Microsoft Defender for Endpoint is an endpoint security platform designed to help customers prevent, detect, investigate, and respond to advanced threats. Microsoft Defender for Endpoint contains many components, licensing differences, and additional protection. Some years ago Defender for Endpoint was only available for Windows. Nowadays the complete Defender for Endpoint stack contains; macOS, Android, iOS, Linux, and Windows. Unmanaged network devices are now also part of the product. With the announcement of the new unified agent more features are available across all versions including Server 2012R2, Server 2016, and higher.
Introduction blog series
This ultimate blog series will contain as much information as possible based on my Defender experience in the past years. Not a copy of Microsoft Docs, but an addition based on practical experience combined with informational details – including the most frequent questions asked by customers focussing on the complete Windows platform. When it’s a success, other platforms like iOS, Android, Linux, and macOS will follow,
Specific question or content idea part of Defender for Endpoint? Use the contact submission form and share the post ideas.
Introduction Defender for Endpoint
Microsoft Defender for Endpoint is an enterprise platform focussing on preventing, detecting, investigating, and responding to threats.
It leverages endpoint behavioral sensors that are built into Windows 10, Windows 11, and Server 2019+ to collect and process behavioral signals from the OS. For other OS versions, all the technical information will be explained in the blog series.
Defender for Endpoint also leverages cloud security analytics to turn behavioral signals into insights, detections, and responses.
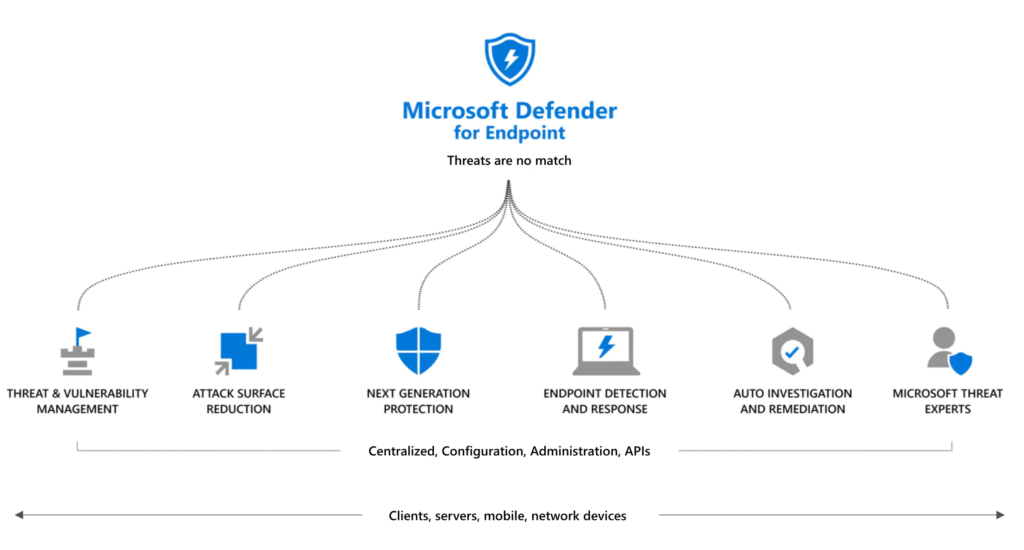
Defender products
Microsoft Defender for Endpoint is available in two purchase options. P1 is the foundation set of capabilities focussing on the prevention area. Microsoft Defender for Endpoint P2 offers a complete set of capabilities, including endpoint detection and response (EDR), Automation investigation (AIR), Incident Response, and Threat and Vulnerability Management (TVM). Compare Defender for Endpoint Plans | Microsoft Docs
Microsoft Defender for Endpoint is part of the Microsoft 365 Defender suite of products and shares a lot of its infrastructure, data schemas, and user experience. More detailed information will be explained in the first part.
Defender for Endpoint directly integrates with various Microsoft solutions, including:
- Microsoft Defender for Cloud
- Microsoft Sentinel
- Intune/ Microsoft Endpoint Manager
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Identity
- Microsoft Defender for Office
- And more….
Defender for Endpoint and related component
Microsoft Defender for Endpoint is part of the Microsoft 365 Defender suite of products. Defender for Endpoint contains a couple of major components including;
- Asset discovery
- Threat & Vulnerability Management (TVM)
- Attack Surface Reduction (ASR)
- Next-Generation Protection (NGP)
- Endpoint Detection & Response (EDR)
- Automated Self-healing/ Automation investigation and remediation (AIR)
- Microsoft Threat Experts
Part of Defender for Endpoint are many components that can be used for expanding the complete security posture. Next-generation protection and Attack Surface reduction are getting more critical in protecting against current and future threats.
- Microsoft Defender Antivirus / Next-generation protection
- Microsoft Defender SmartScreen
- Attack Surface Reduction
- HW-based isolationExploit protectionNetwork protectionControlled folder accessDevice controlWeb protectionRansomware protection
- Attack Surface Reduction rules
- Application control
- Windows Defender Credential Guard
- Tamper Protection
- Microsoft Defender for Endpoint
- And more….
More information: Part 1: What is Defender for Endpoint and how works the product?
Parts of the MDE blog series
View all the published parts of the MDE blog series:
- Part 0: Microsoft Defender for Endpoint – The ultimate blog series (Intro)
- Part 1: What is Defender for Endpoint and how works the product?
- Part 2: Configuring Defender for Endpoint Portal
- Part 3: Onboarding methods
- Part 3A: Onboard using MEM
- Part 3B: Onboarding using Defender for Cloud
- part 3C: Onboard using Azure Arc
- Part 3D: Onboard using MECM/ GPO
- Part 4: Configuration of Defender for Endpoint/ NGP/ AV
- part 4A: Define the AV policy baseline
- Part 4B: Attack Surface reduction and additional protection
- Part 5: Threat Vulnerability Management
- Part 6: Troubleshooting and reporting
- Part 7: Integrations with other “Microsoft” products
- Part 8: Advanced hunting and custom detections
- Part 9: Automation via Logic Apps and Sentinel
- Part 10: Tips and tricks/ common mistakes
Other platforms:
Contribute
Is there something missing? Use the contact submission form and share the post ideas or contact using Linkedin or Twitter. I will take all suggestions into the Defender for Endpoint series and help the community as far as possible.





Thank Jeffrey, for sharing great contents of MDE. Can you share MDE configuration from GPO and from MDE security setting management with MEM?
Good to hear.
MDE security management with MEM: https://jeffreyappel.nl/managing-microsoft-defender-for-endpoint-with-the-new-security-management-feature-in-mem/
Hi Jeffrey,
I was a bit puzzled on how Intune / Defender for Endpoint and the other products interacted but after going through your blog series really learned a lot ! Thanks, amazing overview !