Microsoft released in the past months additional protections for Microsoft Teams. The new Office protection is part of the Defender for Office product and protects against more modern phishing methods via chat messages.
In the past years, phishing was mainly based on mail entities. There has been a huge increase in phishing via messaging apps like Microsoft Teams. Microsoft improved the detections, giving new prevention methods against malicious attempts/ messages via Microsoft Teams, and released new insights.
Why are collaboration tools more attacked?
Since the worldwide COVID pandemic, more and more companies are using collaboration tools and working remotely. Since more customers are using Microsoft Teams it is a good threat factor to send malicious messages. In the past months, multiple attacks were discovered by Microsoft Security researchers. Attackers are always evaluating new methods to abuse and send malicious messages. Since MFA is more and more enabled – attackers are switching to AiTM/ Teams messages to bypass current protections.
In the past months, Microsoft released a couple of new capabilities to detect and prevent malicious attacks via Microsoft Teams. It is all part of Defender for Office P2.
What are the new protections in Microsoft 365 Defender?
Microsoft Defender for Office 365 already provides time-of-click protection for URLs and files in Teams via Safe Links For Microsoft Teams and Safe Attachments for Sharepoint, OneDrive, and Microsoft Teams.
In addition to the above two protections Microsoft released the following capabilities based on the Defender for Office 365 technology:
- Report suspicious Teams messages
- Zero-hour auto protection (ZAP) for Teams
- Teams messages in quarantine
- Teams Message Entity Panel
- Attack Simulation training using Teams messages (private preview)
All features are part of Microsoft 365 Defender and are available when Microsoft 365 E5/ Office 365 Plan 2 is available.
Let’s explain the new futures more in-depth with technical explanation and configuration:
Report suspicious Teams messages
With this feature, users can report suspicious Teams messages. Admins / Security analysts can get visibility into the reported messages. Users can report messages in Teams from internal chats, channels, and meeting conversations. Users can only report messages as malicious. This feature is similar to what currently is available in Microsoft Outlook. All user submissions will also be compiled into an auto-generated investigation for suspicious URL clicks.

Zero-hour auto purge (ZAP) for Teams
Teams is a perfect channel for rapidly spreading malicious files/ content. For a faster response, the zero-hour auto purge (ZAP) can be used. This feature analyzes messages post-delivery and automatically quarantines messages that contain malicious files or content.
This feature is holistic – once a message is identified the entire Microsoft Teams environment will be scanned for the same evidence, and when needed all messages will be quarantined at scale for more protection.
Teams messages in quarantine
Teams messages are now having a quarantine based on ZAP. This allows the admins to control high-confidence phishing via the quarantine. Messages will be blocked for the user.
Teams Message Entity Panel
The new Teams Message Entity Panel is a new place where all metadata is stored for SecOps purposes. Any threat coming from chats/ meetings chats/ groups chats can be viewed from one single page in Microsoft 365 Defender.
Attack Simulation training using Teams messages
Attack Simulation training is a feature where simulation phishing attacks can be sent to the organization. With the new improvements, sending simulation messages via Microsoft Teams to train and adopt awareness across Teams phishing is possible.
Configure Zero-hour auto protection (ZAP)
Configuration
ZAP is available for Microsoft 365 E5 customers or Microsoft Defender for Office 365 P2 subscriptions. For ZAP it is needed to configure the protection in the Microsoft Defender portal.
For enabling ZAP; Go to Microsoft 365 Defender > Settings > Email & collaboration > Microsoft Teams protection
Validate of the Zero-hour auto purge (ZAP) settings is configured with the value On.

After August 22, 2023, ZAP for Teams protection is turned on by default. As additional validation, it is possible to confirm the ZAP protection via the Exchange Online PowerShell cmdlet:
Get-TeamsProtectionPolicy | Format-List ZapEnabledScope ZAP
Currently, ZAP for Teams is not protecting in all situations and is supported for the following Teams activities:
✅ = ZAP supported ❌ = ZAP not supported
| Teams situation | Message route | ZAP protection |
|---|---|---|
| Standard channels | Internal messages | ✅ |
| Standard channels | External messages | ❌ |
| Shared channels | Internal messages | ✅ |
| Shared channels | External messages | ✅ |
| Private channels | All | ❌ |
Important: ZAP is available for internal messages in Teams chats identified as malware or high-confidence phishing. Currently, external messages are not supported by the ZAP feature in Microsoft Teams.
Since Teams is different than e-mail (Teams message copy is delivered to everyone in a Teams chat). The message is blocked for everyone in the chat.
Important: ZAP for Teams protection can take action on messages for all recipients in a chat if any recipients in the chat aren’t excluded from ZAP for Teams protection. This means when a recipient is excluded from ZAP and is part of a group chat the message will be blocked via ZAP.
Report suspicious Microsoft Teams messages
With the recently announced reporting functionality, it is possible to report suspicious messages directly in Teams. The security team will be alerted whenever users report suspicious messages and all details are directly visible in the Microsoft 365 Defender portal.
When the user submits Microsoft Teams messages the auto-generated investigation will start to report the suspicious URL clicks.
Configuration
User reporting of messages in Teams needs to be enabled via two separate settings in Microsoft 365 Defender and Teams admin center.
Microsoft 365 Defender
Go to Microsoft 365 Defender > Settings > Email & collaboration > User-reported settings and configure the user-reported settings. Make sure “Monitor reported messages in Microsoft” is enabled.

The page shows some customization/ branding options. Important is the reported message destinations. The following locations are available for sending reported messages:
- Microsoft only
- My reporting mailbox only
- Microsoft and my reporting mailbox
When selecting Microsoft the reported message will be sent automatically to Microsoft for getting automated investigation or manual investigation to improve the detection accuracy.

Teams admin center
The setting in the Teams admin center is enabled by default. This setting controls whether users can report messages from Teams. When this setting is turned off, users can’t report messages within Teams. When the setting is disabled in the Teams admin center the Microsoft 365 Defender setting will not affect, since the feature is disabled. The setting is available via the Messaging policies. Use https://admin.teams.microsoft.com/policies/messaging for the direct policies page.
Enable the setting: “Report a security concern” to On

When both settings are configured the security concern/ suspicious teams message feature is enabled. Personally, there is one big downside of this feature; following Microsoft docs users can only report messages from internal chats/ channels and meeting conversations. Currently, there is no option to report messages from external chats. Personally; I see the real benefit of the reporting feature mostly for the external messages; since spam/ malicious teams messages will be mostly sent via external accounts and not internal chats. Hopefully, Microsoft will improve this in the future and support external messages as well.
How works the flow?
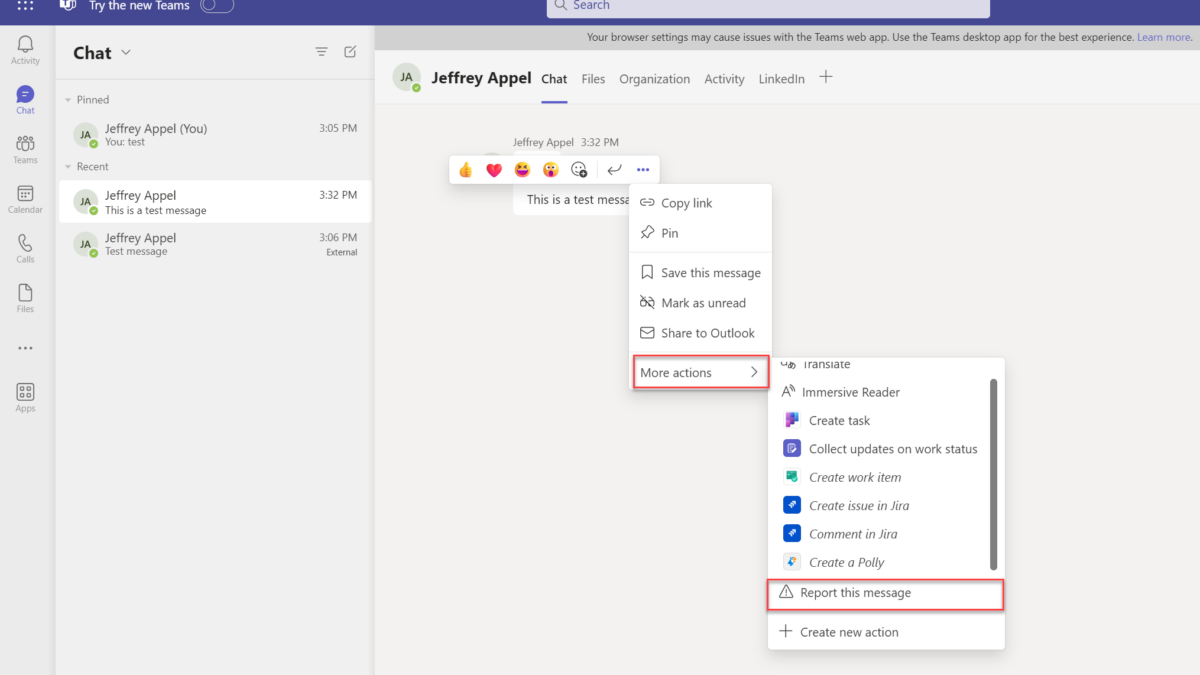
The user can report internal messages in Microsoft Teams via the actions. More options > More actions > Report this message.

The dialog shows the category, the user can select the Security risk – Spam, phishing, or malicious content category. When Purview Communication Compliance is turned off; the dropdown is sometimes not visible.

Now there is something good to know after the user submits the message:
- When the message is reported – the Microsoft Teams message remains visible to the user in the Teams client and can report the messages multiple times.
- The message sender isn’t notified that messages were reported in Microsoft Teams.
- Microsoft sends an email notification to the user who reported the message from submissions@messaging.microsoft.com with the subject, “You have successfully reported a Teams message as a security risk.
Microsoft Teams messages in quarantine
The quarantine experience is available for customers with the Defender for Office 365 Plan 2 product (included in Microsoft 365 E5 or other subscriptions). With the use of zero-hour auto purge, there is an automatic remediation flow that removes the Teams message and quarantines the chat. Similar to the Email experience.
The Teams messages in quarantine experience are available in the Microsoft Defender portal and visible via the Email & collaboration > Review > Quarantine > Teams messages tab.

See: Manage quarantined messages and files as an admin for more information scoped to the admin quarantine feature.
Soon I will publish some new blogs around specific features related to Microsoft Teams protection in combination with modern attacks.
Sources
Microsoft: Microsoft Defender for Office 365 Plan 2 support for Microsoft Teams
Microsoft: New Microsoft Teams Protection | Virtual Ninja Training w/ Heike Ritter