The use of device tags within Microsoft Defender for Endpoint (MDE) is important for environments. Device tags can be used to give more control over how you manage your devices and scope devices for different groups. When onboarded many devices without any good name convention – device types e.q domain controllers can be hard to find. Tags in Defender for Endpoint are extremely powerful for identifying high-value machines during security investigations.
Why this blog?
When we look at large enterprise environments, there is often a huge amount of devices and teams for managing devices. Very common is a large amount of devices from different clouds, locations, and teams.
Now we are switching to a security point of view. As a SOC analyst during alerts – you need to know some basic knowledge of the devices which makes the investigation/ impact decision easier. Hopefully, there is some well-structured device name convention applied where you can read the type during incidents ( Identity servers, domain controllers, e.d) – but if we look at very large environments, is this not always the case. For example; domain controllers created for test purposes, part of Azure Bastion, or migrated environments – you don’t always know it directly.
This blog will show the concept for tagging domain controllers using Advanced Hunting to look up DC servers that are showing domain controller activity based on events. Tagging will be applied with Logic App and MDE API.
Recommended read, blogs published by Microsoft
Tomer brand: Automated machine tagging in just a few simple steps…
Steve Newby: Device tag blog series
NOTICE: Blog is written as a technical concept for sharing the idea. There is no guarantee. Of course – the concept can be extended more with some advanced KQL or Logic App detections. Test it well before doing anything in production.
Which data is available in Defender for Endpoint?
Currently, Microsoft shows different information fields directly for devices on the specific device page. The following device details are available:
- Domain or workgroup
- OS information
- Health state
- IP addresses
- Network activity
- UAC Flags
- SPNs
- Group Memberships
- Logged-on users
Is there information missing? yes, based on my opinion we need to see if the device is for example a domain controller part of the environment. This is useful information especially during the investigation and threat investigation.
Methods available
Multiple ways are available for tagging for example “Domain controllers”.
- Manual tag (set by MDE through the portal)
- Registry tag
- API
Manual tag
One of the easiest ways to tag a device is to simply add a tag value through the machine page in the portal. Multiple tags are supported. This is working for small environments.
Registry tagging
The tag can be applied by using the registry. By setting the tag value in the DeviceTagging key (HKLM:\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection\DeviceTagging)
- Only 1 tag can be used
- Tag cannot be removed from the portal
- Sync once a day – or during reboot to transfer new device information
API
API can be used to directly assign tags using the Defender for Endpoint APIs. With this method, you can add more tags. When there is already a registry tag applied for RBAC – the way of applying tags for specific types (e.g. domain controllers) for getting more insights.
Can we find domain controllers in Advanced Hunting
It seems there is no static value part of the device tables which we can use in Advanced Hunting for detecting all domain controllers.
For detecting domain controllers below gives a pretty accurate result.
Used tables and events:
Using DeviceNetworkEvents where the local port is 88. For removing non-relevant machines LocalIPType “FourToSixMapping” gives in my tested environments a good result without any non-domain controller.
Advanced hunting command:
Test of the results is accurate in the environments and shows known domain controllers:
//Show Domain Controllers using localport 88 - type FourToSixMapping
DeviceNetworkEvents
| where LocalPort == "88"
| where LocalIPType contains "FourToSixMapping"
| distinct DeviceId
| join
(DeviceInfo
| summarize arg_max(Timestamp,*) by DeviceId
)
on DeviceId
| project DeviceId, DeviceName, OnboardingStatusResult Advanced Hunting:

Automate with the use of Logic App
Let’s automate the findings and tag devices automatically with the use of the Defender API. For this blog, we’ll use Azure Logic App and the built-in Defender connector. Notice: Blog will show a simple example of Logic App.
It is now time to create and configure the actual logic app. The below example is using the built-in Defender ATP Actions.
Adding an Azure Logic App
- In the Azure portal, just search for “Logic Apps” and create a new app using the button “Add”

- Select the correct Subscription (1) and Resource group (2)
- Configure the instance type Consumption (3)
- Define a Logic app name (4)
- Select the correct Region (5)
- Press review+ create

Create the logic flow
For the configuration of the app flow, which is needed for applying the correct device tag – I am using the Logic Apps Designer and selecting the start template Blank Logic App.
Schedule trigger
The first start point is the “Schedule” and uses the “Recurrence” as a trigger. Recurrence is used for selecting the interval frequency.

For example, set the flow for a run every Friday, ensuring new domain controllers are tagged weekly. Each specific timing setting can be used for applying device tags. Use a frequency that suits your needs.

Get MDE hunting results
Next up, we will use the first action. The first time you add an MDE action to a Logic App – you have to grant consent for Defender for Endpoint. Search for “Defender” in the action search and click on “Microsoft Defender”

Select the action Advanced Hunting part of Microsoft Defender

Now add the Advanced Hunting query directly in the query field. For the flow, only the machine ID result is required:
DeviceNetworkEvents
| where LocalPort == "88"
| where LocalIPType contains "FourToSixMapping"
| distinct DeviceId
Use the control For Each – for running the action for each unique result part of the Advanced Hunting. The output used is based on the results. Create Add an action for the next step.

Action: Tag Machine
For tagging devices, there is a built-in action part of the MDE group. Search for the Machine tag action. The name of the action: Machine – tag machine
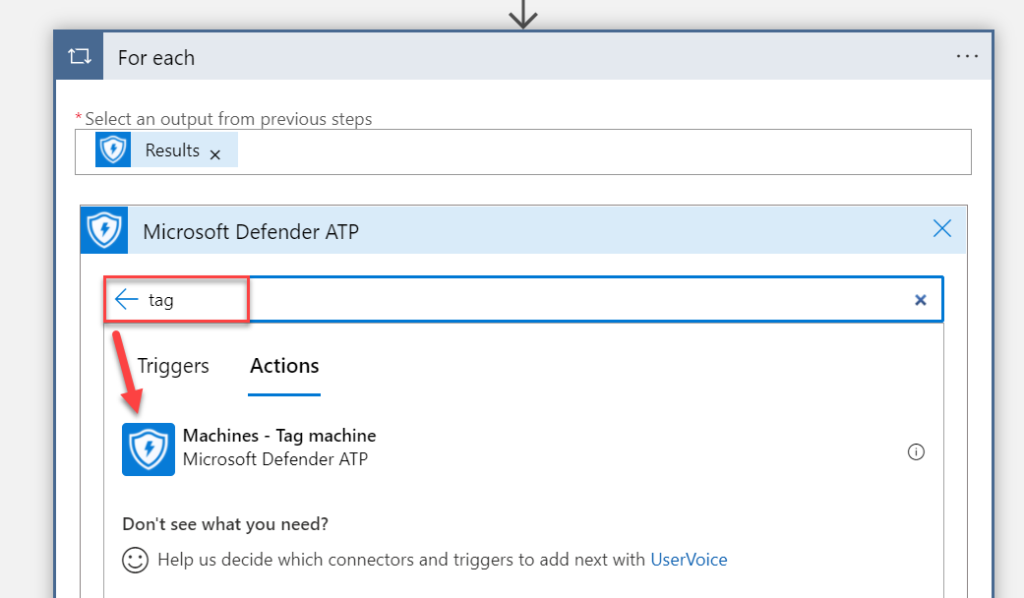
Now the following dynamics attributes are needed for correctly identifying the DeviceID and action.
- ID of the machine: Dynamic content DeviceId (1)
- Value: Specify your preferred tag | example: Domain Controllers (2)
- Action: Select Add (3)

After finishing the action the flow is completed. The flow shows the basics and gives more options for more in-depth control and validation.
The completed flow:
1: Recurrence: Each week on Friday
2: Get results based on Advanced Hunting
3: Apply for each result tag – Domain Controllers

Result Logic App
Advanced Hunting listing the correct DeviceID:

Input contains MDE ID of the machine and value Domain Controller

Output shows the correct MDE machine ID and applied device tag:

Results Defender for Endpoint
Portal
Defender for Endpoint shows directly the device tag for each applied Device ID.

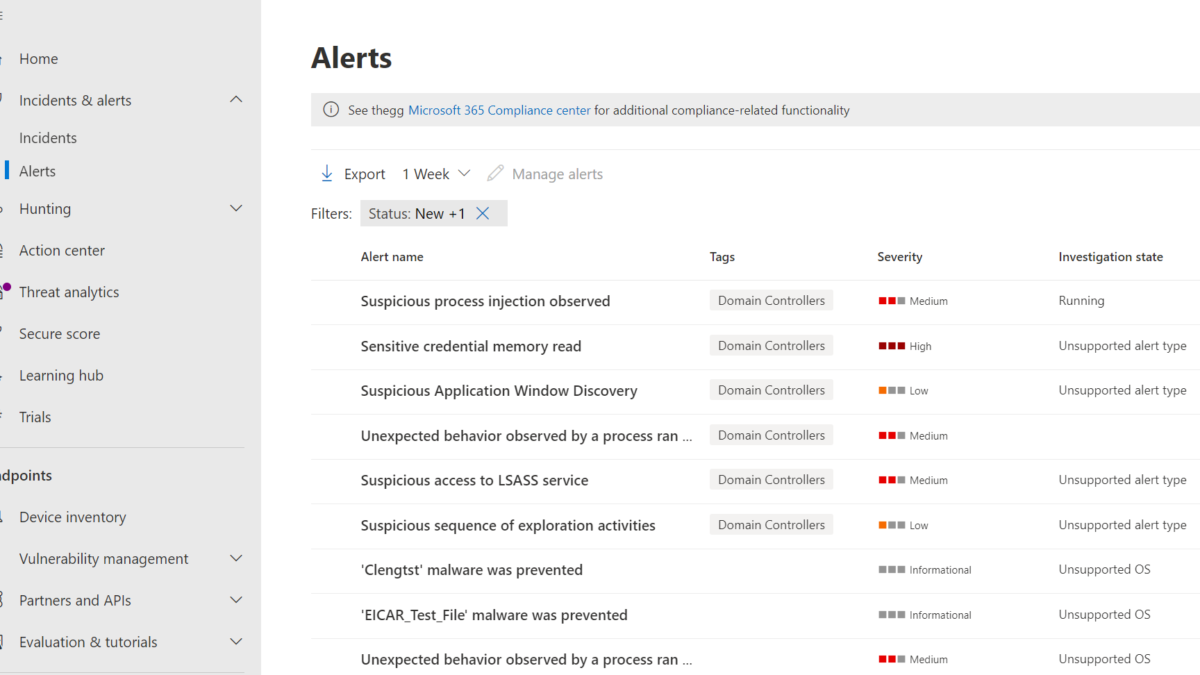
Alert/ incident view
Classification “Domain Controllers” is directly visible in the alert/incident view – without any manual action or look-up for each device.

Let’s summarize what we have learned:
- We helped the SOC analyst during alert triage with some device knowledge for identifying domain controllers
- Scheduled Logic App flow is enabled which syncs tags automatically
The sky is the limit! This concept can be used for many more options based on Advanced Hunting data.
Conclusion
The purpose of this blog was to give you some insights on what you can accomplish with the Microsoft Defender API and Azure Logic apps for identifying domain controllers servers and tag them automatically with the tag “Domain Controllers”. It shows a really basic example of Azure Logic App based on Advanced Hunting results.
The sky is the limit! for tagging devices based on Advanced hunting. Hopefully, this blog shows some of the options for detecting endpoints and tagging them automatically using Logic App.
Sources
Microsoft Docs: Create and manage device tags
Microsoft blog: Tomer brand: Automated machine tagging in just a few simple steps…
Microsoft blog: Steve Newby: Device tag blog series




Thanks! This is really illuminating. I just used this concept to auto-tag all our servers in MDE.