In the past months, there has been a growing increase in QR Code phishing, since attackers are using new creative ways to bypass existing protections. QR Code phishing is commonly used to bypass existing protections and steal/ collect tokens/ user credentials via AiTM methods.
The QR code phishing threat is not new, it has recently grown significantly since COVID. In the past months, Microsoft released and changed protections to protect better against QR codes with default protection and additional controls.
Why is it important to protect against QR code phishing?
QR code phishing campaigns are rapidly changing and become one of the fastest-growing types of email-based attacks. Attackers are using QR code images linked with a malicious content URL.
QR codes are old; since the COVID situation, QR codes are more legitimate in use. Since COVID it is normal to scan QR codes in restaurants/ check-in desks and many more related to marketing activities. In the past 3-4 years the use of QR codes has been rapidly increasing all over the place.
Since last year the combination of AiTM and QR-code-based phish are more used. In this situation, attackers use QR codes which include malicious links going to AiTM or phishing sites to bypass existing protections based on Endpoints.
QR codes are used in phishing attacks for mainly two reasons:
- They move the attack away from more protected corporate environments and use personally owned mobile devices, which may be less secure.
- They leverage the most common credential theft vector which is the URL behind the QR code; this bypasses protection such as URL scanning in existing toolings, since malicious URLs are commonly well-scanned in e-mails.
More interesting information is available in this blog from Microsoft, it is recommended to read all the content of the blog; it includes interesting insights into how Microsoft is protecting against QR phishing and the recent increase in phishing. Protect your organizations against QR code phishing with Defender for Office 365 | Microsoft Tech Community
Methods to deliver QR codes?
There are multiple methods to deliver QR codes via mail/ teams/ chat/ messaging apps. When talking related to Microsoft products the following options are available and common to use:
- QR codes embedded as inline images within the email body
- QR codes within an image in the email body
- QR codes as an image in the attachment
QR codes are commonly scanned with phones or tablets (personal/ work devices).
How does the QR phishing flow work?
1: Phish with QR code included and sent to the victim via mail/ teams including QR code
2: Victim scans code with a mobile device
3: Victim redirected to phishing page (Most of them redirected via Bing or Cloudflare to bypass protection) for credential harvesting (AiTM/ Device token flow)
4: Credentials/tokens stolen via credential harvesting
Example of a mail including QR codes redirecting to phishing sites/ malicious URLs.

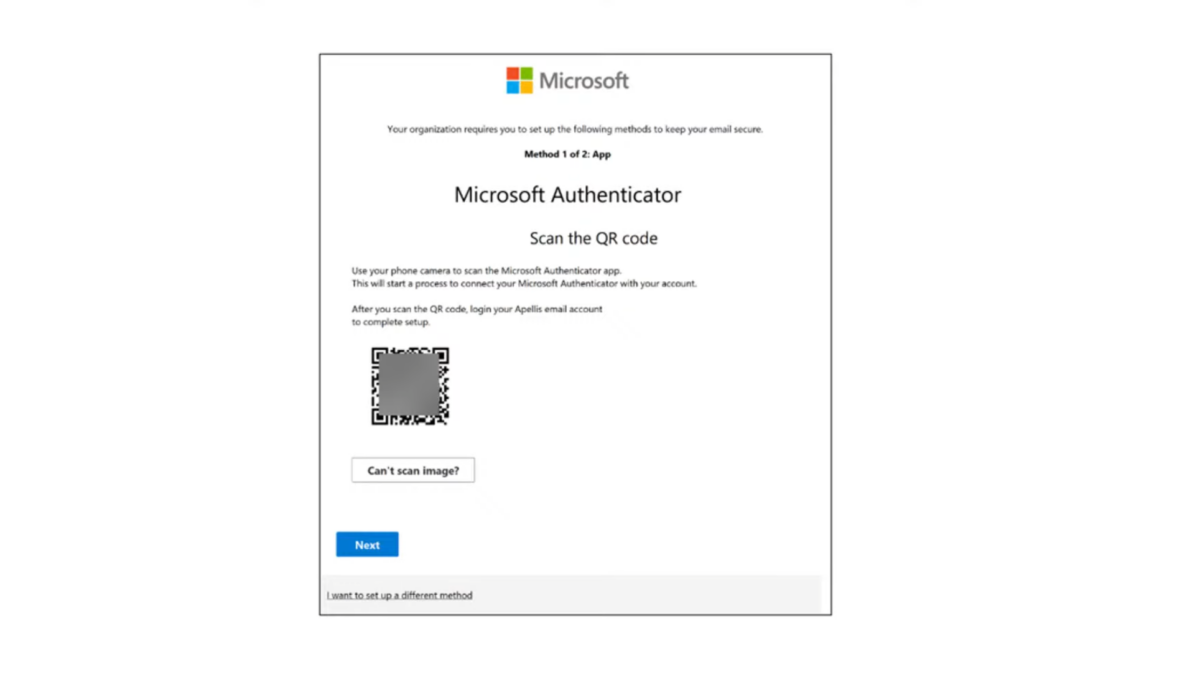
Example of a mail including QR codes which is similar to the Microsoft Authenticator registration flow

Attackers using Bing redirect or Cloudflare CAPTCHA to check and require that the HTTP requests are made from mobile devices, to limit the risk the domain is flagged by well-protected machines with advanced protection and URL-scanning.
Defender product protection to protect against QR codes
Since phones can be personal (not corporate-managed) with less corporate-owned protection it is recommended to implement additional layers of defense across the complete protection suite. It is important to keep the products optional configured, add additional layers across devices (Personal and Company-owned), and include QR phishing in the awareness program. More protection methods are explained in this blog.
Recently Microsoft implemented additional controls to detect QR codes more easily, directly via the Defender for Office protection suite. Before it was extremely hard to detect QR codes with phishing links when the image is included in the email body or attached as an image in the mail. Since the office mail protection is scanning the email content and not the images and sandboxing malicious QR codes.
As an improvement, Microsoft released the following features recently:
Image detection: Microsoft uses image extraction technologies. With the use of Defender for Office 365 and Exchange Online Protection Microsoft detects the QR Code during the mail flow. The system technologies extract the URL metadata from the QR Code; the URL is sent to the existing URL checks. Microsoft can use the URL in the detonation and sandbox environment to detect malicious threats. This process works similarly to the normal URL check.
Threat Signals: Microsoft uses multiple signals based on the message headers/ recipient details/ content filtering and relation via machine learning algorithms to detect potential malicious emails.
URL analysis: The URLs are extracted and analyzed by machine learning models/ Microsoft checks the URL against internal and external sources for reputation. This is all based on the Threat Intelligence layer and other collected sources. For this feature Defender for Officer 365 Plan 1/ Plan 2 is required.
Heuritcs-based Rules: Microsoft also deploys heuristic rules within Defender for Office 365 and Exchange Online Protection to reason over and block malicious messages.
Configuration for QR code protection
For the built-in protection as part of the Defender for Office suite, there is no specific configuration needed. QR code protection applies to EOP and Microsoft Defender for Office 365 Plan 1 & Plan 2 licenses. Good to know the detonation and sandboxing are only working for Office 365 Plan 1 & Plan 2 licenses.
Sandboxing environment
The sandboxing environment is only internal for Microsoft and not accessible by customers to check URLs or QR codes manually. The sandboxing future works automatically on the back end and shares the intelligence with the products themselves to determine the action and URL reputation.
Additional protection
Microsoft is adding a layer of defense with default protection for QR codes in Defender for Office. Not all QR codes can be scanned/ protected. It is always recommended to limit the risk and add additional controls in terms of limiting the risk. With the use of Microsoft technology, it is possible to add the following defenses to limit the risk:
Configure Network Protection/ Web Protection for mobile devices
Network Protection in M365D/ MDE is important – when the user scans the QR code the phishing landing site will be checked/ blocked when malicious and flagged by the detection algorithm.
Network Protection/ Web Protection is available for both endpoint and mobile devices (iOS/ Android). For mobile devices, it requires the implementation of Defender for Endpoint – Mobile Threat Defense. With the use of Network Protection/ Web Protection, it is possible to block automatically malicious URLs.
Microsoft Defender is available for Android and iOS and includes anti-phishing capabilities that block phishing sites from being accessed. This includes protection against malware that may be downloaded via the malicious URL.
Blog: Deploy Microsoft Defender for Endpoint on iOS using Intune/MEM
Protection against AiTM
For AiTM there are some detections/ protections available in the M365D/ Entra ID suite. Important here to make sure there are controls in place when the token is stolen or malicious activity is triggered.
Since most of the QR phishing is used to collect tokens/ cookies it is recommended to protect fully against the AiTM controls.
A good example is when scanning one of the QR codes the URL redirects to an AiTM phishing site.


Protection/ mitigation is possible based on various configurations:
- Phish-resistant MFA solutions (FIDO/ Certificate based authentication)
- Protect attacks using Conditional Access
- Monitoring/ protecting using Microsoft 365 Defender/ Azure AD Identity Protection
- Build-in alerting rules
View the following blogs to get more insights into which methods can be used to protect against AiTM.
AiTM/ MFA phishing attacks in combination with “new” Microsoft protections (2023 edition)
How to use Automatic Attack Disruption in Microsoft 365 Defender (BEC, AiTM & HumOR)
User awareness
End-user training and awareness are important to make awareness that QR codes are not always safe. Defender for Office 365 includes Attack Simulation Training to educate users against QR code phishing.
Attack Simulation Training includes QR code phishing simulations to educate users against QR code-based phishing attacks. It is available with Microsoft 365 E5 or Microsoft Defender for Office 365 P2 plan.
Attack Simulation Training
For using QR-code simulation training it is needed to use the technique How to Guide

As part of the payloads is the following payload available: Teaching Guide: How to recognize and report QR phishing messages

Sources
Microsoft: Protect your organizations against QR code phishing with Defender for Office 365
Microsoft: QR Code Phishing Protection




Appreciate all your posts, Jeffrey.
QR Code phishing was causing us a lot of problems until recently… probably due to this new built-in protection by Microsoft sandboxing and detonating the URLs within the QR code.
Please Microsoft jumped on this as quick as they did.