Microsoft Defender for Business (MDB) is the new Defender product scoped for small businesses. Defender for Business is a new endpoint security solution now generally available within Microsoft 365 Business Premium and as a standalone solution. Defender for business is scoped up to 300 employees.
Blog updated 3 august 2022; added preview information for servers
Currently the following Defender for Endpoint products are available:
- Defender for Business
- Defender for Endpoint P1
- Defender for Endpoint P2
- Server 2012R2 and higher (preview)
Defender for Business is part of the Microsoft 365 Business Premium license. For customers with Microsoft 365 Business Basic or Standard you can upgrade to Business Premium or use the new standalone Defender for Business product. If you have Microsoft 365 Business Premium, Defender for Business is included.
For managing devices Defender for Business supports currently the following operating systems.
– Windows 10 Business or later
– Windows 10 Professional or later
– Windows 10 Enterprise or later
– macOS (the three most current releases are supported
Usecase of Defender for Business
As already written above, Defender for Business is enterprise Endpoint protection in an easy-to-use format for up to 300 employees. It provides components that are already part of Defender for Endpoint P1 and P2. This blog gives more explanation for the features and differences in comparison with P1 and P2.
Currently, Defender for Business is only focusing on end-user platforms. Windows, macOS, iOS, and Android clients are supported. Support for Windows and Linux servers is not yet available. Microsoft gives the following information for server platforms:
Update 03/08/2022 – added server support: Server support is now available in private preview for Defender for Business. View the announcement
“We’re adding support for Windows and Linux servers to Microsoft Defender for Business with up to 300 employees, coming later this year with an add-on solution. You will be able to manage client and server endpoints from a single experience. Windows Server experience will be the same as Windows client. Linux servers will use deployment scripts allowing you to integrate into your existing management platforms such as Chef, Puppet, and Ansible.”
Onboarding is currently possible for:
- Windows 10/11
- macOS
- iOS
License and features
For the best onboarding and security management experience it is recommended to use Defender for Business with Microsoft Intune. Intune is included in Microsoft 365 Business Premium.
There is some difference between Defender for Business (standalone) and Microsoft 365 Business Premium where Defender for Business is included. Read more here.
Other protection products part of Microsoft 365 Business Premium
Microsoft 365 Business Premium comes with some other security licensing. The following is available for customers:
Exchange and Defender for Office
Microsoft 365 Business Premium comes with Exchange Online Plan 1 and Defender for Office 365 Plan 1.
Azure AD
Microsoft 365 Business Premium comes with Azure Active Directory Premium Plan 1 and Conditional Access Plan 1.
Information protection
Microsoft 365 Business Premium comes with Azure Information Protection Premium P1.
Important Combination of P1/ P2/ Defender for Cloud
If you have an existing Microsoft Defender for Endpoint license within your tenant this will affect the administrative experience, within the Microsoft 365 Defender security portal. When the Defender for Business service is enabled, the following experience will be changed:
- Microsoft Defender for Endpoint P1 will be changed to Microsoft Defender for Business.
- Microsoft Defender for Endpoint P2 will remain in place and Microsoft Defender for Business product experience will not be seen until the Defender for Endpoint P2 license is completely removed from the tenant. At which time Defender for Business experience will be seen.
- Microsoft Defender for Servers, or Microsoft Defender for Cloud is active within the Azure tenant. This will also impact the Microsoft 365 Defender admin center and switch it to a more advanced Microsoft Defender for Endpoint Plan 2 product experience. Defender for Business experience will not be seen.
Situation: When Defender for Business is enabled and Defender for Cloud integration is enabled for Defender for Cloud; The advanced Defender for Endpoint Plan 2 experience is the default. Check always which licenses are needed for the use-case of the organization and combination of different Defender products.
More product information:
- Microsoft: New endpoint security for small and medium businesses now available with Defender for Business.
- Microsoft: Get Microsoft Defender for Business
How to configure Defender for Business?
For Defender for Business make sure the license is assigned to the signed-in user. After buying or enabling the trial the following license is available; Microsoft Defender for Business
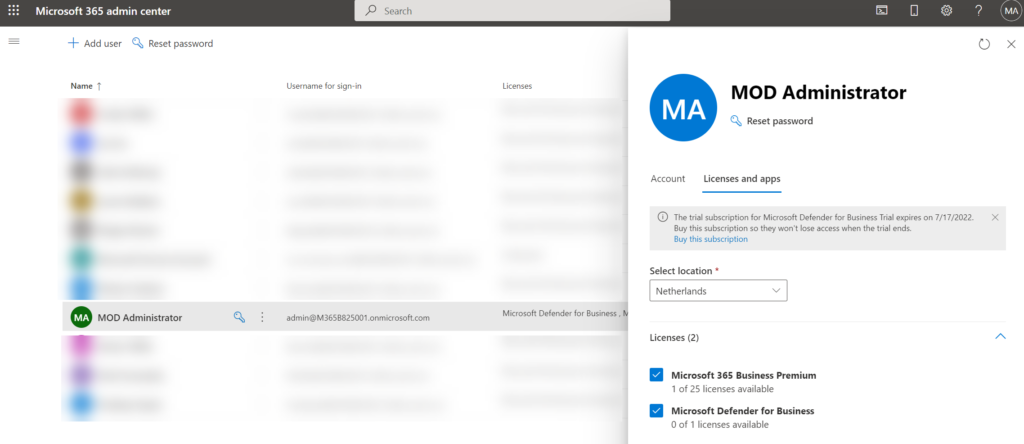
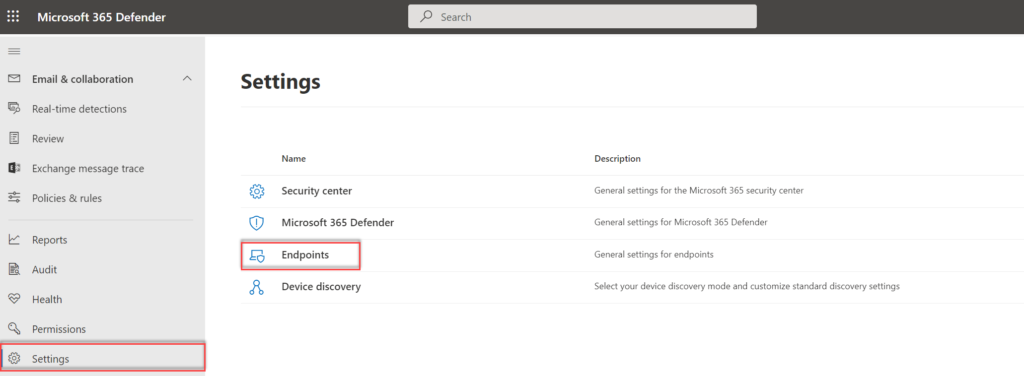
To activate the product, visit the Microsoft 365 Defender security center: www.security.microsoft.com and go to Settings > Endpoints.
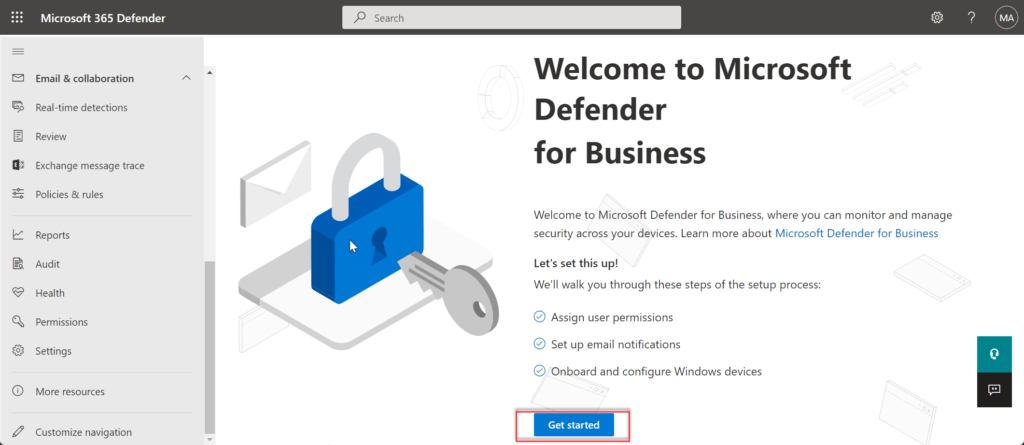
Now the “Welcome to Microsoft Defender for Business” screen is visible. Click on Get Started.
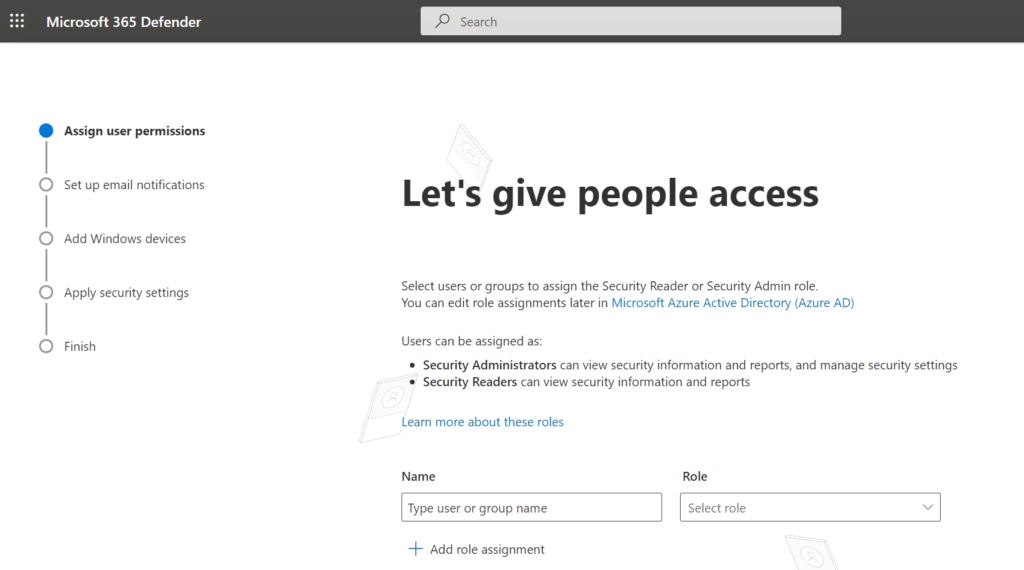
First Defender for Business setup
During the setup the end-user can directly configure user permissions, email notifications, and onboarding/ configure Windows devices.
Now we need to make sure the correct users are assigned. Directly from the security.microsoft.com wizard it is possible to assign Security Reader or Security Admin role permissions. Assignments can be created/ changed later in Azure Active Directory. Of course; it is possible to skip the configuration.
Same for the email notification. During the email notifications wizard it is possible to select recipients and the specific notification type. it is possible to send notifications for alerts, vulnerabilities or alerts & vulnerabilities. The wizard creates rules in the email notification settings part of security.microsoft.com.
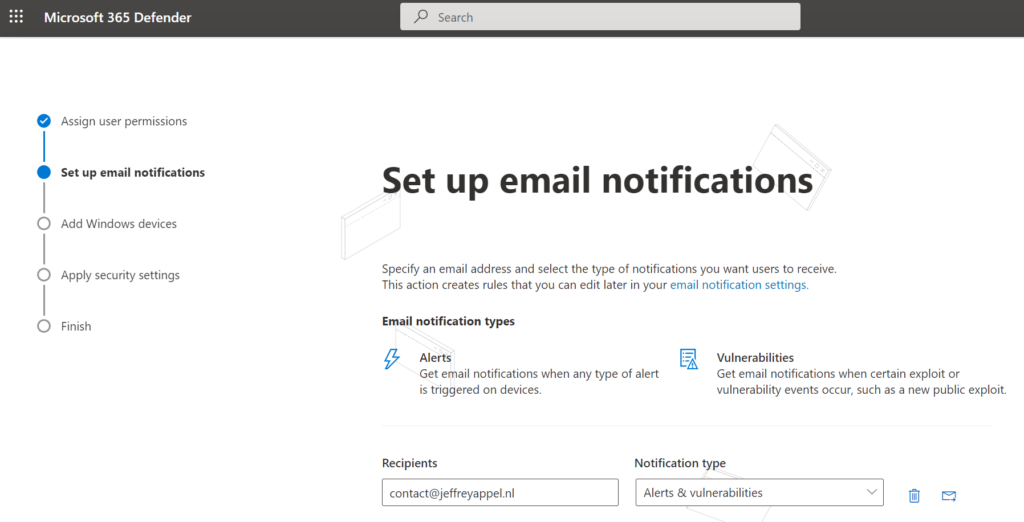
Onboard Windows Devices is important. Defender for Business supports different methods for onboarding devices into Defender for Endpoint. Onboarding is similar in comparison to the P1 and P2 solution from Microsoft.
For onboarding the following options are possible;
- Microsoft Endpoint Manager/ Microsoft Intune
- Local Script
- Group Policy
- VDI Onboarding script
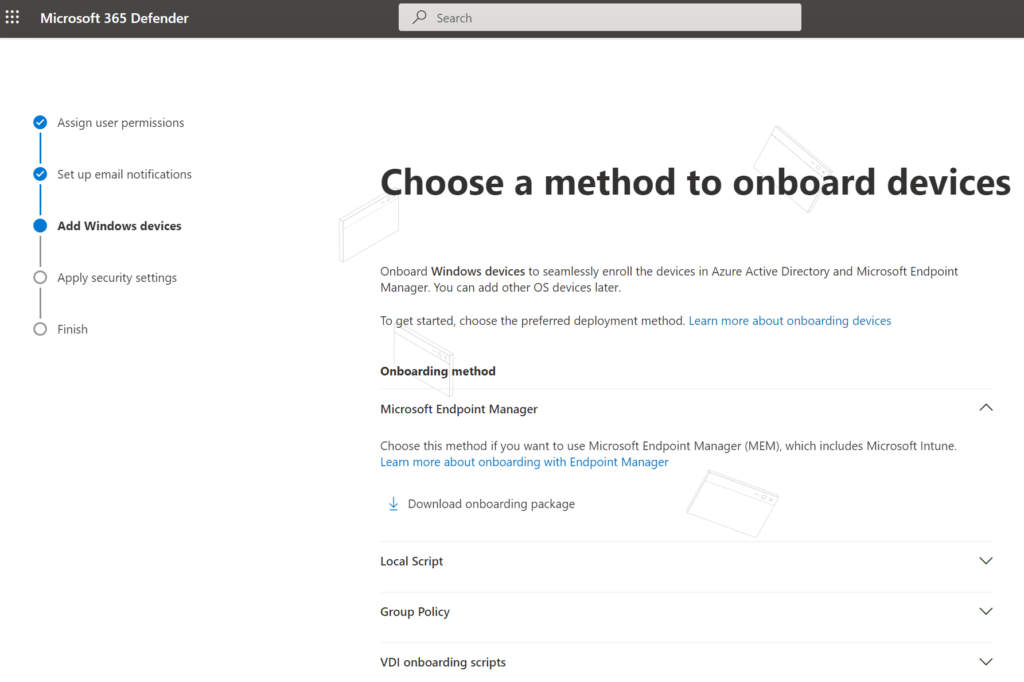
The security settings configuration is different compared to Defender for Endpoint P1 and P2. Microsoft starts with default policies with recommended settings that can be applied to Windows devices. The recommended configuration will include Next-generation protection policies and Firewall policies. It is always possible to change settings later in Device configuration or Intune. More information and policy configuration explanation: Understand next-generation protection configuration settings in Microsoft Defender for Business | Microsoft Docs
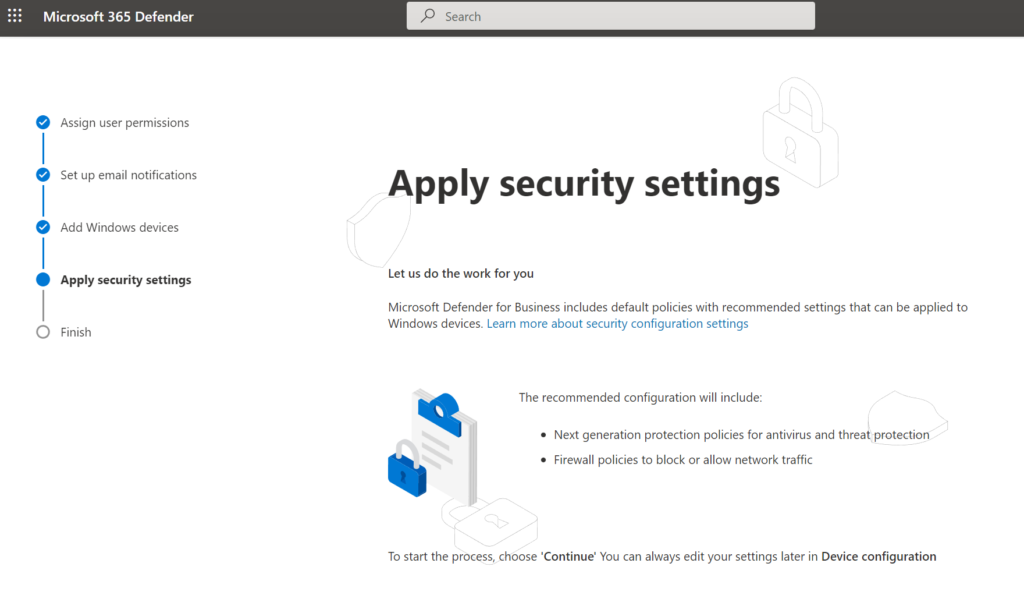
Complete the first-run setup and wait before the Defender instance is enabled. After some minutes (2-3 min) the You’re all set message is visible.
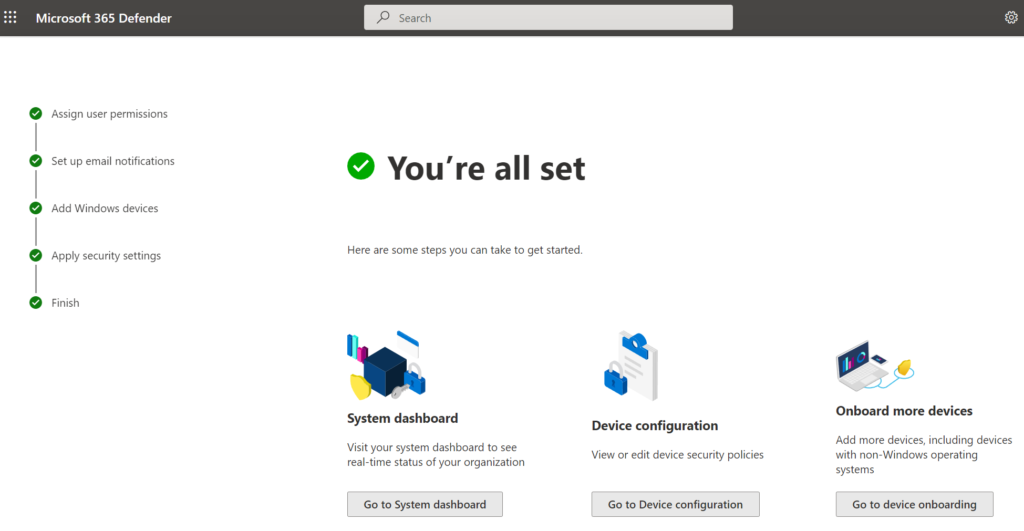
The initial wizard creates automatically the connection that is required between Intune (Endpoint Manager) and Microsoft Defender for Business. All default policies are directly created in Intune, and Advanced Features are automatically enabled.
Currently (21-6-2022) all advanced features are enabled, except Preview features, Tamper Protection and Live Response. It is advised to enable Tamper Protection and Live Response. Preview features can be used to get new security features in the early release ring.
Defender for Business Policies
Based on the first initial setup – Microsoft enables baseline settings for Antivirus, Firewall, and Endpoint detection and response.
Settings can be managed in MEM and MDE. Defender for Business uses the MDE security management feature.
In the Endpoint manager portal (https://endpoint.microsoft.com), we find under Endpoint security the following profiles:
- Antivirus – NGP Windows default policy
- Firewall – Firewall Windows default policy
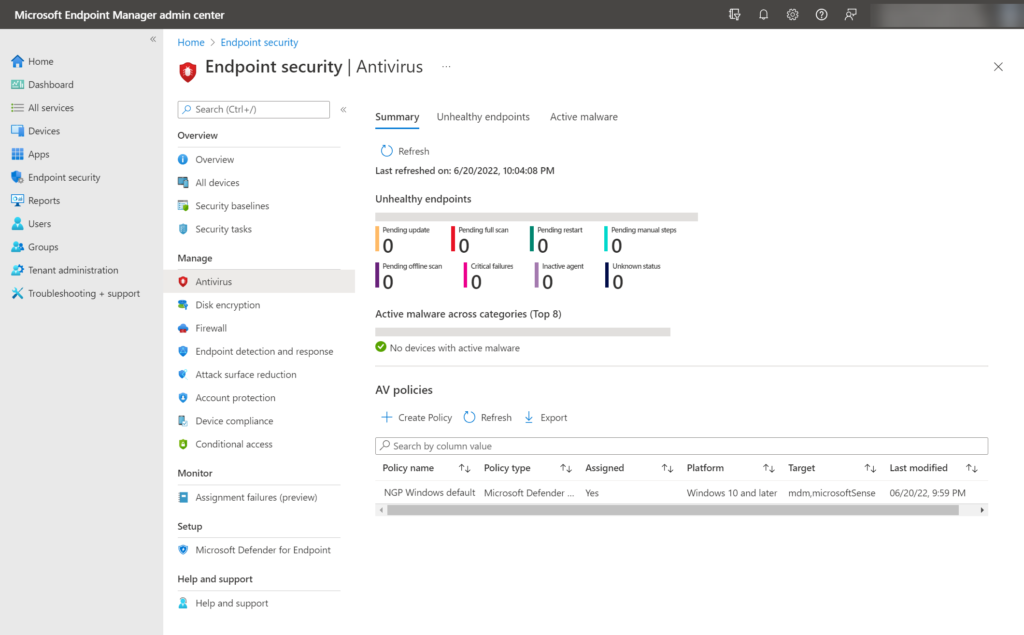
Note: By default the profiles are deployed to All Devices without any additional filter. Currently there is no Attack Surface Reduction and Endpoint detection and response profile configured. ASR and EDR are not yet available in the modern configuration interface, and can be deployed using Microsoft Intune.
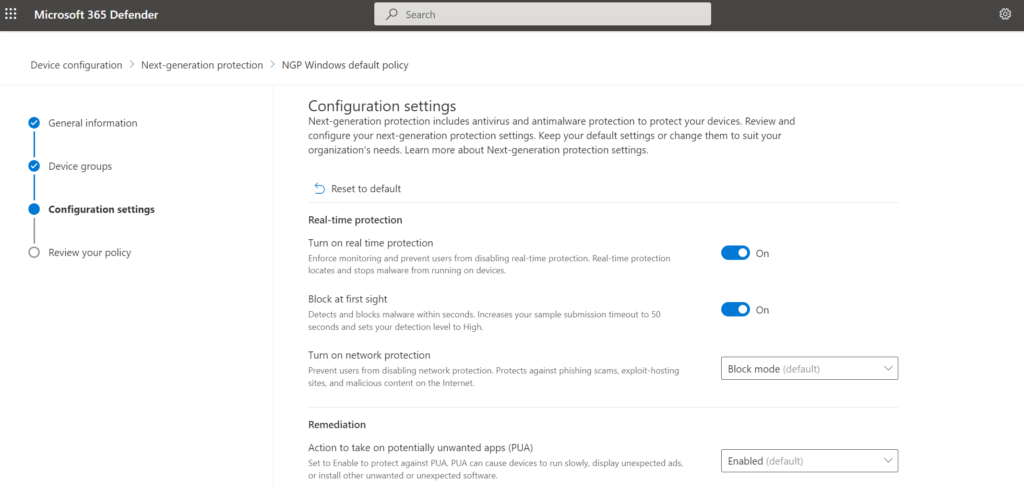
From the Microsoft 365 Defender portal (security.microsoft.com) navigate to Device Configuration under Configuration management. The same policies which are visible in MEM can be directly changed from the Defender portal.
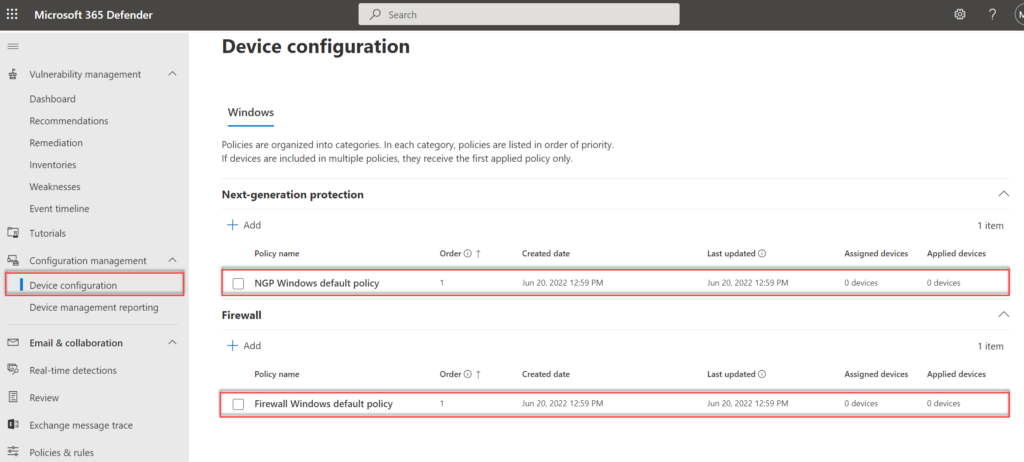
It is possible to edit the default policies, it is not possible to delete the default policies created during the wizard. Default policies will take the lowest order of precedence, so if another policy is created based on a higher rank the settings will be applied following the order.
Key points to remember about policy order
- Policies are assigned an order of priority.
- Devices receive the first applied policy only.
- You can change the order of priority for policies.
- Default policies are given the lowest order of priority.
Configuration management
Configuration management is enabled using Microsoft Endpoint Manager. The default configuration is configured based on Windows Client devices. Note: Server is currently not included in the Defender for Business product.
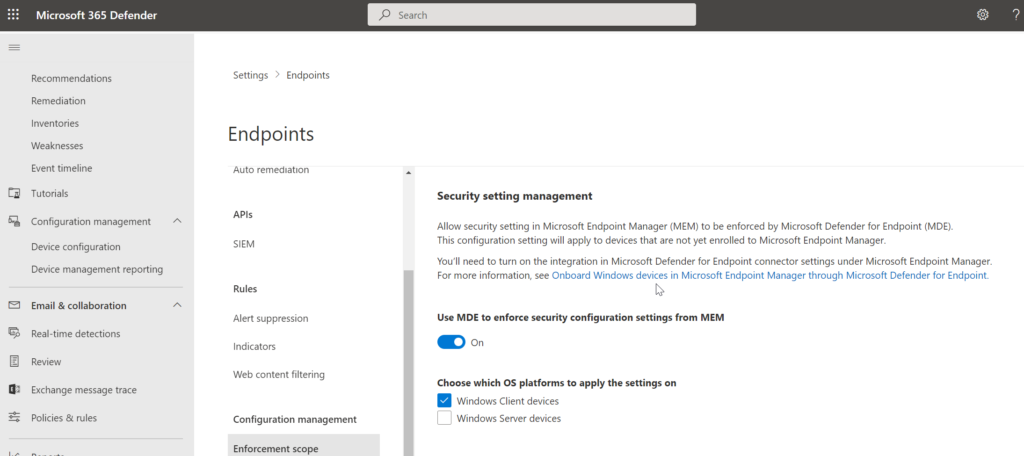
Onboarding machine
As already explained different onboarding methods can be used for Windows. For manually onboarding GPO or Local onboarding script can be used.
For local devices not part of MEM it is possible to manage settings using MDE and MEM, based on the security management feature. After onboarding the devices are onboarded in AzureAD and MEM.
Important: Make sure the correct patches and requirements are installed. Update Defender to the latest Defender product update, which is needed for the management feature. Use aka.ms/mdeclientanalyzer for checking the connectivity and update/system status.
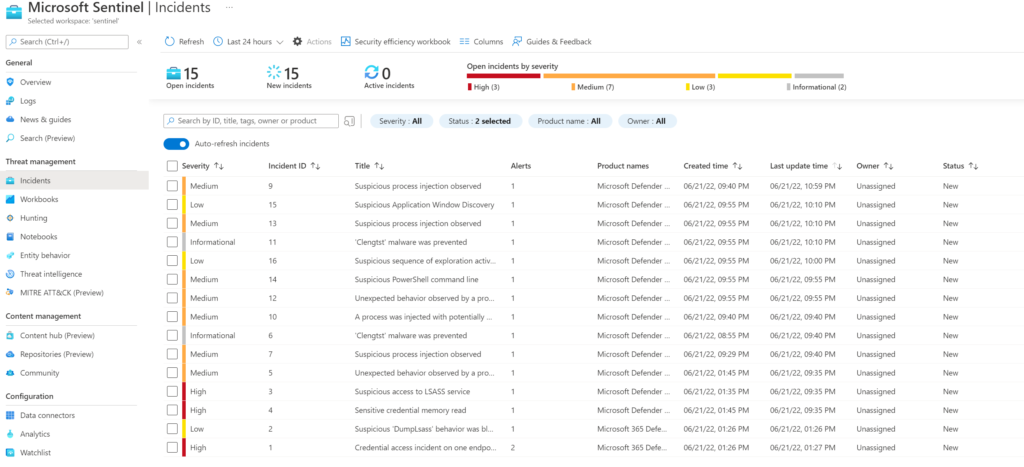
Sentinel integration
For exporting events/ alerts it is possible to use Microsoft Sentinel. Based on my test lab the Microsoft Defender for Endpoint connectors works and creates incidents based on Defender for Endpoint alerts.
Admin experience
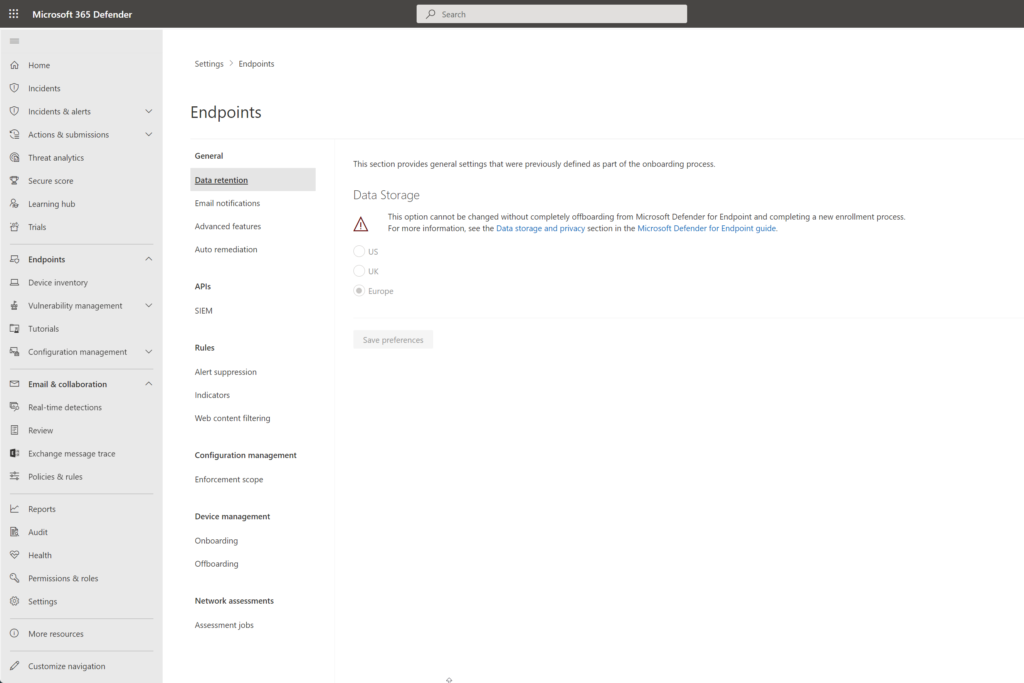
Security.microsoft.com admin experience is different for the Endpoint section. Defender for Business is missing the following configuration items:
- APIs – SIEM
- Permissions – Roles
- Permissions – Device groups
- Rules – Process Memory Indicators
- Rules – Automation uploads
- Rules – Automation folder exclusions
There is no support for creating custom device groups. Defender for Business supports the following roles:
| Permission level | Description |
|---|---|
| Global administrators (also referred to as global admins) As a best practice, limit the number of global admins. | Global admins can perform all kinds of tasks. The person who signed up your company for Microsoft 365 or for Microsoft Defender for Business is a global administrator by default. Global admins are able to access/change settings across all Microsoft 365 portals, such as: – The Microsoft 365 admin center (https://admin.microsoft.com) – Microsoft 365 Defender portal (https://security.microsoft.com) |
| Security administrators (also referred to as security admins) | Security admins can perform the following tasks: – View and manage security policies – View and manage security threats and alerts (these activities include taking response actions on endpoints) – View security information and reports |
| Security reader | Security readers can perform the following tasks: – View security policies – View security threats and alerts |
More information: Microsoft Defender for Business roles
Incident experience
Defender for Business incident experience is different. In comparison with Defender for Endpoint P2 there are some differences in the incident/ investigation experience.
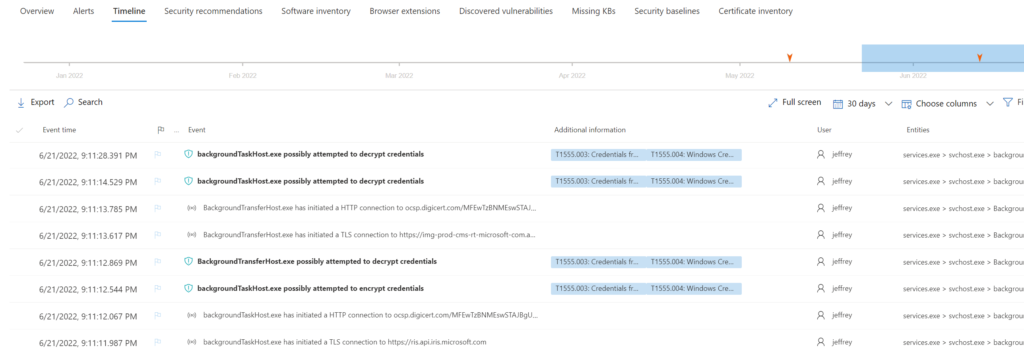
Advanced Hunting
First, there is no Advanced Hunting. Defender for Endpoint is not saving 30 days of event data and 180 days of retention data. Based on this behavior there is no option to hunt for specific device events.
Timeline
Defender for Endpoint P2 supports the timeline events. There is no additional event data in Defender for Business, which gives no centralized Device Timeline event.
Incident actions
As part of the incident investigation, there are some differences in the alert story. Below is the difference between Defender for Endpoint P2 and Defender for Business based on file type actions.
Defender for Business
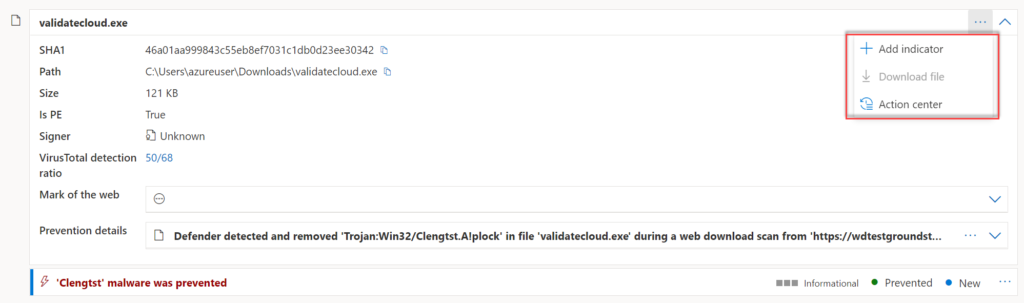
Defender for Endpoint P2

Defender for Business is not supporting the following investigation features:
- Open file page button
- Download files
- Submit to deep analysis
- Stop and Quarantine Files
- Ask Defender Experts
- Go Hunt
Device page experience
The device page contains some differences in comparison with Defender for Endpoint P2. Most of the device actions are available for Defender for Business except the threat expert feature.
What is not available on the device page?
Actions
| Defender for Business | Defender for Endpoint P2 | |
| Isolate device | Y | Y |
| Run antivirus scan | Y | Y |
| Collect investigation package | Y | Y |
| Initiate Live Response Session | Y | Y |
| Initiate Automated Investigation | Y | Y |
| Exclude device | Y | Y |
| Go Hunt | N | Y |
| Restrict app execution | Y | Y |
| Turn on Troubleshooting mode | Y | Y |
| Ask Defender Experts | N | Y |
Information
From an information point of view, the most important feature which is missing is the Timeline tab including all related security events. All other information ( alert, security recommendations, inventory….) is available.
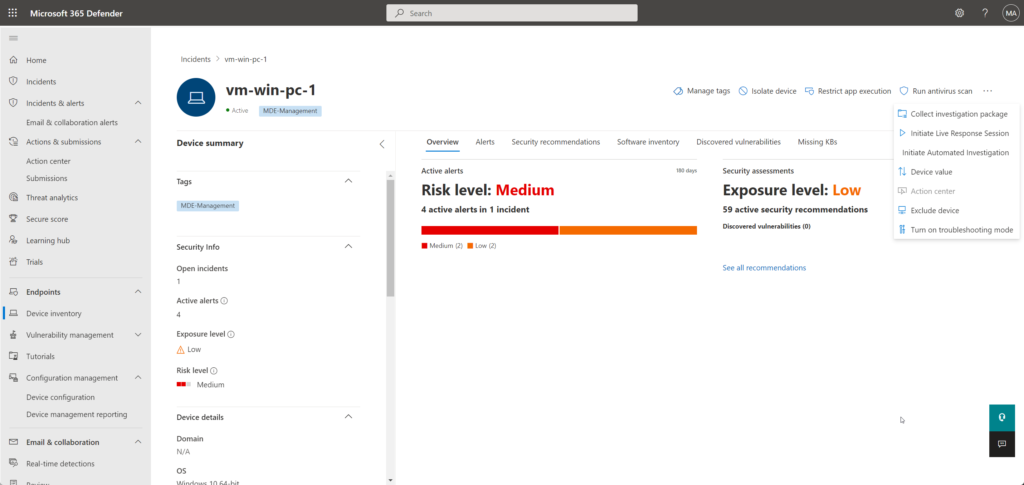
Reporting
Defender for Business supports not all Defender for Endpoint P2 reports.
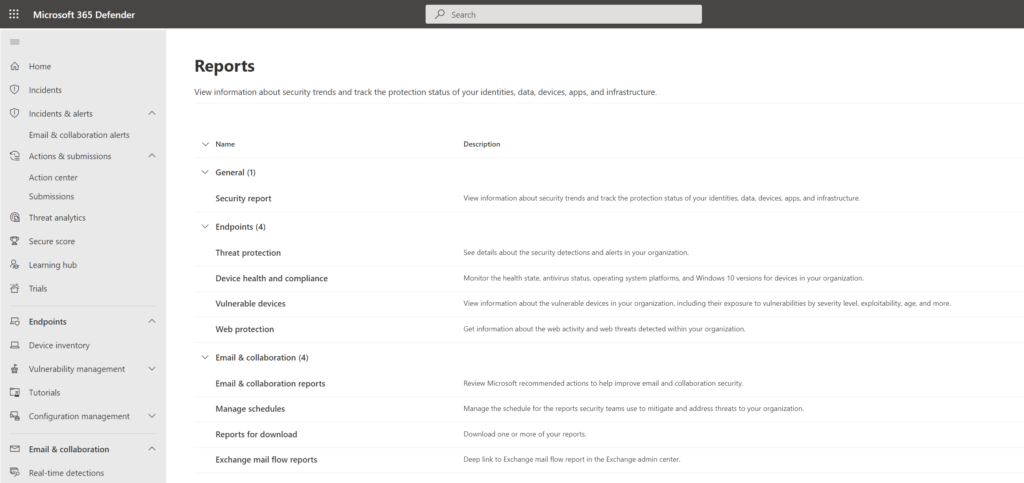
The following is available (URL: https://security.microsoft.com/securityreports)
| Defender for Business | Defender for Endpoint P2 | |
| Threat Protection | Y | Y |
| Device health and compliance | Y | Y |
| Vulnerable devices | Y | Y |
| Web protection | Y | Y |
| Firewall | N | Y |
| Device Control | N | Y |
| Attack Surface Reduction Rules | N | Y |
Defender for Business Limitations
Not all features are available in Defender for Business; there is a cap between Defender for Business and Defender P2. Already quite a lot of features are described in this blog. In high-level terms the following is the difference.
Defender for Business includes most of the Defender for Endpoint P2 features. The following differences are available:
- No advanced Hunting/ threat hunting
- No Threat Experts services
- No 6-months data retention
- No device timeline
- Servers not yet supported (coming in separate offer)
- Threat analytics optimized for small and medium-size business
- No sandbox feature
- Limited in hunting and file/ remediation
Conditional Access
Conditional Access for specific device risk policies is included in Microsoft 365 Business Premium or AzureAD P1.
Compare Defender plans
| Feature/Capability | Defender for Business (standalone) | Defender for Endpoint Plan 1 (for enterprise customers) | Defender for Endpoint Plan 2 (for enterprise customers) |
|---|---|---|---|
| Threat & vulnerability management | Yes | No | Yes |
| Attack surface reduction capabilities | Yes | Yes | Yes |
| Next-generation protection | Yes | Yes | Yes |
| Endpoint detection and response | Yes | No | Yes |
| Automated investigation and response | Yes | No | Yes |
| Threat hunting and six months of data retention | No | No | Yes |
| Device discovery | Yes | No | Yes |
| Custom detections | No | No | Yes |
| Sandbox | No | No | Yes |
| Device timeline events | No | No | Yes |
| Threat analytics | Optimized for small and medium-sized businesses | No | Yes |
| Cross-platform support (Windows, macOS, iOS, and Android OS) | Limited | Limited | Yes |
| Server support | Yes | No | Yes |
| Microsoft Threat Experts | No | No | Yes |
| Partner APIs | Yes | Yes | Yes |
| Microsoft 365 Lighthouse integration (For viewing security incidents across customer tenants) | Yes | Yes | Yes |
| Stream events to Sentinel | Yes | ? | Yes |
| Web Content Filtering | Limited | ? | Yes |
Conclusion
For SMBs based on Microsoft 365 Business Premium the Defender for Business product is included. Compared with Defender for Endpoint P2, some advanced features are missing. It brings more value in comparison with Defender for Endpoint P1. Hopefully Microsoft will add more support for Attack Surface Reduction rules and additional policies (Security Baseline) in the centralized policy management.
Based on the price and cost of the license – it is not bad for small businesses.
Source
Microsoft: What is Defender for Business
Microsoft: Defender for Business – Frequently asked questions and answers
Microsoft: Compare security features




One questions comes to mind, does purchasing one P2 license enable the functionality for all Business endpoints?
Licensing is user-oriented. This means that each employee needs a Microsoft Defender for Endpoint P2 license. User is allowed to use the software on up to 5 devices, on Windows, MacOS, iOS, Android.
So, Defender for buisness is now included in Buisness Premium, almost Defender fro Endpoint P2.
What happends if you upgrade from Defender for buisness to a P2 license? The onboarding process is different according to Microsoft.
Yes, Defender for Business is using the same onboarding package. Only difference is based on the features and AV management.
In P2 it is better to use the complete Intune suite for managing features. Defender Business is created with the device configuration tab.
Note: When upgrading one license the complete licensee is migrating to the MDE P2 license. For getting the correct compliancy, it is needed to buy a P2 license for all machines.
Hi Jeffrey,
Please guide how to Stream events from Microsoft Defender for Business to Microsoft Sentinel.
Thanks