Microsoft Defender SmartScreen is available in various Microsoft products and adds an extra/first layer/filter of protection. The core component of Microsoft Defender SmartScreen is protecting against phishing or malware websites/ applications. For Windows 11 more features are available including SmartScreen Enhanced phishing protection
Microsoft Defender SmartScreen is not part of Defender for Endpoint and is included in the Windows security protection capabilities of the machine.
| Blog information: Blog published: March 2, 2023 Blog latest updated: March 2, 2023 |
Introduction Defender SmartScreen
Microsoft Defender SmartScreen is a core component of Windows and protects against phishing or malware and downloading of potentially unwanted applications. Some years ago Microsoft started with SmartScreen. SmartScreen was first introduced in Internet Explorer 7, then known as the Phishing Filter. Since Internet Explorer 8 SmartScreen is available as a filter for socially engineered malware.
SmartScreen is cloud-based and nowadays integrated into multiple products:
- Internet Explorer (Legacy)
- Windows Explorer
- Microsoft Edge
- Windows 11 Enhanced Phishing Protection (Windows 11, version 22H2)
How works Defender SmartScreen
Defender SmartScreen protects against phishing/ malware and unknown applications. It is not part of the Defender for Endpoint installation, there are some dependencies/ integrations between both products.
Websites
Websites are checked against known indicators or suspicious behavior. Defender SmartScreen determines if the page is suspicious based on the detected behavior on the websites or known indicators.
Websites are checked against a dynamic list of reported phishing sites and malicious sites. When there is a match between the website and the dynamic list it reports the phishing site. This list is based on consumer devices and corporate environments.
Microsoft Defender SmartScreen checks the reputation of any website, application, or web app during the first run.
Downloads
Defender SmartScreen is able to detect potentially malicious downloaded apps or app installers. Each downloaded file is checked against a list of reported malicious software and unsafe programs classified by Microsoft. When there is a hash based on the downloaded file Defender SmartScreen warns the user of a potentially malicious download.
Defender SmartScreen is even checking against a list of files that are well-known and downloaded by users (consumer and enterprise). If the file is not commonly detected it reports a warning during the download.
Downloads are detected for any performed download and are integrated into the Windows 10 operating system.
Why is Defender SmartScreen important?
When using Defender for Endpoint the component Defender SmartScreen is important. When using Microsoft Edge it is needed to configure Defender SmartScreen for enabling Network Protection. The Network Protection component depends on the layer of SmartScreen for the Microsoft Edge browser. Other browsers (Chrome, Firefox, Operate, and more 3rd party) are based on Defender Network Protection itself.
How works the network protection flow
| Feature | Microsoft Edge | 3rd-party browsers | Non-browser processes (e.g. PowerShell) |
|---|---|---|---|
| Web Threat Protection | SmartScreen must be enabled | NP has to be in block mode | NP has to be in block mode |
| Custom Indicators | SmartScreen must be enabled | NP has to be in block mode | NP has to be in block mode |
| Web Content Filtering | SmartScreen must be enabled | NP has to be in block mode | Not supported |
SmartScreen is built directly in Microsoft Edge and is responsible for Web Content Filtering, Custom Indicators, and Cloud App Rules. Only enabling Network Protection is not enough for getting network protection enabled in Microsoft Edge. Only Network Protection results in no protection for Microsoft Edge browsers.

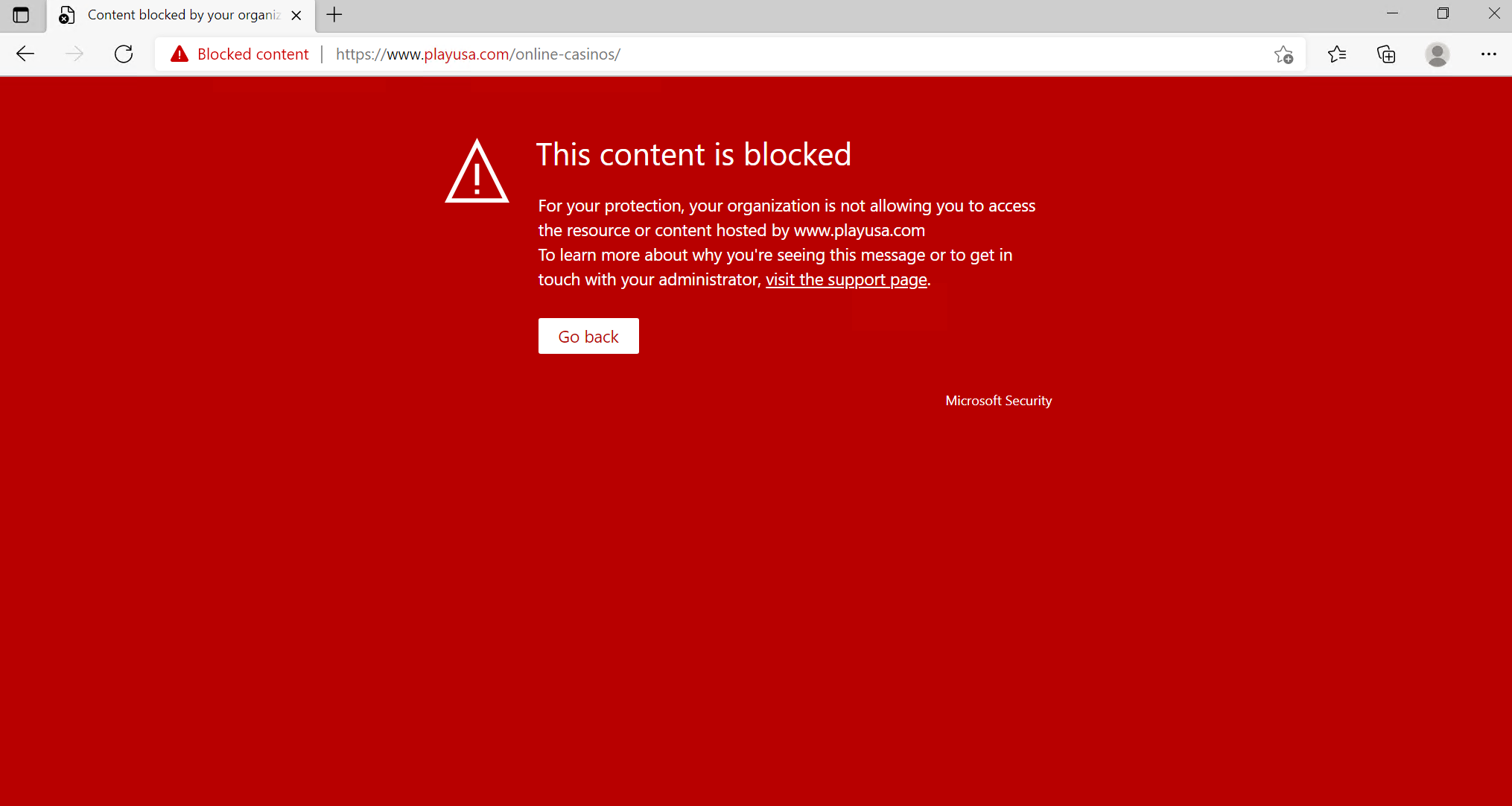
Image source: Microsoft
Block result: SmartScreen (MS Edge)
Where to configure Defender SmartScreen?
Currently, there are multiple methods where Defender SmartScreen can be configured. Intune and GPO are common for configuring SmartScreen. This blog is focussing on the deployment using Intune.
Intune settings
In Intune, SmartScreen configurations are located everywhere (security baselines, device restriction profiles, custom catalog, endpoint security profiles). My personal preference is to configure all the configurations of a feature in one profile instead of using multiple profiles for a feature/configuration. This makes it easier and works better to avoid possible conflicts.

In this blog post, I will configure SmartScreen via Microsoft Intune custom catalog profiles and configure the following profiles:
- SmartScreen base settings
- SmartScreen for explorer
- SmartScreen for Microsoft Edge
- SmartScreen Potentially unwanted app blocking
- SmartScreen Phishing protection Windows 11 (Only available since Windows 11) 22H2
- Malicious apps and sites warning
- Warn about password reuse
- Warn about unsafe password storage
Intune base settings (Edge/ Explorer)
For the configuration of the first profile go to Intune and create the first Settings catalog profile:
- First, sign in to the Intune Portal and go to Devices > Windows > Configuration Profiles. Select Create Profile.
- Select Platform as Windows 10 and later and Profile Type as Settings catalog and click Create
- Specify the name and optionally add a description
The Intune settings catalog makes it possible to configure all related settings needed for Microsoft Defender SmartScreen. On the Configuration settings window; select Add settings and type Defender SmartScreen.

Select the following settings in the settings picker selection:
- Administrative Templates\Windows Components\File Explorer
- Configure Windows Defender SmartScreen
- Microsoft Edge’SmartScreen settings
- Configure Microsoft Defender SmartScreen
- Configure Microsoft Defender SmartScreen to block potentially unwanted apps
- Enable Microsoft Defender SmartScreen DNS requests
- Force Microsoft Defender SmartScreen checks on downloads from trusted sources
- Prevent bypassing Microsoft Defender SmartScreen prompts for sites
- Prevent bypassing of Microsoft Defender SmartScreen warnings about downloads

Configure the following settings:
| Setting | Value | Explanation |
| Configure Microsoft Defender SmartScreen | Enabled | This policy needs to be enabled so Microsoft Defender SmartScreen is turned on, and cannot be disabled via the end-user. |
| Configure Microsoft Defender SmartScreen to block potentially unwanted apps | Enabled | This policy needs to be enabled to block potentially unwanted apps based on low-reputation scores. |
| Enable Microsoft Defender SmartScreen DNS requests | Enabled | With this policy Microsoft Defender SmartScreen is allowed to create DNS requests to get the IP address and use it for the IP-based protection layer. |
| Force Microsoft Defender SmartScreen checks on downloads from trusted sources | Enabled | With the enablement of this policy Defender SmartScreen checks always the download reputation from trusted sources |
| Prevent bypassing Microsoft Defender SmartScreen prompts for sites | Enabled | Users cannot bypass the Microsoft Defender SmartScreen warnings for potentially malicious websites |
| Prevent bypassing of Microsoft Defender SmartScreen warnings about downloads | Enabled | Users cannot bypass the Microsoft Defender SmartScreen warnings for unverified downloads |
| File explorer | ||
| Configure Windows Defender SmartScreen | Enabled | With this policy Microsoft Defender SmartScreen is enabled for the file explorer in Windows. |
| Pick one of the following settings (device) | Warn and prevent bypass | Users cannot bypass the Microsoft Defender SmartScreen warnings for unverified downloads |
Warn and prevent bypass vs Warn
Good to know. There is a difference in the type of protection/ prevention. Defender SmartScreen configuration is possible using the following preferences Warn and prevent bypass and Warn. What is the difference between the values?
Warn and prevent bypass – there is no option for the user to skip the warning message. It is not possible to bypass the warning and open the file/ website/ app.
Download warn and prevent bypass experience

Website warn and prevent bypass experience

Warn – The SmartScreen warning is visible when there is suspicious activity, but the user is allowed to bypass the warning and go to the website/ download the file. The warning is always visible.
Download warn experience

Website warn experience

SmartScreen Phishing protection Windows 11
Since Windows 11 version 22H2 there is enhanced phishing protection available in the SmartScreen component. Enhanced phishing protection helps with protecting work accounts against phishing and detects/ protects against unsafe usage on sites and apps. A nice one is the plaintext warning, when passwords are stored in plaintext (Notepad, Word, or any other Microsoft 365 app for example)
The new SmartScreen Phishing protection feature is part of the WebThreatDefense policy type in Defender. The best practice in Intune is to use the Settings Catalog for the configuration of the new settings.
For the configuration of the first profile go to Intune and create the first Settings catalog profile:
- First, sign in to the Intune Portal and go to Devices > Windows > Configuration Profiles. Select Create Profile.
- Select Platform as Windows 10 and later and Profile Type as Settings catalog and click Create
- Specify the name and optionally add a description
The Intune settings catalog makes it possible to configure all related settings needed for Microsoft Defender SmartScreen. On the Configuration settings window; select Add settings and type Enhanced Phishing Protection.

Select the following settings in the settings picker selection:
- Enhanced Phishing Protection
- Notify Malicious
- Notify Password Reuse
- Notify Unsafe App
- Service Enabled
Configure the following settings:
| Setting | Value | Explanation |
| Service Enabled | Enabled | Enhanced Phishing Protection in Microsoft Defender SmartScreen is in audit mode or off. All telemetry will be sent through Microsoft Defender. Enable = passive mode. |
| Notify Malicious | Enabled | Warns the user in the following situations: – Into a reported phishing site – into a Microsoft login URL with an invalid certificate – into an application connecting to either a reported phishing site or a Microsoft login URL with an invalid certificate When enabled notifications are enabled for the user. |
| Notify Password Reuse | Enabled | Enhanced Phishing Protection in Microsoft Defender SmartScreen warns your users if they reuse their work or school password. When enabled notifications are enabled for the user. |
| Notify Unsafe App | Enabled | Enhanced Phishing Protection in Microsoft Defender SmartScreen warns your users if they type their work or school passwords in Notepad, Winword, or M365 Office apps When enabled notifications are enabled for the user. |
Test: Unsafe app
Testing the enhanced phishing protection is easy. The notification for the unsafe app can be triggered by typing the work password in text apps. When the password it copied; there is a notification visible with the text: “It’s unsafe to store your password in this app”

Test: Password reuse
Currently, there is no whitelist available for specific apps. In some sort of situations, there are false positives when there is no full SSO experience and the account password is used to sign in with the same password.

Test: Notify Malicious
Notify Malicious is warning users when their work/ school passwords are used on websites:
– Into a reported phishing site
– Into a Microsoft login URL with an invalid certificate
– Into an application connecting to either a reported phishing site or a Microsoft login URL with an invalid certificate
Simulation is a bit difficult based on the reported phishing site/ Microsoft login URL with an invalid certificate.
Test SmartScreen features
Use the SmartScreen demo site for testing the configured SmartScreen configurations for Microsoft Edge and Windows Explorer.
The demo site is available via: demo.wd.microsoft.com
Test the Defender SmartScreen URL Reputation and App Reputation features.
URL reputation
Test the following feature in Microsoft Edge.
- Phishing page
- Malware page
- Blocked download

App reputation
Test the following feature in Microsoft Edge.
- Unknown program (warning when bypass is possible)
- Known Malware (block)

Available data in Defender for Endpoint
Using Defender for Endpoint Advanced Hunting it is possible to find the SmartScreen data in Defender for Endpoint. Part of the DeviceEvents is the action type SmartSreenAppWarning.
| SmartScreen Action type part of the DeviceEvents |
| SmartScreenAppWarning |
| SmartScreenExploitWarning |
| SmartScreenUrlWarning |
| SmartScreenUserOverride |
KQL query for showing all SmartScreenAppWarning/ SmartScreenUrlWarning events. Part of the AdditionalFields is the experience (Untrusted/ Phishing/ Malicious/ Exploit/ CustomBlockList)
DeviceEvents
| where ActionType has_any('SmartScreenAppWarning','SmartScreenUrlWarning')
| extend TriggerReason = parse_json(AdditionalFields).ExperienceSources
- Microsoft: Enhanced Phishing Protection
- Microsoft: Microsoft Defender SmartScreen overview





Thanks! This is great. Do you know a way to create a workable web filter to block porn, games, social media etc for those without Defender ATP?
Within the Defender stack, it is not possible to block websites by category for devices where Defender for Endpoint is not enrolled. Maybe there are other toolings available.