Microsoft announced recently the new troubleshooting mode functionality for Defender for Endpoint. With the new troubleshooting mode, it is possible to disable the tamper protection and change Defender Antivirus settings locally for testing different scenarios, even when they’re controlled by the organization’s policy. The troubleshooting mode runs for 3 hours.
Note: Blog updated 12-09-2022: Added support for Server 2012R2/ 2016
Important: as always security is important; use the new feature carefully, and implement minimal exclusions. Don’t disable features completely when the “application” works fine after disabling critical features like Network protection, ASR, real-time protection, or other important settings. Analyze performance issues when the AV engine is completely running. Before enabling the troubleshooting mode make sure there is no active threat giving the performance load.
What is MDE Troubleshooting mode?
Microsoft Defender for Endpoint troubleshooting mode allows you to troubleshoot various Microsoft Defender antivirus features which are normally protected by the organization policy or the tamper protection functionality.
The troubleshooting mode is disabled by default and needs to be manually enabled from the Microsoft Defender for Endpoint interface.
Tamper Protection can be enabled from the Defender for Endpoint portal or from Intune/ Configuration Manager Tenant Attach. The biggest disadvantage was always that there was no possibility of deploying Tamper Protection for devices managed by ConfigMgr, PowerShell, or GPO. System-wide MDE deployment gives before no flexibility to troubleshoot issues with app compatibility or performance. With troubleshooting mode it is possible to flexible troubleshoot single machines and configure Tamper Protection globally from the portal for all supported platforms including ConfigMgr and GPO-managed devices.
Prerequisites
Microsoft Defender for Endpoint Troubleshooting mode works for a selective set of devices and is supported for the following OS versions.
- A device running Windows 10 (version 19044.1618 or later), Windows 11, Windows Server 2019, or Windows Server 2022 is supported.
- Defender for Endpoint must be running Microsoft Defender Antivirus, version 4.18.2203 or later ( Use Get-MpComputerStatus for validating the version)
- Access to Microsoft 365 Defender
- Manage Security settings permissions in Defender for Endpoint
Update 12-09-2022: Server 2012R2/ Server 2016 installed with the MDE unified agent and updated with the latest EDR sensor (KB5005292/ Defender product update (KB4052623) is now supported for the new troubleshooting mode.
Server 2012R2 requires the following versions:
- Sense version 10.8049.22439.1084 or later (KB5005292)
- Defender Antivirus – Platform: 4.18.2207.7 or later (KB4052623)
- Defender Antivirus – Engine: 1.1.19500.2 or later (KB2267602)
Local admins will be able to configure all other security settings in the Microsoft Defender Antivirus suite (for example, cloud protection, and tamper protection).
How works the flow?
Microsoft Defender for Endpoint troubleshooting mode allows troubleshooting of various Defender antivirus features by enabling/ disabling them locally from the device. Troubleshooting mode can be useful for the following use-cases:
- Microsoft Defender Antivirus functional troubleshooting /application compatibility
- Microsoft Defender Antivirus performance troubleshooting
For better visibility – let’s explain the complete flow from the initial action, including all reporting and file creations.

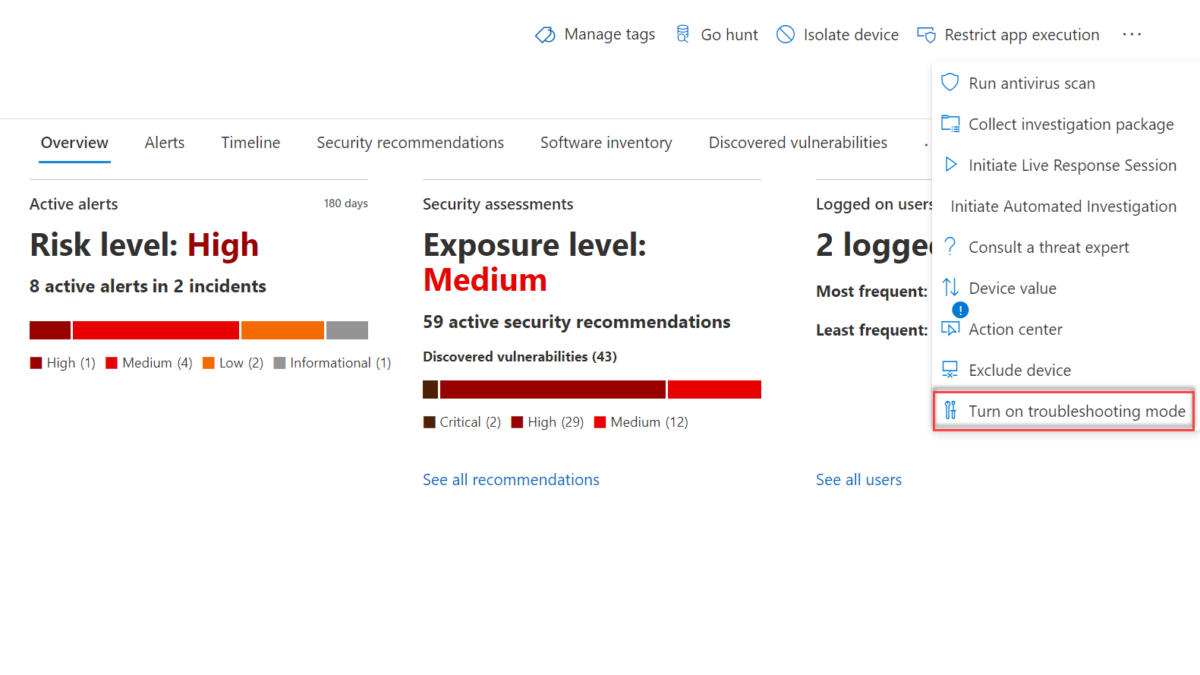
Turn on Troubleshooting mode
Troubleshooting mode is initiated by a single-use command that is created for a single device which can be enabled from the Microsoft 365 Defender portal. The troubleshooting window is 3 hours and can’t be changed in a shorter or longer window. Currently there is no option to cancel the troubleshooting mode before the 3 hours.
For enabling devices in troubleshooting mode navigate to the Device page/ Machine page for the device and select the Turn on Troubleshooting mode.

Troubleshooting mode required Manage security settings in Security Center permissions for Microsoft Defender for Endpoint. Only this specific permission role makes the enablement of troubleshooting mode possible.
Confirm the enablement of troubleshooting mode for the device.

After enablement the device page menu item will remain greyed out for the complete maintenance time and shows the status: Troubleshooting mode is pending or Troubleshooting mode is on.

Timeline event
The start of the troubleshooting mode is reported in the timeline/ device events. The event Troubleshooting mode status is enabled and contains the start trigger including the following information:
- Event: Troubleshooting mode status is enabled
- Event Time: Timestamp of the event
- Action Type: TroubleshootingModeStatus
- Current state: Enabled
- Previous state: Disabled
- Start time: Time of the troubleshooting mode start
- Expiration time: Expiration time of the maintenance mode
- Minutes left until expiration: Minutes remaining ( calculating based on event time)

Maintenance mode
Before the enablement, a snapshot will be captured from all MpPreference settings. When maintenance mode is enabled; local administrators are allowed to disable the Tamper Protection and change security settings part of Defender for Endpoint.
Disable tamper protection
After enabling the maintenance mode Tamper Protection can be disabled. For recent versions of Windows Server or Windows 10/11 the Tamper Protection disablement is possible via the Defender GUI.

Disablement for older versions is possible using PowerShell. There is no GUI available for 2012R2. For disablement of Tamper Protection use the following PowerShell command – command works only when troubleshooting mode is enabled.
Set-MPPreference -DisableTamperProtection $true Important: as always security is important; use the new feature carefully, and implement minimal exclusions. Don’t disable features completely when the “application” works fine after disabling critical features like Network protection, ASR, real-time protection, or other important settings. Analyze performance issues when the AV engine is completely running. Before enabling the troubleshooting mode make sure there is no active threat giving the performance load.
Now it is possible to disable using PowerShell security settings using the Set-MpPreference module. For example:
- Set-MpPreference -DisableRealTimeMonitoring $True for disabling RTP
- Set-MpPreference -EnableNetworkProtection Disabled for disabling network protection
For checking of exclusion folders can fix the issues, it is possible to use the following commands:
- Set-MpPreference -ExclusionPath
- Set-MpPreference –ExclusionExtension
- Set-MpPreference –ExclusionProcess
Disablement actions are visible in the timeline of the specific device. Defender is still reporting events that are related to disablement of main protection features/ or exclusions folder which are set.
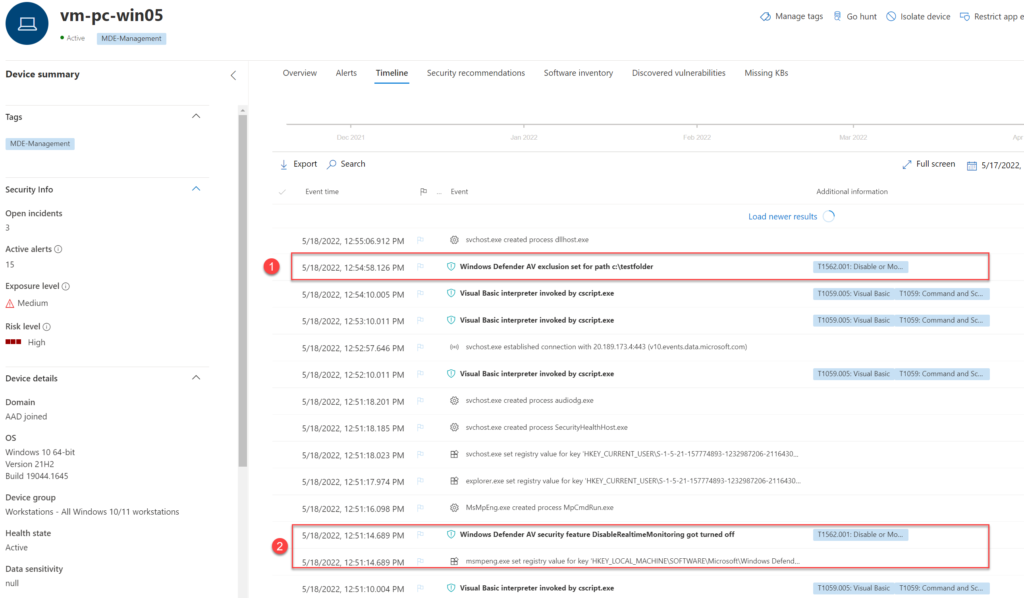
During the maintenance mode – EDR and AV events are reporting to Defender for Endpoint. Malicious attempts are correctly reported. While troubleshooting mode is active, endpoint detection and response (EDR) will not block any files, folders, or processes that Microsoft Defender Antivirus has excluded from scans.

Microsoft explains a couple of Troubleshooting mode scenarios Troubleshooting mode scenarios in Microsoft Defender for Endpoint
Disabling Troubleshooting mode
There is no option to disable the troubleshooting mode. After the enablement the maintenance mode is always active for 3 hours.
Before the end of the troubleshooting mode another second snapshot is captured from all MpPreference settings.
When the troubleshooting mode is disabled, all policy-managed configurations will become read-only again and will revert to the original state – including Tamper Protection enabled.

Logs
Microsoft Defender for Endpoint collects logs and investigation data throughout the troubleshooting process. Before the troubleshooting mode begins a snapshot of MpPreference will be taken – another snapshot will be taken just before the troubleshooting expires. All data and logs including the operational logs can be collected with the Collect investigation package button in Microsoft 365 Defender. Only after the investigation package collection, the files will be deleted from the system.
- Local share: C:\ProgramData\Microsoft\Windows Defender\Snapshots
- Previous_TSPolicyConfigs.snp
- Previous_TSPreferenceConfigs.snp
Part of the investigation package:
- WdSupportLogs: WdSupportLogs\MPSupportFiles\ProgramData\Microsoft\Windows Defender\Snapshots
- Previous_TSPreferenceConfigs.snp
- Previous_TSPolicyConfigs.snp

Advanced Hunting
Microsoft pre-created some advanced hunting queries to give more visibility in the troubleshooting mode event. Part of the DeviceEvents table is the ActionType AntivirusTroubleshootModeEvent
Source: Troubleshooting mode – Advanced hunting queries
Get troubleshooting mode events for a single device
let deviceName = "<device name>"; // update with device name
let deviceId = "<device id>"; // update with device id
search in (DeviceEvents)
(DeviceName == deviceName
) and ActionType == "AntivirusTroubleshootModeEvent"
| extend _tsmodeproperties = parse_json(AdditionalFields)
| project $table, Timestamp,DeviceId, DeviceName, _tsmodeproperties,
_tsmodeproperties.TroubleshootingState, _tsmodeproperties.TroubleshootingPreviousState, _tsmodeproperties.TroubleshootingStartTime,
_tsmodeproperties.TroubleshootingStateExpiry, _tsmodeproperties.TroubleshootingStateRemainingMinutes,
_tsmodeproperties.TroubleshootingStateChangeReason, _tsmodeproperties.TroubleshootingStateChangeSource Result

Devices currently running in troubleshooting mode
search in (DeviceEvents)
ActionType == "AntivirusTroubleshootModeEvent"
| extend _tsmodeproperties = parse_json(AdditionalFields)
| where Timestamp > ago(3h)
| where _tsmodeproperties.TroubleshootingStateChangeReason == "Troubleshooting mode started"
|summarize (Timestamp, ReportId)=arg_max(Timestamp, ReportId), count() by DeviceIdSources
Microsoft: Get started with troubleshooting mode in Microsoft Defender for Endpoint
Microsoft: Troubleshooting mode scenarios