It is time for part 3B of the ultimate Microsoft Defender for Endpoint (MDE) series. After Part 3A (Onboard Defender for Endpoint using Microsoft Intune) it is now time for some more technical deep-dive scoped on Defender for Cloud. Part 3B is focused on onboarding using Defender for Cloud (previously Azure Defender).
Important: Defender AV/ Next Generation Protection onboarding is critical and part of the complete protection platform. All AV/ Next Generation Protection information will be explained more in-depth including migration from other AV states.
NOTE: Blog series focuses on features in Microsoft Defender for Endpoint P2 all Microsoft Defender for Endpoint P1 features are available in P2.
Specific question or content idea part of Defender for Endpoint? Use the contact submission form and share the post ideas.
What is Defender for Cloud / Defender for Servers
Microsoft Defender for Cloud/ Defender for Servers is the way for onboarding Windows Servers in Defender for Endpoint. With Microsoft Defender for Servers (part of Defender for Cloud), you automatically deploy Microsoft Defender for Endpoint Plan 2 to server resources using the integration. The license is part of Defender for Servers.
Defender for Cloud contains two plans which enable Defender for Endpoint Plan 2. In Defender for Cloud there is a Defender for Servers Plan 1 and Plan 2 available. Plan 2 enables more benefits and additional enhanced security features.
Comparison table between Defender for Servers P1/ P2 offering: For 10$ extra in cost there are more features part of Defender for Servers that can be used for increasing the security posture. Defender for Servers Plan 1 is good when using only the Defender for Endpoint / Vulnerability management and agent onboarding. There is no difference in Defender for Endpoint, both P1 and P2 enable the Defender for Endpoint Plan 2 product.
When using Defender for Servers P2, it includes the Defender Vulnerability Management add-on capabilities part of the Defender for Servers P2 capabilities. No extra license is required.
| Feature/Capability | Defender for Servers Plan 1 ($ 5) | Defender for Servers Plan 2 ($ 15) |
|---|---|---|
| Microsoft Defender for Endpoint P2 | ✅ P2 | ✅ P2 |
| Microsoft threat and vulnerability management | ✅ | ✅ |
| Automatic agent onboarding, alert, and data integration | ✅ | ✅ |
| Security Policy and Regulatory Compliance | ❌ | ✅ |
| Integrated vulnerability assessment powered by Qualys | ❌ | ✅ |
| Log Analytics 500 MB free data ingestion | ❌ | ✅ |
| Threat detection (network/ OS/ control) | ✅ (MDE) | ✅(MDE and MDC) |
| Adaptive application controls (AAC) | ❌ | ✅ |
| File Integrity Monitoring (FIM) | ❌ | ✅ |
| Just-in-time VM access for management ports | ❌ | ✅ |
| Adaptive network hardening | ❌ | ✅ |
| Docker host hardening | ❌ | ✅ |
| Fileless attack detection | ✅ (MDE) | ✅ (MDE and MDC) |
| Microsoft Defender Vulnerability Management Add-on | ❌ | ✅ |
| Network map | ❌ | ✅ |
More information: Microsoft Defender for Servers plan features
How works the flow
Microsoft Defender for Endpoint integrates seamlessly with Microsoft Defender for Servers. Onboarding is automatic with the extension provisioning.
The following integrations are enabled using Defender for Endpoint with Defender for Cloud:
- Automated onboarding: Defender automatically enables the Defender for Endpoint sensor using the new unified agent for all supported system
- Single pane of glass: The Defender for Cloud portal pages display Defender for Endpoint alerts. Where you can drill down into Defender for Endpoint portal for more in-depth alert information
Auto-provisioning
When enabling Defender for Servers Plan 1 or Plan 2 and configuring the Defender for Endpoint integration – the Defender for Endpoint agent is automatically provisioned on all supported machines in the configured subscription. When enabled all supported machines in the subscription will be onboarded.
When enabled Defender for Cloud/ Defender for Servers deploys the MDE.Windows extension. Part of the MDE.Windows extension installation is the following:
- Onboard to Defender for Endpoint (MDE)
- Install Defender for Endpoint unified client for 2012R2/ 2016 (MD4WS.MSI)
- Uninstall when needed SCEP
- Install missing patches when needed
- Trying to update Defender AV product version for 2016 when not updated
Installation flowchart
A basic flowchart explaining the Defender for Servers Plan 1/ Plan 2 integration flow:
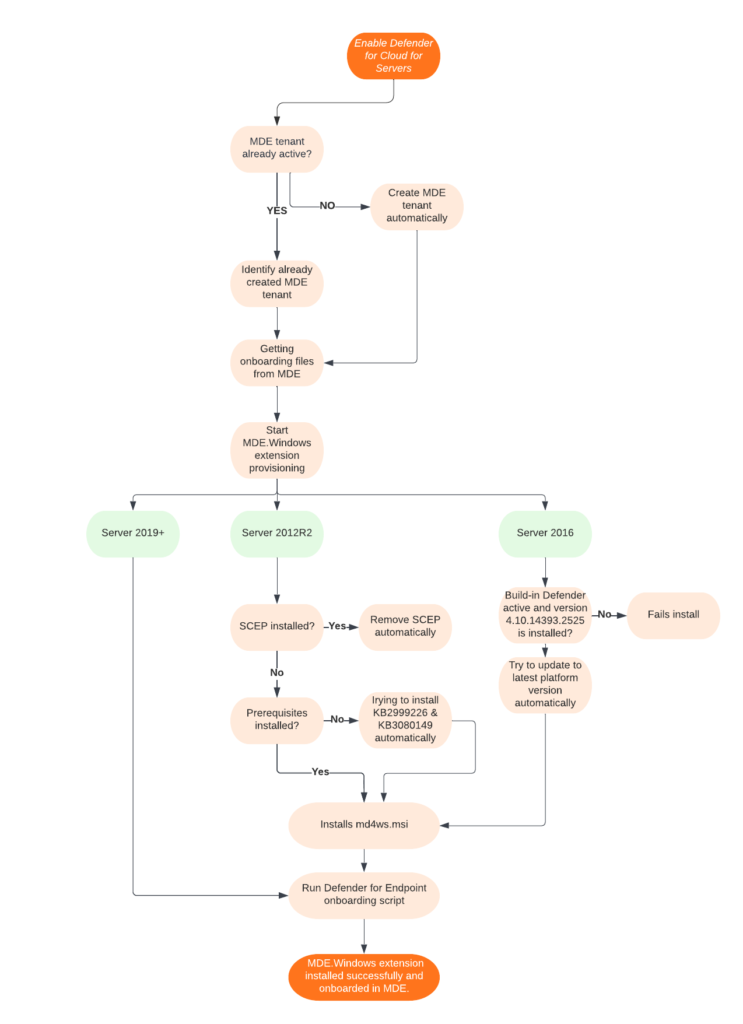
Prerequisites
Before starting with the integration, we need to confirm a couple of prerequisites for Defender for Endpoint. All MDE prerequisites are explained in part 3 of the series. The following is important when using the integration in combination with Server 2012R2 and Server 2016:
Unified agent
Defender for Cloud/ Defender for Servers installs the new unified agent for Server 2012R2 and Server 2016 via Azure Policy. The new agent requires some new prerequisites which are important for validating the installation of the MDE.Windows extension:
2012R2:
- Update machines with the latest monthly rollup
- KB2999226 & KB3080149 are required for 2012R2 (when using the latest monthly rollup, patches are already installed)
2016:
- The Servicing Stack Update (SSU) from September 14, 2021 or later must be installed.
- The Latest Cumulative Update (LCU) from September 20, 2018 or later must be installed. It’s recommended to use the latest available SSU and LCU and make sure the machines are fully updated before installing Defender
- Defender Antivirus server role feature must be enabled and running / up to date
- Update/ install the latest Defender Antivirus platform version (download package from Microsoft Update Catalog or MMPC)
For more information see: Prerequisites for Server 2012R2 and Windows Server 2016 | Microsoft Docs
Onboard on-premises / non-Azure machines
On-premises/ non-azure machines can be onboarded using Azure Arc or the new Direct onboarding options.
The preferred way of adding non-Azure machines to Microsoft Defender for Cloud is with the use of Azure Arc. When onboarded using Azure Arc the machine becomes an Azure resource and can be easily integrated with Defender for Endpoint. Defender for Servers integration works the same for Azure Arc devices. More information: Connect your non-Azure machines to Microsoft Defender for Cloud
When Azure Arc is not possible the new Direct onboarding solution is possible. With this new method it is possible to onboard servers directly to Defender for Endpoint with the script files and integrate it via Defender for Server for the licensing without additional agents on the server.
View part 3C for more in-depth Azure Arc/ Direct onboarding information. Microsoft Defender for Endpoint series – Onboard using Azure Arc – Part3C
Enable the integration – Defender for Cloud
In Defender for Cloud it is needed to enable Defender for Servers P1/ P2. Both versions are using the same provisioning. Below explains the manual enablement – PowerShell/ API can be used for enabling the integration for all subscriptions.
For enabling Defender for Servers:
- Sign in to the Azure portal
- Search for Microsoft Defender for Cloud
- In Defender for Cloud, select Environment settings

- Open the subscription page
- Enable Defender for Servers Plan 1 or Plan 2

For configuring Plan 1 or Plan 2 use the Change plan button for selecting the relevant plan.

Defender for Servers will be activated for all supported resources in the subscription – when enabled it will onboard Windows and Linux machines to Defender for Endpoint. Linux will be installed with the MDE.Linux extension. NOTE: Linux is onboarded in passive mode.
Enable Defender for Endpoint integration
In the same view for the specific subscription enable the Defender for Endpoint integration. In the section Defender plans open settings & monitoring.

Enable the component Endpoint protection

For new subscriptions, the unified solution and Linux machines integration are enabled and automatically configured.
(1) The button unified solution is only visible for older subscriptions (before June 20th, 2022) where Defender for Servers was already enabled. Advised is to use always the new unified solution which removes the complexity from the legacy MMA solution. When the button is visible; click; Enable unified solution.
(2) The button Linux machines is only visible when the subscription was created earlier than August 2021, with Defender for Servers enabled. Where there is no fix button part of the Endpoint security component all is fine.

Without Defender for Endpoint provisioning?
The following Azure policies can be used for installation without the provisioning in Defender for Cloud.
New available Azure policies:
- Deploy Microsoft Defender for Endpoint agent on Windows virtual machines
- Deploy Microsoft Defender for Endpoint agent on Windows Azure Arc machines
- Deploy Microsoft Defender for Endpoint agent on Linux hybrid machines
- Deploy Microsoft Defender for Endpoint agent on Linux virtual machines
Auto-provisioning Log Analytics agent / Azure Monitor agent
A common question from organizations; do we need to enable auto-provisioning when using only Defender for Servers/ Defender for Endpoint?

The new MDE solution for 2012R2/ 2016 doesn’t use or require the installation of the Log Analytics agent via auto-provisioning. The Defender solution is based on the SENSE service (compared with Windows 10/ Server 2019 and higher). Auto-provisioning is only needed for the following Defender for Server features. It is always recommended to use more features in Defender for Servers and use the auto-provisioning of the Azure Monitor Agent to use the benefit of all features.
- Endpoint protection assessment- Security posture management (CSPM)
- Adaptive application controls – Defender for Servers Plan 2
- File Integrity Monitoring – Defender for Servers Plan 2
- Fileless attack detections – Defender for Servers Plan 2
For Defender for Servers Plan 2 the following capabilities require additional monitoring agents. Endpoint protection recommendations check if an endpoint protection solution is installed. OS baseline recommendation checks the OS recommendations part of the system.
| Capability | Log Analytics | Azure Monitor Agent | Guest Configuration Extension |
|---|---|---|---|
| OS Baseline recommendation (CSPM) | ✅ | ✅ | ✅ (preview) |
| Endpoint protection recommendations | ✅ | ✅ | |
| File Integrity Monitoring | ✅ | ✅ | |
| Adaptive Application Controls | ✅ | ✅ | |
| OS-level and fileless attack detections | ✅ | ✅ |
Recommended webinar for more in-depth information: Demystifying Microsoft Defender for Servers
Defender AV – installed mode
There is no auto deactivation of Defender if there is another AV for servers active and Defender for Servers is enabled. Only Linux installs automatically in passive mode. When Defender AV is not primary it can be advised to configure Defender AV in passive mode. Important: make sure Defender AV is active when there is no 3rd party AV solution installed. Using the following registry key it is possible to force the passive mode:
- Path: HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection
- Name: ForceDefenderPassiveMode
- Type: REG_DWORD
- Value: 1
Monitor the installation
The installation of the extension can be monitored via the Azure machine extensions page. The onboarding is completely based on the MDE.Windows extension for Windows Endpoints. Extension installation status can be checked via Extension + Applications in Azure:
Open the specific VM -> open Extensions+applications -> open the MDE.Windows extension for more details

When clicking on the MDE.Windows extension name you will receive more detailed details about the provisioning and status.

When the extension is failed – it is always recommended to check of all prerequisites are correctly configured. Based on my experience the following is common:
- Defender not running in active mode for 2016/2019
- Defender server role not installed for Server 2016
- Correct prerequisites updates not installed
- Connectivity requirements not correctly configured
- Defender disabled via a registry key/ GPO setting
Conclusion
Part3B of the Microsoft Defender for Endpoint series is completed – focused on the initial Defender for Endpoint onboarding using Defender for Cloud. Stay tuned for the next parts; where more in-depth knowledge and experience will be shared around Defender for Endpoint focusing on all the components and additional settings.
Next, some smaller sub-parts focusing on the initial deployment for:
- Microsoft Endpoint Configuration Manager
- Group Policy
- Local script (PowerShell)
Searching for specific Defender for Endpoint information? Use the contact submission form and share the post ideas or contact using LinkedIn or Twitter. I will take all suggestions into the Defender for Endpoint series and help the community as far as possible.
View next part – Onboard using Azure Arc – Part3C
Sources
Microsoft: Deploy the Azure Monitor Agent with auto-provisioning
Microsoft: Migrate to Azure Monitor Agent from Log Analytics agent




Your defender series is just amazing! Thank you!
2 questions:
1. Can the script be deployed via GPO?
2. Have you see defender for business for servers? Seems like it doesn’t need all of this setup – just use a script and then MDE enforcement MEM policies.
yes – in general it is possible to onboard servers via the script. Currently, the only way of licensing is via Defender for Servers P1/P2.
So possible yes, all licensing is difficult.
Defender for Business is indeed possible via the script; all is Defender for Business focuses on smaller environments.
See: https://jeffreyappel.nl/microsoft-defender-for-business-how-to-use-it-and-what-are-the-differences/
Thanks for the reply!
I’ve am finally staring to deploy Defender for Business servers (same think just for small business). I’ve been using GPO with registry tagging and WMI filtering.
My issue is I am still trying to figure out how I should manage policies in Intune. We have a default Endpoint Security policy applied to all devices, which is meant for Client OSs.
How would I separate servers from the bunch without having to manage static groups manually? Most of our clients are on Business Premium licensing (so no E3/5 features).
Maybe its easier to just manage server polices in MDE instead of MEM?
I think I just found my answer that will be deployed this week!
https://techcommunity.microsoft.com/t5/intune-customer-success/support-tip-windows-server-devices-will-now-be-identified-as-a/ba-p/3767773
For example a subscription having windows and Linux arc machines Onboarded for which the MDC is being applied. Now I want to install MDC only for Linux servers but not for windows servers. Can I do that?
All windows servers should only install AMA agent and they use MIcrosoft Sentinel. But All linux servers should be onboarded to Microsoft Defender for Cloud(with MDE+GuestConfig+ASM agent).
Hi Jeffrey, exceptional blog series and of extreme use. However, could you explain what happens if you have endpoints onboarded to DFE by the enterprise license for on-premises systems and you wanted to onboard them via Arc into DFC and utilise the DFS capability, from a licensing perspective?
Would the agent be installed twice, thus meaning double costs?
Would you need to off-board the endpoint from the MDE tenant, onboard via Arc and redeploy the agent via the auto-provisioned MDFC connection?
What about servers with p1 and others with p2 ?
Os the licence apply to the subscription or resource group ?
If subscription is resource group based, maybe we can create RG_DFC_P1 and RG_DFC_P2 and assign different plan ?
Thank you