A Password Spraying Attack is a type of brute force attack where a malicious actor attempts the same password on many accounts before moving on to another one and repeating the process. In this blog the explanation of detection and protection against password spray attacks.
Three steps are needed for running a password spray attack:
Three steps are needed for a successful password spray attack
Step 1: It all starts with a list of accounts and e-mails. With all the cloud-based toolings and leaks not too hard to complete in some hours. Most organizations have a formal convention for the e-mail address, for example: firstname.lastname@companyname.com. Based on social media channels and for example LinkedIn easy to generate account names. And of course, there is a lot of data available from hacks which are containing e-mail information.
Step 2: Spray the passwords is the next step. Not too hard to find some passwords on the public web. From the internet each year there are multiple lists available with the top-used password. 123456, password and qwerty is still one of the most used passwords. ( always good to not using this type of password or use password-less.) Of course hackers will use the dark web for more password information. With a Password spray attack hackers will deploy often-used passwords to multiple users during some time behind each sign-in ( to give the insights based on a normal sign-in)
Step 3: The goal is to complete the access with one of the passwords for one of the accounts. For attackers one successful password+username is enough to complete most of the time internal reconnaissance on the target network and go deeper into the systems via elevation pf privilege.
Important is the way of protection against password spray attacks. In this blog the explanation of the following protection features:
- Azure AD Password Protection
- Azure AD Identity Protection
- Azure Sentinel insights
Run the password spray
It is quite simple to create an input.txt file with the usernames from any public leak or social site. When you known the format you can easily fill in most of the e-mails. Multiple Python scripts are available for validating email accounts against AzureAD. With the result only Office365 accounts.
Now use one of the Password Spray PowerShell scripts or any other toolings to run a Password Spray attack. In case of no matching password:
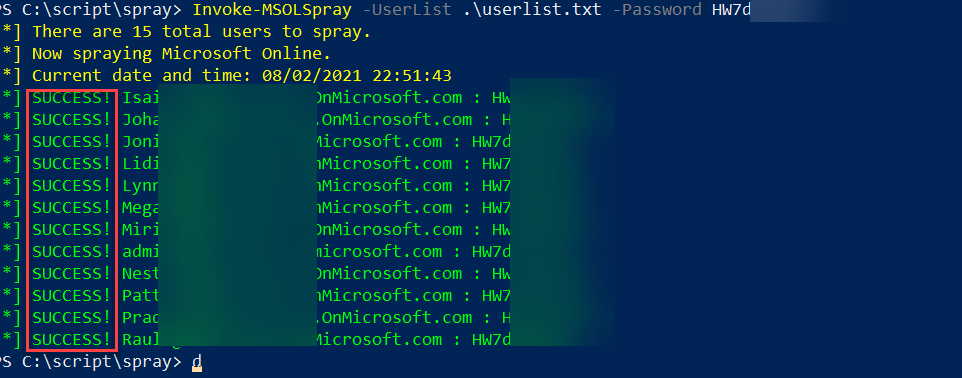
Bingo! Password matching
When you have access without MFA. Quite easy to view the other AzureAD information with some AzureAD framework tools.
Most common events for Password spraying:
| Error Code | 50126 |
| Message | Error validating credentials due to invalid username or password. |
| Remediation | The user didn’t enter the right credentials. It’s expected to see some number of these errors in your logs due to users making mistakes. |
| Error Code | 50053 |
| Message | The account is locked, you’ve tried to sign in too many times with an incorrect user ID or password. |
| Remediation | The user is blocked due to repeated sign-in attempts. See https://docs.microsoft.com/azure/active-directory/identity-protection/howto-unblock-user |
Detection with Microsoft toolings
Now it is time for the detection. Of course prevention is always better. The next topic is all based on prevention with Microsoft toolings. In case to minimize the impact discovery is important. Multiple toolings are available. For example:
- AzureAD Identity Protection
- Azure Sentinel
Important to track the following events: 50126 and 50063.
Azure Sentinel
For Azure Sentinel connect the Azure Active Directory connector. Collect the Sign-in Logs/ Audit Logs and other Sign-in logs. Always good to enable more events for analysis.
For enabling the Azure Active Directory connector:
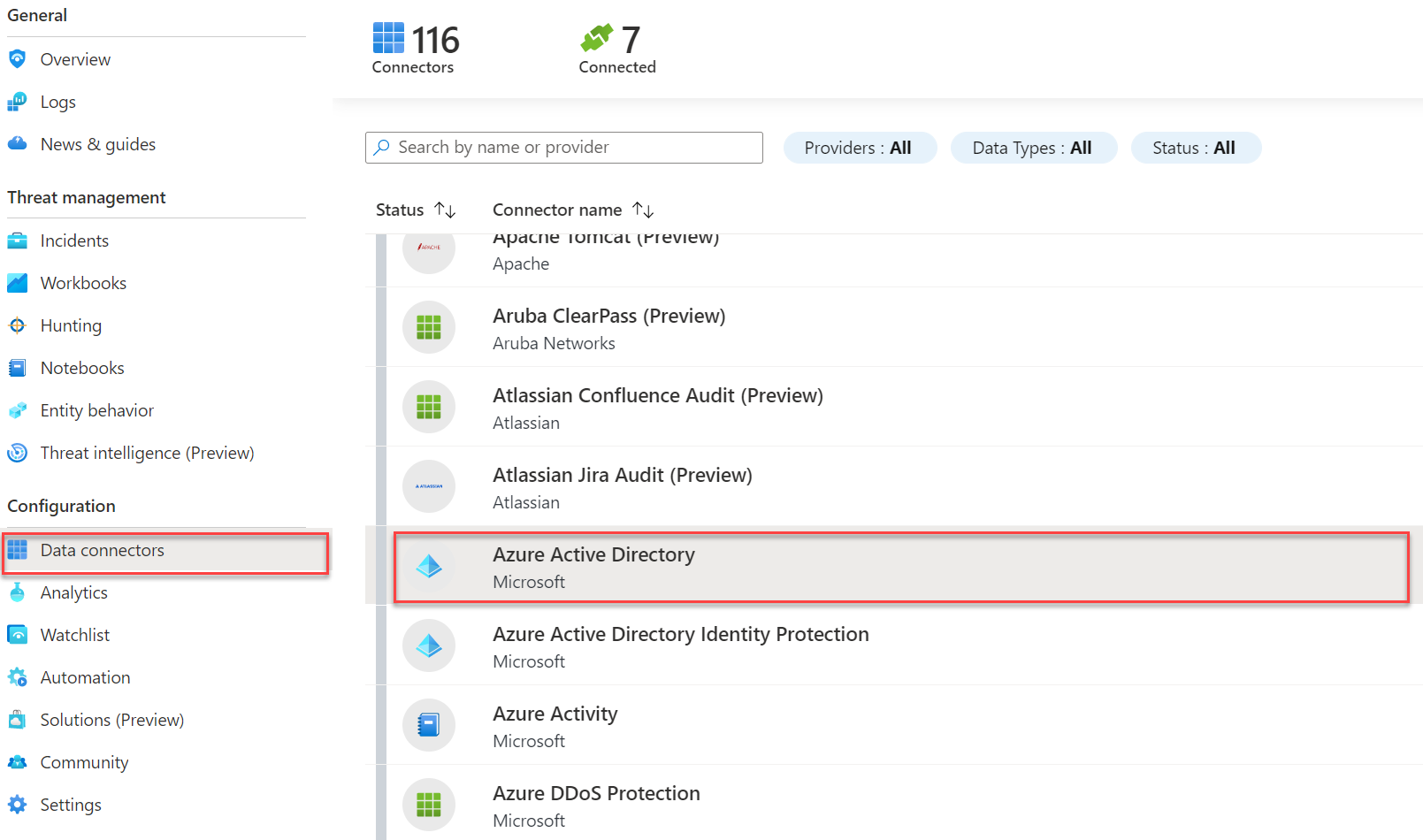
- Go to Azure Sentinel
- Click on Data connectors
- Search for Azure Active Directory
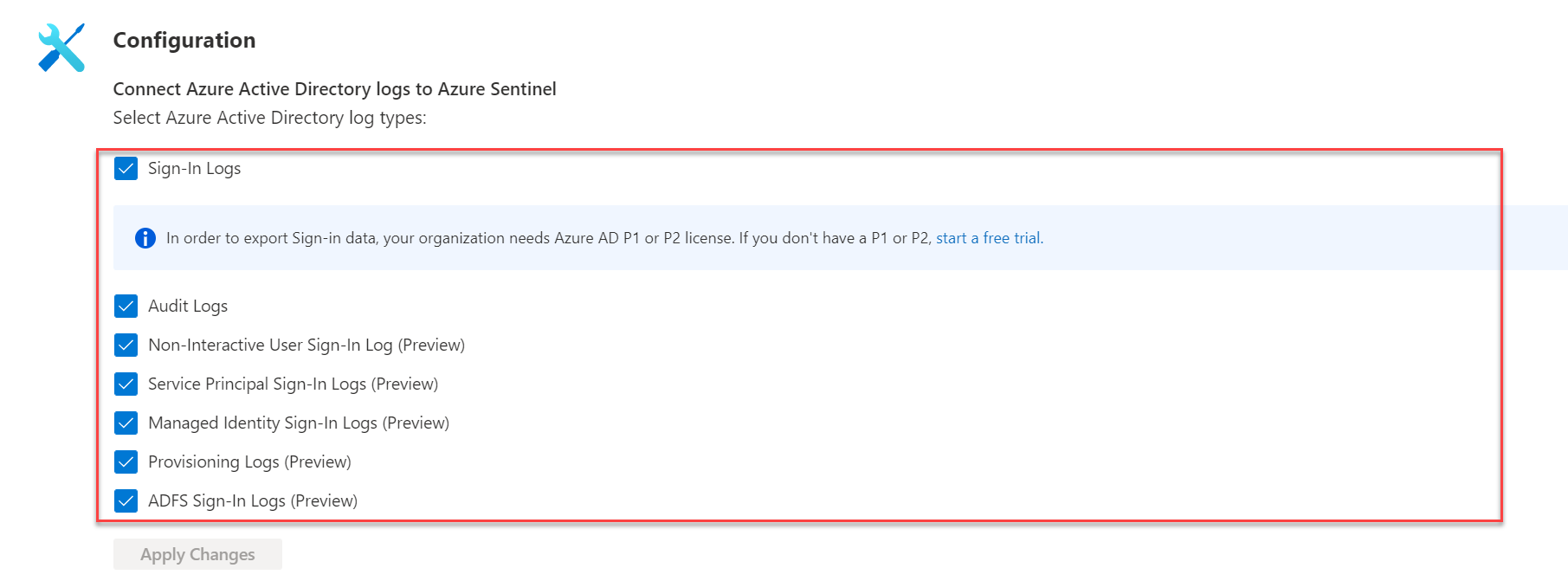
- Configure the log types
- Make sure Audit Logs is enabled
Note: Azure P1 or P2 is needed for export Sign-in data.
Azure Sentinel – KQL
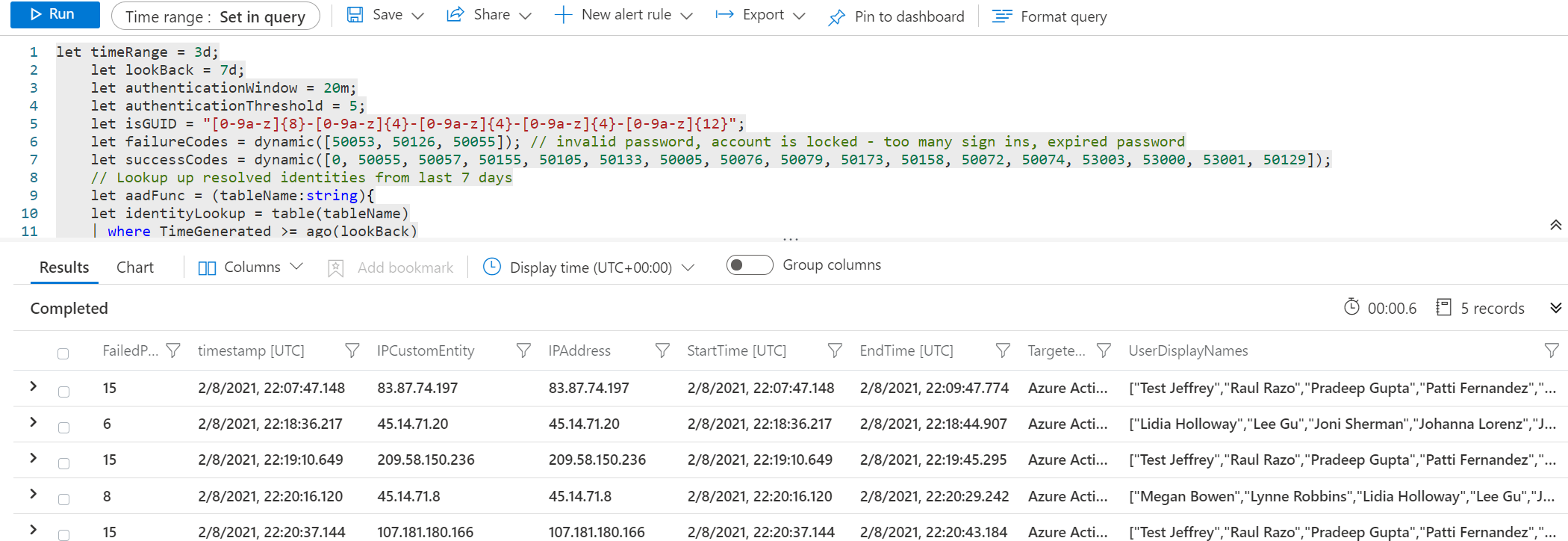
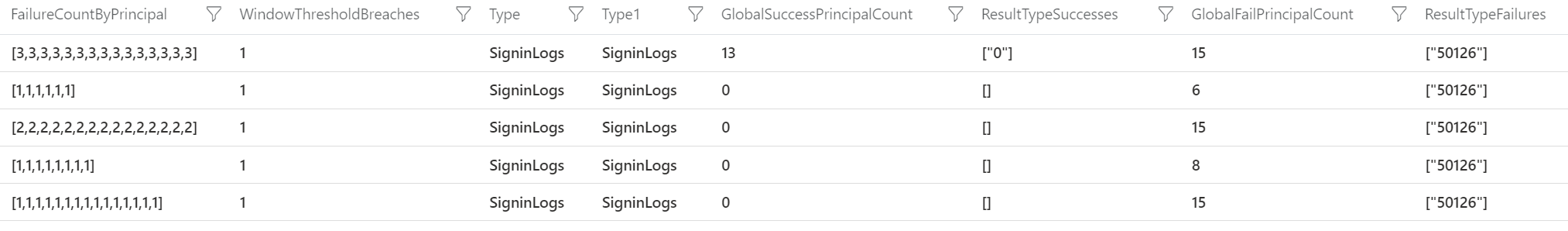
Based on eventID 50053/ 50126 multiple ways are available for discovering password spray attacks. With the option summarize by location there is the option to summarize users based on the location and IP. All below are basic KQL query’s.
For production environments extension of the query is possible with some watchlist items with all corporate IPs.
Basic example:
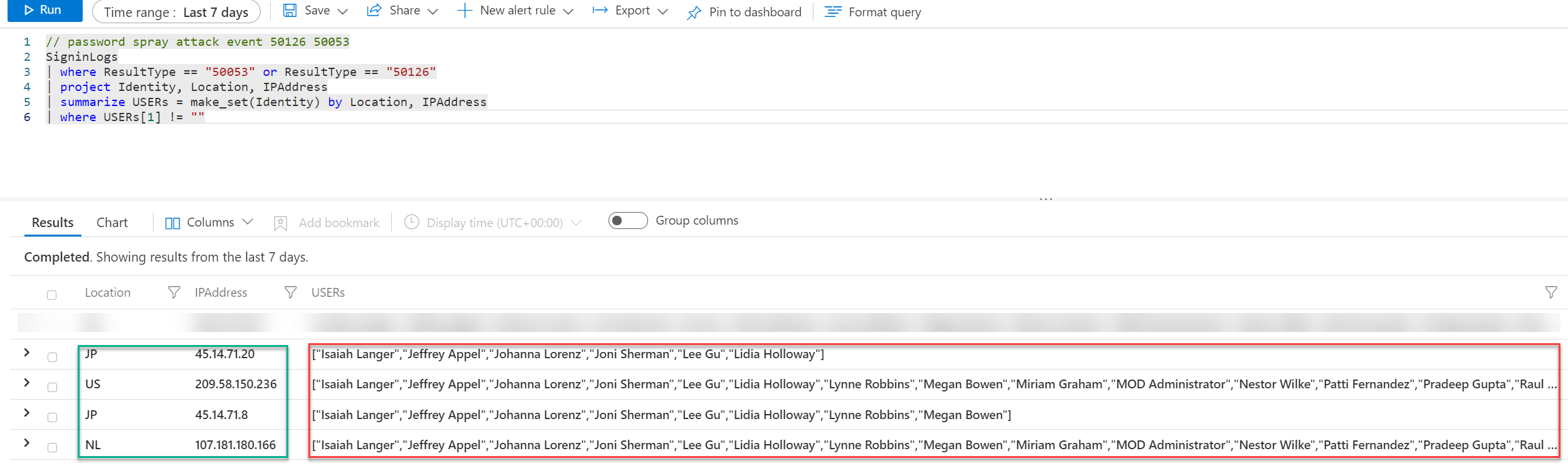
// password spray attack event 50126 50053
SigninLogs
| where ResultType == “50053” or ResultType == “50126”
| project Identity, Location, IPAddress
| summarize USERs = make_set(Identity) by Location, IPAddress
| where USERs[2] != “”>
With the item USERs[2] != “” you can specify the visible users. For example with [2] all results are based on 2+ users. With [10] all events are visible with more than 10+ users.
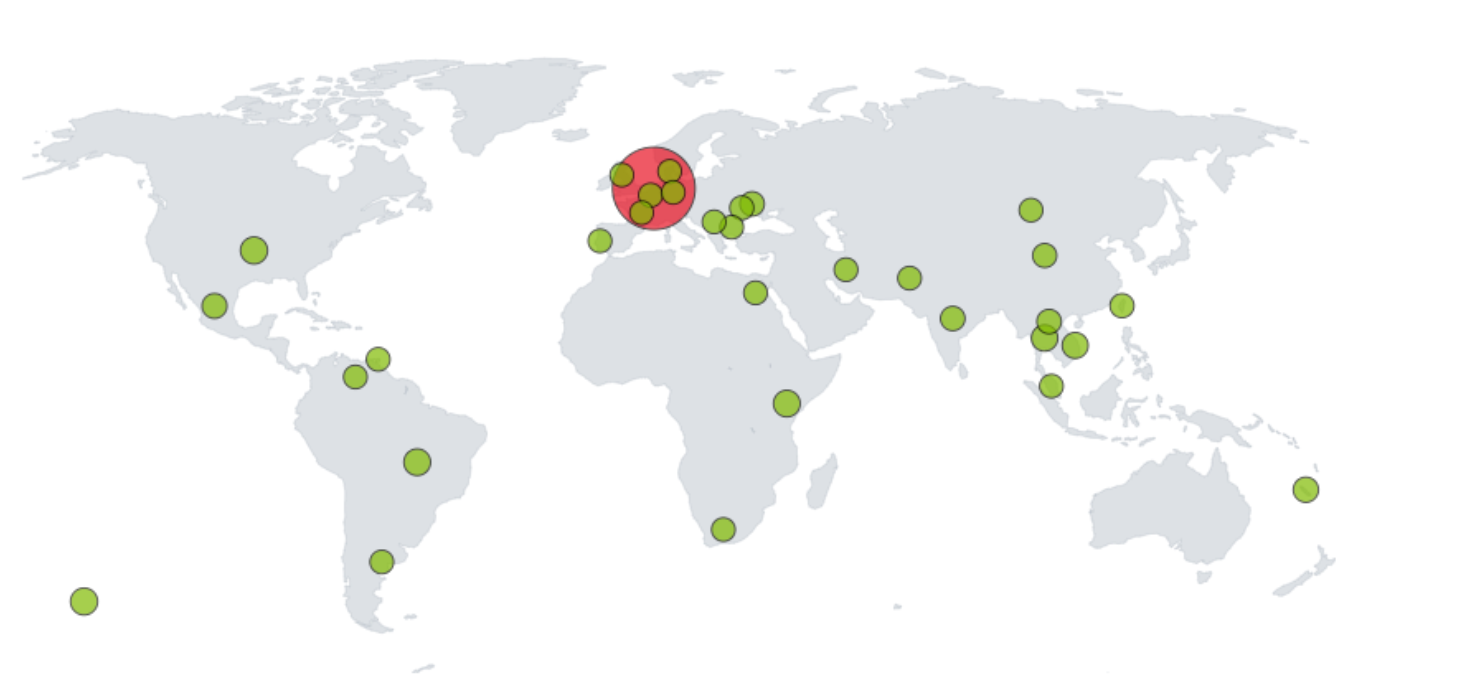
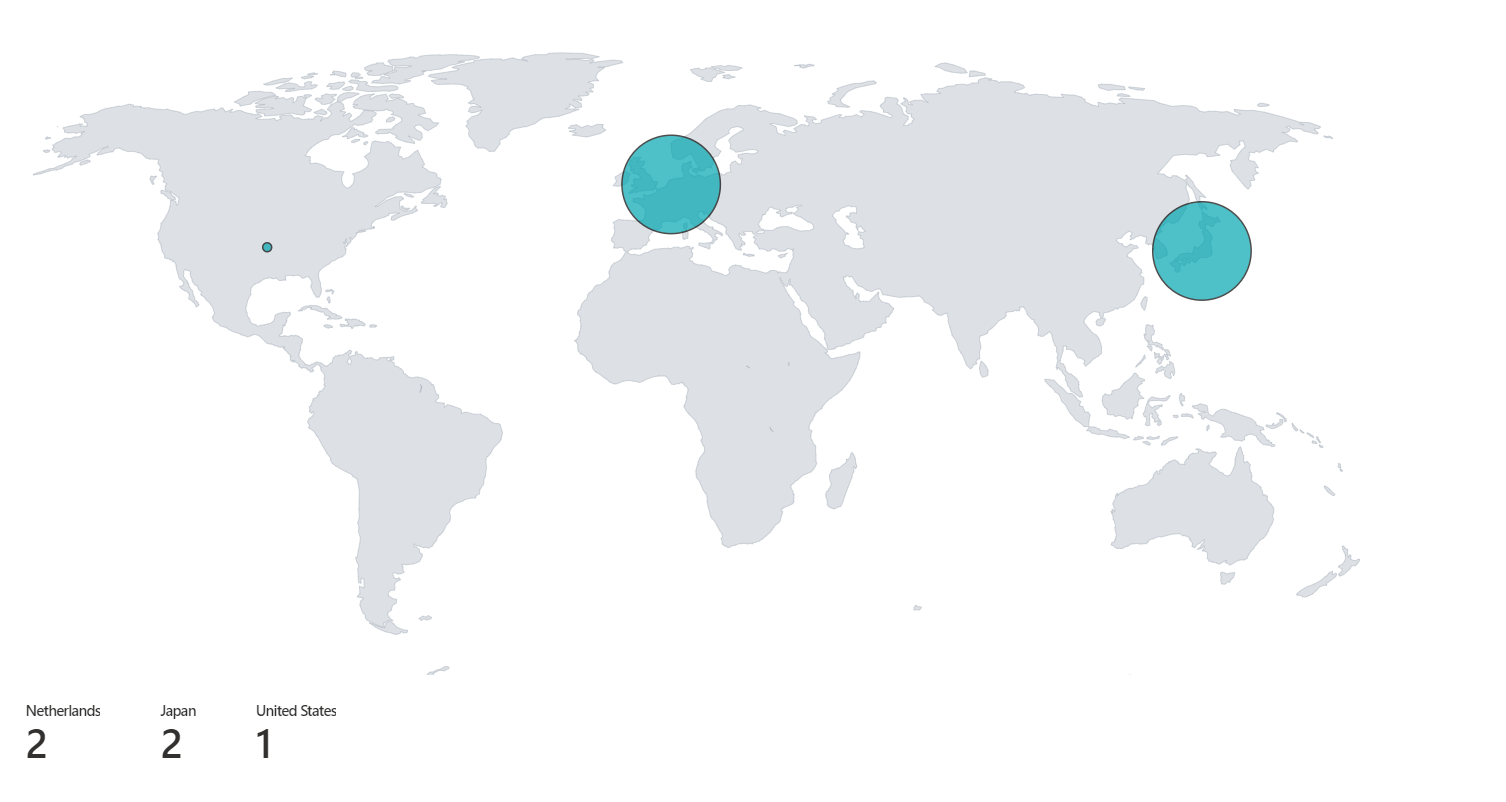
Example below: From location JP with the IP 45.14.71.20 the password spraying for the users is visible.
Azure AD Identity Protection
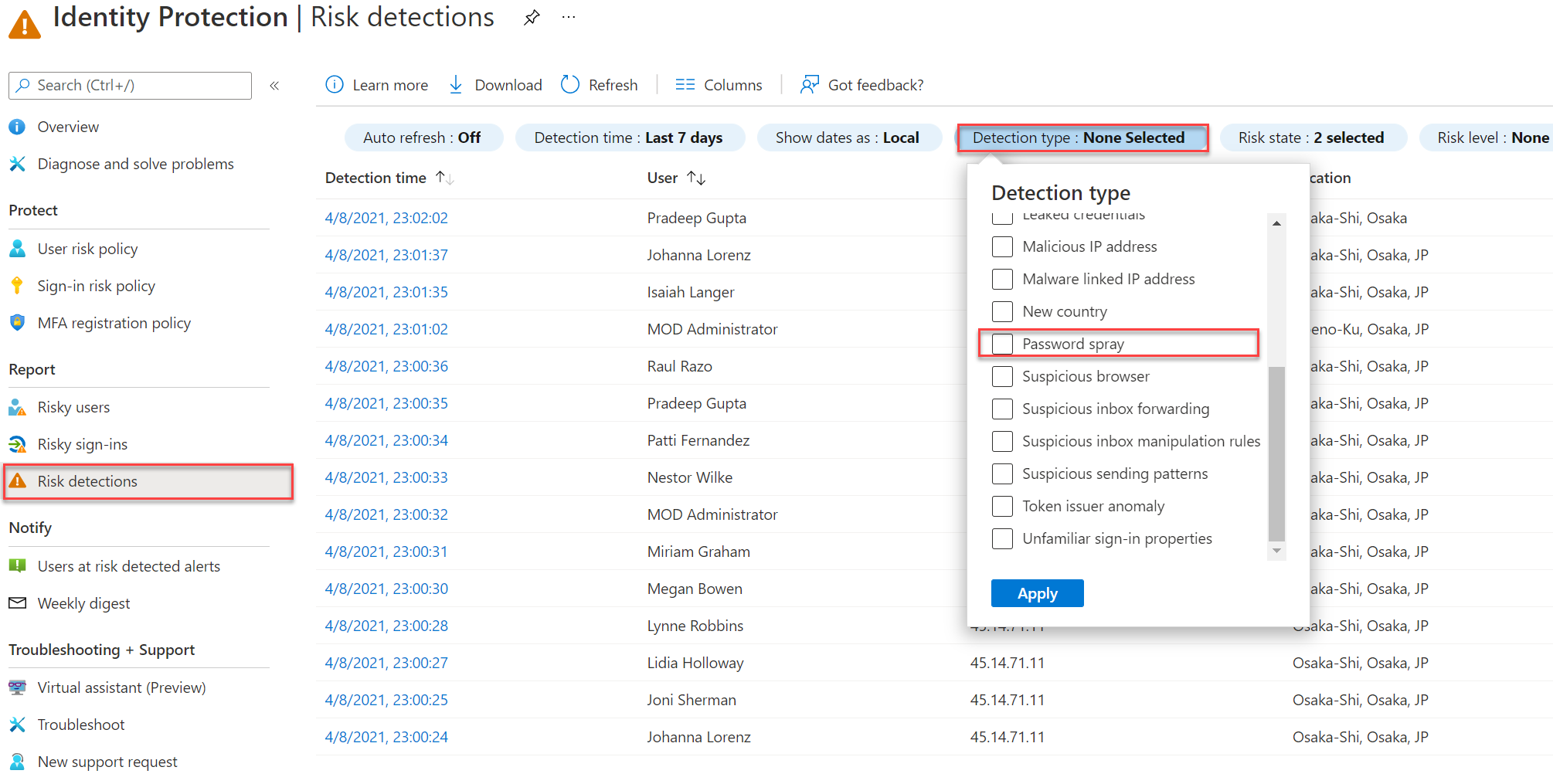
With machine learning logic AzureAD Identity Protection have the option to detect Password spray attacks. For viewing the Identity Protection Brute force risk detections.
- Go to Azure AD
- Open Identity Protection
- Go to Report – Risk detections
- Use the filter option for configuring the detection type. For the Password spraying events the detection type contains: Password spraying
The best way to train the system to learn a user’s properties is to use the risky sign-in policy with MFA. When a risky sign-ins is prompted for MFA and the user successfully responds to the request, the sign-in can succeed and help to train the system on the legitimate user’s behavior.
The Password Spray detection is part of the Sign-in risk with the detection type: Offline
Protection of the Azure AD environment
AzureAD protection is important. Multiple toolings are available for detection and protection against brute-force/ password spraying.
Azure AD Password Protection
First Azure AD Password Protection is important. With AzureAD Password Protection it is possible to protect users against easily guessed passwords and customize the lockout settings for the environment. Password Protection is available for cloud and on-prem resources.
Banned password list
For corporate environments, it is useful to protect multiple passwords by default which contain information that is easy to connect with the organization, such as:
- Company names
- Product names
- Locations
- Company terms
- Internal terms
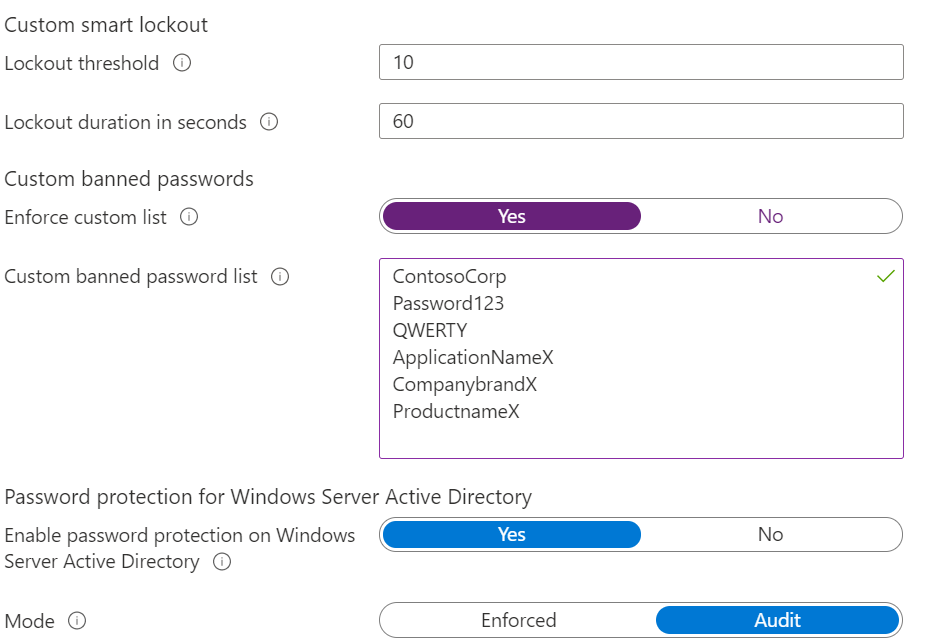
Microsoft will add more combinations automatically in the list of combinations. Once terms are added to the custom banned password list, they will be combined with the global banned password list when validating new passwords. For example, if you add the password “ContosoCorp” the following combination will be blocked by the algorithm.
- ContosoCorp!1
- ContosoCorp@
- ContosoCorp!2
- 1ContosoCorp
- …
- …
For configuring the banned password list. Browse to Azure Active Directory > Security > Authentication methods > Password protection.
Protect passwords & identity
The best and most effective way in combination with the other protection features is the reduction of passwords. For AzureAD multiple passwordless solutions are available. For example:
- Windows Hello
- FIDO2 Security keys
- Microsoft Authentication app/ Phone sign-in
Of course, start always with enabling Multi-Factor Authentication for all accounts and start with a good Conditional Access baseline for all accounts. Including Service accounts, admin accounts, and the break-glass account.
Blogs for more information about Protection passwords & Identity:
- Track the registration and usage of all authentication methods
- Monitor Azure AD break-glass accounts with Sentinel
- Go Fully passwordless with the new AzureAD TAP feature
Legacy authentication
Another important task is to block legacy authentication for all sign-ins. Legacy authentication is the most compromising sign-in. Microsoft is going to disable basic/ legacy authentication. It is recommended to implement Legacy Authentication as soon as possible and switch users to the latest modern authentication protocol. MFA or Passwordless is not enough. Hackers can still brute force passwords using older protocols without any modern authentication.
More about Legacy authentication in this blog: https://jeffreyappel.nl/block-legacy-authentication-now-and-dont-wait-for-microsoft/
Identity protection
Identity Protection is the tool for protecting AzureAD accounts. Microsoft uses a new machine learning technique in Identity Protection to detect password spraying.
For protecting and insights it is highly recommended to enable Identity Protection. Read this blog for more information: https://jeffreyappel.nl/azure-ad-identity-protection-user-risk-and-sign-in-risk-protection-with-automation/
Conclusion
Insights against brute force are important. Some basic AzureAD protection features can give easy protection against password spraying. With Sentinel more insights are possible.
And if you have no MFA enabled: enable it and configure some Conditional Access rules for block legacy authentication, service account only from the corporate location, Break-Glass accounts, and some compliance baselines. The basics are important.
Next blog more information about Cloud App Security & Defender for Identity for on-prem AD events.
Source
Medium/ Derk van der Woude: Azure AD Password spray; from attack to detection (and prevention)
Microsoft: Eliminate bad passwords using Azure Active Directory Password Protection
Microsoft: Connect Azure Active Directory (Azure AD) data to Azure Sentinel
Microsoft: Protecting your organization against password spray attacks