Microsoft released a new product with the name; Microsoft Defender EASM (External Attack Surface Management). The new product is based on the earlier products/ technology from the RiskIQ acquisition. Defender EASM is a new product in the Defender stack to provide an external view of the Attack Surface of internet-exposed assets.
| Blog information: Blog published: October 13, 2022 Blog latest updated: October 14, 2022 |
What is Defender EASM
Microsoft Defender External Attack Surface Management (Defender EASM) continuously discovers the digital attack surface to provide a view that is externally based on the online (internet-exposed) devices.
Defender EASM used the crawling technology part of the Microsoft infrastructure to discover assets related to online infrastructure, the technology actively scans to discover more insights and detects weak points. Data is based on the security graph and additional sources.
Defender EASMS discovers the following assets; (currently supported)
- Domains
- Hostnames
- Web Pages
- IP Blocks
- IP Addresses
- ASNs
- SSL Certificates
- WHOIS Contacts
All the above assets are used as a ‘seed’ to search through publicly available information. The biggest advantage is the combination with other data sources for calculating the Attack Surface Priorities/ Security Posture/ GDPR Compliance and OWASP.
With the use of this visibility, security and IT teams may recognize unknowns and gives visibility in the risk/ vulnerability scope and exposure control outside of the corporate firewalls.
What is the cost
For each resource, there is a 30-day free trial. After 30 days the price is $0.011 asset/day. For smaller companies, not a big deal. For larger companies/ enterprises, the EASM service can be quite expensive when you have millions of assets.
More information for the official pricing; https://azure.microsoft.com/en-us/pricing/details/defender-external-attack-surface-management/
Privacy and publicly available information
Microsoft Defender External Attack Surface Management contains global data. The pre-created attack surfaces from many organizations are available and can be added without any proof of ownership.
EASM can be abused by people with bad intentions. As already mentioned by Derk van der Woude | Medium, some sort of proof of ownership (TXT, Cname, Domains in Azure) would be nice in the future to prevent abused insights.
Microsoft shares the following;
For security purposes, Microsoft collects users’ IP addresses when they log in. This data is stored for up to 30 days but may be stored longer if needed to investigate potential fraudulent or malicious use of the product.
Microsoft Learn
More information: Data residency, availability and privacy
How to create Microsoft Defender EASM
First, we need to configure Microsoft Defender EASM via Azure. Go to Azure and search for Microsoft Defender EASM.
For the creation select the subscription and resource group. For the instance details configure the name and region. The name is the custom instance name of Defender EASM.
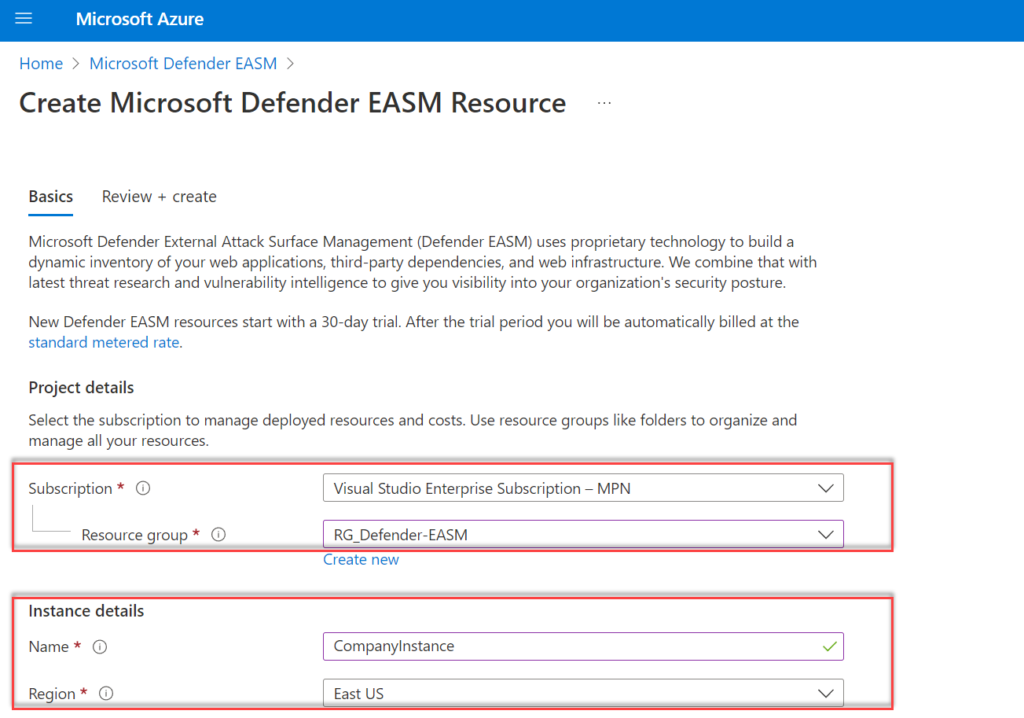
Region: Currently only the following regions are supported for Defender EASM:
- southcentralus
- westus3
- eastus
- eastasia
- swedencental
- Australieast
- japaneast
When the provided location is not supported – the following error is visible during the resource creation;
The provided location 'westeurope' is not available for resource type 'Microsoft.Easm/workspaces'. List of available regions for the resource type is 'southcentralus,westus3,eastus,eastasia,swedencentral,australiaeast,japaneast'. (Code: LocationNotAvailableForResourceType)New Defender EASM resources start with a 30-day trial. After the trial period, the normal pricing is counted for Defender EASM.
After the creation of the resource, the EASM instance is visible in the Defender EASM view in Azure with the configured instance name.
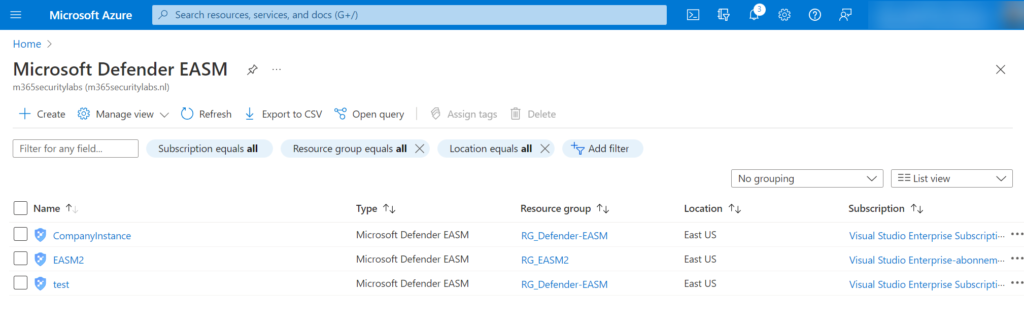
There is the option to combine data from different sources in one single instance. Personally, I would split the data and divide it into different resources – with the reason; visibility of data and the correct security exposure.
Use pre-created inventory
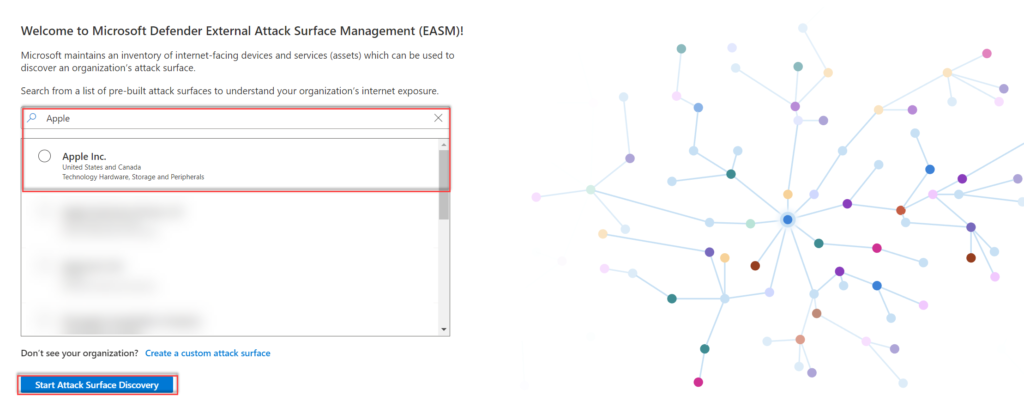
Microsoft maintains an inventory of internet-facing devices and services. From the list, multiple pre-built organization profiles are available. Search the company name (1); when not exists in the list click on Create a custom attack surface (2).
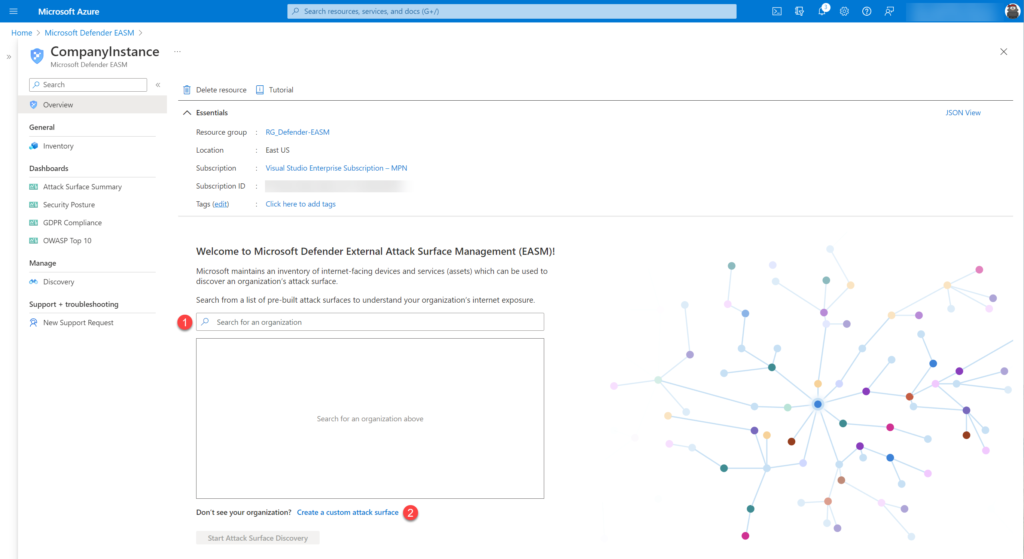
When the organization name is available select the organization and click Start Attack Surface discovery
Use custom attack surface profile
Organization not available in the list of pre-built attack surfaces? Click on; Create a custom attack surface. Recommended is to start with a single domain – after the initial creation, more seeds can be entered.
The following seeds can be configured:
- Domain
- IP Blocks
- Hosts
- Email Contacts
- ASNs
- Whois Organizations
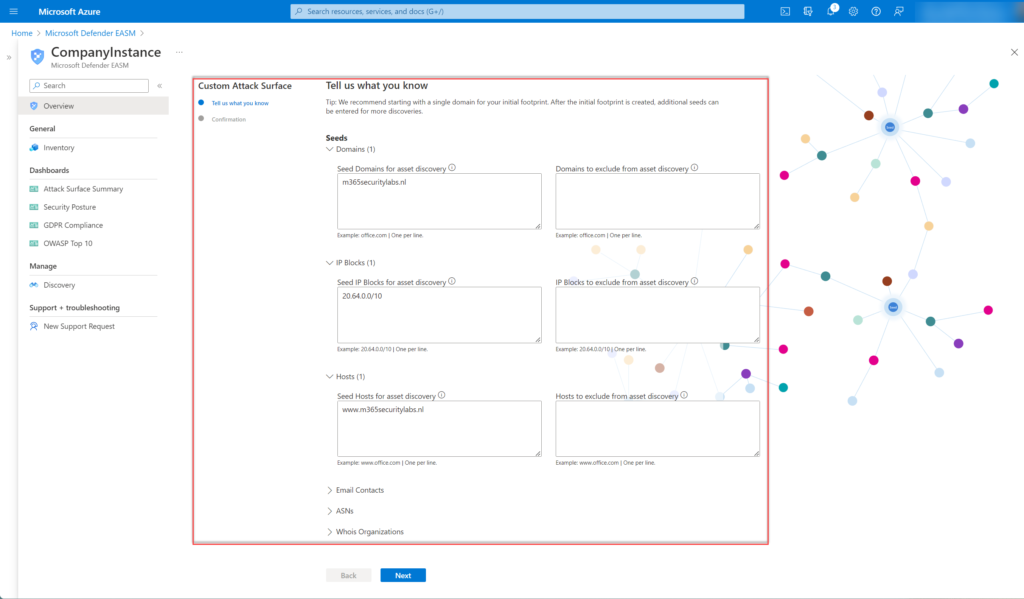
Click Next and confirm the custom Attack Surface configuration and configured seeds.
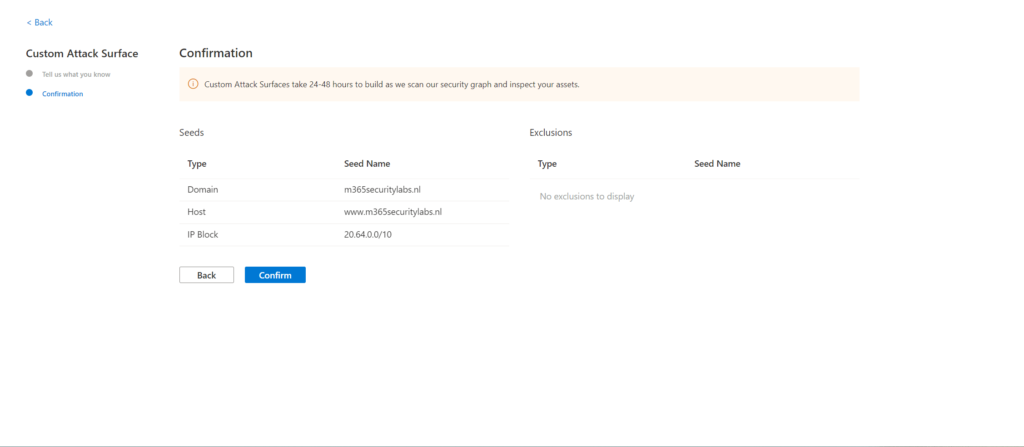
After the confirmation, it takes 24-48 hours before the attack surface profile is created. Microsoft scans the available security graph with the seed as input and creates associations based on the inventory and relations combined with other data (CVE, Threat insights, Asset types)
Discovery technology
The discovery technology searches recursively for connectors to known legitimate assets. Microsoft included externally facing assets that are exposed to the open internet outside of the traditional network components based on the following order;
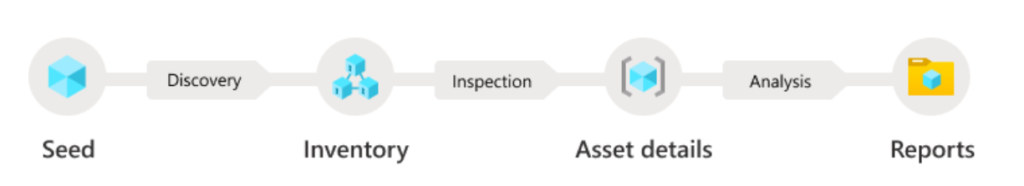
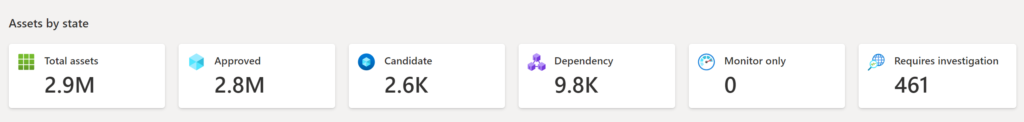
When the data is visible there are a couple of assets visible which are categorized in states. The following states are available: (Source: Microsoft)
| State name | Description |
|---|---|
| Approved Inventory | A part of your owned attack surface; an item that you are directly responsible for. |
| Dependency | Infrastructure that is owned by a third party but is part of your attack surface because it directly supports the operation of your owned assets. For example, you might depend on an IT provider to host your web content. While the domain, hostname, and pages would be part of your “Approved Inventory,” you may wish to treat the IP Address running the host as a “Dependency.” |
| Monitor Only | An asset that is relevant to your attack surface but is neither directly controlled nor a technical dependency. For example, independent franchisees or assets belonging to related companies might be labeled as “Monitor Only” rather than “Approved Inventory” to separate the groups for reporting purposes. |
| Candidate | An asset that has some relationship to your organization’s known seed assets but does not have a strong enough connection to immediately label it as “Approved Inventory.” These candidate assets must be manually reviewed to determine ownership. |
| Requires Investigation | A state similar to the “Candidate” states, but this value is applied to assets that require manual investigation to validate. This is determined based on our internally generated confidence scores that assess the strength of detected connections between assets. It does not indicate the infrastructure’s exact relationship to the organization as much as it denotes that this asset has been flagged as requiring additional review to determine how it should be categorized. |
Available data
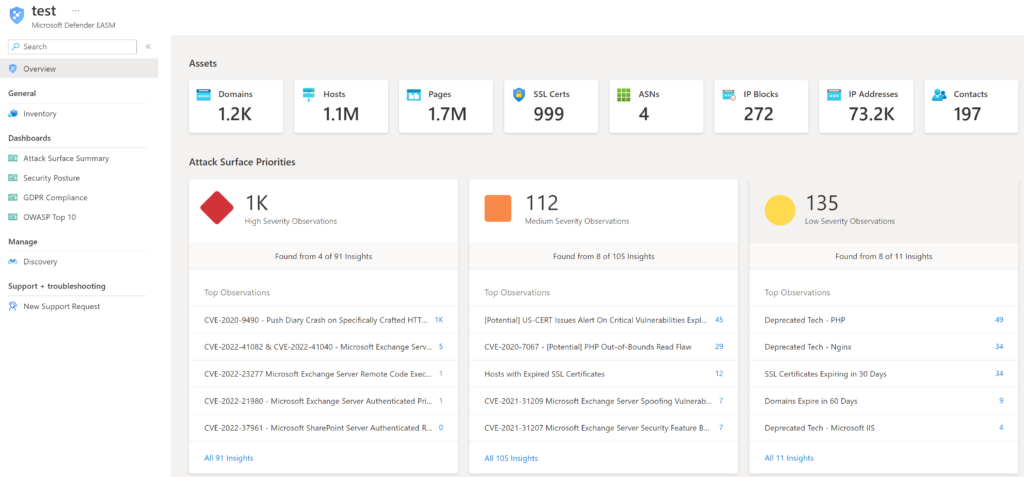
After some time the data is visible in the EASM resource instance. When data is loaded the overview page shows the count for each asset. EASM contains the following tabs:
- Overview: General dashboard with all information
- General – inventory: Overview of all discovered assets
- Dashboards: Pre-created dashboards
- Manage – Discovery: Configuration of the discovery profile
Overview
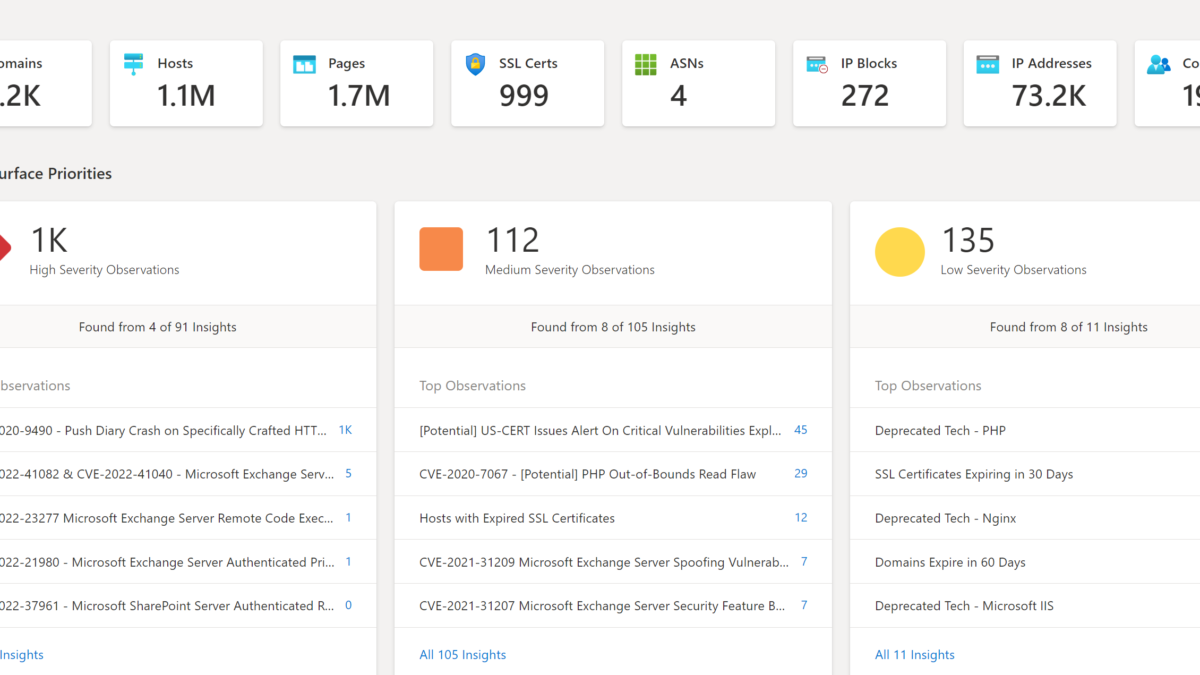
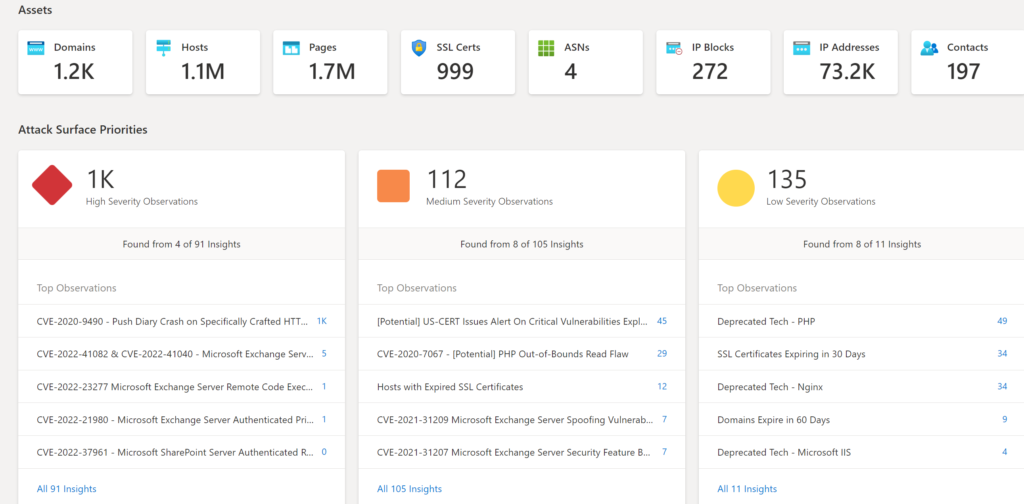
The Overview tab”provides additional insights and gives a quick insight into all available data; Assets, Attack Surface Priorities, Software Based CVSS distribution, and Assets by state:
Assets + Atack Surface Priorities: Shows Attack Surface Priorities for high-severity observations, medium observations, and low-security observations. Data is matched with publicly available CVE data. For example (CVE-2022-41082 & CVE-2022-41040). When clicking on the count the related assets are directly visible.
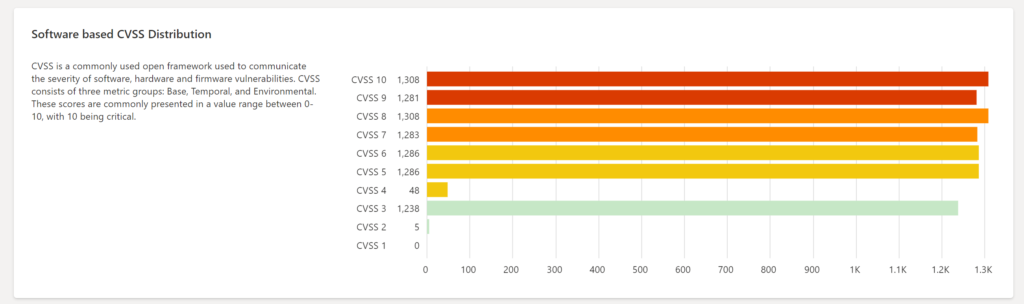
Software-based CVSS Distribution: Summary of the assets and CVSS distribution framework. The score is ranged between 0-10 where 10 is critical.
Assets by state: Asset breakdown in the available states.
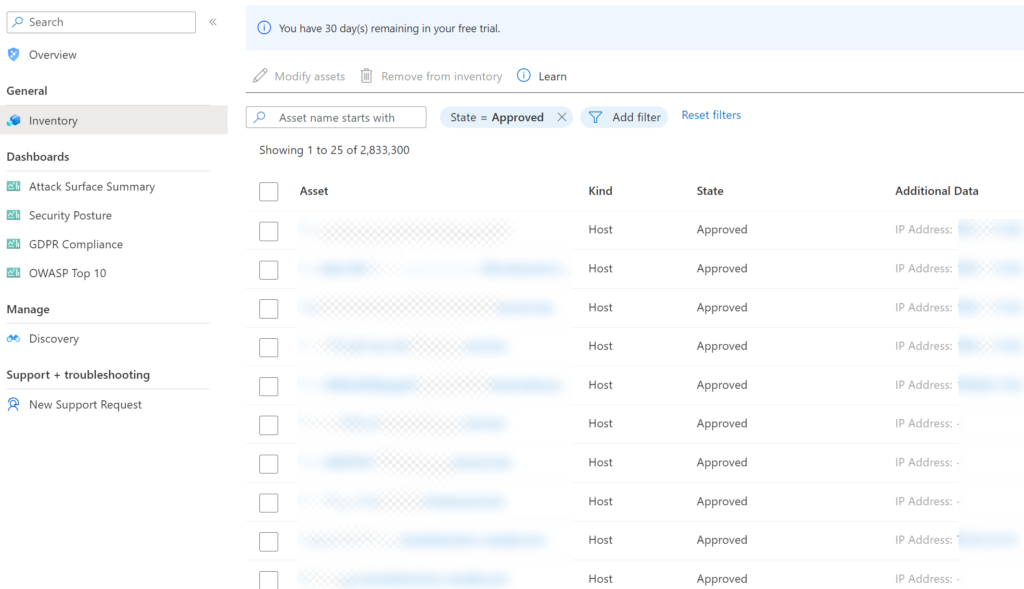
Inventory
The inventory page contains the full list of all discovered assets part of the configured seeds. Assets can be searched, removed, or modified (state).
Dashboards
Currently, there are 4 build-in reports available:
- Attack Surface Summary
- Security Posture
- GDPR Compliance
- OWASP Top 10
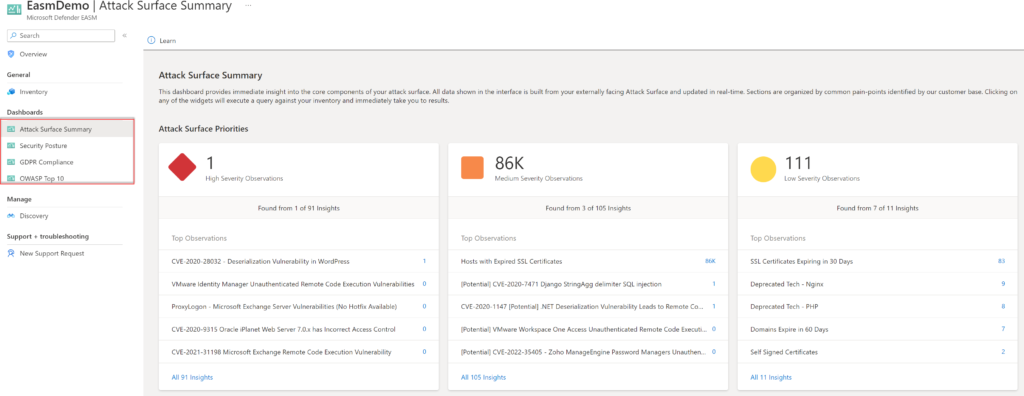
Attack Surface Summary
Attack Surface Summary provides a high-level overview of the Attack Surface-based on priorities/ composition, Cloud technology, Sensitive Services, SSL/ Domain expiration, and IP Reputation.
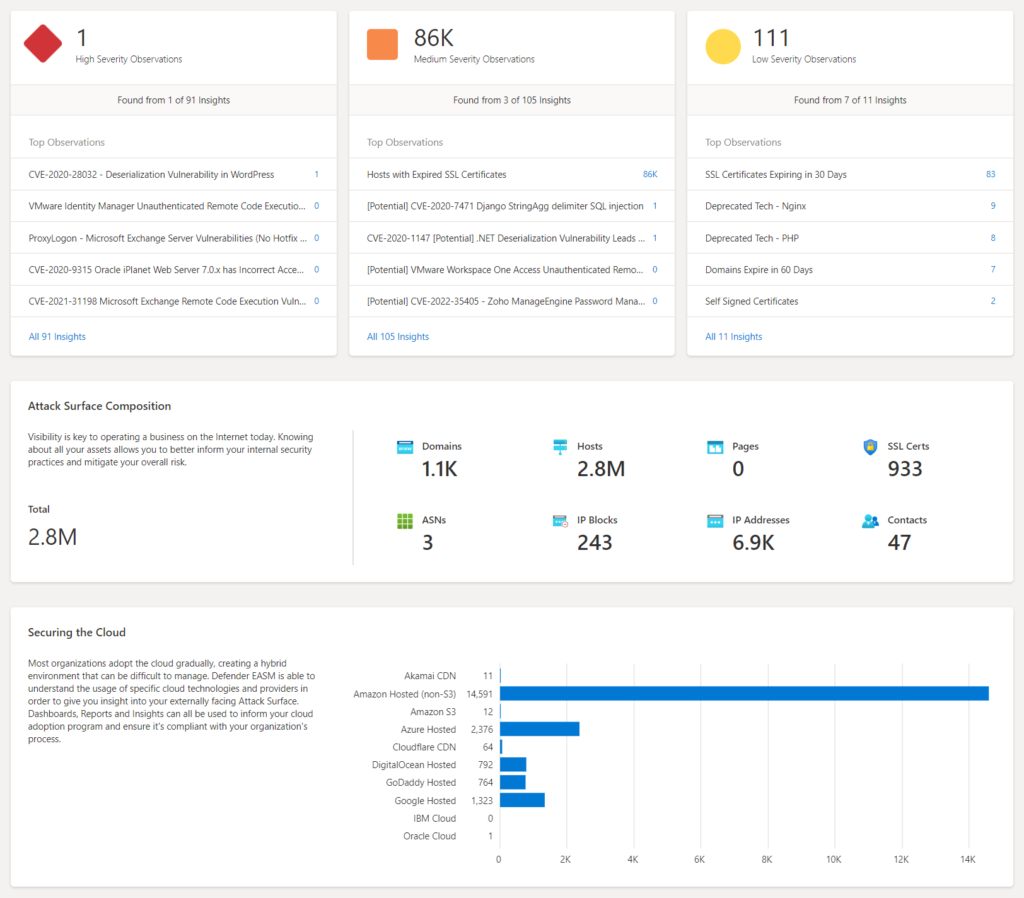
More information: Attack Surface Summary | Microsoft Docs
Security Posture
Based on metadata from discovered assets the posture is filled-in. This dashboard provides insight into CVE exposure, domain administration, and configuration, hosting and networking, open ports, and SSL certificate configuration.
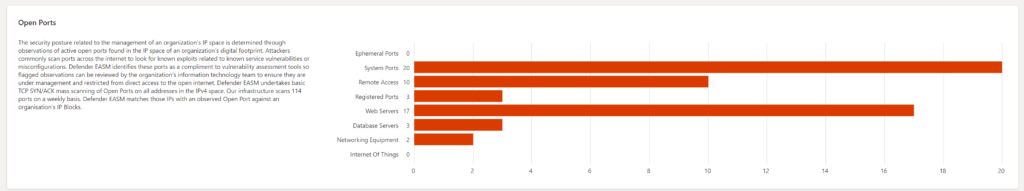
Interesting values are the domain configuration and Open Ports for each category (Ephemeral Ports, System Ports, Remote Access, Registered Ports, web Servers, Database Servers, Network Equipment, and Internet of Things).
SSL configurations contain the used certificate ( SHA1/ MD5 or expired)
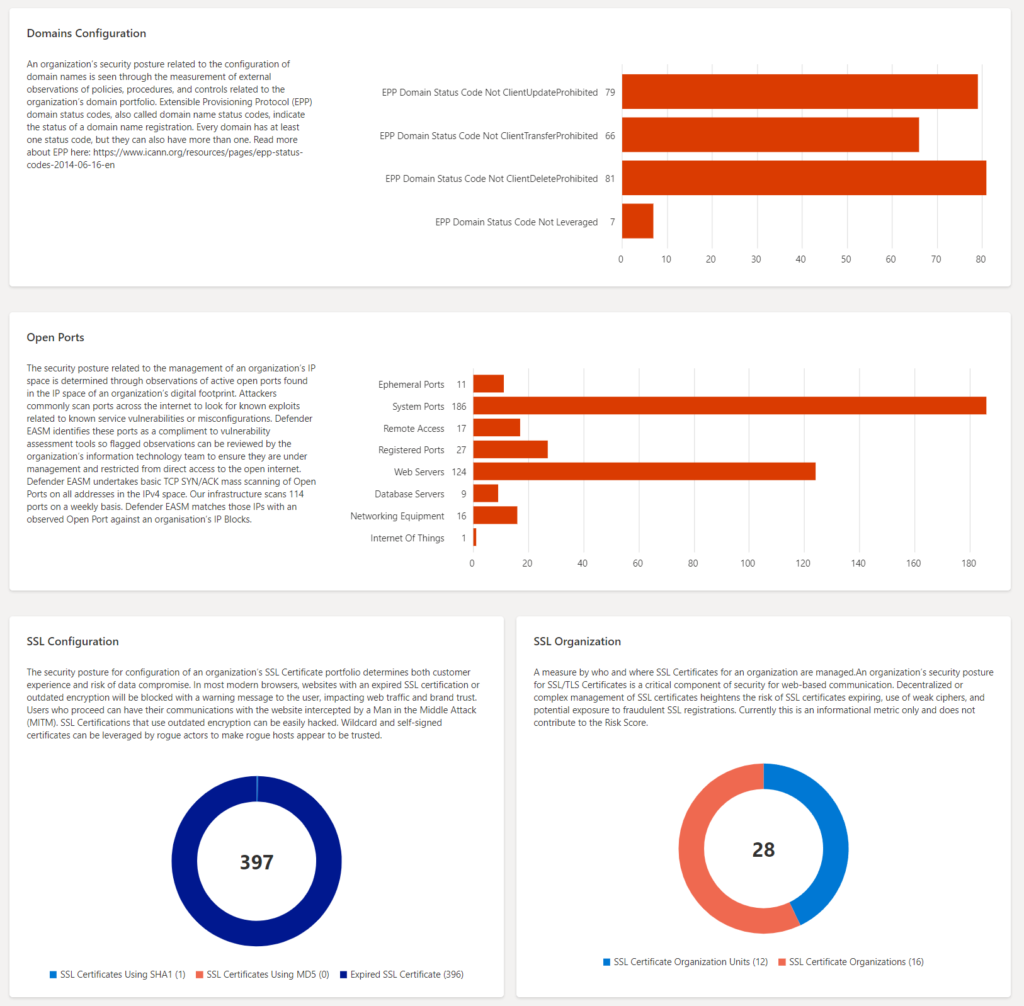
More information: Security Posture dashboard | Microsoft Docs
GDPR Compliance
The GDPR compliance dashboard presents an analysis of assets in the confirmed inventory against GDPR controls. Part of the dashboard;
- Website by status
- SSL Certificate Posture
- SSL Certificate Expiration
- Sites with SHA 1 / SHA256
- P11 Posture
- Login posture
- Cookie posture
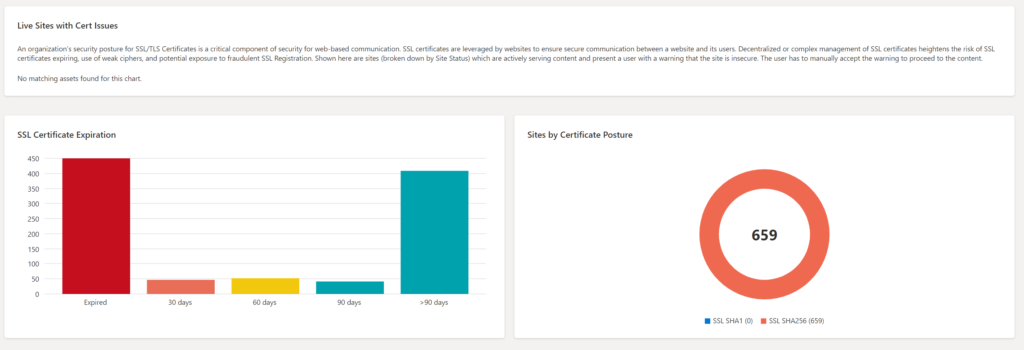
More information: GDPR compliance dashboard
OWASP Top 10
The OWASP Top 10 dashboard is designed to provide insight into the most critical security recommendations designated by OWASP for web application security. The dashboard contains the OWASP Top 10 including:
- Broken access control
- Cryptographic failure
- Injection
- Insecure design
- Security misconfiguration
- Vulnerable and outdated components
- Identification and authentication failures
- Software and data integrity failures
- Security logging and monitoring
- Server-side request forgery
The count and asset are clickable; for showing all assets. Click on the asset name for more in-depth information.
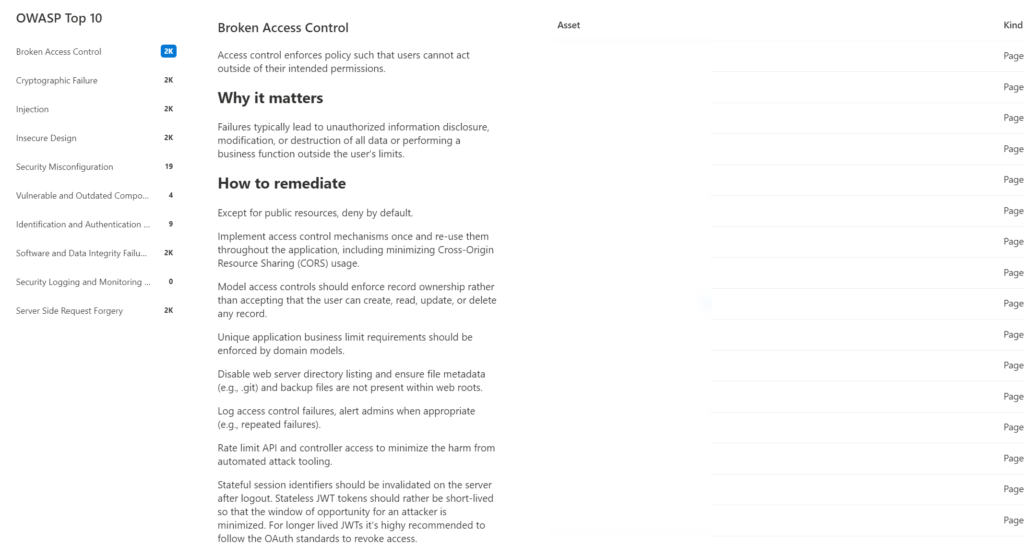
More information: OWASP top 10 dashboard | Microsoft Docs
Specific use-cases
Asset details
There is a huge amount of data available. Each asset contains in-depth details with global Security Graph information.
More information: Asset details | Microsoft Learn
CVE – Exchange
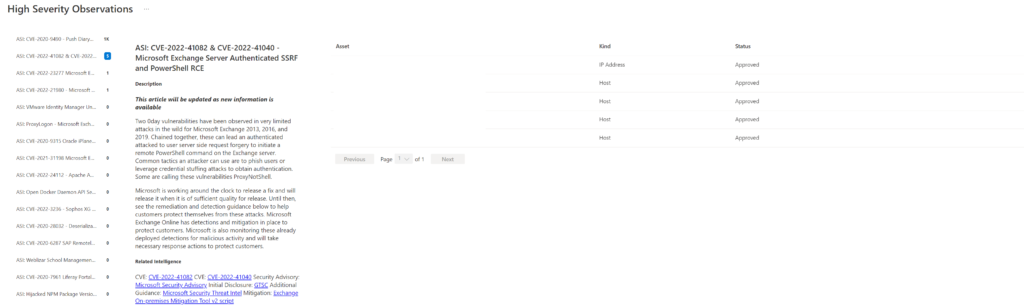
Data is mapped against CVE detecting. When viewing the Attack Surface Priorities, top observations are based on the seed discovery. For example; CVE-2022-41082 & CVE-2022-41040 – Microsoft Exchange Server.
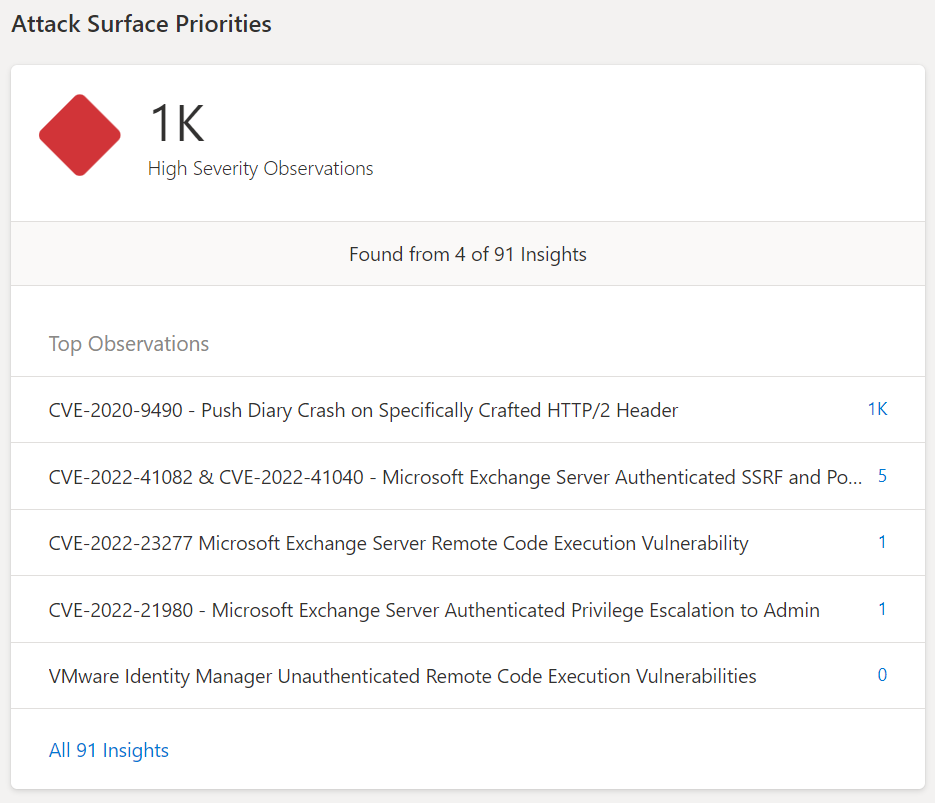
When clicking on the count – more in-depth information is visible. Microsoft described the CVE with more in-depth information and available remediation/ intelligence. Discovered assets are directly visible with the type.
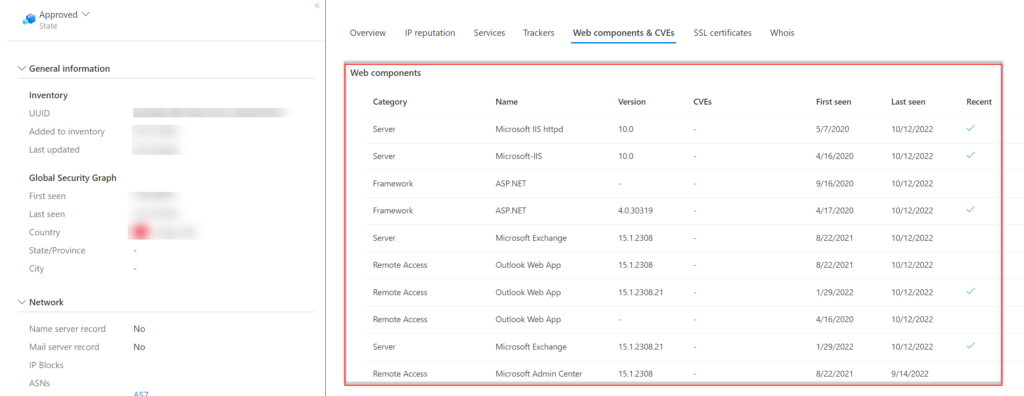
When clicking on the asset itself – there is more detailed information. (IP reputation, services, trackers, Web components/CVEs, SSL certificates, and host). Including specific versions. In the below example, we see exchange version 15.1.2308.
Open ports
In the Security Posture, there is a view of the open port part of discovered public resources.
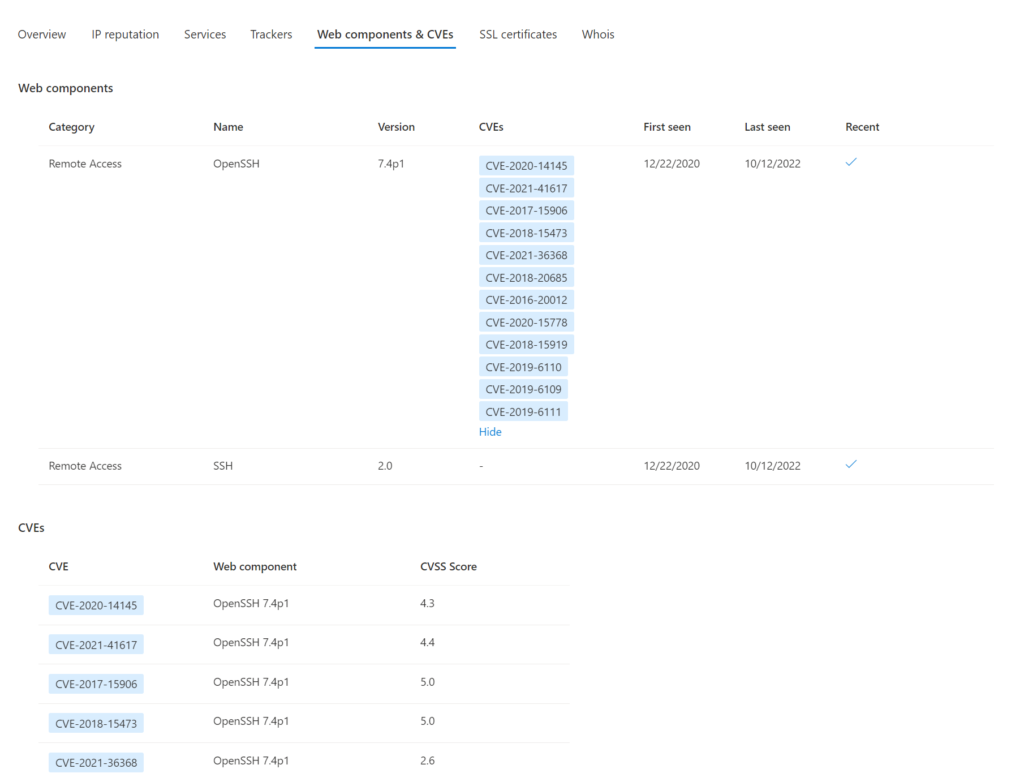
When clicking on the count the more detailed view is visible. Web components & CVEs give more visibility in the available CVEs/ first seen and installation version. In the example below the OpenSSH 7.4p1 (released; on 2016-12-19) is detected with a couple of CVEs. (-;
Conclusion
The new Microsoft Defender External Attack Surface Management tool is really interesting and can be used for various reasons to prevent the unknown and get more valuable insights into the online internet-exposed posture.
Currently, there are no integrations available – hopefully, more integrations will be released with Defender XDR and Sentinel for bringing the data together.
Sources
Community
- Derk van der Woude: Introduction into Microsoft Defender EASM (External Attack Surface Management)
- msandbu.org: Getting started with Microsoft Defender EASM (External Attack Surface Management)
Microsoft
- Microsoft: Defender EASM Overview
- Microsoft: What is Discovery