Recently there was some news with new gTLD domains. Google Registry launched eight new top-level domains: .dad, .phd, .prof, .esq, .foo, .zip, .mov, and .nexus. From a security point of view, the .zip and .mov can be dangerous (of course more TLDs are known as malicious targets). Malicious actors can put an index.html which triggers a download for viruses and trojans. Other domains that are heavily used for malicious activity are (.xyz, .click, .rest). Check Spamhaus for the top 10 most abused top-level domains. From my point of view, there is currently no benefit of using one of the new domains.
IMPORTANT update 1-6-2023: The solution seems overall not really stable, in some situations the internet is disconnected for the complete machine. Use the below information during the test. In my test lab, the configuration works perfectly on a couple of machines; where one machine (hosted in Azure) is disconnected completely from the internet. Use the below instruction at your own risk and deploy always to one single test device. Currently investigating why some machines are disconnected completely and all traffic is blocked.
| Blog information: Blog published: May 15, 2023 Blog updated: May 30, 2023 |
- gTLD: Generic top-level domains (.com)
- FQDNS: Full qualified domain name (Google.com)
When we check the recently registered .zip domains it contains a lot of “potential” malicious domains including domains like; (already registered)
- Microsoft-update(dot)zip
- microsoftoutlook(dot)zip
- Office365-update(dot)zip
- Officeupdate(dot)zip
- Software-update(dot)zip
- Microsoftdefender(dot)zip
- familyphotos(dot)zip
- rapid7setup-windows64(dot)zip
- sentinelone-installer(dot)zip
When the attacker sent the following message: I’ve attached familyphotos(dot)zip – download all photos via the sended link – for most of the users/regular consumers it is hard to read it is a potential phishing site. Source: Twitter
Another issue with the .zip gTLD is that software can automatically attach hyperlinks to ZIP file names in the text. See SANS.edu for more information and a snapshot of .zip domains with functional NS records. Source: SANS
Checked some of the registered domains and already there is some phishing stuff/ malicious content hosted on the domains. Microsoft-office(dot)zip is showing a nice Microsoft sign-in page to capture sign-in credentials.
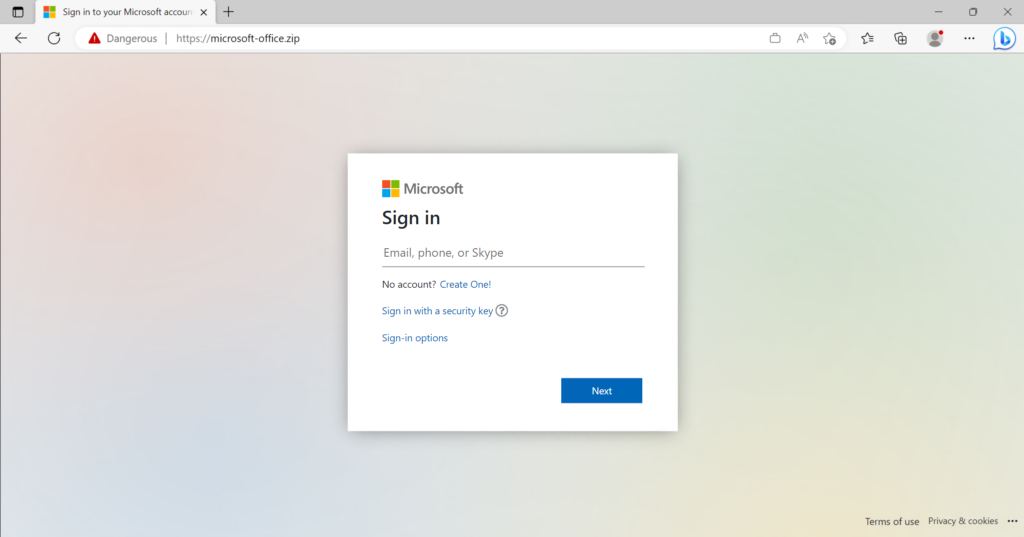
TIP: Defender SmartScreen is detecting the website as potentially malicious. Always recommended to enable Defender SmartScreen. See this blog for more technical information.
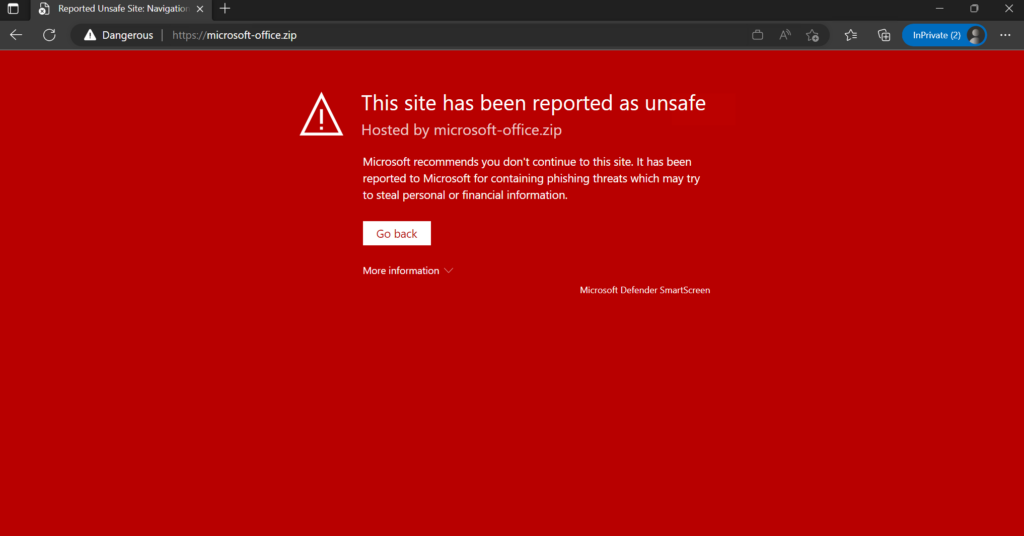
Enough information scoped on the potential risk – let’s explore how we can block the complete TLD domain using Microsoft technologies and Microsoft Intune.
How to block gTLD/ .zip domains
With the use of Defender for Endpoint there is the option for adding custom indicators. Indicators are not supported for blocking the complete top-level domain (.zip/ .prof/ .dad..) and are supported only the block the individual IPs/ URLs.
In combination with the Windows Firewall component, blocking the gTLDs and FQDNs is possible. Recently Microsoft announced a couple of new management features in Intune for managing the Windows Firewall easier.
Announced recently
6 months ago Microsoft announced the support for Fully Qualified Domain Name (FQDN) rules to block using Windows Defender Firewall and Microsoft Intune. This feature can be used for blocking FQDN rules and gTLD top domains.
Prerequisites
- Defender Antivirus must be turned on and updated to at least 4.18.2209.7 or later as platform version.
- Network Protection needs to be in block or audit mode.
- DNS over HTTPS (DoH) should be disabled
- Microsoft Intune (Settings seems currently only available via Intune management)
Reusable settings in Microsoft Intune
For blocking FQDN/ gTLD domains it is recommended to use the new reusable setting feature in Intune. With the new capabilities, it is possible to reuse setting in multiple policies. Admins can create and manage the policy from one single view- that can be reused across multiple policies. The new reusable group feature is currently supported for:
- Remote IP address ranges
- Fully Qualified Domain Name (FQDN) definition and auto-resolution
For configuring reusable go to Microsoft Intune (Intune.Microsoft.com) -> Endpoint Security and click Firewall
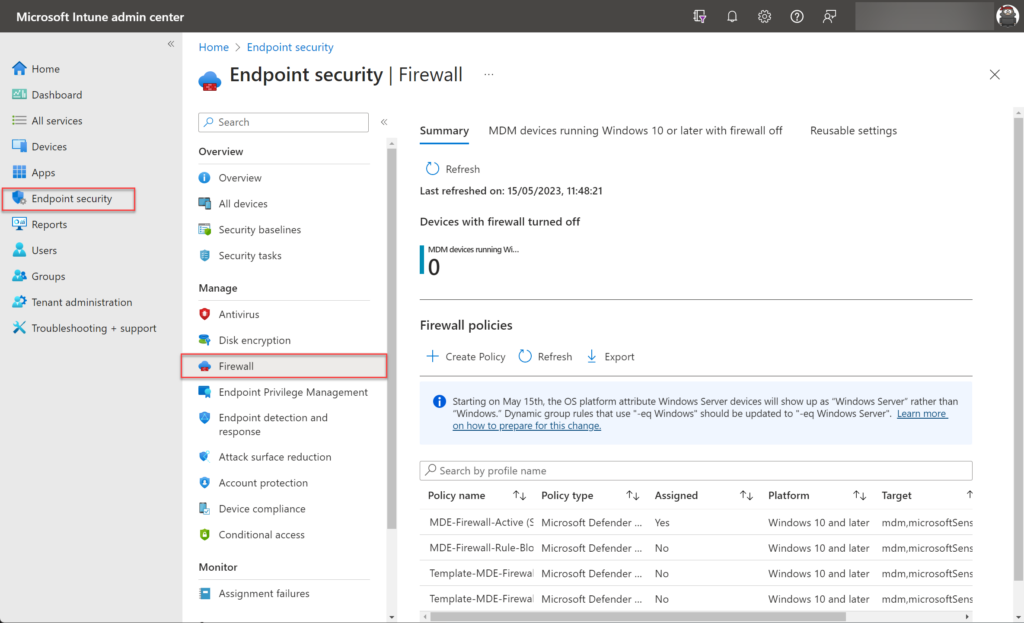
In the summary blade select the option Reusable settings and click Add
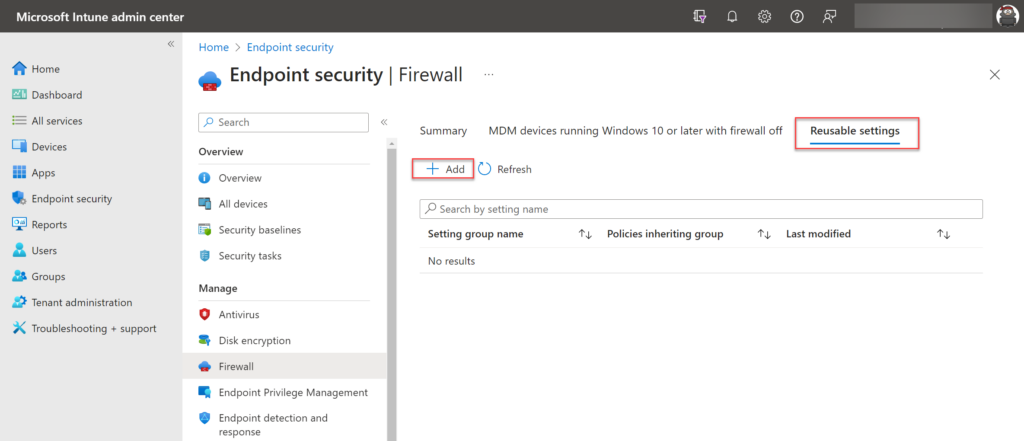
When creating the reusable settings it can be attached to more firewall policies, when updating the policies from the reusable settings page it updates all policies automatically. In this case, we can create a policy (Blocklist gTLDs) and include the “potential” malicious gTLDs.
During the configuration, it is important to enable Auto Resolve to true. When the Auto Resolve flag is set to true the fully qualified domain name and the addresses will be automatically resolved. This feature works in combination with Defender for Endpoint/ Sense. Without Sense enrolled this feature is not working. (not documented all it seems MDE is a requirement)
Click on Edit instance turn on Auto Resolve and add the domains. Add the domains in the keyword section including wildcard (*.zip) Do this again for each gTLD or FQDN.
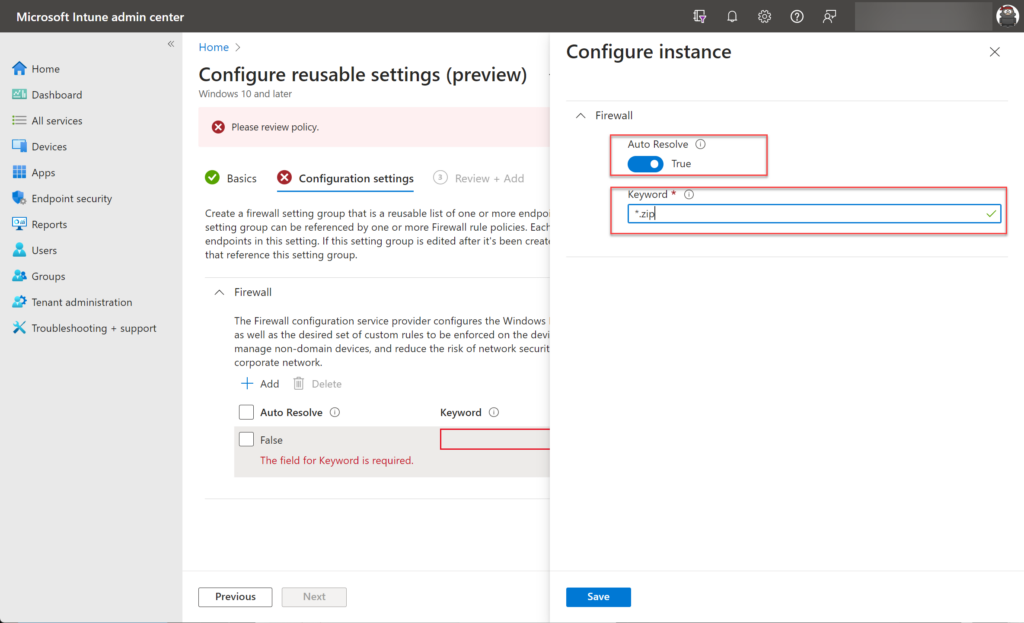
When all domains are added save the policy. When the reusable setting is created we can re-use the setting in one of the firewall policies/ or create a new firewall rules policy and deploy the policy to the endpoints.
New firewall rules policy
In Intune go to Endpoint Security – Firewall and create a new policy. Select as platform Windows 10, Windows 11, and Windows Server and profile Microsoft Defender Firewall Rules.
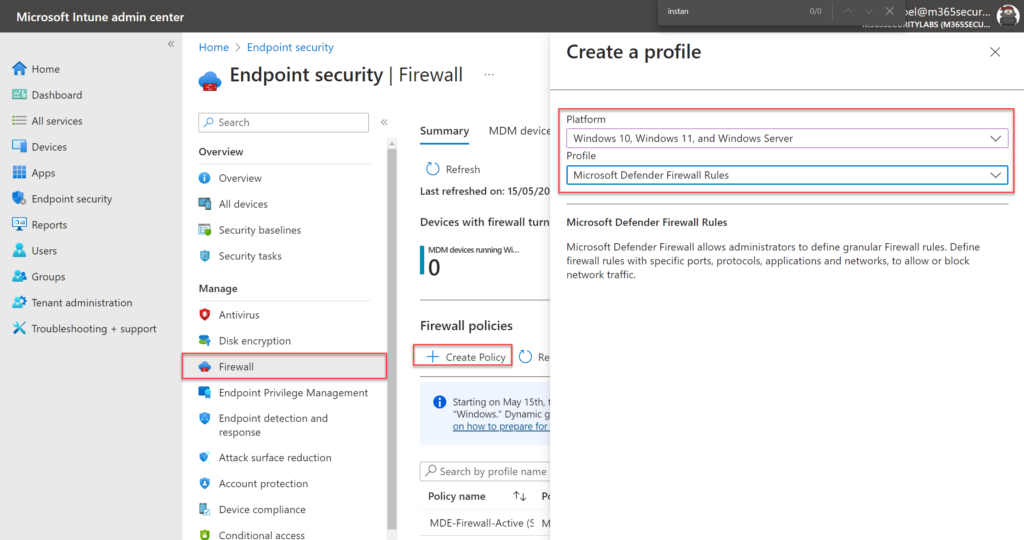
In the configuration settings of the new profile, we can select the earlier created reusable settings group.
Click Set reusable settings and choose the earlier created reusable settings for including the setting in the profile. After adding the reusable setting; click Edit rule.
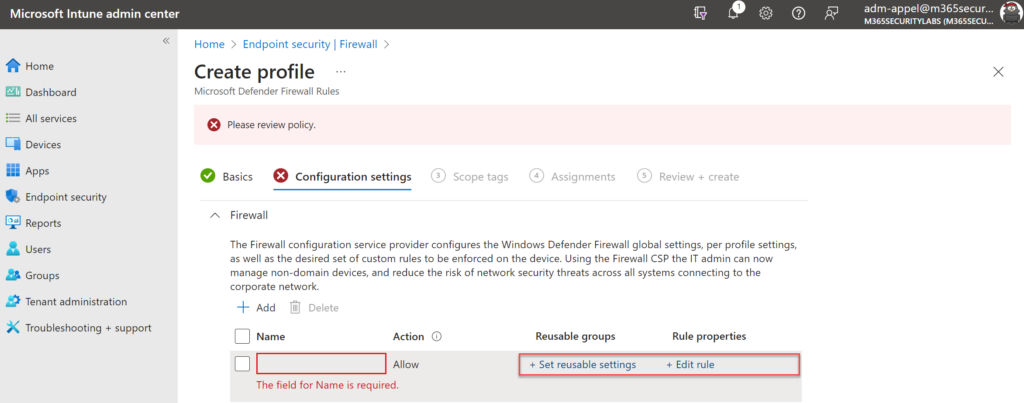
IMPORTANT: Before deploying the profile make sure that the reusable setting is selected and part of the reusable groups. Without selecting/ adding the profile it will block all traffic. Important to test always the rule on a couple of test machines. When added correctly the reusable groups are visible from the configuration setting page.
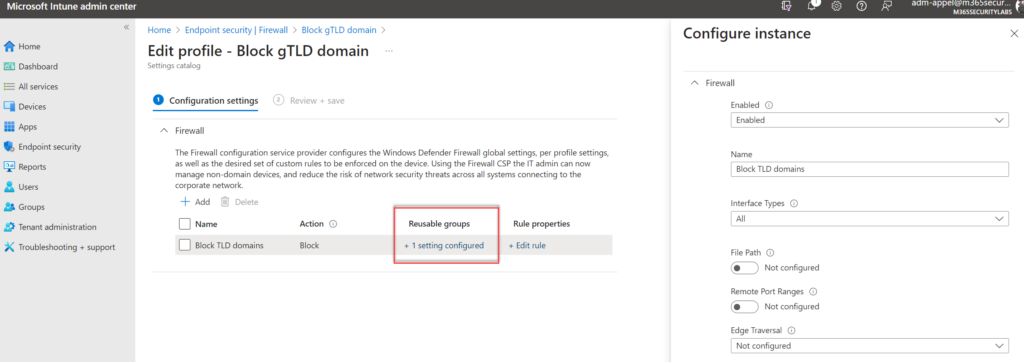
Configure the following settings for blocking the configured domains. The below configuration is scoped to all network interfaces (Wireless, LAN, Mobile Broadband, Remote access) and included all network types (Domain, Private, Public). Define/ change the policy when needed or target only specific network types/ interface types when relevant.
| Setting | Value |
| Enabled | Enabled |
| Name | Choose custom name |
| Interface Types | All |
| Edge Traversal | Not configured |
| Network Types | FW_Profile_Type_ALL |
| Direction | The rule applies to outbound traffic |
| Action | Block |
Deploy the policy to one of the groups. Ideally always testing firewall policies in a smaller scope including test devices before targeting the production channels.
Result
When the policy is applied the result is a blocked domain. With the use of reusable settings and FQDN/ TLD blocking there is the option for blocking the complete top-level domain. Using MDE it is always possible to block the full URL (test.zip) instead of the complete domain – it can be really useful to block the complete top levels domains. From my point of view, there is currently completely no reason why .zip/ .mov and more are useful for any normal reason. Of course, for malicious reasons they are great.
Credits to Nathan McNulty Twitter.com/NathanMcNulty for bringing attention to the prevention in combination with Windows Defender Firewall on Twitter.
Sources
Microsoft: Announcing enhanced control for configuring Firewall rules with Windows Defender





Does this not also block every zip download? because of the pattern *.zip match?
Thank you for explaining this. Do you know if it possible to add an exception? Like there is a *.zip URL that you do need access to.
Hi and thank you for the clear article.
I do run into problems with this setup; the *.zip TLD block seems to also block other websites not on this TLD. But I can’t figure out why.
I have setup the reusable rule and the policy, after some waiting it works and I can’t reach https://financialstatement.zip/ anymore. Chrome neatly starts the my newly created rule is blocking this.
BUT I also can’t reach a few other websites not on the .zip TLD, like:
https://www.learningcontainer.com/
and
https://hudito.nl/
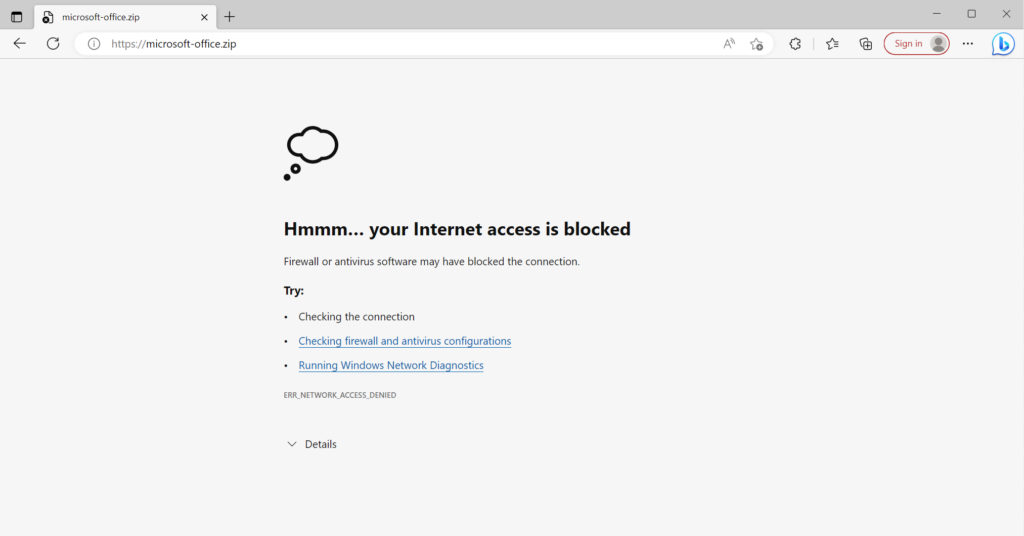
I can’t figure out why.. The error in the browser: ERR_NETWORK_ACCESS_DENIED
The Network diagnostics tool mentions the rule name which I have configured so I’m sure that this change affected this..
Hi Frank, Getting today the same on one of my machines, it seems not really stable and sometimes machines are blocked completly from the internet or specific URLs where the .zip is not part of the domain.
Currently checking why this happen; since it works for all other devices good. Removal of the firewall rule will fix the issue.
Additional information is added in the post as warning. Currently testing more in-depth.
A bit more information about my previous comment: https://learn.microsoft.com/en-us/answers/questions/1276288/blocking-a-tld-in-defender-for-endpoint
The MS employee stated that blocking a TLD is not supported which could explain the unpredictable behaviour.
Hi Jeffrey,
I followed the above steps and the internet got disconnected from the machine.
how can I revert back?
Hi, getting today the same on one of my machines, it seems not really stable and sometimes machines are blocked completly from the internet.
Currently checking why this happen; since it works for all other devices good. Removal of the firewall rule will fix the issue.
Additional information is added in the post as warning. Currently testing more in-depth.
Are there any specific strategies or best practices that can be recommended to enhance users’ ability to recognize and avoid phishing sites, considering the challenges highlighted in the provided Twitter source?
Thanks Jeffry for the post, I have opened a case at Microsoft support for them to explain what can happen. When I have news I will write.
I had this working flawlessly until the last round of MS updates. Now none of the TLDs are being blocked. Not quite sure what to do.