Microsoft Teams and other online collaboration tools increases massively in the last 2-3 years. Working from home became the new normal in most of the work environments and securing IT cloud environments changes. Recent changes in Microsoft Teams bring more options for attackers for sending messages directly to users and misuse app consent.
In this blog post, the basic capabilities of the Microsoft Teams integration with Microsoft Sentinel will be explained.
Introduction
Moving to, or increasing usage of Microsoft Teams means that the service should be more of a focus for defenders than ever due to its critical role in communications and data sharing. With the use of Microsoft Sentinel multiple insights can be created based on the office365/Teams data. In this blog, we are going to explain the collection of Teams activity logs and explain some of the options which can be created based on the Teams activity logs data.
Microsoft Teams is the hub for teamwork and focuses on chat, video meetings, calling, and personal/corporate data. External applications or bots can be added to Team workspaces. Of course, Microsoft Teams itself brings some security settings which are recommended ( guest access, default file permission, and approved apps). With the use of Sentinel we can build (custom) detections based on activity logs.
Teams – Microsoft Sentinel connector
The default Office 365 log connector enables the integration with Microsoft Teams. The connection is generally available and can be used in any environment. In comparison with the first Microsoft Teams connector release, no more App Registration or playbooks are needed to ingest Teams and parse logs in Sentinel.
Ingesting Teams logs via the O365 connector is free and part of the Office365 connector.
Prerequisites
- You must have read and write permissions on your Microsoft Sentinel workspace.
- You must be a global administrator or security administrator on your tenant.
- Your Office 365 deployment must be on the same tenant as your Microsoft Sentinel workspace.
For adding the new Microsoft Sentinel connector follow the below steps:
- Open Microsoft Sentinel
- In the menu select Data connectors (1)
- Select the office 365 connector (2)
- Open the connector page (3)

Now from the Office365 connector page configure the new data sources. Make sure you have read and write permissions. For Microsoft Teams data integration enable the Teams checkbox, in the configuration area, and then click the Apply Changes button.

Give Microsoft Sentinel some time before the first events are visible in Sentinel. It can take up some time before the Teams events are coming in for the first time.
Validate Microsoft Sentinel data
Validate the data source with the OfficeActivity table. Events are part of the OfficeWorkload MicrosoftTeams. For viewing recent events part of the Sentinel data source, use the KQL below query:
OfficeActivity
| where OfficeWorkload == "MicrosoftTeams"
| limit 100 Result:

The following items are some of the available Teams operations which can be used in KQL queries:
- TeamsSessionStarted
- MemberAdded
- AppInstalled
- BotAddedToTeam
- MemberAdded
- TabAddedTeamCreated
- TeamDeleted
- TeamSettingChanged
- TeamSessionStarted
Example: Teams operation: TeamSettingChanged contains Teams privacy/ permission change from private to public initiated by the user.

Microsoft Sentinel – default hunting / analytics rules
After configuring the connector we can build some logic and rules. Pre-created a couple of Sentinel rules are available and configured in Microsoft Sentinel.
Tested the extra value part of the Microsoft Teams content hub package. Except for 2 Logic Apps all data is already created in Sentinel with some more information and improved queries. Below comparison between the content hub (green) and Sentinel build-in rule (red).

The following data is already available in Microsoft Sentinel. (tested with new Sentinel environment)
- 2 Analytics rules
- External user added and removed in short timeframe
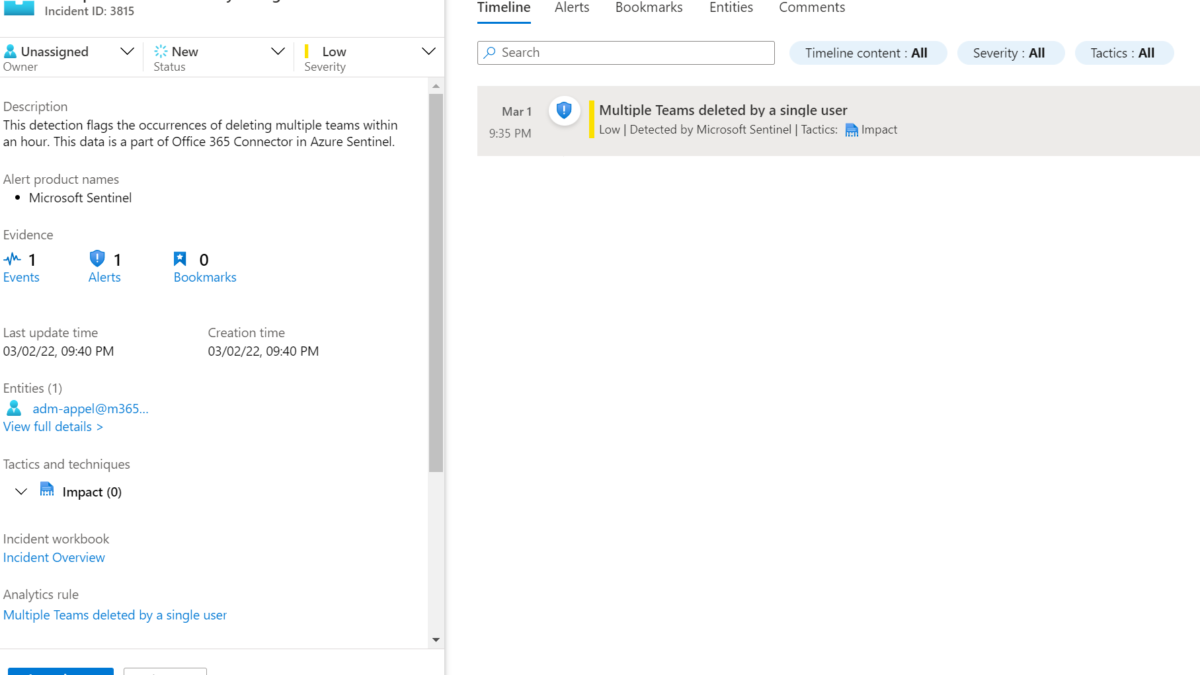
- Multiple Teams deleted by a single user
- 8 Hunting queries
- Multiple Teams deleted by a single user
- Bots added to multiple teams
- User added to Team and immediately uploads file
- Files uploaded to teams and access summary
- Multiple Teams deleted by a single user
- User made Owner of multiple teams
- Previously unseen bot or application added to Teams
- External user from a new organisation added to Teams
Microsoft Sentinel Results
Multiple Teams deleted by a single user: In a time frame of an hour when the users deleted 3 Teams the alert will trigger. The delete count can be easily changed in the query.


Previously unseen bot or application added to Teams: 3P apps like AgilePolly, 360 Tours, adam.ai, Adobe Sign, and many more are visible in Microsoft Teams. Each app requires content permissions which results in Enterprise applications part of AzureAD. In the best situation, there is a general policy in Microsoft Teams enabled for preventing non-approved bots/ apps. The hunting query can be used for detecting Bots/ apps added to Teams.
Recommended blog: OAuth consent: Protect against AzureAD OAuth Consent phishing attempts (Illicit consent attack)

More queries part of the community
Microsoft Community
In the Sentinel community some good examples are created for Microsoft Teams. Of course the data can be combined with AzureAD sign-in information or other events.
Matt Zorich/ Github.com/reprise99
- Finds guest accounts who were added to a Team and then downloaded documents straight away
- Detect new Teams app
Microsoft
Query a specific user to check if they were added to a Teams channel in the last seven days, or within a week:
OfficeActivity
| where TimeGenerated > ago(7d)
| where Operation =~ "MemberAdded"
| where Members has "<DisplayName>" or Members has "<UserPrincipalName>"
| project TeamName, Operation, UserId, MembersQuery whether a user’s role changed for a Team in the last seven days:
OfficeActivity
| where TimeGenerated > ago(7d)
| where Operation =~ "MemberRoleChanged"
| project TeamName, Operation, UserId, Members
| mv-expand bagexpansion=array Members
| evaluate bag_unpack(Members)
| where Role == '1'List of teams sites that have federated external users. These users have a domain name and/ or a UPN suffix that isn’t owned by your organization.

OfficeActivity
| where TimeGenerated > ago(7d)
| where Operation =~ "MemberAdded"
| where parse_json(Members)[0].Role == 3
| project TeamName, Operation, UserId, Members
| mv-expand bagexpansion=array Members
| evaluate bag_unpack(Members)Conclusion
Hopefully, this blog gives some insights into the Microsoft Teams data ingestion and possibilities in Microsoft Sentinel.
Stay tuned for more Microsoft Sentinel and security blogs. Blogs based on Microsoft Defender for Cloud Apps and Microsoft Teams are on the schedule for more in-depth protection.
Sources
Microsoft: Use Microsoft Sentinel to monitor Microsoft Teams
Microsoft: Office365 data source