Cloud App Discovery is one of the most interesting functions available in Microsoft Cloud App Security. This blogpost is about the new MCAS monitoring mode for soft-block apps and gives user more information.
Earlier blogs explained more details about the enablement from Defender for Endpoint, integration with Azure Sentinel and the method for blocking unsanctioned or low reputation apps. Now all the focus on the new monitoring tag.
View the Cloud App Security blog tag for all the related blogposts
Important: At the moment of writing this, the warn feature is still in preview
What is cloud discovery?
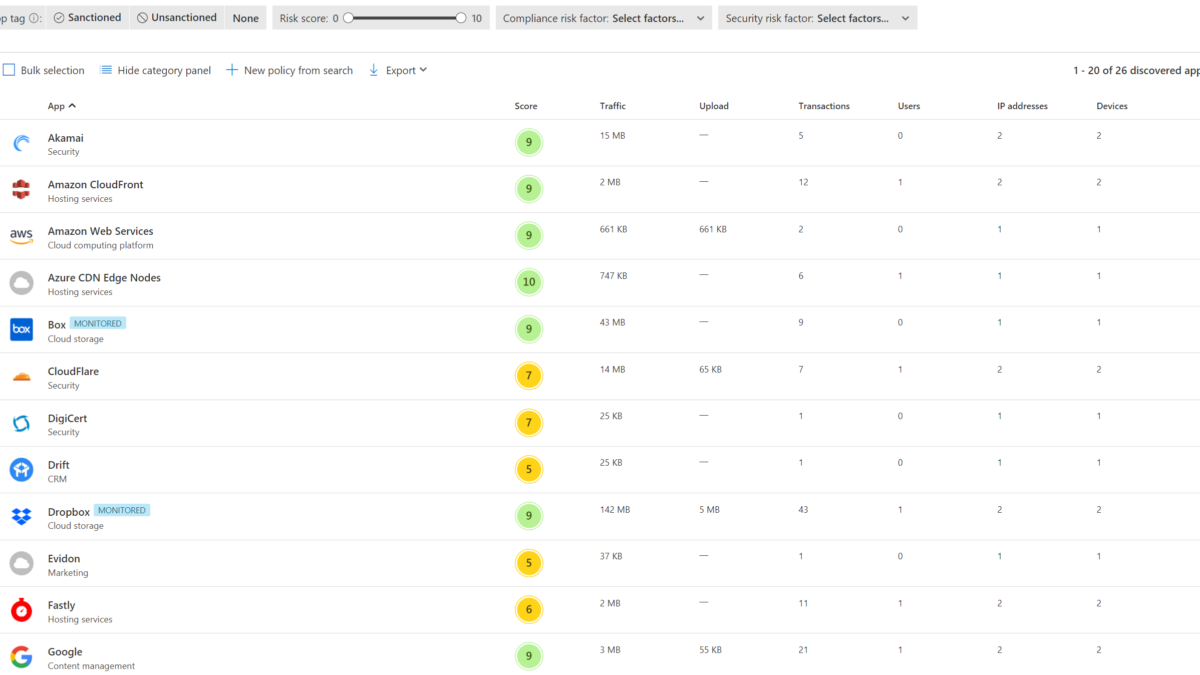
Cloud Discovery, which is one of the MCAS features, helps organizations to identify application and user activities, traffic, and usage hours for each application. For example the default storage app is OneDrive, with Cloud discovery it is possible to detect and block other cloud storage apps like Dropbox, Box and more.
The current challenge
But what about Shadow IT apps that are widely used by employees and used for productivity? For these apps a good balance is needed between employee productivity and the need for risk and compliance awareness. With the recently announced warn functionality more awareness is possible without direct user impact by blocking the app completely.
The situation
CompanyA using OneDrive as the main corporate cloud storage app. Some employees work with Dropbox for productivity and collaboration with external experts. Box is completely blocked for the environment.
With the new monitoring mode, it is possible to show detailed information for the Monitored apps. In this situation, it is mostly enough to warn users for the unmanaged app, so users can get more context on why they were blocked in the first place and what valid alternatives do they have for such apps in the organization and read more context for the internal data leakage rules of corporate data.
With the new soft block experience monitoring mode, admins are still able to monitor these apps and view the app trends. With details focussed on the bypass and app usage.
Cloud Discovery
The first requirement is to export events from the devices into Cloud App Security. Continuous reports give the option to import app events into Cloud App Security. Based on this blog we have the focus on Defender for Endpoint. Nice to know, more integrations are available with Log Collectors, Secure Web Gateway support – such as Zscaler.
Defender for Endpoint integrates with Microsoft Cloud App Security with the Defender for Endpoint agent. Cloud App Security uses the traffic information collected by Microsoft Defender for Endpoint (MDE). The native integrations work on each Windows 10 machine in different network environments ( public, Wi-Fi, remote access, or any other connection method).
For the correct working make sure the prerequisites are configured following this Microsoft article.
Defender for Endpoint
First, enable the MCAS integration from the Defender for Endpoint portal. For enabling the feature – follow the steps below:
- Go to the Security.microsoft.com portal
- Open Settings –> Endpoints
- Click on Advanced features
- Enable the Microsoft Cloud App Security feature

Custom network indicator feature
For the actions, it is needed to enable the Custom network indicators feature. With the custom network indicator, it is possible to block connections to IP addresses, domains, or URLs.
Go to the same MDE portal, and enable the Custom network indicators feature.
For the network indicator feature devices must be running Windows 10 version 1709 or later. The network protection feature requires Defender for Endpoint version 4.18.1906.3 or higher.

Microsoft Cloud App Security
Open the Microsoft Cloud App Security portal for enabling the Defender for Endpoint integration.
Note: Once the integration is done in both products, each app marked as unsanctioned will be added to the MDE custom indicators list. With network protection feature on block – each URL indicator will be blocked on the device.
For enabling the integration:
- Go to the MCAS portal
- Open Settings
In the setting view open the Microsoft Defender for Endpoint setting and enable the Microsoft Defender for Endpoint integration with the check-box Enforce app access.

Monitoring notification
The monitored functionality works without the user warning message. Optional is the redirect URL and Bypass duration.
- Redirect URL: Set a custom redirect URL for a company information page.
- Bypass duration: Set the Bypass duration time after which the user will get warned once again on access to the app.

Block the app / monitor the app
App tagging in Microsoft Cloud App Security is possible with multiple tag options. The following tags are available:
- Unsanctioned
- Sanctioned
- Monitored (new)
Monitored is the new way for giving the user a new soft block experience. Sanctioned means the app is approved. unsanctioned is blocked.
Recommended: Explanation Shadow IT Discovery / Microsoft – Boris Kacevich
The tags “sanctioned”, “unsanctioned” or “Monitored“ can be applied as tag to the detected applications. The custom tags can be used for specific monitoring purposes.
For tagging apps: open the MCAS Cloud app catalog page with the continuous report based on the Win10 Endpoint users. For each app the actions: sanctioned/ unsanctioned are visible.

Click on the three dots for more actions. For configure the Monitored mode, select tag app Monitored.

For each app tagged with the Monitored tag – the blue monitored label is visible.

Unsanctioned app result
If the application is not allowed to use in the organizations, tag the app as “unsanctioned”. With the Defender for Endpoint network protection feature enabled it will direct block access to the app.
For the unsanctioned apps the URL/Domain indicator is added in Defender for Endpoint with action type: block

Block Screen: Network protection enabled (block mode) and app unsanctioned in MCAS

Monitored app
For widely used non-approved apps by employees the monitored app tag is one of the options to not block the productivity and show only a warning message with compliance awareness information. Of course, check always the type of app and usage before.
When a user attempts to access the Monitored app, they will be blocked by Windows defender network protection but will allow the user to bypass the block.
For the monitored apps the URL/Domain indicator is added in Defender for Endpoint with action type: warn

Monitoring Screen: Network protection enabled (block mode) and app unsanctioned in MCAS
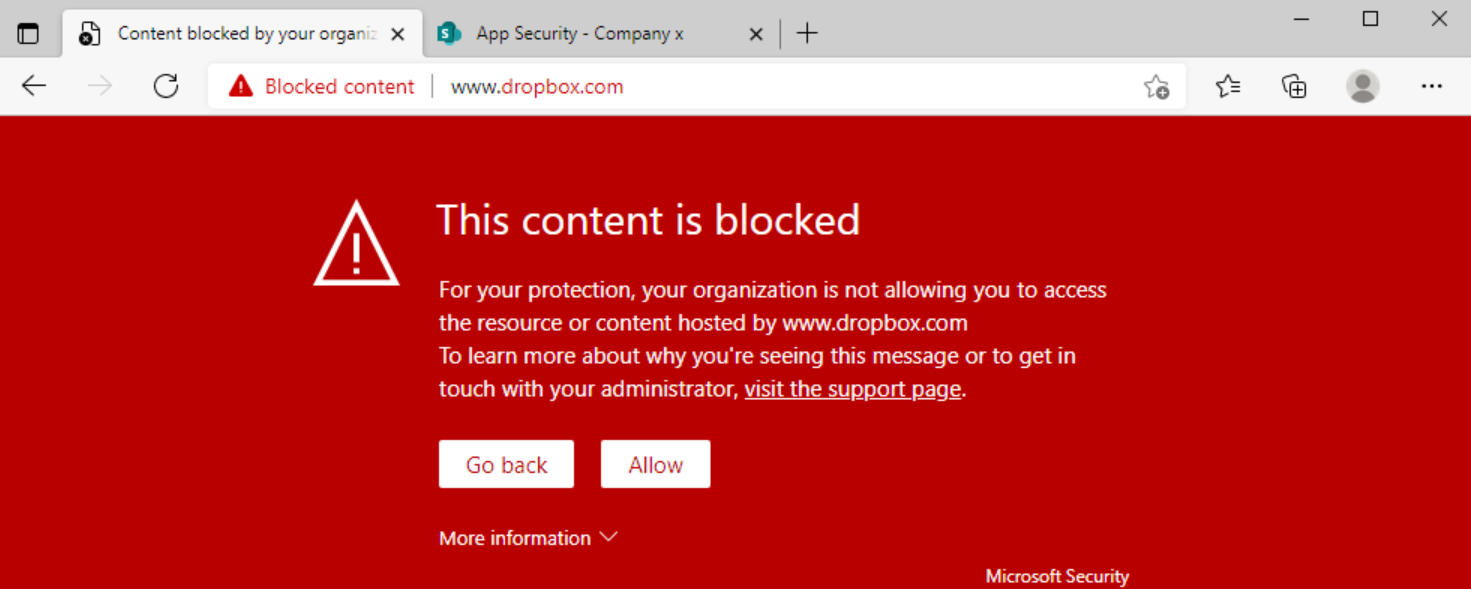
In the above block screen, there are some differences in comparison with block. First, the Allow button is visible. With Allow you can open always the site. If you click on the: visit the support page button you will redirect direct to the support page set in the MCAS settings. Example internal Sharepoint site with more app security information.

If the user clicks on Allow. Microsoft Cloud App Security will register the bypass in the MCAS detail page of the app.
Reporting
All the app/ user details are visible in Cloud App Security. The reporting contains new information with the following information:
- Users Blocked
- Users Accessed
- User bypassed
For viewing the information: Open the Discovered apps page and open the specific app page. For getting all the details for the specific app; click on Cloud app usage:

Conclusion
In this blog I have covered how you can take control of the Shadow IT management focusing on the new monitoring mode.
More blogs focussed on MCAS will follow soon. Open the MCAS page for previous blogs.