Defender for Cloud was since the release based on the Microsoft Monitoring Agent (MMA). Since august 2022 it is possible to auto-deploy the Azure Monitoring Agent. With this new improvement, it is finally possible to migrate entirely from the Microsoft Monitoring Agent (MMA) and switch to the new modern Azure Monitoring Agent (AMA) for Defender for Endpoint (MDE) and Defender for Cloud (MDC). Azure Monitoring Agent enables multiple advantages and new features.
Feature currently in public preview. Article latest updated: 15 Augustus 2022

History
Since the release of Defender for Cloud the feature was based on the Microsoft Monitoring Agent (MMA). The MMA agent was used to collect additional logs and onboard Defender for Endpoint. Defender for Endpoint some months ago migrated to the new unified solution which is based on the new unified agent and SENSE service for 2012R2 and 2016.
Difference between AMA and MMA
| Feature | AMA agent | MMA/OMS agent |
| Environments | Azure Other cloud ( Azure Arc) On-premises (Azure Arc) | Azure Other cloud On-premises |
| EPS per server on Windows | 5K | 1K |
| Events | All security events Common Minimal Custom | All security events Common Minimal None |
| Support for file-based logs | Public Preview | Yes |
| Support for IIS, DNSS logs | Public Preview | Yes |
| Support for DCR Data Collection Rules | Yes | No |
| Supports scoping | Yes | No |
Recommended read; Migrate to Azure Monitor Agent from Log Analytics agent | Microsoft
New feature
Part of the latest release is the new public preview availability for the Azure Monitoring Agent (AMA) which is now integrated as part of the auto-provisioning in Defender for Cloud. Defender for Endpoint is already moved from Microsoft Monitoring Agent. For the following Defender for Cloud services the auto-provisioning is used:
- Endpoint protection assessment- Security posture management (CSPM)
- Adaptive application controls – Defender for Servers Plan 2
- File Integrity Monitoring – Defender for Servers Plan 2
- Fileless attack detections – Defender for Servers Plan 2
Data collection is required to provide visibility into missing updates, misconfigured OS security settings, Endpoint protection status, and additional data collection.
Migrate from MMA to AMA
Migration from the Microsoft Monitoring Agent is possible directly with auto-provisioning. Before starting the migration it is important to check if Defender for Endpoint is already switched to the new unified solution for removing the dependency of the MMA agent.
Defender for Endpoint
The new Defender for Endpoint unified agent is generally available since April 11th, 2022. The new unified Microsoft Defender for Endpoint solution is supported for Server 2012R2 and Windows Server 2016 (systems based on the MMA agent). Announced: Defender for Servers Plan 2 now integrates with MDE unified solution
Microsoft announced the release of the unified agent integration which makes it possible to directly enable the new Defender for Endpoint unified solution and remove the dependency with Log Analytics Agent (MMA) and other legacy AV toolings like SCEP. Microsoft removes the complexity of the provisioning and created two machine extensions.
The following extensions are now available and available for Windows, Linux machines in Azure, and non-Azure machines connected through Azure Arc-enabled servers:
- MDE.Windows
- MDE.Linux
The MDE.Windows extension will remove SCEP from the Server 2012R2 machines during the installation of the new MDE unified solution. Part of the MDE.Windows extension is the onboarding of Defender for Endpoint (SENSE)
New available Azure policies:
- Deploy Microsoft Defender for Endpoint agent on Windows virtual machines
- Deploy Microsoft Defender for Endpoint agent on Windows Azure Arc machines
- Deploy Microsoft Defender for Endpoint agent on Linux hybrid machines
- Deploy Microsoft Defender for Endpoint agent on Linux virtual machines
The Defender for Endpoint unified installation package Md4ws.msi is part of the MDE.Windows Extension. Other scripts and the onboarding file are part of the package. The same goes for MDE.Linux extension where the Linux files are visible.
Windows MDE installation files are located in the following folder; C:\Packages\Plugins\Microsoft.Azure.AzureDefenderForServers.MDE.Windows
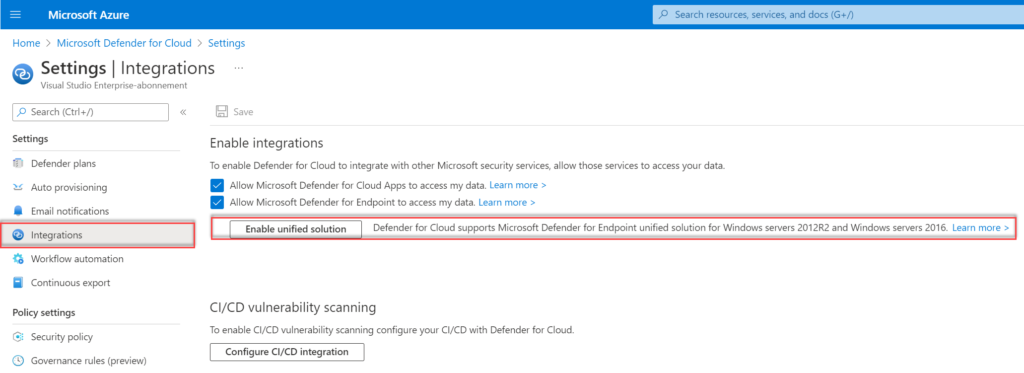
To enable the MDE unified solution in existing subscriptions you can easily opt-in to the unified solution on the subscription environment settings/integrations page. For opening the settings:
- Go to Defender for Cloud
- Go to Environment settings and select the subscription
- Go to Integrations
The button Enable unified solution is visible when the MDE integration was enabled before June 20th, 2022.
View the following blog post for the complete migration; How to upgrade from MMA-based Defender for Endpoint to MDE unified solution in Defender for Cloud? – Jeffreyappel.nl
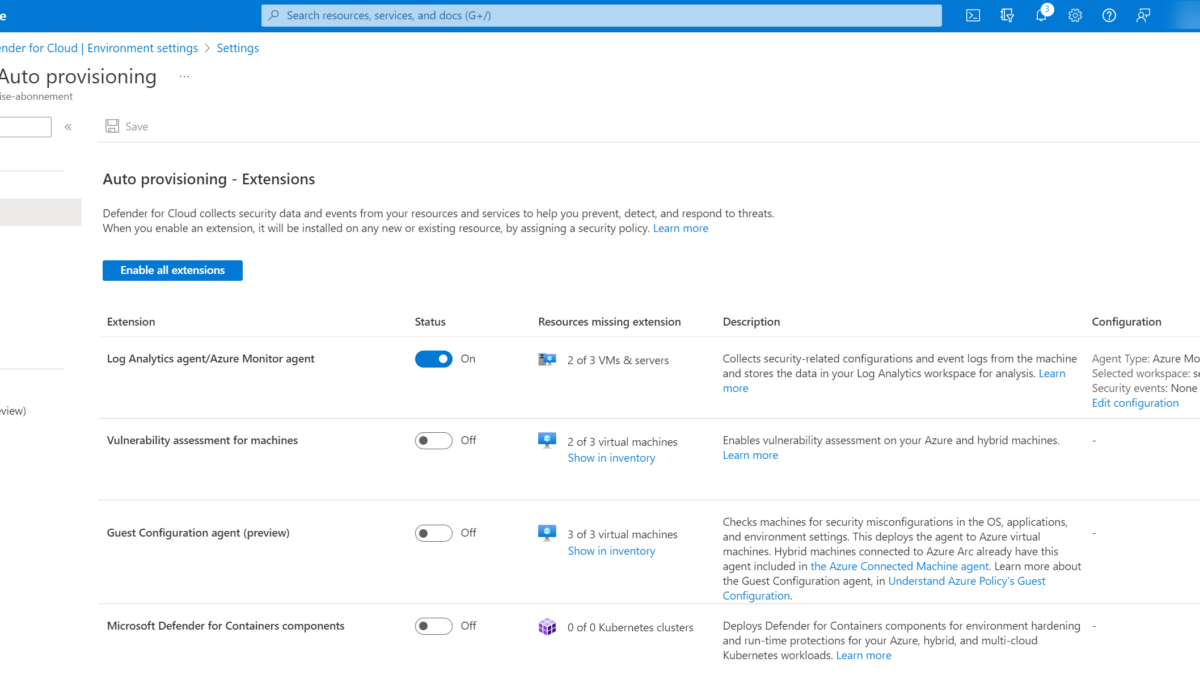
Configure auto-provisioning with Azure Monitoring Agent
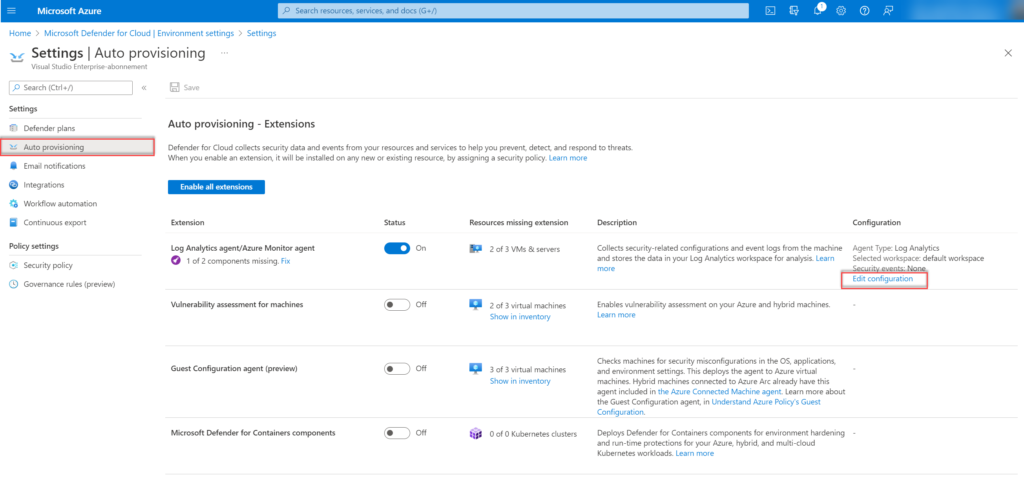
To deploy the Azure Monitoring Agent with auto provisioning use the following steps;
- Go to Microsoft Defender for Cloud and open Environment settings
- Select the correct subscription(s)
- Open the Auto-provisioning page
- For the Log Analytics agent / Azure Monitoring Agent, select Edit Configuration
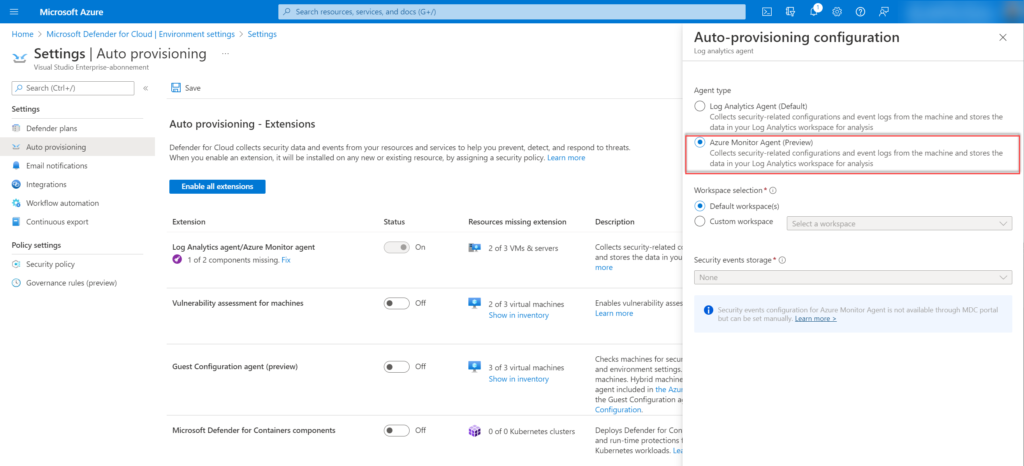
In the configuration screen there are two different agent types:
- Log Analytics Agent (Default)
- Azure Monitoring Agent (Preview)

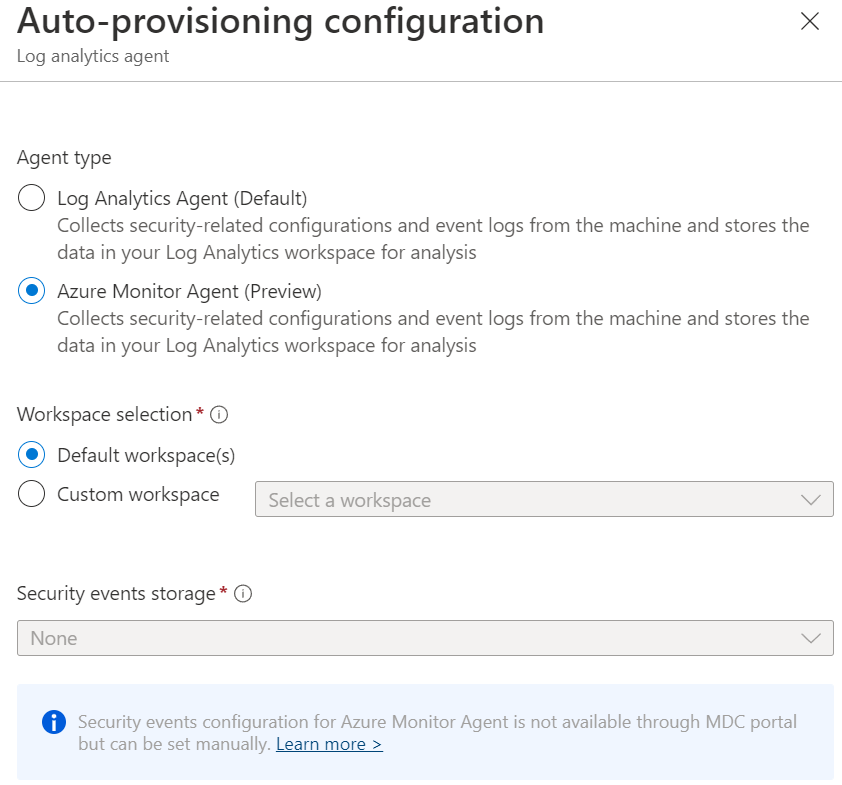
Log Analytics Agent (Default) is the agent based on the Microsoft Monitoring Agent. For the Azure Monitoring Agent select Azure Monitoring Agent (preview).
Data collected by Defender for Cloud is stored in Log Analytics workspace(s). For auto-provisioning, there is the option to use the default workspace(s) or a custom workspace.

When configuring the default workspace option; Defender for Cloud creates a new resource group and default workspace in the same geolocation, and connects the agent to that workspace. If a subscription contains VMs from multiple geolocations, Defender for Cloud creates multiple workspaces to ensure compliance with data privacy requirements. Based on the following name convention; DefaultWorkspace-[subscription-ID]-[geo]
When switching the toggle it will automatically install the Azure Monitoring Agent on all existing machines in the selected subscription, and all new machines created in the subscriptions.
Important: When using a custom workspace make sure to enable the additional workspace solutions manually. See part; Extensions.
Removal of the Log Analytics agent
When switching the toggle from MMA to AMA there is no automated uninstall. Make sure there is no duplicate data streaming enabled for the MMA and AMA agent. Microsoft says;
If a VM already has either SCOM or OMS agent installed locally, the Log Analytics agent extension will still be installed and connected to the configured workspace. Any other solutions enabled on the selected workspace will be applied to Azure VMs that are connected to it. For paid solutions, this could result in additional charges. For data privacy considerations, please make sure your selected workspace is in your desired region.
Microsoft Defender for Cloud portal
Duplicate agent
It is possible to run the Log Analytics and Azure Monitoring Agent on the same machine. Important to know – recommendations or alerts are reported by both agents and appear twice in Defender for Cloud. Advised is to use only one agent.
Security event collection
Based on the Log Analytics agent provisioning it is possible to enable additional security event collection – directly from the Defender for Cloud portal.

With the new Azure Monitoring Agent there is no option to collect additional security events to the workspace. When collecting events to Microsoft Sentinel it is advised to enable Data Collection Rules for collecting required events.
Tip: View the following blog post for the Data Collection Rules (DCR) configuration; Collect Security Events in Microsoft Sentinel with the new AMA agent and DCR – Jeffreyappel.nl
Extensions
The Azure Monitoring Agent installs additional extensions. The ASA extension is installed, which supports Endpoint Protection recommendations and fileless attack detection. The ASA extension is automatically installed when the auto-provisioning is enabled for the Azure Monitoring Agent.
Azure Monitoring agent uses two Log Analytics workspace solutions which are automatically installed when the auto-provisioning of the Azure Monitoring Agent is enabled with the default workspace.
The following Log Analytics workspace solutions are required;
- Security posture management (CSPM) – SecurityCenterFree solution
- Defender for Servers Plan 2 – Security solution
When using a custom Log Analytics workspace make sure the Log Analytics workspace solutions are installed manually.
Sources
Microsoft: Deploy the Azure Monitor Agent with auto-provisioning
Microsoft: Migrate to Azure Monitor Agent from Log Analytics agent




Hello Jeffrey, what would AMA bring us on top of MDC and MDE and integration between the two? I mean – we deploy Arc for our on-premises machines, MDE.Windows gets pushed because of the integration, so we don’t have autoprovisioning enabled (because before we could not have MMA installed as that would break the existing SCOM config, and when AMA came available, we didn’t even bother. Machines are visible in Arc, MDC and MDE and we don’t have a log analytics workspace to look after. We just can’t tell if we are missing any recommendations (We are currently on MDE plan P1, maybe later move to P2 if that is worthwile)
Hi Andre,
I will explain the question more in-depth in one of the next blogs.
Have received the same question in the past few weeks.
I have done this with a client and after migrating to the AMA agent, I am seeing that all servers are showing as “monitoring agent not installed” and shows an error.
Do you know if this is expected?
Hi Jeffrey,
by default, the new onboarded VM’s in Log Analytics Workspace are vissible within the workspace as ‘Direct connected’. When installing the new Azure Monitor Agent (preview), the connection type is ‘Azure Monitoring Agent’. Now I see the specific VM twice in the workspace. Is this normal? And how can we delete the ‘old’ direct connected connection?
Thanks, Mark
Hi Mark, Is the MMA agent still installed on the machine with the workspace?
Both the AMA and MMA/OMS agents can co-exist on the same machine and send data. If they both send data, from the same data source to a Microsoft Sentinel workspace, at the same time, from a single host, duplicate events and double ingestion charges will occur.
Let me know when more information is needed. Feel free to ping me on one of the socials.
More information: https://learn.microsoft.com/en-us/azure/sentinel/ama-migrate