Microsoft recently added a new function that gives the option for stream events from Azure AD Identity Protection into Microsoft Sentinel. In this blog the instruction for export user risk events from Azure AD Identity protection into Microsoft Sentinel.
Identity Protection – Risk data
Risk data is part of Azure AD Identity protection and stores the data with some small retention period. With the new stream option – it is possible to extend the default retention period and create use-cases based on more data.
Azure AD stores reports and security signals for a defined period. Below is the table with the max retention period for AzureAD free, AADP1, and AADP2 for each of the signals. With AADP2 the max retention period is 30 days for the audit logs, sign-ins, risky sign-ins, and AzureAD MFA usage.
| Report / Signal | Azure AD Free | Azure AD Premium P1 | Azure AD Premium P2 |
|---|---|---|---|
| Audit logs | 7 days | 30 days | 30 days |
| Sign-ins | 7 days | 30 days | 30 days |
| Azure AD MFA usage | 30 days | 30 days | 30 days |
| Risky sign-ins | 7 days | 30 days | 90 days |
For several years Azure AD Identity Protection is available with the Azure AD P2 license. Azure AD Identity Protection gives the following key tasks for organizations:
- Automate detection and remediation for identity risk events
- Investigate risk
- Protect users automatically based on risk
Identity Protection uses the threat intelligence information from AzureAD and all the threat intelligence information from customers worldwide. Based on the analyzed events Microsoft protects users from threats.
Two main risk detection components are part of the Azure AD Identity Protection solution:
- Sign-in risk
- User-risk
More technical Azure AD Identity Protection information in this blog: Azure AD Identity Protection: User Risk and Sign-in Risk protection with automation
Stream events with Diagnostic settings
From the Diagnostic settings panel, it is possible to stream risk events from Azure AD Identity protection into Microsoft Sentinel/ Log Analytics based on two new tables. After the enablement the following tables will be created:
- AADUserRiskEvents
- AADRiskyUsers
Enable the event streaming
For sending the RiskyUser and UserRiskEvents data to a Log Analytics workspace, storage account or Event hub go to the Azure Active Directory diagnostic setting:
Azure portal > Azure Active Directory, Diagnostic settings
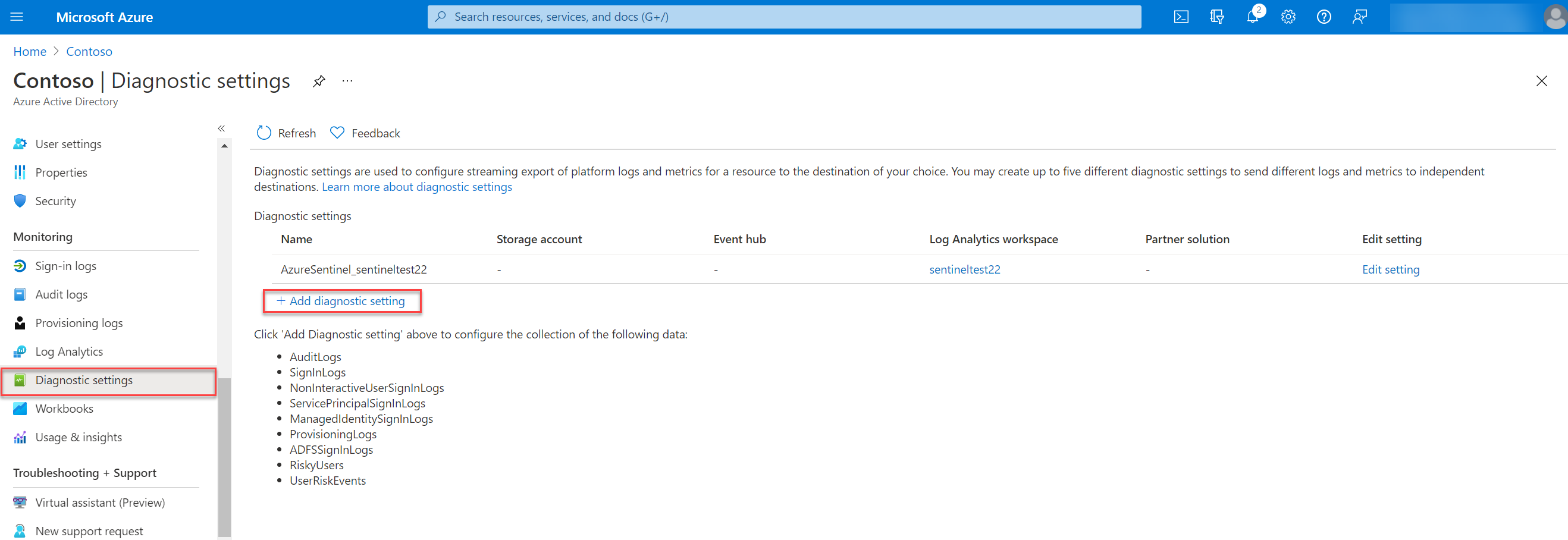
For the event destination 4 options are available:
- Send to Log Analytics workspace
- Archive to a storage account
- Stream to an event hub
- Send to partner solution
For adding the new diagnostic settings source click on Add diagnostic settings

The next step is to fill in the diagnostic settings name and select the category details and destination details. First the category details:
Log category details
With this blog, we focussing only on the risk events from Identity Protection. For streaming the Identity Protection data select RiskyUsers and UserRiskEvents.
Destination details
For exporting events into Microsoft Sentinel. We using in this blog the export option Send to Log Analytics workspace. For sending events into the Microsoft Sentinel workspace – select the subscription and workspace.
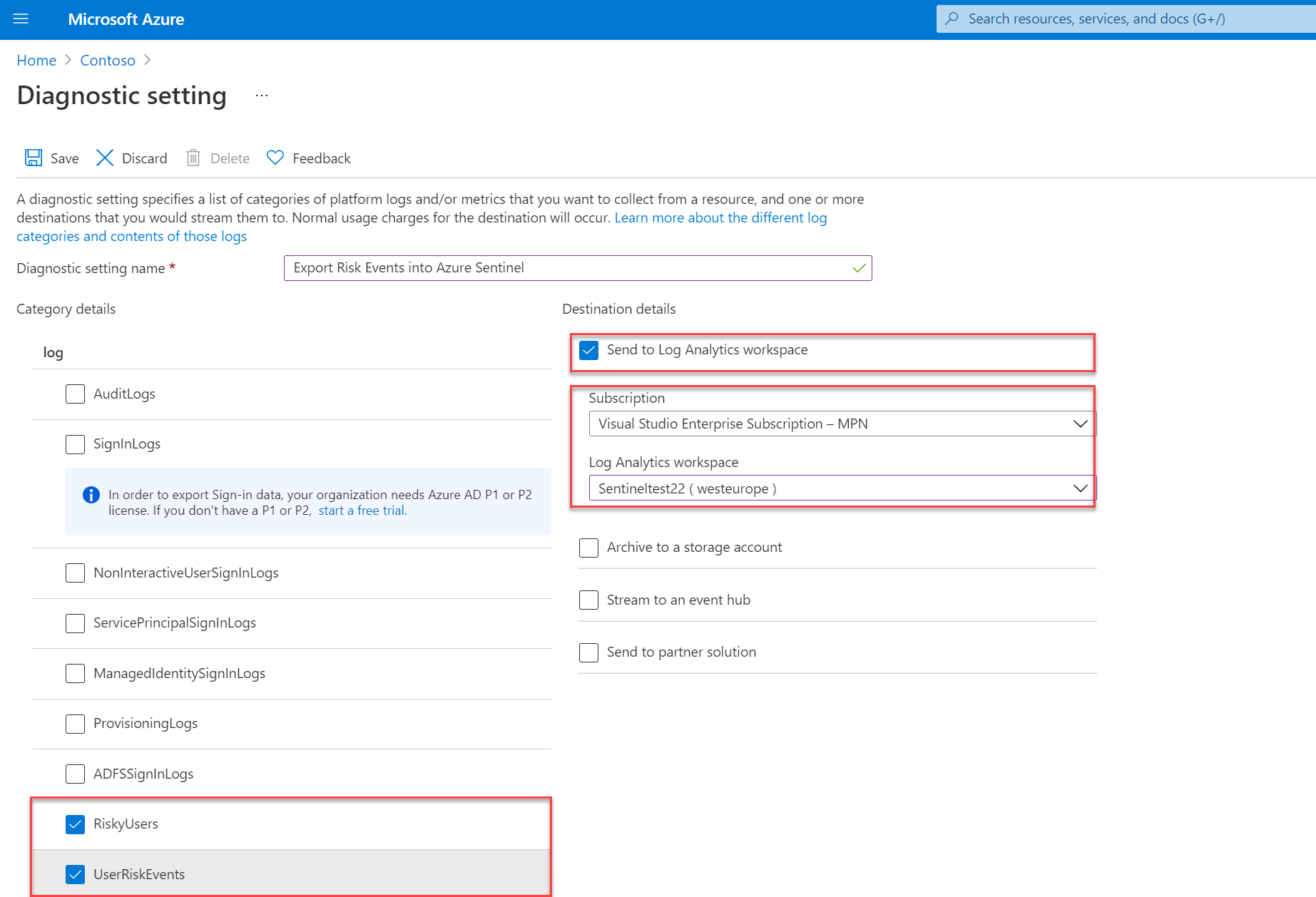
Once enabled two new data tables are available in the Log Analytics workspace. Based on the RiskyUsers and UserRiskEvents log the following tables are available:
- AADRiskyUsers – Provides data like the Risky users report in Identity Protection
- AADUserRiskEvents – Provides data like the Risk detections report in Identity Protection
Investigate data with KQL
Based on the data flow KQL can be used for more in-depth investigation and for matching data against other log sources. ( example the AzureAD sign-in information)
AADUserRiskEvents
AADUserRiskEvents contains the risk user events from Identity Protection and Microsoft Cloud App Security. Interesting to view quite easily the detection logic from Identity Protection. With the DetectionTimingType the real-time or offline attribute is visible. See the Microsoft docs for the table reference.
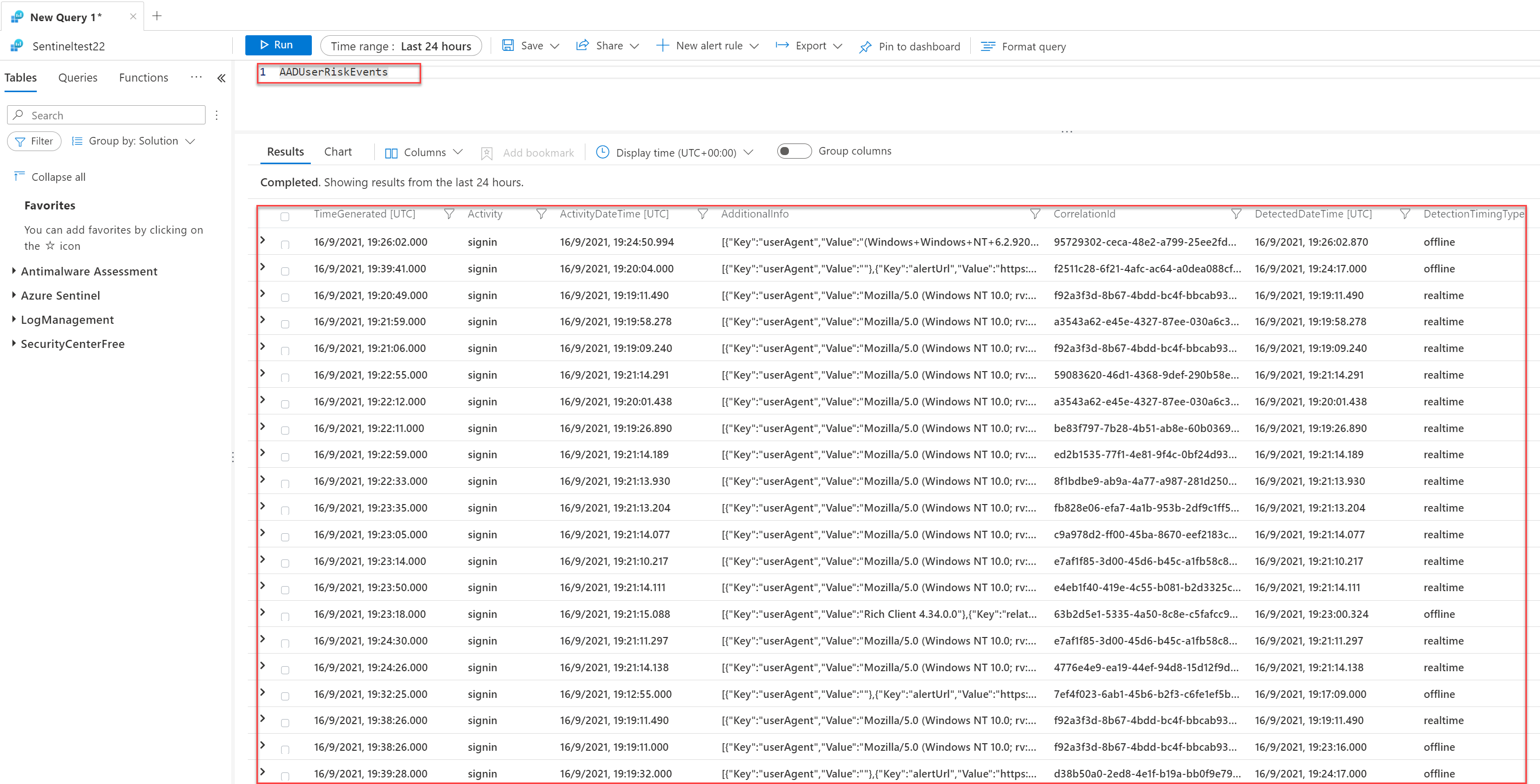
Information like RiskDetail, RiskEventType, RiskLevel, RiskState DetectionTimeType, TokenIssuerType, and source is available from the AADUserRiskEvents table.
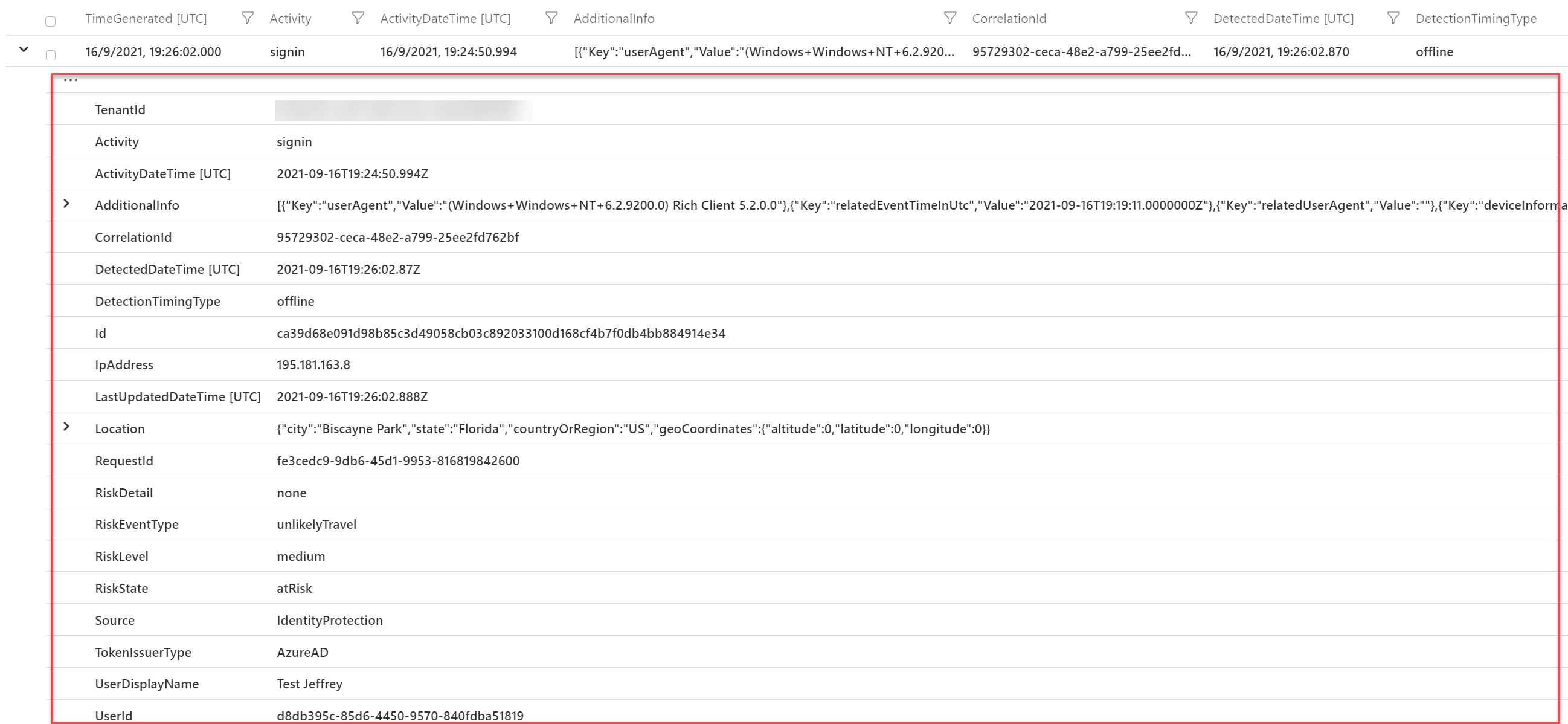
RiskDetail with the value aiConfirmedSigninSafe is interesting. This is basically Microsoft flagging the risk event as safe based on the AI and Identity protection events. The exact reason why it is safe is not available. It seems some combination of user events, IP Address history, location, and common sign-ins from other users.
DetectionTimingTypes: Sign-in risk can be calculated in real-time or calculated offline using Microsoft’s Internal and internal threat intelligence feeds. With the field; DetectionTimingTypes the calculation real-time/ offline is visible. For some examples of TimingTypes: Read my other AAD Identity Protection blog.
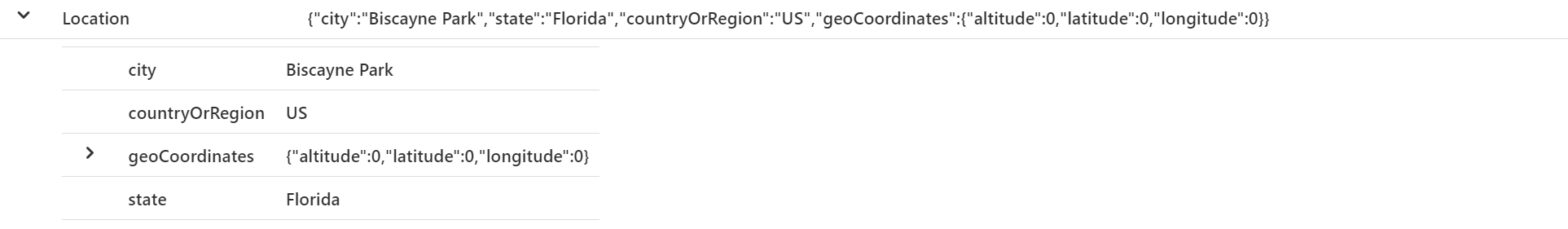
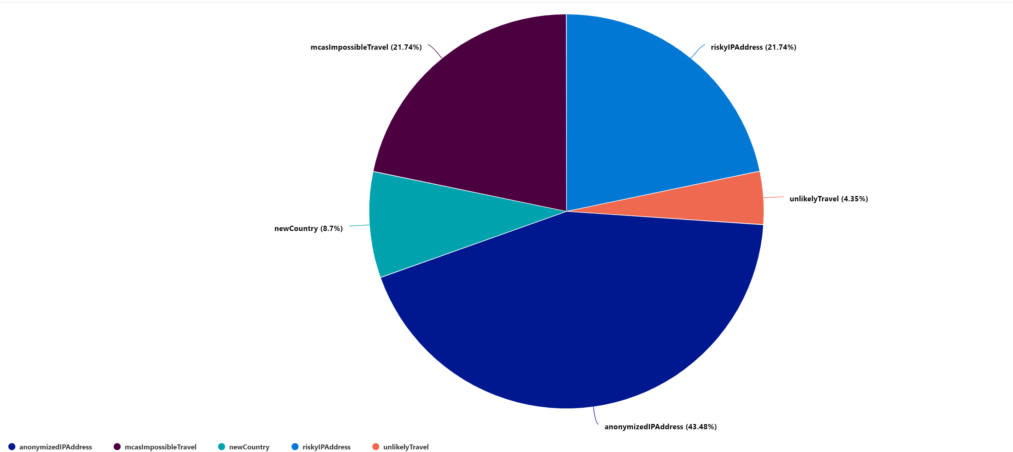
With the RiskEventType you can track the specific type for the risk. Location contains the specific location details with specific geoCoordinates.
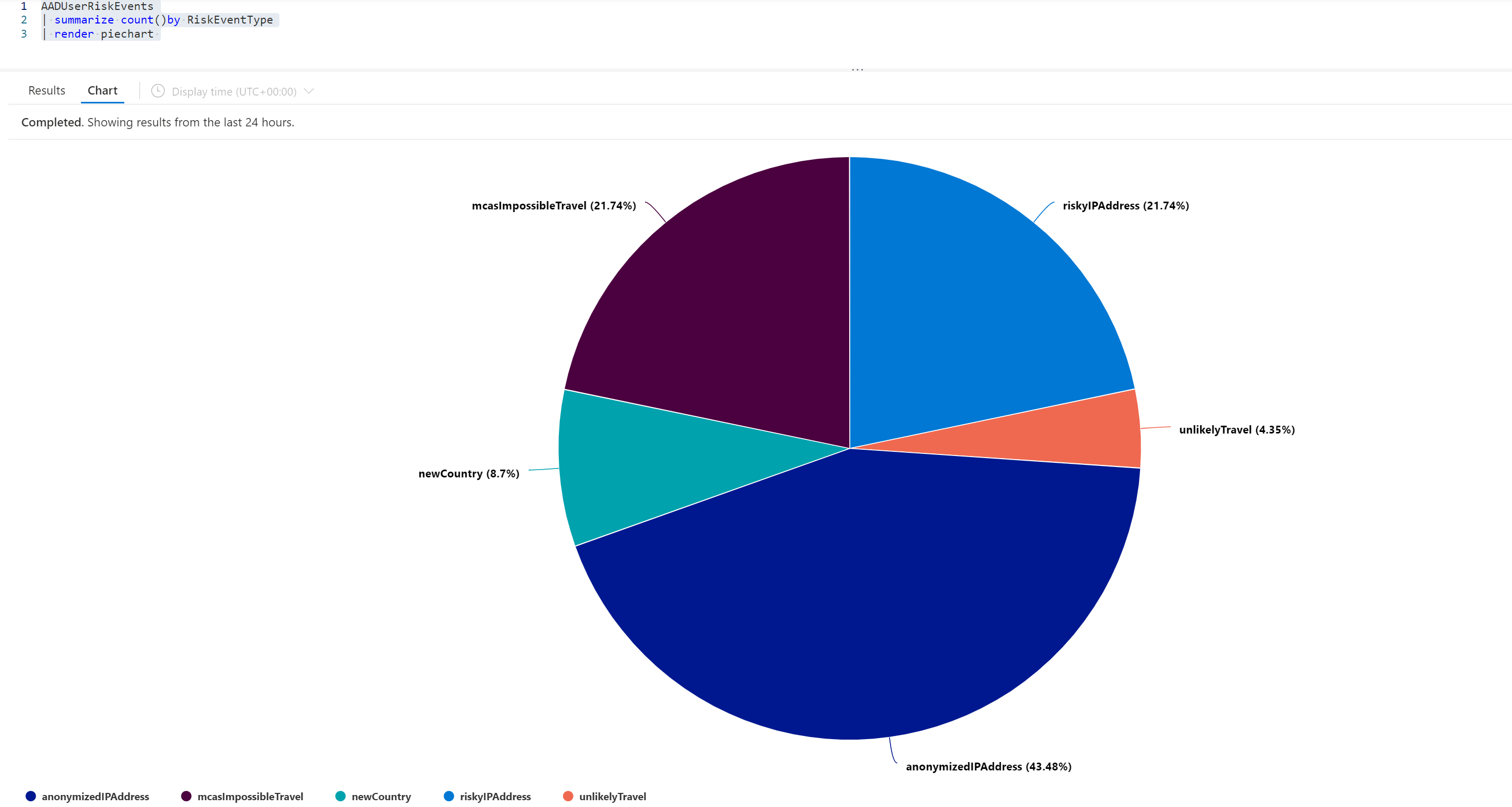
With the KQL query:
AADUserRiskEvents
| summarize count()by RiskEventType
| render piechartYou can visualize the data based on RiskEventType.
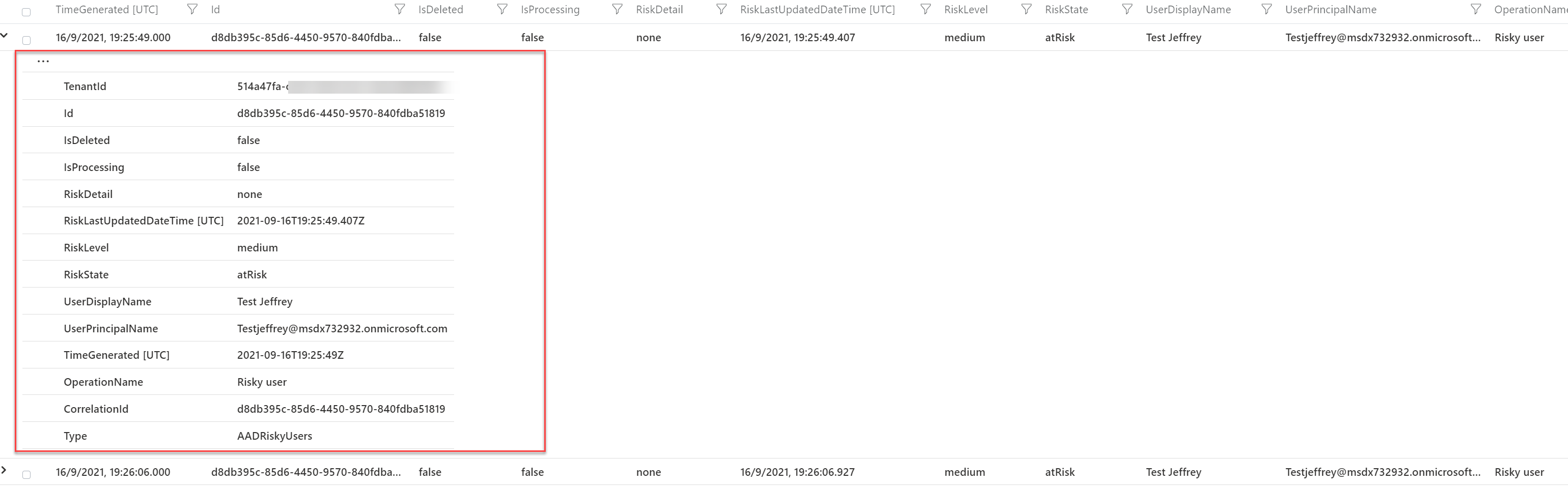
AADRiskyUsers
AADRiskyUsers table shows the state of a user and how their risk has changed. You can combine AADUserRiskEvents and AADRiskyUsers to view the changing pattern.
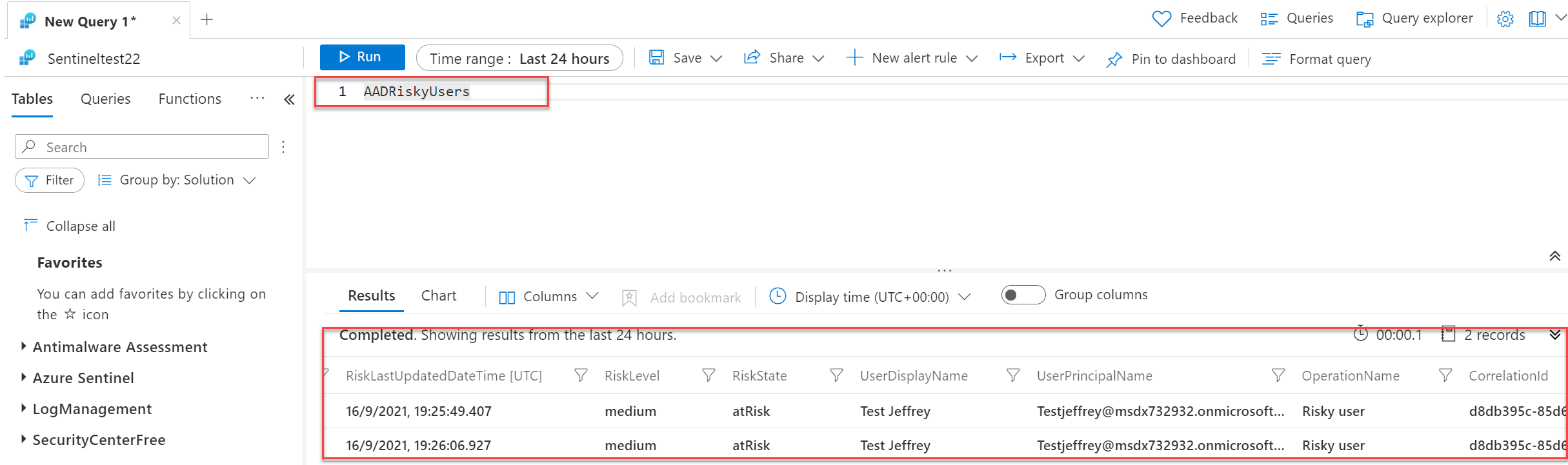
Information available:
- IsDeleted
- IsProcessing
- RiskDetails
- RiskLastUpdateDateTIme
- RiskLevel
- RiskState
- UserDIsplayName
- UserPrincipalName
- OperationName
- Type
Tip: For more KQL examples with the new risk events – view the blog; learnsentinel.blog
Conclusion
In this blog, I have covered how you can collect Azure AD Risk Events from Identity Protection and stream them directly to Microsoft Sentinel/ Log Analytics.
With the new data tables, multiple use cases are possible for filtering the real-time risk and available attributes.
Sources
Microsoft: How To: Export risk data
Learnsentinel.blog: Streaming Azure AD risk events to Azure Sentinel




Thank you for sharing. I found this informative and helpful. Since Azure AD Identity Protection/SecurityAlert (IPC) and Microsoft Defender for Cloud Apps/SecurityAlert (Defender for Cloud Apps) are listed as FREE data sources for a Sentinel Log Analytics workspace, there should be no additional costs to incur.