Microsoft announced earlier this year that it would block VBA macros on downloaded documents by default for all customers. Last week Microsoft announced that it will roll back this change based on ‘user feedback’ which raises security concerns.
Microsoft announced the change in February 2022. Starting by July 2022 a rollback has started for the Current Channel. There is still a plan to make it the default for all users.
Microsoft gives the following update;
Following user feedback, we have rolled back this change temporarily while we make some additional changes to enhance usability. This is a temporary change, and we are fully committed to making the default change for all users.
@Microsoft
Update July 20, 2022;
We’re resuming the rollout of this change in Current Channel. Based on our review of customer feedback, we’ve made updates to both our end user and our IT admin documentation to make clearer what options you have for different scenarios. For example, what to do if you have files on SharePoint or files on a network share.
@ Microsoft
For years Microsoft Office contains automation capabilities called active content, the most common and most used automation capabilities are macros in the Office stack. Office warns users about these macros, users could still decide to enable the macros by clicking a button. Bad actors sends macros in Office which include malicious payloads. The impact is large where malware and malicious code can be enabled using the macros feature in Office.
A wide range of threat actors continues to target customers by sending documents and including them with malicious macro code.
What was the initial idea?
Microsoft announced in February 2022 the new default behavior for Office apps where VBA macros obtained from the internet will be blocked by default. A message bar will appear for users notifying them with a button and warning text. Blocking macros obtained from the internet reduces the threat possibility massively, and blocks threat actors from using the Macro technique. Image source: Microsoft
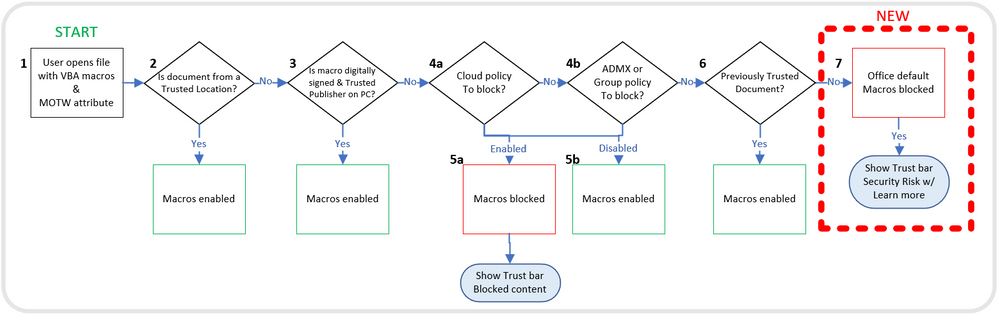
The change announced in February 2022 includes Access, Excel, PowerPoint, Visio, and Word. Specific targeted on version 2203 and higher.
Don’t wait for Microsoft
As already written above, Microsoft Reverses the decision to block VBA Macros by default. When viewing the current attack landscape, Office VBA macros are still heavily used by threat actors for deploying malicious macros code. It is not ideal to wait for Microsoft – immediate action is recommended to restrict VBA macros usage. Fortunately, there are several options, which we will discuss later for blocking/ restricting VBA macros usage and protecting it for all Office versions without any more waiting time from Microsoft.
Malicious activity Emotet/ Macros usage
Malicious Office documents have continued to be an issue for organizations. A good example is Emotet, TrickBot, QakBot, Icedid, and many more. For example, Emotet uses multiple interesting reverse engineering techniques (code obfuscation, calculations) and is back after some months of silence.
Emotet is a really a really great piece of malware to practice more advanced reverse engineering techniques on. It uses several different levels of code obfuscation to complicate static analysis. pic.twitter.com/Emr2kcMS2I
— MalwareTech (@malwaretech) July 2, 2022
Malware “Emotet” is becoming more common in the news. Distribution of Emotet is mainly via email and focussing the attack method on Word and Excel including macros code. Emotet does not contain malicious code and acts more as a platform allowing infected devices to infiltrate other malware.
Credit card stealing with Emotet
Emotet developers are currently adding new ways and techniques. Added recently is a new credit card module that is designed to harvest saved credit card information stored in Google Chrome profiles.
Emotet is rising after months of silence
Interesting read, published by sans.edu on Emotet Infections with Cobalt Strike. After a couple of months of inactivity, Emotet is still active and rising.
Based on key findings from the ESET Threat Reports T1 2022 is that the Emotet botnet has risen. ESET threat report shares the following information:
We can also confirm that Emotet – the infamous malware, spread primarily through spam emails – is back after last year’s takedown attempts, and has shot back up in our telemetry. Its operators spewed spam campaign after spam campaign, with Emotet detections growing by more than a hundredfold!
The largest part of Emotet activity involved Word documents tainted with malicious macros/code. Emotet was first sighted as a banking trojan in June 2014. Emotet has changed massively and focussing now more on a crime-as-a-service platform that is selling access to compromised systems to other groups.
Once Emotet is running on a computer, it typically downloads and executes other strains of malware, example; Dridex, Gootkit, IcedId, Nymaim, Qbot, TrickBot, Ursnif, and Zbot.
Recommended read by welivesecurity.com(ESET); How Emotet is changing tactics in response to Microsoft’s tightening of Office macro security
Besides Emotet, there are many more examples that actively target Office macros. Where Microsoft rolls back the feature; it is time for manual action to reduce the risk.
Prevention – Disable internet macros using GPO
Without the action from Microsoft; organizations can block internet macros based on Group Policy settings. Block macros from running in Office files from the Internet prevents users from inadvertently opening files containing macros from the internet.
The Policy is available for Access, Excel, PowerPoint, Visio, and Word.
| Application | Policy location |
|---|---|
| Access | Microsoft Access 2016\Application Settings\Security\Trust Center |
| Excel | Microsoft Excel 2016\Excel Options\Security\Trust Center |
| PowerPoint | Microsoft PowerPoint 2016\PowerPoint Options\Security\Trust Center |
| Visio | Microsoft Visio 2016\Visio Options\Security\Trust Center |
| Word | Microsoft Word 2016\Word Options\Security\Trust Center |
Prevention – Disable internet macros using MEM/Intune
Microsoft Intune can be used for blocking internet macros. The settings catalog is generally available (GA) for Windows and macOS devices. The settings catalog lists all the settings you can configure in one single place.
Usage of the settings catalog is quite easy. For configuring the first policy go to Microsoft Endpoint Manager admin center.
- Select Devices – Configuration profiles – Create profile
- Select platform Windows 10 and later
- Select profile type Settings catalog


Fill in the basics (name, description) and click during the Configuration settings panel on Add settings.

Search now for the setting; block macros from running in Office files from the Internet. The result gives configuration options available for Access, Excel, PowerPoint, Visio, and Word. Select the available settings
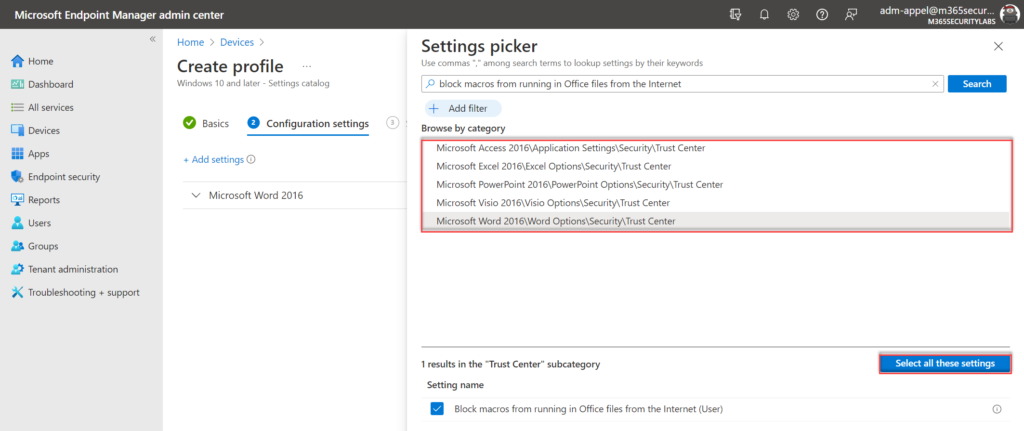
Configure the value in the settings panel on Enabled for the selected configuration settings. Recommended is to block for all relevant Office applications the macros downloaded from the internet.

Use additional Attack Surface Reduction Rules
In the above section, the block is focused on internet macros. It is possible to restrict the attack surface using attack surface reduction (ASR) rules. ASR is a collection of controls that restrict common malware and exploit techniques on Windows endpoints, part of Defender for Endpoint
Reducing your attack surface means protecting your organization’s devices and network, which leaves attackers with fewer ways to perform attacks. A couple of rules are available for specific Office protection. Recommended is to start enabling the rules in audit/ warn mode, and evaluate the events before blocking ASR on all devices.
Related Office ASR rules. ASR deployment is possible using Intune, GPO, PowerShell, or other supported deployment methods. More information here.
| ASR rule | ID |
| Block all Office applications from creating child processes | d4f940ab-401b-4efc-aadc-ad5f3c50688a |
| Block Office applications from creating executable content | 3b576869-a4ec-4529-8536-b80a7769e899 |
| Block Office applications from injecting code into other processes | 75668c1f-73b5-4cf0-bb93-3ecf5cb7cc84 |
| Block Office communication application from creating child processes | 26190899-1602-49e8-8b27-eb1d0a1ce869 |
| Block Win32 API calls from Office macros | 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b |
| Block execution of potentially obfuscated scripts | 5beb7efe-fd9a-4556-801d-275e5ffc04cc |
Further protection?
Where disabling internet macros gives some extra protection; it is advised to restrict VBA/ Macros usage even further on the system. Ideally, the complete Office macros feature is disabled. Many organizations currently rely on Office macros for day-to-day business functions. Organizations that are still using macros should develop a strategy for replacing them.
Unfortunately, the first step from Microsoft has been postponed. Which makes it more critical to make some progress in the disablement/ restriction of VBA/ Macros usage.
The security baseline for Microsoft 365 Apps for enterprise is a well-recommended security baseline for protecting Microsoft 365 Apps for Enterprise. (designed by Microsoft).
Disable VBA macros when possible, or when not possible – start the migration/ progress. VBA macros are still incredibly powerful for bad actors.
@jeffreyappel.nl
The following action items are recommended:
- Disable internet macros and don’t wait for Microsoft
- Disable macros where they’re not used
- Reduce your dependency on macros (when disablement is not possible)
- Disable macros unless they are in trusted files (when complete disablement is not possible)
- Implement attack surface reduction (ASR) rules for disabling some high-risk macros capabilities.
- Implement Office protection / Endpoint/EDR software ( Defender for Endpoint/ Defender for Office)
Conclusion
Office VBA Macros are still heavily used by organizations and threat actors for the deployment of malicious code/scripts. Microsoft reverses Office macros blocking. As already described; it is advised to deploy the configuration as soon as possible – and don’t wait for Microsoft. Ideally, block Office macros more in-depth and not only for internet downloaded files.



