It is time for the first part of the ultimate Microsoft Defender for Endpoint (MDE) series. After the announcement and the great response, it is time for the first part. Part 1 contains information related to Defender for Endpoint’s basics. Upcoming parts are more deep-dived into the components. See part 1 as the high-level overview of the components and parts under the Microsoft Defender for Endpoint (MDE) umbrella.
Introduction blog series
This ultimate blog series will contain as much information as possible based on my Defender experience in the past years. Not a copy of Microsoft Docs, but an addition based on practical experience combined with informational details – including the most frequent questions asked by customers focussing on the complete Windows platform. When it’s a success, other platforms like iOS, Android, Linux, and macOS will follow.
NOTE: Blog series is focussing on features in Microsoft Defender for Endpoint P2 all MDE P1 features are available in P2.
Specific question or content idea part of Defender for Endpoint? Use the contact submission form and share the post ideas.
What is Defender for Endpoint?
Microsoft Defender for Endpoint (MDE) is a comprehensive solution for preventing, detecting, and automating the investigation and response to threats against endpoints. Defender for Endpoint is supported for multiple platforms, including Windows, Linux, macOS, and mobile platforms iOS and Android. Microsoft Defender for Endpoint (MDE) is a massive platform of features and not a single product. It is a platform with tons of security features, services, and controls. Hopefully, this complete blog series gives more explanation in high-level overviews and in-depth technical information based on my own best practices.
Microsoft Defender for Endpoint is a key component of the Microsoft 365 Defender architecture and part of the Microsoft 365 Defender platform. It shares data/ signals and architecture with the following products;
- Microsoft Defender for Endpoint (MDE)
- Microsoft Defender for Office365 (MDO
- Microsoft Defender for Cloud Apps (MDA)
- Microsoft Defender for Identity (MDI)
- Azure AD Identity Protection (AADIP)
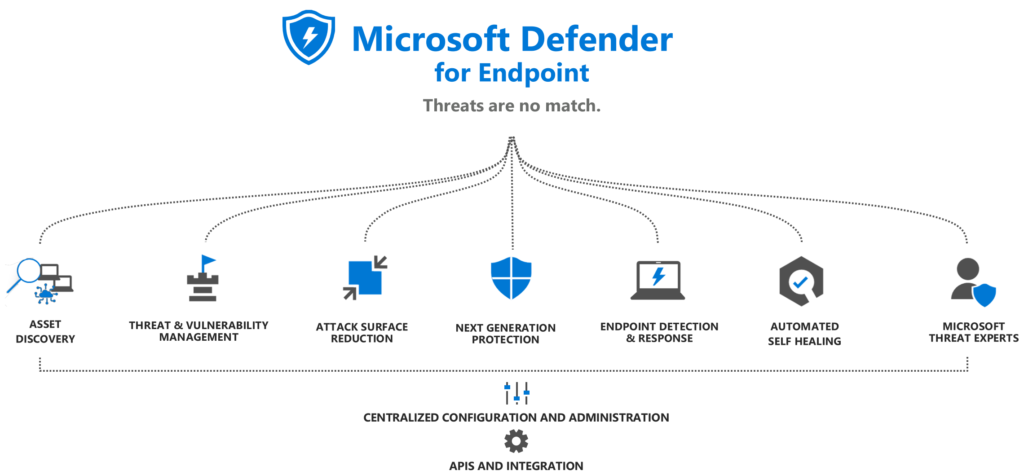
Defender for Endpoint contains a couple of major components including;
- Asset discovery
- Threat & Vulnerability Management (TVM)
- Attack Surface Reduction (ASR)
- Next-Generation Protection (NGP)
- Endpoint Detection & Response (EDR)
- Automated Self-healing/ Automation investigation and remediation (AIR)
- Microsoft Threat Experts
Microsoft has released in the last couple of months quite some new features which make the Defender product one more centralized portal including the following bullets:
- Endpoint = Defender for Endpoint
- Email & Docs = Defender for Office 365
- Apps & Cloud Apps = Defender for Cloud Apps
- Identities = Defender for Identity and Azure AD Identity Protection
Currently, all of the Defender products listed above are available in one single portal. Which reduces heavily the availability of the different portals. 2-3 years ago all the products were available in separate portals; for example Defender for Identity and Defender for Cloud Apps were completely separate. Microsoft is following the direction to share the architecture and combine all security toolings together in one single Microsoft 365 Defender portal. Natively integrating all products within Microsoft 365 Defender streamlines the process of investigation and mitigating threats for the complete attack surface. The Hunting experience is more integrated with all products compared with some years ago, which makes hunting and specific use-case development easier.
The below image shows it in one single view; Microsoft 365 Defender gives the option for centralized incident/alerts, hunting, actions/submissions, and analytics. Where each product is natively integrated.
Microsoft 365 Defender portal:

Microsoft 365 Defender incident view:

What is Defender XDR?
Microsoft Defender XDR is a unified pre- and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications. Defender for Endpoint is part of the Defender XDR suite.
The following products are part of Defender XDR:
- Microsoft Defender for Endpoint
- Microsoft Defender for Office 365
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
- Microsoft Defender Vulnerability Management
- Microsoft Entra ID Protection
- Microsoft Data Loss Prevention
- App Governance
More Defender XDR information: What is Microsoft Defender XDR? | Microsoft Learn
Which Defender plans are available?
Currently, there are multiple Defender plans available. Defender for Individuals is the new consumer product. For the comparison between Defender for Business and Defender for Endpoint P2 view the blog post published earlier.
- Defender for Individuals
- Defender for Business
- Defender for Endpoint P1
- Defender for Endpoint P2
The following add-ons are currently available:
- Defender Vulnerability Management add-on
The following standalone products are available
- Microsoft Defender Vulnerability Management
View the following page for the full Defender for Endpoint P1 and P2 comparison.
Simplified comparison table Defender for Endpoint plans.
| Feature/Capability | Defender for Business (standalone) | Defender for Endpoint Plan 1 (for enterprise customers) | Defender for Endpoint Plan 2 (for enterprise customers) |
|---|---|---|---|
| Threat & vulnerability management | ✅ | ❌ | ✅ |
| Attack surface reduction capabilities | ✅ | ✅ | ✅ |
| Next-generation protection | ✅ | ✅ | ✅ |
| Endpoint detection and response | ✅ | ❌ | ✅ |
| Automated investigation and response | ✅ | ❌ | ✅ |
| Threat hunting and six months of data retention | ❌ | ❌ | ✅ |
| Device discovery | ✅ | ❌ | ✅ |
| Custom detections | ❌ | ❌ | ✅ |
| Sandbox | ❌ | ❌ | ✅ |
| Device timeline events | ❌ | ❌ | ✅ |
| Threat analytics | Optimized for small and medium-sized businesses | ❌ | ✅ |
| Cross-platform support (Windows, macOS, iOS, and Android OS) | Limited | Limited | ✅ |
| Server support | ❌ | ❌ | ✅ |
| Microsoft Threat Experts | ❌ | ❌ | ✅ |
| Partner APIs | ✅ | ✅ | ✅ |
| Microsoft 365 Lighthouse integration (For viewing security incidents across customer tenants) | ✅ | ✅ | ✅ |
| Stream events to Sentinel | ✅ | ✅ | ✅ |
| Web Content Filtering | Limited | ✅ | ✅ |
More information: Compare Microsoft endpoint security plans
Defender for Cloud vs Defender for Endpoint vs Defender for Server
Common question; What is the difference between Defender for Endpoint, Defender for Cloud, Defender for Server, and Azure Arc? And why do we need all components when deploying Defender for Endpoint on servers? Let’s explain it more in-depth.
Defender for Cloud is a Cloud-native application protection platform based on Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP).
Defender for Cloud offers multiple Defender plans for more in-depth security. Available plans:
– Defender CSPM
– Defender for Servers
– Defender for App Service
– Defender for Databases
– Defender for Storage
– Defender for Containers
– Defender for Key Vault
– Defender for Resource Manager
– Defender for DNS
The Defender for Servers plan is part of Defender for Cloud and is available in two pricing models; P1/ P2. P1 focussed on a limited set of defenses with a strong focus on Defender for Endpoint technology. P2 contains the full set of Defender for Cloud-enhanced security features including for example; Network layer threat detection, FIM, Qualys vulnerability assessment, and 500MB free data ingestion.
P1=$5 Server/Month (calculated for running time)
P2=$15 Server/Month (calculated for running time)
When you have Microsoft Defender for Severs Plan 1, it includes Microsoft Defender for Endpoint Plan 2. Both P1/ P2 contains all features of Defender for Endpoint P2.
By integrating Defender for Endpoint with Defender for Cloud, it gives the following benefits:
- Automated onboarding
- Azure Arc (On-Prem) can be easily deployed using Defender for Cloud
- The Defender for Cloud portal pages display Defender for Endpoint alerts
After enabling the Defender for Endpoint integration in Defender for Cloud machines will be provisioned. The configuration/ installation is pushed using Azure Policies and contains the onboarding script and additional configuration. The result is the MDE.Windows VM extension for Windows Server 2012R2 and higher.
Azure Arc functions as a bridge that extends the Azure platform to on-premises environments or other clouds (AWS/ GCP). For connecting servers with Azure Arc, it is needed to use Azure Arc-enabled servers and the Azure Connected Machine agent on supported systems.
In simple terms;
1: In Defender for Cloud
2: Is the plan Defender for Servers P1 or P2 enabled
3: Which onboards Defender for Endpoint P2 via Azure Policy
Components
Let’s explain quickly the main components part of Defender for Endpoint in this overview blog part. All features will be explained more in-depth in one of the next parts.
Threat & Vulnerability management
Threat & Vulnerability Management (TVM) is based on my option one of the most important features in Defender for Endpoint and shows continuous real-time TVM discovery. Good to know TVM part of Defender for Endpoint is included in the Defender SENSE/ EDR services, which gives no additional software installation or configuration. Prioritization is based on the actual threat landscape.

Defender Vulnerability Management rapidly and continuously prioritizes vulnerabilities and provides security recommendations to mitigate the risk.
Currently, multiple vulnerability management offerings are available for Defender for Endpoint.
- Defender Vulnerability Management core capabilities
- Defender Vulnerability Management add-on
- Defender Vulnerability Management Standalone
Microsoft Defender Vulnerability Management offerings
As already explained; Microsoft Defender supports multiple offerings for Microsoft Defender Vulnerability Management. Currently, there are the following offerings available:
Defender for Endpoint P2:
- Core TVM capabilities included
Add-on for Defender for Endpoint P2:
- Defender Vulnerability Management add-on
Defender Vulnerability Management Standalone
- Full vulnerability management capabilities
Simplified comparison table Defender for Endpoint Vulnerability Management offerings.
| Feature/Capability | Core Vulnerability management (MDE P2) | Defender Vulnerability Management add-on for MDE P2 | Defender Vulnerability Management Standalone |
|---|---|---|---|
| Device Discovery | ✅ | Included in core | ✅ |
| Device inventory | ✅ | Included in core | ✅ |
| Vulnerability assessment | ✅ | Included in core | ✅ |
| Risk-based prioritization | ✅ | Included in core | ✅ |
| Remediation tracking | ✅ | Included in core | ✅ |
| Continuous monitoring | ✅ | Included in core | ✅ |
| Software assessment | ✅ | Included in core | ✅ |
| Security baselines assessment | ❌ | ✅ | ✅ |
| Block vulnerable applications | ❌ | ✅ | ✅ |
| Browser extensions | ❌ | ✅ | ✅ |
| Digital certificate assessment | ❌ | ✅ | ✅ |
| Network share analysis | ❌ | ✅ | ✅ |
| Hardware and firmware assessment | ❌ | ✅ | ✅ |
| Authentication scan for Windows | ❌ | ✅ | ✅ |
Important: If you use Defender for Servers P2, it includes the Defender Vulnerability Management add-on capabilities part of the Defender for Servers P2 capabilities. No extra license is required.
Attack Surface Reduction
Attack Surface Reduction (ASR) is a large set of features in the Defender product focussing on reducing the attack surface of the devices.
Attack Surface Reduction rules are a good example where for example obfuscated suspicious script can be blocked or persistence through WMI event subscription. ASR is really powerful in reducing the available attack paths for attackers.
The following features are part of Attack Surface Reduction:
- HW-based isolation
- Exploit protection
- Network protection
- Controlled folder access
- Device control
- Web protection
- Ransomware protection
- Attack Surface Reduction rules
- Application control
Next-Generation Protection
Next-Generation Protection (NGP) is the Defender Antivirus part of Defender for Endpoint. It is not only focussing on traditional signature-based protection. Next-Generation protection is focussing heavily on cloud-based protection/ machine learning in-depth threat research and big-data analysis. Cloud-delivered protection, behavior monitoring (Execution behavior), and collaboration with EDR are heavily available.

Image source: Microsoft
Next-Generation Protection starts years ago in the Microsoft landscape. It started all with Security Essentials and System Center Endpoint Protection (SCEP). Recently Microsoft released the new unified agent for Server 2012R2 and Server 2016 systems. Now all recent platforms include the Next-generation protection feature. The following features are part of the next-generation protection services:
- Behavior-based
- Heuristic
- Real-time antivirus protection
- Cloud-delivered protection
Cloud Protections works directly with new (cloud)-based technologies that work together with data in the Microsoft Intelligent Security Graph and artificial intelligence-driven machine learning models. Part of Cloud protection is Cloud metadata, sample data, sandbox data, and big data based on signals across Microsoft.
Endpoint Detection & Response
Next-Generation protection/ Defender Antivirus is mostly based on Pre-Execution blocking. When Defender Antivirus allowed the file to run and it turned out to be malicious, the EDR sensor alerted any suspicious activities based on the SENSE services. EDR gives Post-Execution insights and shows visibility into the full scope of the attack flow. Defender EDR evaluates endpoint-system-level behaviors and applies data analytics to detect suspicious behaviors. Defender for Endpoint continuously collects behavior cyber telemetry. Data can be used for up to 6 months for advanced threat hunting and data correlation based on identity and other product data. The language part of the hunting schema is KQL/Kusto Query Language
Endpoint Detection & Response contains a large number of features in Defender for Endpoint. For example; Investigation experience, response actions, detections, indicators, Advance Hunting, and many more features.
Automated Investigation and response
Automated investigation and response (AIR) is part of Defender for Endpoint. Automated investigation and response uses inspection algorithms to examine alerts, determine whether the threat requires action, and perform necessary remediation actions on affected machines from the alert context.

The automated investigations run locally on the device and perform multiple actions based on the file, network, process, and other information. Based on the findings automated investigations can automatically remediate malicious items and threats and automatically close the alert/incident.
Multiple levels of automation are available which makes it flexible and ask for approvals when needed. Ideally, automated Investigations run completely automatically based on the full automated device level without any user input. The full automated device level runs 24/7 which increases the security posture massively.
Microsoft Threat experts
Microsoft provides multiple managed services based on Microsoft Defender. Microsoft Threat Experts enabled the following features:
- Microsoft Threat Experts – Targeted attack notification provides proactive hunting for the most important threats to your network, including human adversary intrusions, hands-on-keyboard attacks, or advanced attacks like cyber espionage.
- Microsoft Threat Experts – Experts on Demand enables the option to connect with Microsoft security experts directly from the Microsoft 365 Defender console. Experts provide more in-depth investigation for alerts which gives additional clarification on alerts.
More detailed information later in this blog series. Discuss the eligibility requirements with your Microsoft Technical Service provider and account team. Microsoft Threat Experts – Experts on Demand is an additional service.
Additional information; Microsoft announced recently new managed services:
- Microsoft Defender Experts for Hunting
- Microsoft Defender Experts for XDR
- Microsoft Security Services for Enterprises
Asset discovery
Unmanaged devices are most of the time a weak point in the corporate network/ environment and are optional targets. With the current situation more and more BYOD devices are connected to the enterprise network environment. With the new Defender for Endpoint Discovery functionality, it is possible to scan and protect the corporate network for unmanaged devices. In each environment, there are multiple devices like IoT devices, printers, network devices, unmanaged devices, scanners, and many more. Asset discovery is part of Threat and Vulnerability management.

Device discovery uses onboarded endpoints to actively probe, or scan your network to discover unmanaged devices. Asset discovery is supported for the following “unmanaged” devices:
- Enterprise endpoints (Windows, Linux,macOS, iOS, and Android) that are not yet onboarded to Microsoft Defender for Endpoint
- Network devices (routers and switches)
- IoT devices
An interesting part of Asset discovery is to find unmanaged client devices which are not onboarded in Defender for Endpoint. Defender for Endpoint device inventory shows all devices which are not onboarded or not supported.
Recently Microsoft added more information to the asset discovery blade. With the integration of the RiskIQ dataset, Microsoft add the tag “internet facing” for devices exposed to the external network. All information is part of the device inventory blade.

Architecture
Microsoft Defender for Endpoint is a complete platform part of the Microsoft Defender platform and supports multiple integrations.
Important to know each customer’s Defender for Endpoint instance is completely separate and only used for the customer. Currently, data storage is possible with a maximum of six months (Defender for Endpoint P2) and supports storage in the following locations:
- US
- UK
- Europe
More in-depth explanations about the integrations will be explained in the next section. Below are some of the available integrations with Defender for Endpoint.
- Microsoft Sentinel
- Defender for Cloud
- Microsoft Information Protection (Endpoint DLP)
- PowerBI/ SIEM connector
- Microsoft Endpoint Manager
- Microsoft Defender integrations
Automatic attack disruption
Automatic attack disruption is important and part of Microsoft 365 Defender and part of the full XDR picture. Automatic attack disruption is designed to contain attacks in progress, limit the impact, and remediate parts of the attack automated. Attack Disruption is built-in and starts automatically when alerts are flagged as disruption alerts. Microsoft uses all signals from multiple sources to determine the compromised assets.
Last year Microsoft announced a new feature called; Automatic attack disruption which uses correlated insights from the Microsoft 365 ecosystem and powerful AI models to stop sophisticated attack techniques while the attack is in progress. Automatic attack disruption supports the adversary-in-the-middle (AiTM) attacks.
Since May 17, 2023 Microsoft supports automatic attack disruption for adversary-in-the-middle attacks (AiTM) attacks on top of the included BEC and human-operated ransomware attacks.
Automatic attack disruption is part of the Microsoft XDR capabilities. When the incident is part of an Attack Disruption the tag title is visible with the value Attack Disruption. On the incident itself, there is a yellow banner visible including the automated actions part of the attack disruption flow.
The below image is from Microsoft (Source; Microsoft). More in-depth information will be explained later in this blog.

Recently explained Attack Disruption more in-depth during AiTM attacks. Blog: AiTM/ MFA phishing attacks in combination with “new” Microsoft protections (2023 edition)
Enablement roadmap
As written above; Defender for Endpoint contains a large set of features. The following key points are increasing the security posture massively. Of course; all points will be explained in the next parts in more detail. Below gives an idea of what is coming in the next sections and a reference point for a complete MDE configuration.
- Use centralized management (Intune) or Unified MDE management), alternatively when MEM is not possible GPO, Intune, or PowerShell. Centralized management makes exclusions management easier.
- Configure Cloud Protection/ Next-Generation Protection
- Optimize Next-Generation protection/ Defender AV (local admin merge, Cloud Block Level, Extended Timeout, Signature interval)
- Use Automated Investigation and remediation for automated response and automatically clean systems and remove malicious files
- Enable Always remediate PUA for blocking Potentially unwanted applications which are detected as PUA
- Enable EDR in block mode when third-party AV is configured
- Enable Tamper Protection tenant-wide for enabling tamper protection globally and protect tampering with Defender.
- Enable Targeted Attack Notification for more in-depth notifications
- Onboard additional Attack Surface Reduction features in audit and ideally block
- Configure Compliance policies when using MEM for blocking non-compliant devices ( risk-level)
- Integrate with Defender for Cloud Apps for deeper visibility in cloud apps and shadow IT based on MDE-detected traffic
- Enable custom network indicators for blocking IOCs from various sources
- Report Defender status using Advanced Hunting, TVM, and/or PowerBI
- Define Device Groups for information insights ( location, country/ type e.d) and selective scoping of exclusions
- Hunt and research the data using Advanced Hunting and Threat and Vulnerability Management
- Follow-up/ follow-up and follow-up based on TVM, Alerts, and data.
- Create additional detections that are not part of the product and improve the detections based on the collected data.
Information sources
Microsoft Defender for Endpoint (MDE) is a large topic with various products/ services and features. There is a large list of community work and official Microsoft information sources.
Microsoft
- Microsoft Security Twitter
- Microsoft Defender for Endpoint Tech community (Activity)
- Microsoft Defender for Endpoint Tech community (Blogs)
- Microsoft Defender for Endpoint Ninja training
- Microsoft Defender for Endpoint Virtual Ninja Training
- Microsoft Learn path – Microsoft Defender for Endpoint
Probably forgot to add a couple of resources, ping me when there are more good community resources. Below are some good sources for MDE and MDE-inspired KQL.
Community websites
- Ru Campbell / Campbell.scot
- Fabian Bader / Cloudbrothers.info
- Derk van der Woude / Medium
- Sami Lamppu / Samilamppu.com
Twitter sources
- Olaf Hartong
- Jan Geisbauer
- Thijs Lecomte
- Stefan Schörling
- Matt Zorich
- Kevin Beaumont
- Thomas Naunheim
- Pawel Partyka
- Gianni/ Kustoking
- Alex Verboon
Conclusion
Part 1 of the Microsoft Defender for Endpoint series is completed – focussed on the general explanation and function explanation in Microsoft Defender for Endpoint. Stay tuned for the following parts; where more in-depth knowledge and experience will be shared around Defender for Endpoint focussing on configuration, design decisions, validating, evaluating, troubleshooting, and more.
Searching for specific Defender for Endpoint information? Use the contact submission form and share the post ideas or contact using Linkedin or Twitter. I will take all suggestions into the Defender for Endpoint series and help the community as far as possible.
View previous part – The ultimate blog series for Windows (Intro) – P0





What are some of the most common support questions around onboarding and customizing Anti-Phishing, Safe Links, or Safe Attachments policies,?