would permit the omission of the uninstall/offboard of a Server 2016 prior to in-place upgrade to 2019?
If so, that would be very useful to know for sure.
Hi Jeffrey,
I have followed all your steps and created AV and ASR policies.
They have been applied successfully on WS2022/2019 but I am having issues with ASR rules being applied to W2016 machines managed by MDE.
I have installed KB5005292 and DFE is up to date.
Any ideas?